本期实验适用在防火墙ipsec vpn多出口的场景,看拓扑
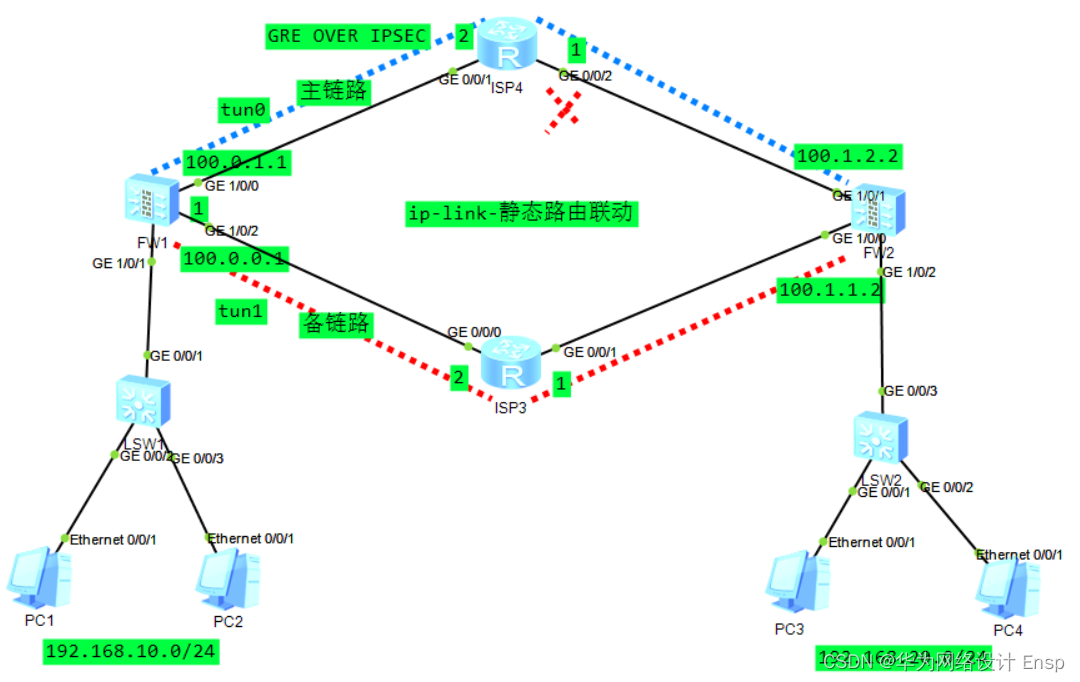
IPSEC 对两个私网流量加密,通过GRE进行选路,通过静态路由来控制选路,但是主链路中的热任何节点故障,防火墙的主备ipsec流量该如何切换成为难题,这里用ip-link和静态的联动,有效的解决该问题。
上配置
FW1
sysname FW-1
#
ipsec 配置
由于是over进gre所以不需要写感兴趣流
ipsec proposal 1
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
ike peer all
pre-shared-key %^%#SkSdV.BEAL&T*nX~\eD9E#XH<[UdLFb^PLE^:x@I%^%#
ike-proposal 1
#
为两个gre隧道口创建两个ipsec名
ipsec profile fw1-fw2-100
ike-peer all
proposal 1
ipsec profile fw1-fw2-101
ike-peer all
proposal 1
#
接口配置
interface GigabitEthernet1/0/0
undo shutdown
ip address 100.0.1.1 255.255.255.252
service-manage ping permit
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 192.168.10.254 255.255.255.0
service-manage ping permit
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 100.0.0.1 255.255.255.252
service-manage ping permit
#
gre隧道接口配置
interface Tunnel0
ip address 1.1.1.1 255.255.255.252 隧道地址
tunnel-protocol gre 隧道模式为gre
keepalive gre的保活
source 100.0.1.1 本段防火墙出接口地址
destination 100.1.2.2 对端防火墙出接口地址
ipsec profile fw1-fw2-100 调用ipsec
#
interface Tunnel1
ip address 2.2.2.1 255.255.255.252
tunnel-protocol gre
keepalive
source 100.0.0.1
destination 100.1.1.2
ipsec profile fw1-fw2-101
#
防火墙接口加入到区域中
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/1
add interface Tunnel0
add interface Tunnel1
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
add interface GigabitEthernet1/0/2
#
配置ip-link,保证中间链路,路由可达,ip-link状态就会up,通过静态建立ip-link所需要的路由
ip-link check enable
ip-link name test1
source-ip 100.0.1.1
destination 100.1.2.2 mode icmp
destination 100.1.2.2 interface GigabitEthernet1/0/0 mode icmp next-hop 100.0.1.2
ip-link name test2
source-ip 100.0.0.1
destination 100.1.1.2 mode icmp
destination 100.1.1.2 interface GigabitEthernet1/0/2 mode icmp next-hop 100.0.0.2
#
配置到对端防火墙出口路由
ip route-static 100.1.1.0 255.255.255.0 100.0.0.2
ip route-static 100.1.2.0 255.255.255.0 100.0.1.2
配置ipsec流量进入gre隧道流量
ip route-static 192.168.20.0 255.255.255.0 Tunnel1 preference 100 track ip-link test2
ip route-static 192.168.20.0 255.255.255.0 Tunnel0 track ip-link test1
#
安全策略
security-policy
放行ipsec 和 gre 协商策略
rule name tun
source-zone local
source-zone trust
source-zone untrust
destination-zone local
destination-zone trust
destination-zone untrust
action permit
防火墙ipsec业务来回策略
rule name vpn
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.0 mask 255.255.255.0
action permit
rule name vpn-
source-zone untrust
destination-zone trust
source-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
action permit
------------------------------------------------------------------------------------------------------------------------------
FW2
sysname FW-2
#
ipsec proposal 1
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
ike peer all
pre-shared-key %^%#k,_T.U5*aRIHR768Z}#V!"8UUGuKnNtsHqYkUy!3%^%#
ike-proposal 1
#
ipsec profile fw2-fw1-100
ike-peer all
proposal 1
ipsec profile fw2-fw1-102
ike-peer all
proposal 1
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 100.1.1.2 255.255.255.0
service-manage ping permit
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 100.1.2.2 255.255.255.0
service-manage ping permit
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 192.168.20.254 255.255.255.0
service-manage ping permit
#
interface Tunnel0
ip address 1.1.1.2 255.255.255.252
tunnel-protocol gre
source 100.1.2.2
destination 100.0.1.1
ipsec profile fw2-fw1-100
#
interface Tunnel1
ip address 2.2.2.2 255.255.255.252
tunnel-protocol gre
keepalive
source 100.1.1.2
destination 100.0.0.1
ipsec profile fw2-fw1-102
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/2
add interface Tunnel0
add interface Tunnel1
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
add interface GigabitEthernet1/0/1
#
ip route-static 100.0.0.0 255.255.255.0 100.1.1.1
ip route-static 100.0.1.0 255.255.255.0 100.1.2.1
ip route-static 192.168.10.0 255.255.255.0 Tunnel1 preference 100 track ip-link
test2
ip route-static 192.168.10.0 255.255.255.0 Tunnel0 track ip-link test1
#
ip-link check enable
ip-link name test1
source-ip 100.1.2.2
destination 100.0.1.1 mode icmp
destination 100.0.1.1 interface GigabitEthernet1/0/1 mode icmp next-hop 100.1.2.1 ip-link name test2
source-ip 100.1.1.2
destination 100.0.0.1 mode icmp
destination 100.0.0.1 interface GigabitEthernet1/0/0 mode icmp next-hop 100.1.1.1
#
security-policy
rule name tun
source-zone local
source-zone trust
source-zone untrust
destination-zone local
destination-zone trust
destination-zone untrust
action permit
rule name vpn
source-zone trust
destination-zone untrust
source-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
action permit
rule name vpn-
source-zone untrust
destination-zone trust
source-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.0 mask 255.255.255.0
action permit
验证测试
路由
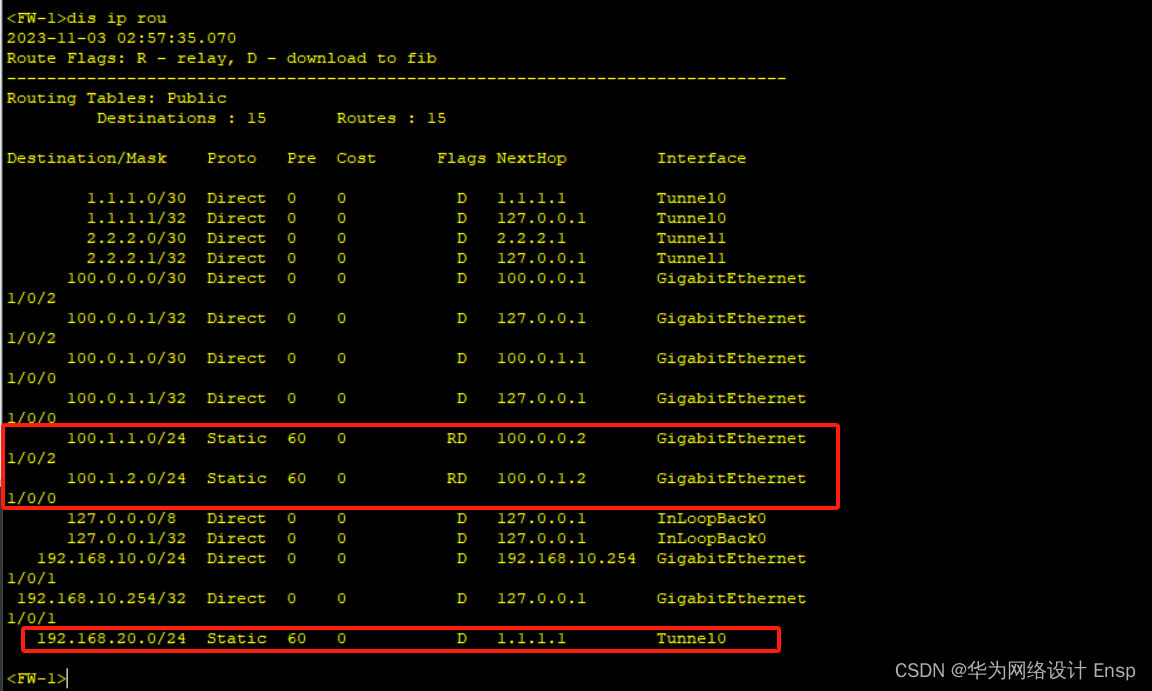
fw1

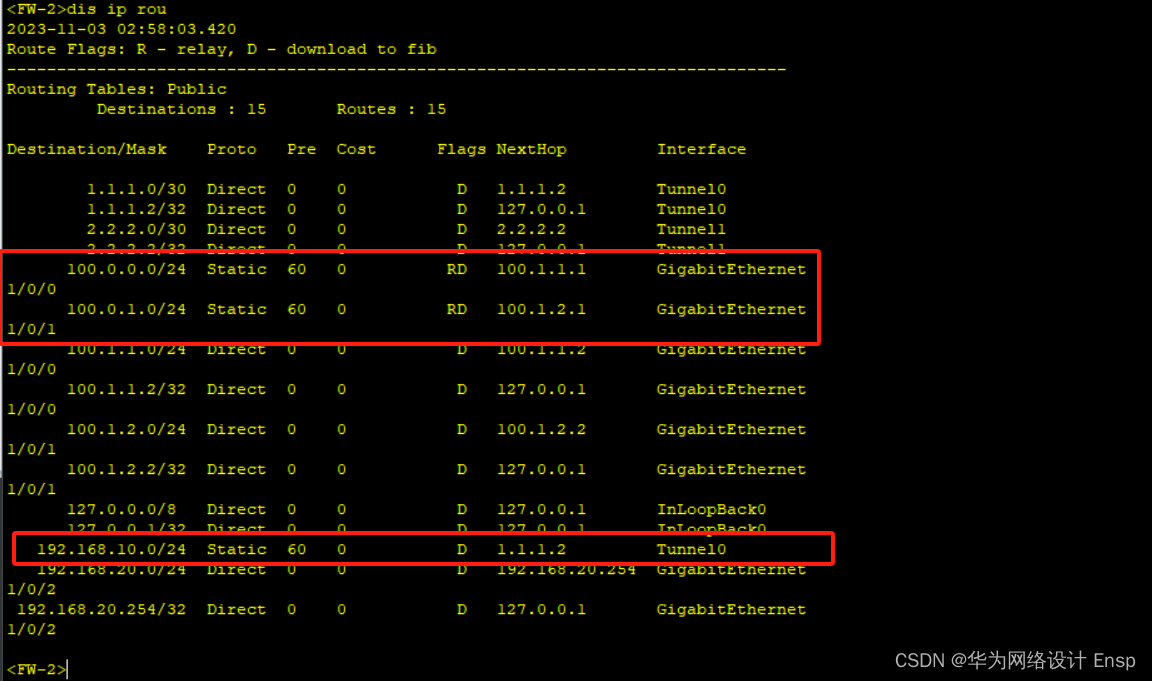
fw2
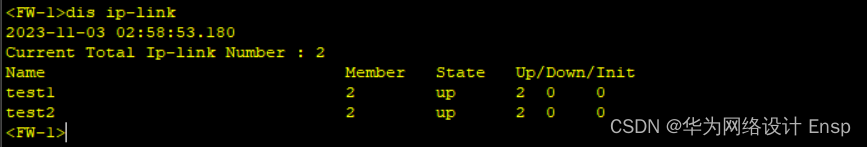
ip-link验证
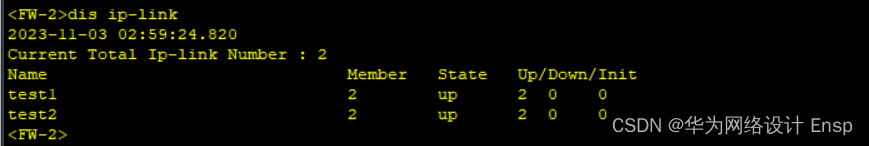
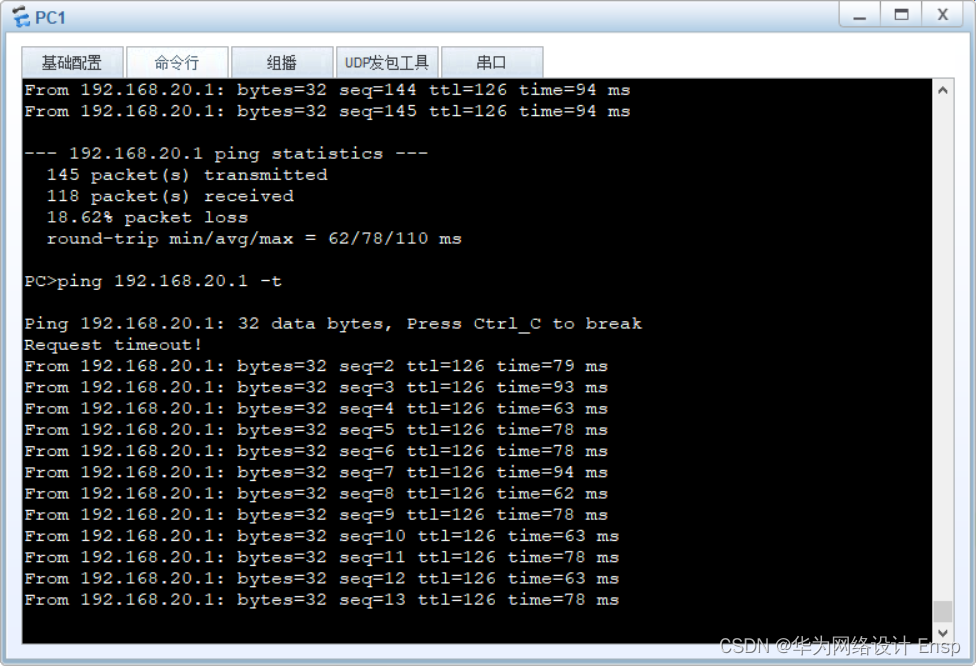
ping测试
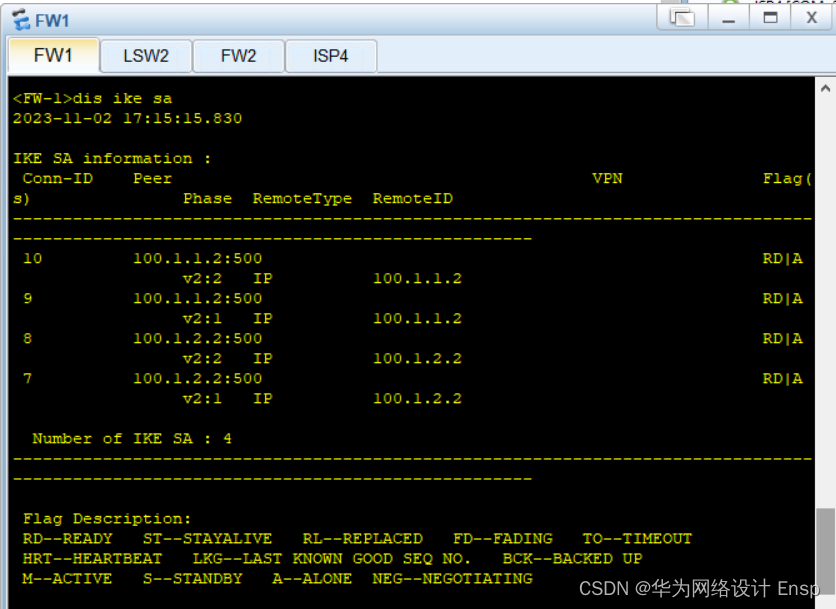
防火墙ike验证
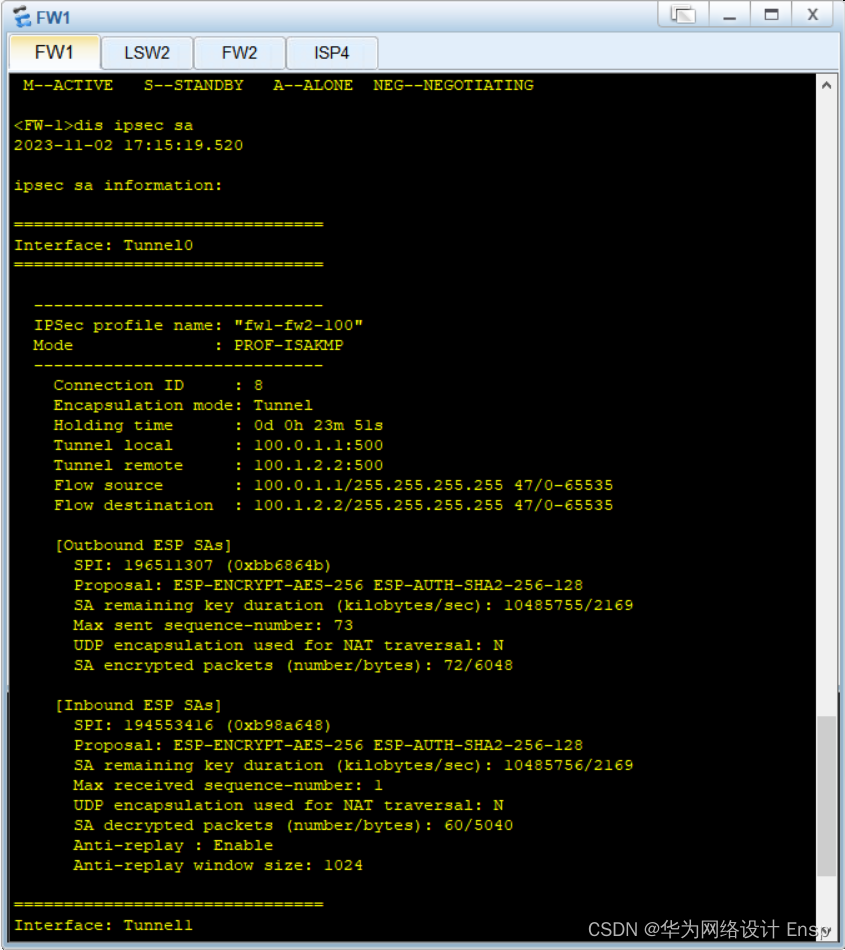
防火墙ipsec 验证
断开主链路
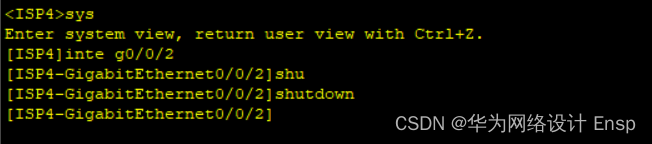
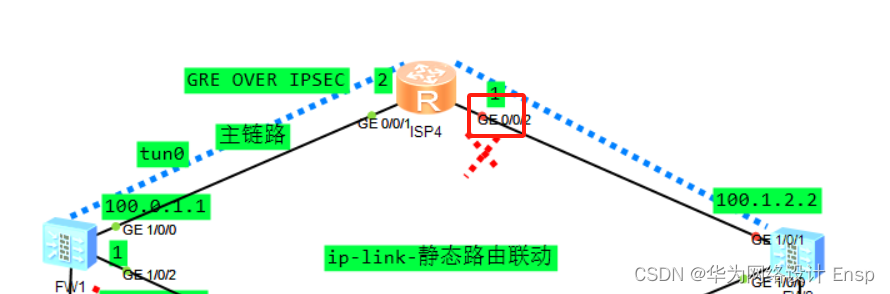
测试
FW监测到直连故障,ip-link探测成功,进行主备切换
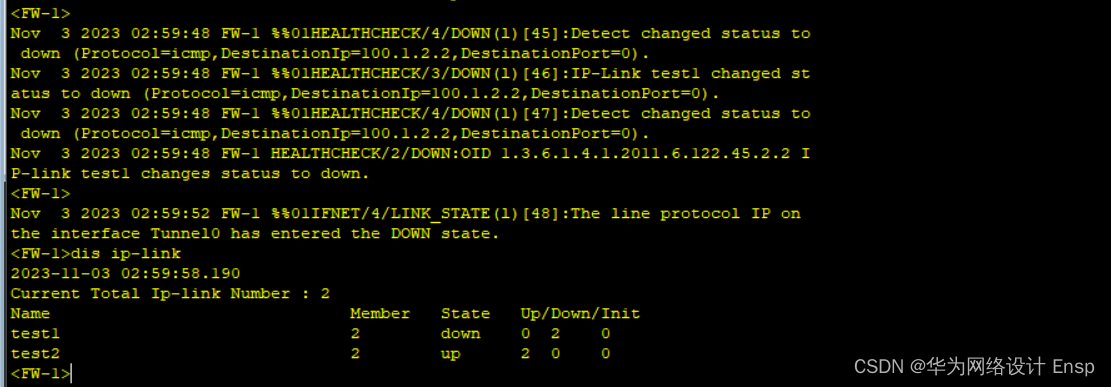
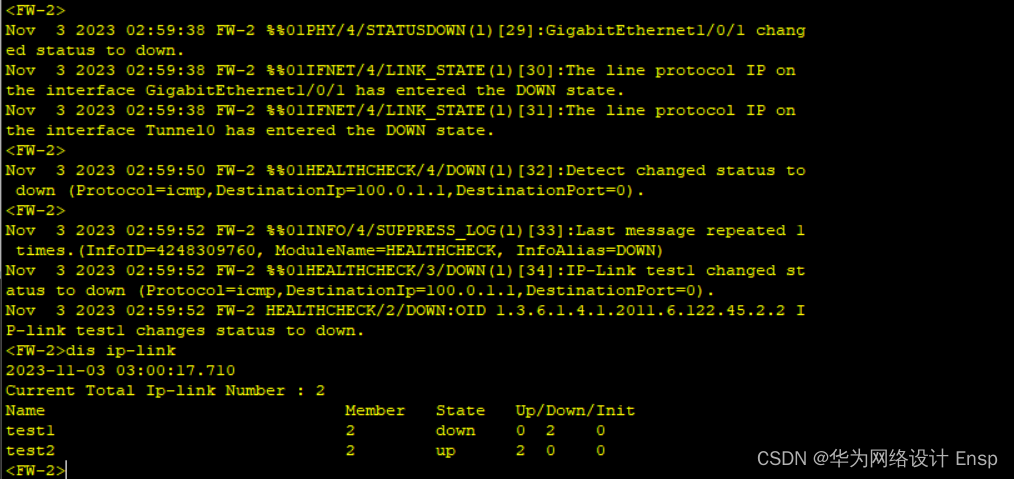
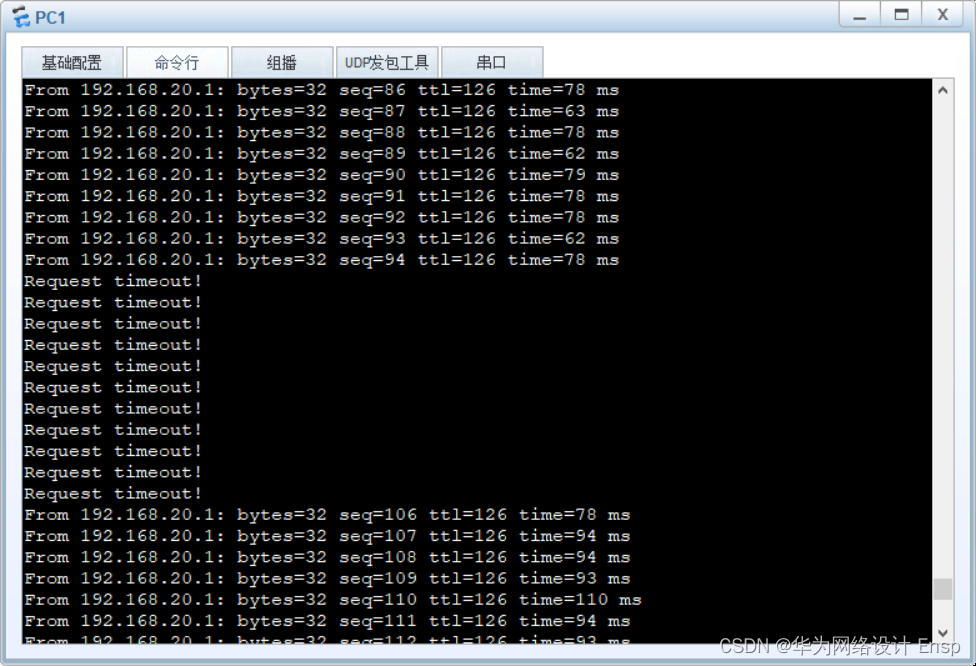
切换成功,回切
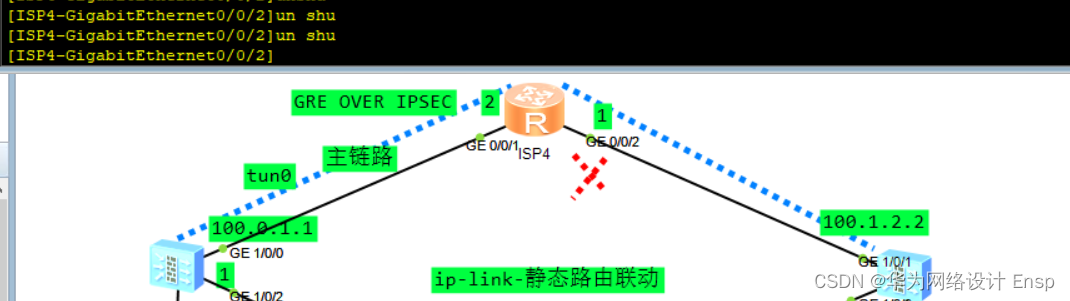
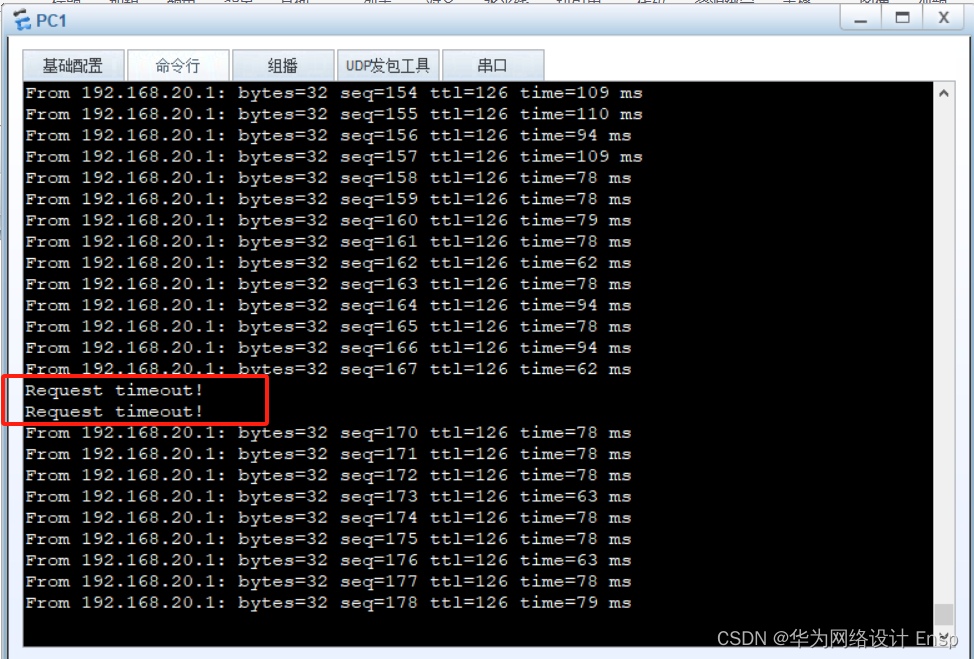
完成整个主备切换测试验证,防火墙推荐用ip-link联动,可以根动态、静态、vrrp等多种协议配合,非常好使。