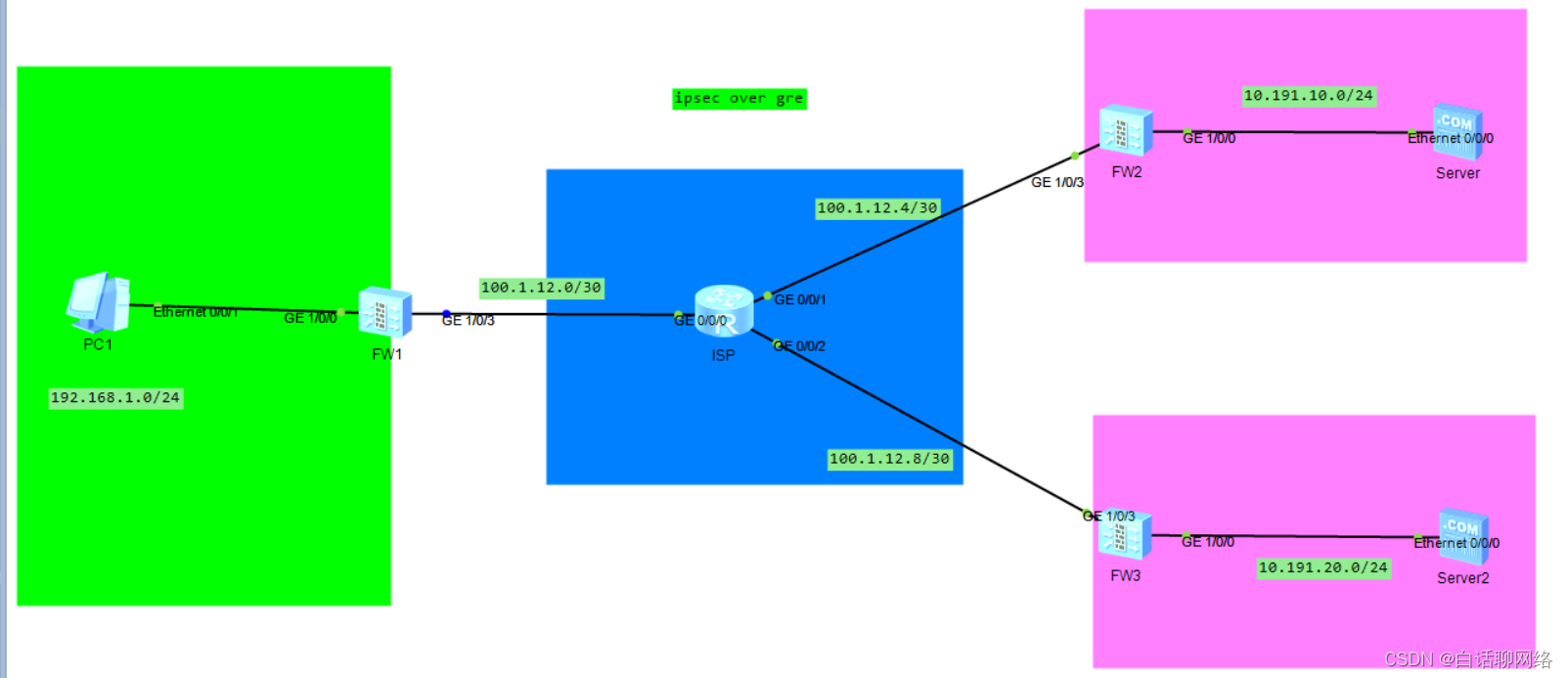
IPsec
主要作用是对数据进行加密,因为他能提供所有有时候被单独用作实现加密的一种方法!IPsec建立的是一个逻辑隧道,并不是真正意义上的隧道!并且不能提供路由功能,因为IPsec不支持非ip流量,也不支持广播(组播)!
GRE
GRE是一种三层VPN封装技术。GRE可以对某些网络层协议(如IPX、Apple Talk、IP等)的报文进行封装,使封装后的报文能够在另一种网络中(如IPv4)传输,从而解决了跨越异种网络的报文传输问题,虽然无法提供加密,但是能很好的支持非ip流量和广播!
GRE over IPSec(使用IPsec来加密隧道进行传输)
GRE OVER IPSEC 是 gre 做内层封装, ipsec 做外层封装,ipsec 感兴趣数据流为 gre源目地址,适用于两点都是固定 ip 或者一方是动态 IP 或内网环境,由于 ipsec 不能传广播和组播,gre 可以,这种环境还可以运行一些适用组播和广播的协议。
IPSec over GRE(加密数据流后从隧道传输)
IPSEC OVER GRE 是 IPSEC 做内层封装,GRE 做外层封装,适用于两端路由器都是固定IP,ipsec 策略应用在物理口,ipsec 感兴趣数据流为业务网段,只对业务数据进行加密。
配置
sysname FW1
配置感兴趣流,源目都是业务地址段
acl number 3000
rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 10.191.10.0 0.0.0.255
acl number 3001
rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 10.191.20.0 0.0.0.255
安全提议正常配置,保证两端的参数一致就ok
ipsec proposal 1
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
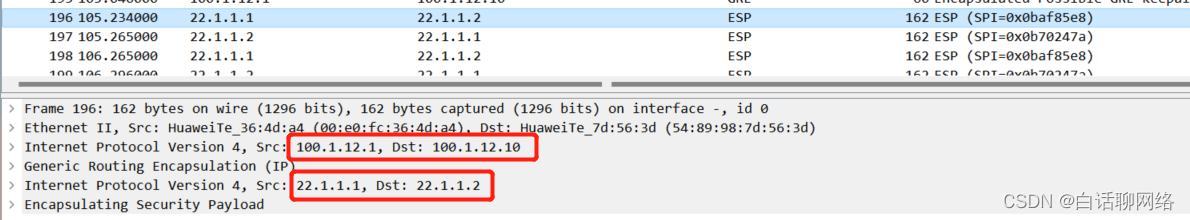
对端地址值得注意,ips over gre的对端地址是隧道地址
ike peer fw2
pre-shared-key huawei@123
ike-proposal 1
remote-address 12.1.1.2 //对端隧道地址
ike peer fw3
pre-shared-key huawei@123
ike-proposal 1
remote-address 22.1.1.2 //对端隧道地址
点到多点的场景中创建两个ipsec策略
ipsec policy ips1 1 isakmp
security acl 3000
ike-peer fw2
proposal 1
ipsec policy ips2 1 isakmp
security acl 3001
ike-peer fw3
proposal 1
interface GigabitEthernet1/0/0
undo shutdown
ip address 192.168.1.254 255.255.255.0
interface GigabitEthernet1/0/1
undo shutdown
ip address 172.16.0.254 255.255.255.0
interface GigabitEthernet1/0/3
undo shutdown
ip address 100.1.12.1 255.255.255.252
service-manage ping permit
interface Tunnel0
ip address 12.1.1.1 255.255.255.252
tunnel-protocol gre
keepalive
source GigabitEthernet1/0/3 //指定原接口
destination 100.1.12.6 //指定对端地址
ipsec policy ips1 //调用ipsec
interface Tunnel1
ip address 22.1.1.1 255.255.255.252
tunnel-protocol gre
keepalive
source GigabitEthernet1/0/3
destination 100.1.12.10
ipsec policy ips2
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/0
add interface GigabitEthernet1/0/1
add interface Tunnel0 //隧道接口要加入安全域,加入到非信任也可以
add interface Tunnel1
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/3
ip route-static 0.0.0.0 0.0.0.0 100.1.12.2
ip route-static 10.191.10.0 255.255.255.0 Tunnel0 //去往对端私网的路由指向隧道口
ip route-static 10.191.20.0 255.255.255.0 Tunnel1
security-policy
rule name t-un //防火墙繁琐之处,私网到私网的流量一定要设置正反向
source-zone trust
destination-zone untrust
source-address 192.168.1.0 mask 255.255.255.0
destination-address 10.191.10.0 mask 255.255.255.0
destination-address 10.191.20.0 mask 255.255.255.0
action permit
rule name un-t
source-zone untrust
destination-zone trust
source-address 10.191.10.0 mask 255.255.255.0
source-address 10.191.20.0 mask 255.255.255.0
destination-address 192.168.1.0 mask 255.255.255.0
action permit
rule name ipsce //如果隧道口放非信任区,就省去了两个命令,local-unt就都包含了
source-zone local
source-zone trust
source-zone untrust
destination-zone local
destination-zone trust
destination-zone untrust
action permit
rule name to-isp //放行nat的流量
source-zone trust
destination-zone untrust
source-address 192.168.1.0 mask 255.255.255.0
action permit
nat-policy
rule name no-ips //无论防火墙还是路由器,在nat中一定要先把隧道的流量禁止
source-zone trust
destination-zone untrust
source-address 192.168.1.0 mask 255.255.255.0
destination-address 10.191.10.0 mask 255.255.255.0
destination-address 10.191.20.0 mask 255.255.255.0
action no-nat
rule name to-isp
source-zone trust
destination-zone untrust
source-address 192.168.1.0 mask 255.255.255.0
action source-nat easy-ip
sysname FW2
acl number 3000
rule 5 permit ip source 10.191.10.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
ipsec proposal 1
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike peer fw1
pre-shared-key huawei@123
ike-proposal 1
remote-address 12.1.1.1
ipsec policy ips 1 isakmp
security acl 3000
ike-peer fw1
proposal 1
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.0.1 255.255.255.0
alias GE0/METH
interface GigabitEthernet1/0/0
undo shutdown
ip address 10.191.10.254 255.255.255.0
interface GigabitEthernet1/0/3
undo shutdown
ip address 100.1.12.6 255.255.255.252
service-manage ping permit
interface Tunnel0
ip address 12.1.1.2 255.255.255.252
tunnel-protocol gre
keepalive
source GigabitEthernet1/0/3
destination 100.1.12.1
ipsec policy ips
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/0
add interface Tunnel0
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/3
firewall zone dmz
set priority 50
ip route-static 0.0.0.0 0.0.0.0 100.1.12.5
ip route-static 192.168.1.0 255.255.255.0 Tunnel0
security-policy
rule name t-un
source-zone trust
destination-zone untrust
source-address 10.191.10.0 mask 255.255.255.0
destination-address 192.168.1.0 mask 255.255.255.0
action permit
rule name un-t
source-zone untrust
destination-zone trust
source-address 192.168.1.0 mask 255.255.255.0
destination-address 10.191.10.0 mask 255.255.255.0
action permit
rule name ipsce
source-zone local
source-zone trust
source-zone untrust
destination-zone local
destination-zone trust
destination-zone untrust
action permit
rule name to-isp
source-zone trust
destination-zone untrust
source-address 10.191.10.0 mask 255.255.255.0
action permit
nat-policy
rule name t-un
source-zone trust
destination-zone untrust
source-address 10.191.10.0 mask 255.255.255.0
destination-address 192.168.1.0 mask 255.255.255.0
action no-nat
rule name to-isp
source-zone trust
destination-zone untrust
source-address 10.191.10.0 mask 255.255.255.0
action source-nat easy-ip
sysname FW3
acl number 3000
rule 5 permit ip source 10.191.20.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
ipsec proposal 1
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike peer fw1
pre-shared-key huawei@123
ike-proposal 1
remote-address 22.1.1.1
ipsec policy ips 1 isakmp
security acl 3000
ike-peer fw1
proposal 1
interface GigabitEthernet1/0/0
undo shutdown
ip address 10.191.20.254 255.255.255.0
interface GigabitEthernet1/0/3
undo shutdown
ip address 100.1.12.10 255.255.255.252
service-manage ping permit
interface Tunnel0
ip address 22.1.1.2 255.255.255.252
tunnel-protocol gre
keepalive
source GigabitEthernet1/0/3
destination 100.1.12.1
ipsec policy ips
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/0
add interface Tunnel0
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/3
firewall zone dmz
set priority 50
ip route-static 0.0.0.0 0.0.0.0 100.1.12.9
ip route-static 192.168.1.0 255.255.255.0 Tunnel0
security-policy
rule name t-un
source-zone trust
destination-zone untrust
source-address 10.191.20.0 mask 255.255.255.0
destination-address 192.168.1.0 mask 255.255.255.0
action permit
rule name un-t
source-zone untrust
destination-zone trust
source-address 192.168.1.0 mask 255.255.255.0
destination-address 10.191.20.0 mask 255.255.255.0
action permit
rule name ipsce
source-zone local
source-zone trust
source-zone untrust
destination-zone local
destination-zone trust
destination-zone untrust
action permit
rule name to-isp
source-zone trust
destination-zone untrust
source-address 10.191.20.0 mask 255.255.255.0
action permit
nat-policy
rule name t-un
source-zone trust
destination-zone untrust
source-address 10.191.20.0 mask 255.255.255.0
destination-address 192.168.1.0 mask 255.255.255.0
action no-nat
rule name to-isp
source-zone trust
destination-zone untrust
source-address 10.191.20.0 mask 255.255.255.0
action source-nat easy-ip
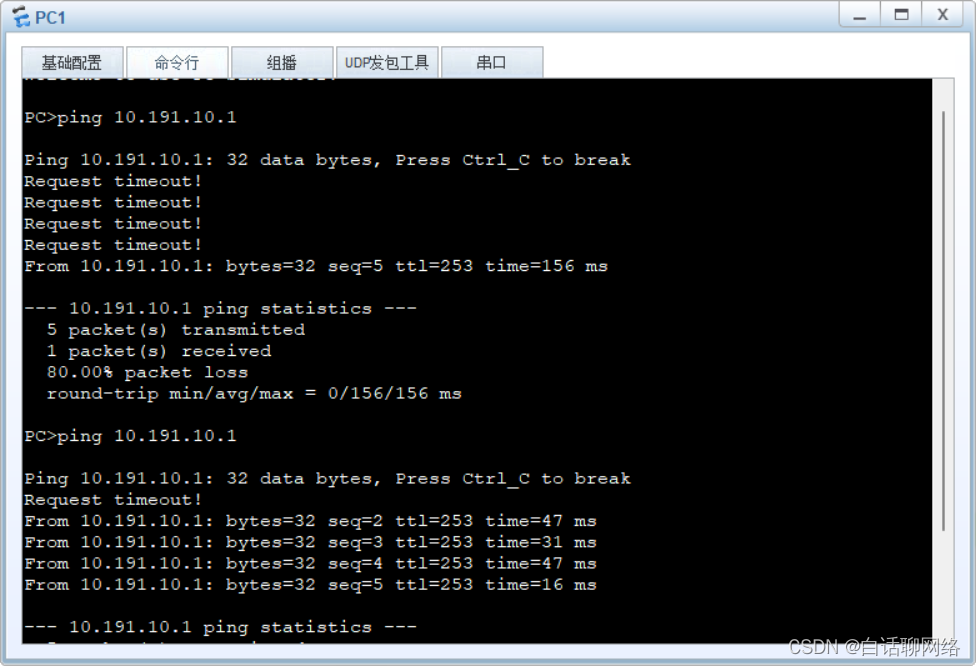
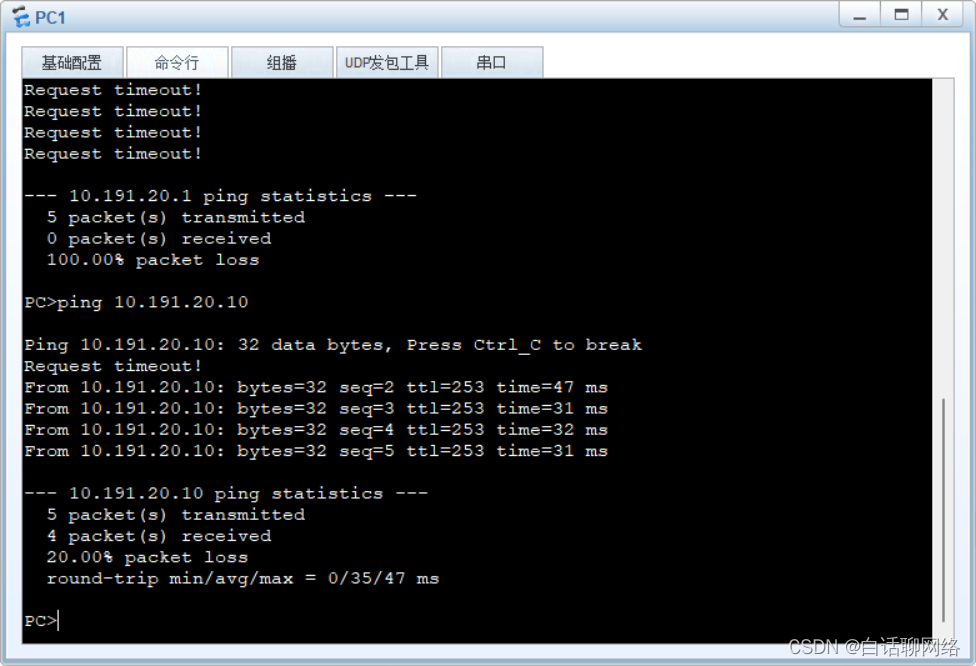
如果是点到点,总部配置删除一组即可
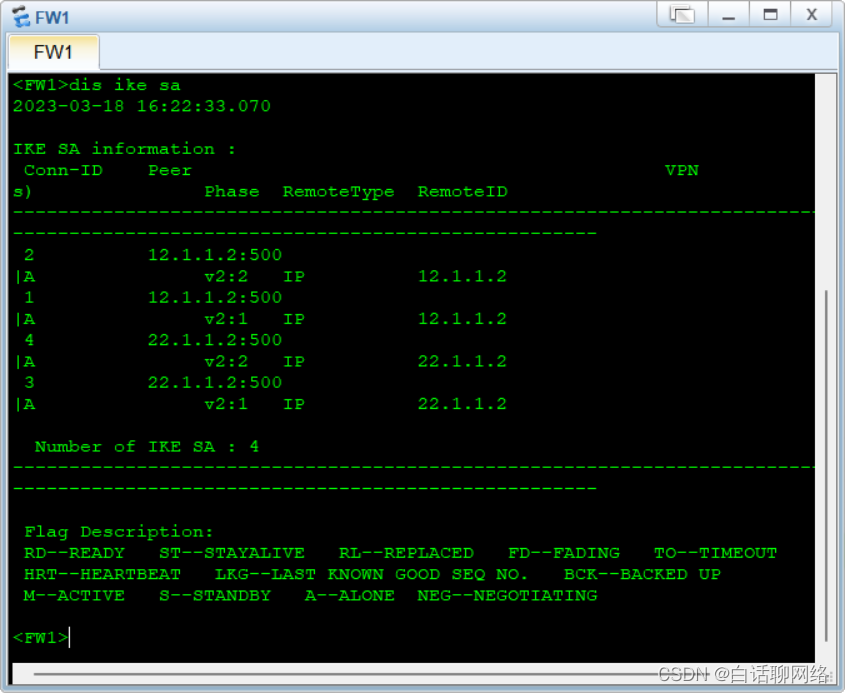
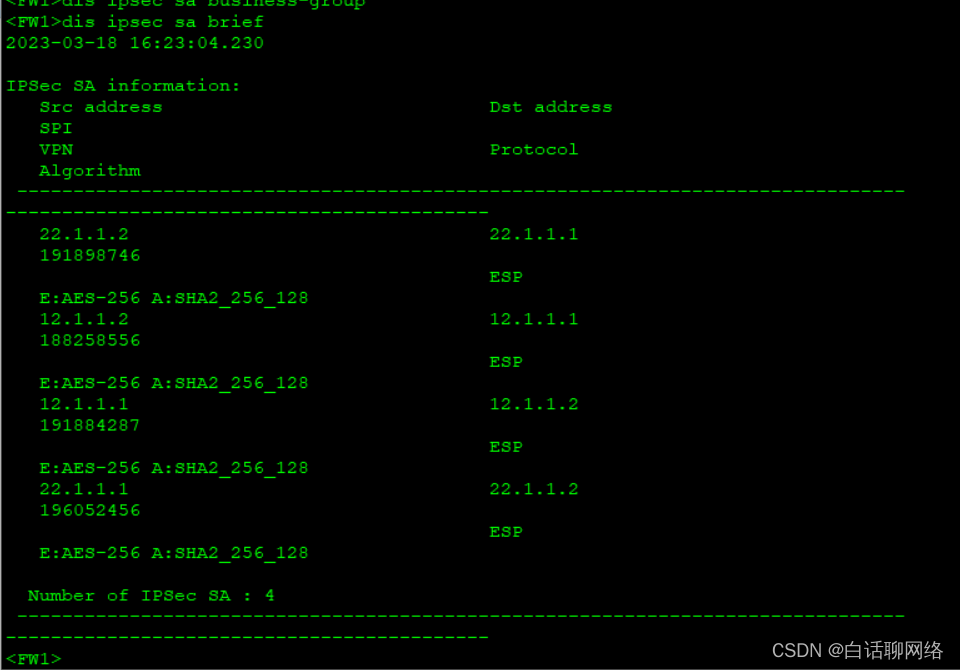
验证