Network security market trends
2016-2020 China's network security industry market size (unit: 100 million yuan)

Since 2016, the Ministry of Public Security has carried out practical offensive and defensive exercises against critical information infrastructure every year, which is called "Network Protection Operation". With the advent of the Equal Protection 2.0 era, the scope of the "Network Protection Operation" in 2019 has been expanded to the industry , Security, Armed Police, Transportation, Railway, Civil Aviation, Energy, News, Radio and Television, Telecom Operators, etc. The implementation of Equal Guarantee 2.0 will bring new growth momentum to the cyber security industry.
In 2020, global APT activities have shown three characteristics: epidemic hotspot information has become a common decoy for APT activities, supply chain and remote office have become entry points for attacks, and targeted blackmail threats have become a new trend in APT activities.
In 2020, the types of security incidents of large and medium-sized government and enterprise organizations, the top three types are:Malicious program (54.5%); Vulnerability exploitation (27.7%); Phishing emails (4.8%).
The report pointed out that 77.6% of enterprises still seek emergency response after major safety incidents have occurred. Only 17.3% of institutions can organize in time through independent inspections before major incidents occur. This shows that the daily safety operation and construction level of domestic government and enterprise institutions still needs to be greatly improved. In particular, 37.3% of agencies sought emergency response after being blackmailed, but at this time it was often too late to remedy the situation.
Cloud security
2017-2021 China's cloud security market scale and growth forecast In
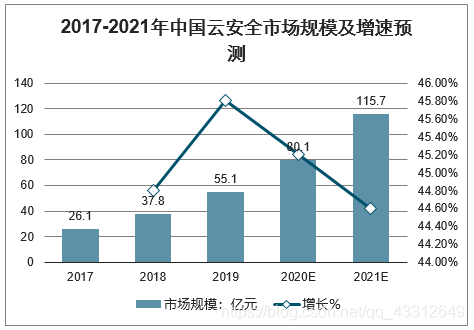
2019, China's cloud security market will reach 5.51 billion yuan, a growth rate of 45.8%, and it is expected to maintain a rapid growth of 40% per year in the next few years.
Traditional threats are in the client and enterprise private cloud environments. As businesses go to the cloud, security risks also go to the cloud. For example, in the past, it was traditionally believed that the Linux system had no malware and no security software. Today, the industrial Internet has become popular, and this misconception has been completely broken. The cloud has become a new battlefield of cyber security filled with smoke.
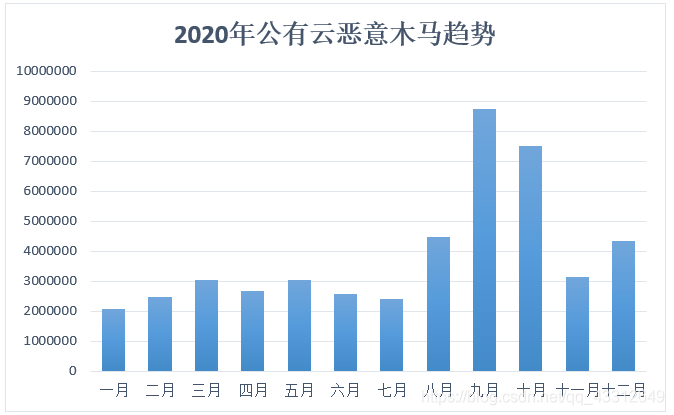
Malicious Trojan horse incidents have increased significantly, 27% have found that Trojan horses have not been dealt with in time
The report shows that 6.3% of public cloud environments have had malicious Trojan horse incidents within one month. This shows that it is no longer a small probability event that the host on the cloud encounters a malicious Trojan horse threat (statistically, a probability of less than 5% is considered a small probability event). Among the common types are: mining Trojans, DDoS attack Trojans, backdoor Trojans, and mining Trojans are the most popular. From the processing results, 27% of the malicious Trojan horse incidents found were not handled in a timely manner, and even 1% were trusted. From the monthly trend of malicious Trojans, there is a clear upward trend.
Blasting attacks occur throughout the year at UHF, and the default user name and port name have been attacked billions of times
Blasting attacks increased significantly throughout the year. On the attack ports, the default ports 22 and 3389 were attacked by a staggering 3.2 billion times and 1.7 billion times. From the user name used in blasting attacks, the default user name was attacked 7 billion times. Among them, root has exceeded 3.7 billion times, administrator has nearly 3.3 billion times, and admin has nearly 2.2 billion times.
VPN vulnerability attack
In 2020, APT attacks using VPN vulnerabilities are very active. According to foreign security agencies, Fox Kitten organized by APT used multiple VPN vulnerabilities to launch attacks against multiple target organizations, including Pulse Secure (CVE-2019-11510), Fortinet FortiOS (CVE-2018-13379) and Palo Alto Networks VPN (CVE-2018-1579) and other security vulnerabilities in VPN systems. Related activities continued throughout 2020.
In addition, from February to April 2020, Darkhotel and Wellmess organizations also used security vulnerabilities in a well-known VPN system in my country to conduct attacks. The actions of the former are mainly aimed at grassroots units, while the latter are mainly aimed at important institutions such as China's aerospace and research institutes. In addition to VPN, in 2020, a world-renowned video conference software will also be repackaged by the APT organization and put on multiple download sites at home and abroad.
references
"Qianxin Releases Seven Cyber Security 2020 Annual Research Reports"
"Tencent 2020 Public Cloud Security Report"