配置GRE Over IPSec传输组播数据
如下图所示,R1与R3之间传输组播数据,并要求对数据进行IPSec加密;
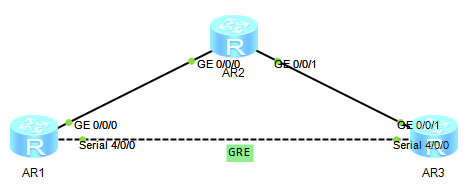
配置接口IP地址:
[r1]int g0/0/0
[r1-GigabitEthernet0/0/0]ip address 12.1.1.1 24
配置RIP协议:
[r1]rip 1
[r1-rip-1]version 2
[r1-rip-1]network 12.0.0.0
[r2]rip 1
[r2-rip-1]version 2
[r2-rip-1]network 12.0.0.0
[r2-rip-1]network 23.0.0.0
[r3]rip 1
[r3-rip-1]version 2
[r3-rip-1]network 23.0.0.0
配置GRE:
[r1]int Tunnel 0/0/0
[r1-Tunnel0/0/0]ip address 100.1.1.1 24
[r1-Tunnel0/0/0]tunnel-protocol gre
[r1-Tunnel0/0/0]source 12.1.1.1
[r1-Tunnel0/0/0]destination 23.1.1.2
[r3]int t0/0/0
[r3-Tunnel0/0/0]ip address 100.1.1.2 24
[r3-Tunnel0/0/0]tunnel-protocol gre
[r3-Tunnel0/0/0]source 23.1.1.2
[r3-Tunnel0/0/0]destination 12.1.1.1
配置IPSec:
[r1]acl number 3000
[r1-acl-adv-3000]rule 5 permit gre source 12.1.1.1 0 destination 23.1.1.2 0
[r1]ipsec proposal a1
[r1]ike local-name aaa
[r1]ike peer routerc v1
[r1-ike-peer-routerc]exchange-mode aggressive
[r1-ike-peer-routera]local-id-type name
[r1-ike-peer-routerc]pre-shared-key simple 12345
[r1-ike-peer-routerc]remote-name bbb
[r1-ike-peer-routerc]remote-address 23.1.1.2
[r1]ipsec policy xxx 1 isakmp
[r1-ipsec-policy-isakmp-xxx-1]security acl 3000
[r1-ipsec-policy-isakmp-xxx-1]ike-peer routerc
[r1-ipsec-policy-isakmp-xxx-1]proposal a1
[r1]int g0/0/0
[r1-GigabitEthernet0/0/0]ipsec policy xxx
[r3]acl 3000
[r3-acl-adv-3000]rule 5 permit gre source 23.1.1.2 0 destination 12.1.1.1 0
[r3]ipsec proposal b1
[r3]ike local-name bbb
[r3]ike peer routera v1
[r3-ike-peer-routera]exchange-mode aggressive
[r3-ike-peer-routera]local-id-type name
[r3-ike-peer-routera]pre-shared-key simple 12345
[r3-ike-peer-routera]remote-name aaa
[r3-ike-peer-routera]remote-address 12.1.1.1
[r3]ipsec policy yyy 1 isakmp
[r3-ipsec-policy-isakmp-yyy-1]security acl 3000
[r3-ipsec-policy-isakmp-yyy-1]ike-peer routera
[r3-ipsec-policy-isakmp-yyy-1]proposal b1
[r3]int g0/0/1
[r3-GigabitEthernet0/0/1]ipsec policy yyy
查看IKE第一阶段建立结果:
[r1]display ike sa
Conn-ID Peer VPN Flag(s) Phase
---------------------------------------------------------------
25 23.1.1.2 0 RD|ST 2
24 23.1.1.2 0 RD|ST 1
Flag Description:
RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT
HRT--HEARTBEAT LKG--LAST KNOWN GOOD SEQ NO. BCK--BACKED UP
查看IKE第二阶段建立结果:
[r1]display ipsec sa
===============================
Interface: GigabitEthernet0/0/0
Path MTU: 1500
===============================
-----------------------------
IPSec policy name: "xxx"
Sequence number : 1
Acl Group : 3000
Acl rule : 5
Mode : ISAKMP
-----------------------------
Connection ID : 25
Encapsulation mode: Tunnel
Tunnel local : 12.1.1.1
Tunnel remote : 23.1.1.2
Flow source : 12.1.1.1/255.255.255.255 47/0
Flow destination : 23.1.1.2/255.255.255.255 47/0
Qos pre-classify : Disable
[Outbound ESP SAs]
SPI: 1838552178 (0x6d961472)
Proposal: ESP-ENCRYPT-DES-64 ESP-AUTH-MD5
SA remaining key duration (bytes/sec): 1887326208/3588
Max sent sequence-number: 4
UDP encapsulation used for NAT traversal: N
[Inbound ESP SAs]
SPI: 2881932501 (0xabc6ccd5)
Proposal: ESP-ENCRYPT-DES-64 ESP-AUTH-MD5
SA remaining key duration (bytes/sec): 1887436286/3588
Max received sequence-number: 5
Anti-replay window size: 32
UDP encapsulation used for NAT traversal: N