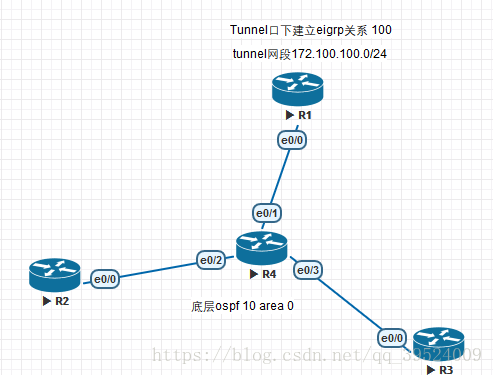
实验环境:利用tunnel口建立GRE隧道,Tunnel口地址建立邻居关系
基于Tunnel口来进行隧道的加密,此时加密点和传输点一致:
- 加密点:对流量进行加密的接口
- 传输点:加密的流量的源目地址对
只有加密点和传输点一致的环境,可以使用transport模式;默认是tunnel模式(会封装新的头部)
流程步骤
- 内部IP头部源地址为私网地址
- 流量进入SITE路由器,匹配路由发往tunnel口,封装新的IP头(基于tunnelde source和destination)
- 发往实际的物理出口,ESP对数据包进行加密,因为加密点和传输点一致,所以使用传输模式,不需要再封装ESP新头部。
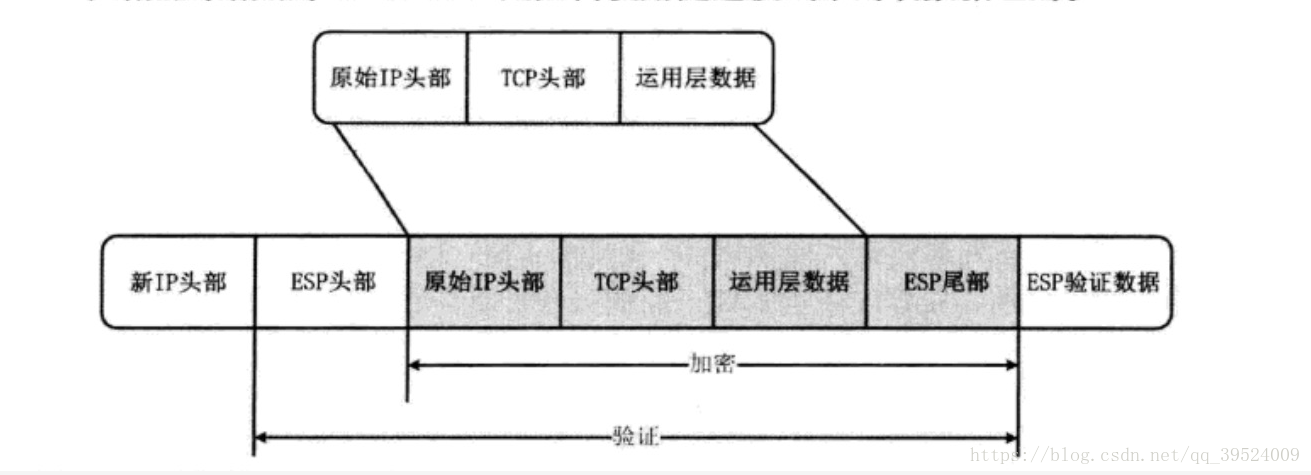
隧道模式:
隧道模式:
加密配置(物理口调用):[SITE-A]
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 21.15.13.3
!
crypto ipsec transform-set lw esp-aes esp-md5-hmac
mode transport //也可以是tunnel但是会多个二层封装头部,是数据帧变长
!
crypto map vpn 10 ipsec-isakmp
set peer 21.15.13.3
set transform-set lw
match address 110
!
interface Ethernet0/0
crypto map vpn
access-list 110 permit gre host 61.100.1.1 host 21.15.13.3
//此时的感兴趣流协议为GRE(因为有限经过tunnel口进行隧道封装)此时的源目地址为tunnel口地址加密配置(Tunnel口调用):
SiteB(ipsec-profile)#do show run | s cry
no service password-encryption
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 61.100.1.1
crypto ipsec transform-set lw esp-aes esp-md5-hmac
mode transport
crypto ipsec profile lw
set transform-set lw
SiteB(ipsec-profile)#int tunnel 10
SiteB(config-if)#tunnel protection ?
ipsec Use ipsec to protect this tunnel interface
SiteB(config-if)#tunnel protection ipsec ?
profile Determine the ipsec policy profile to use.
SiteB(config-if)#tunnel protection ipsec profile ?
WORD IPSec policy profile
SiteB(config-if)#tunnel protection ipsec profile lw
SiteB(config-if)#
*Sep 12 03:12:31.470: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
SiteB(config-if)#
*Sep 12 03:12:34.823: %OSPF-5-ADJCHG: Process 10, Nbr 172.100.100.1 on Tunnel10 from LOADING to FULL, Loading Done
//不需要定义PEER和感兴趣流,由tunnel口下的源目地址来填充这一部分缺失
针对于所有的GRE或者MGRE的隧道都可以使用方法二来进行隧道加密;物理口下和tunnel口下的加密方式是可以共存的
DMVPN
四大协议部分
- MGRE,形成点到多点的隧道网络环境(区别于点到多点)
- NHRP
- 帮助我们在MGRE环境中确定TUNNEL的destination;同时解决组播转单播的映射问题
- IGP
- tunnel 和tunnel之间的动态路由协议
- IPSEC对隧道加密
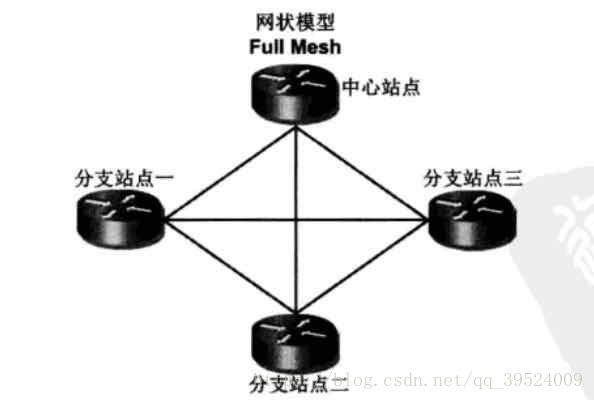
传统IPSEC VPN星型拓扑:
- 中心站点配置最大(每次有新的站点加入都要建立新的tunnel)
- 分支站点间流量延时较大(多次的加密解密)
- 分支站点流量占用中心带宽
网状IPSEC VPN 模型:
- 中心与分支站点配置量大
- 分支站点维护过多的IPSEC SA(功能上已经没有分支和核心的区别)
- 分支站点需要固定的IP地址
R2(config-if)#tunnel source 24.1.1.2
R2(config-if)#tunnel mode gre multipoint
//没有配置destination 而是修改gre为mgre模式
由NHRP协议完成destination的配置HUB端:
HUB(config)#int tunnel 10
HUB(config-if)#ip nhrp network-id 1 //同一域内
HUB(config-if)# ip nhrp redirect //开启nhrp重定向
HUB(config-if)#ip nhrp map multicast dynamic //开启动态接受组播映射
HUB(config-if)#ip nhrp authentication lw //nhtp认证,在同一个vpn环境中使用相同的认证名
HUB(config-if)#tunnel source 24.1.1.2
HUB(config-if)#tunnel mode gre multipoint SPOKE端:
//
interface Tunnel10
ip address 172.100.100.3 255.255.255.0
no ip redirects
ip nhrp authentication lw
ip nhrp map multicast 14.1.1.1
//Mgre网络类型不支持组播,必须要组播转单模进行hello包的发送;
HUB端动态接受spoke发送来的映射,spoke端根据手动静态配置的组播地址映射地址
封装二层头部进行数据发送
------------基本nhrp配置
ip nhrp network-id 1
ip nhrp shortcut
tunnel source Ethernet0/0
tunnel mode gre multipoint静态映射
R2(config-if)#ip nhrp nhs 172.100.100.1
//配置映射时 先tunnel地址 后物理地址
R2(config-if)#ip nhrp map 172.100.100.1 14.1.1.1
//此时nhrp主动由spoke端向hub端发送注册消息现象
//HUB端的nhrp映射为spoke端发送注册信息所获得
HUB#show ip nhrp detail
172.100.100.2/32 via 172.100.100.2
Tunnel10 created 00:07:38, expire 01:54:31
Type: dynamic, Flags: unique registered used nhop
NBMA address: 24.1.1.2
172.100.100.3/32 via 172.100.100.3
Tunnel10 created 00:03:26, expire 01:57:35
Type: dynamic, Flags: unique registered used nhop
NBMA address: 34.1.1.3 R2(config-if)#do show ip nhrp detail
172.100.100.1/32 via 172.100.100.1
Tunnel10 created 00:06:20, never expire
Type: static, Flags: used
NBMA address: 14.1.1.1 R2(config-if)#do show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
T1 - Route Installed, T2 - Nexthop-override
C - CTS Capable
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
==========================================================================
Interface: Tunnel10, IPv4 NHRP Details
Type:Spoke, NHRP Peers:1,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 14.1.1.1 172.100.100.1 UP 00:10:30 STUNNEL 口下的IGP配置
HUB(config-if)#no ip split-horizon eigrp 10- //关闭EIGRP的水平分割,否则从tunnel 口学到的spoke1的路由是没有办法传递给spoke other的
- 如果tunnel口运行的是ospf则需要修改网络类型为点到多点
- HUB:ip nhrp redirect,通过nhrp的重定向 将spoke端发出的nhrp映射,重定向给其他hub端
- SPOKE:ip nhrp shortcut:接收到来自hub的nhrp重定向消息,在spoke和spoke选择最优路径形成隧道
- 动态形成spoke和spoke之间隧道后,流量可以基于spoke之间的动态tunnel来封装的;
- 但是此时数据包转发依旧受制于ip路由的下一跳
interface Tunnel10
ip address 10.62.62.1 255.255.255.0
no ip redirects
no ip next-hop-self eigrp 10
//通过在hub tunnel口下取消下一跳自己,使spoke和spoke之传递的路由 下一跳为对端spoke而不是hub
no ip split-horizon eigrp 10
//取消水平分割
ip nhrp authentication lw
ip nhrp map multicast dynamic
ip nhrp network-id 1
ip nhrp redirect
tunnel source 12.1.1.1
tunnel mode gre multipoint在EIGRP中动态形成全网拓扑
Spoke1(config)#do show ip rou
Gateway of last resort is not set
1.0.0.0/32 is subnetted, 1 subnets
D 1.1.1.1 [90/27008000] via 10.62.62.1, 00:00:44, Tunnel10
3.0.0.0/32 is subnetted, 1 subnets
C 3.3.3.3 is directly connected, Loopback0
4.0.0.0/32 is subnetted, 1 subnets
D 4.4.4.4 [90/28288000] via 10.62.62.4, 00:00:44, Tunnel10
5.0.0.0/32 is subnetted, 1 subnets
D 5.5.5.5 [90/28288000] via 10.62.62.5, 00:00:44, Tunnel10
--------修改hub关闭ip nexi-hop-self使spoke之间建立隧道进行通信--------
Gateway of last resort is not set
1.0.0.0/32 is subnetted, 1 subnets
D 1.1.1.1 [90/27008000] via 10.62.62.1, 00:00:55, Tunnel10
4.0.0.0/32 is subnetted, 1 subnets
D 4.4.4.4 [90/28288000] via 10.62.62.4, 00:00:55, Tunnel10
5.0.0.0/32 is subnetted, 1 subnets
D 5.5.5.5 [90/28288000] via 10.62.62.5, 00:00:55, Tunnel10DMVPN排错:
如果查看所有DMVPN配置都正常;从HUB端到spoke端逐一shutdown tunnel接口
从hub到spoke端的tunnel口,会使得tunnel口重新发送nhrp注册消息
发送预共享秘钥的对端地址不明确,所以用0.0.0.0 0.0.0.0 来代替
crypto isakmp policy 10
encr aes
hash md5
authentication pre-share
group 2
crypto isakmp key cisco address 0.0.0.0
!
!
crypto ipsec transform-set lw esp-aes esp-md5-hmac
mode tunnel
!
crypto ipsec profile Mgre
set transform-set lw