前言
RSA加解密知识自行百度了解决一下
1、取得公钥与私钥方法
下载后将其发布成网站进入:http://127.0.0.1:3000/demo/index.html (各自服务器站口不一样自行)
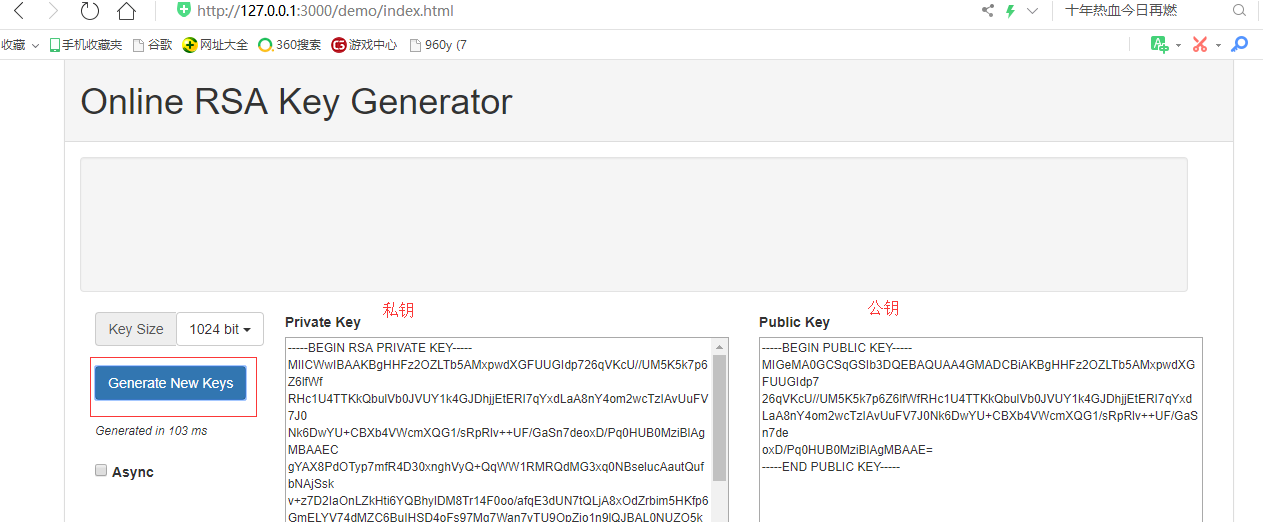
这样就得到一公钥和私钥
另一种生成公钥与私钥的方法如下:引用 https://blog.csdn.net/qq_39081974/article/details/81059022
======================================Begin======================================
1. OpenSSL官网
官方下载地址: https://www.openssl.org/source/
2. Windows安装方法
OpenSSL官网没有提供windows版本的安装包,可以选择其他开源平台提供的工具。例如 http://slproweb.com/products/Win32OpenSSL.html
以该工具为例,安装步骤和使用方法如下:
2.1 选择32位或者64位合适的版本下载,例如Win64OpenSSL_Light-1_0_2h.exe:
2.2 设置环境变量,例如工具安装在C:\OpenSSL-Win64,则将C:\OpenSSL-Win64\bin;复制到Path中
2.3 打开命令行程序cmd(以管理员身份运行),运行以下命令:
这里路径就是保存地址
利用 openssl 生成公钥私钥
生成公钥: openssl genrsa -out rsa_private_key.pem 1024
生成私钥: openssl rsa -in rsa_private_key.pem -pubout -out rsa_public_key.pem
======================================End=======================================
2、实践(引用:https://www.jb51.net/article/117127.htm)
参数传递的+号处理,在传输时会把+变成空格,不处理后端就报错了。
1、前端代码
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
|
<!DOCTYPE html>
<html>
<head>
<meta name=
"viewport"
content=
"width=device-width"
/>
<title>Login</title>
<script src=
"jquery-1.10.2.min.js"
></script>
<script src=
"jsencrypt.min.js"
></script>
<script type=
"text/javascript"
>
$(
function
() {
var
encrypt =
new
JSEncrypt();
encrypt.setPublicKey($(
"#tra"
).val());
var
data = encrypt.encrypt(
"123456789"
);
alert(data);
$(
"#btn"
).click(
function
() {
$.ajax({
url:
'@Url.Action("Login")'
,
data:
"pwd="
+ encodeURI(data).replace(/\+/g,
'%2B'
),
//+号的处理:因为数据在网络上传输时,非字母数字字符都将被替换成百分号(%)后跟两位十六进制数,而base64编码在传输到后端的时候,+会变成空格,因此先替换掉。后端再替换回来
type:
'post'
,
success:
function
(msg) {
alert(msg);
}
});
});
});
</script>
</head>
<body>
<div>
<input type=
"button"
id=
"btn"
value=
"点我"
/>
<textarea id=
"tra"
rows=
"15"
cols=
"65"
>
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCa4KHNwDX44gGmmIAtRu4gjVYt
GWZzcm4t+1wjUD4dn7fMLPvuK7ai4UrfDeEJE1RPwudJw+lJ6crql8wSIg7/DbTl
G3ihsCT6dT9H5B9OoeR7K9VWUesaW/iyVL6HXiYOANabW14pvJATDmdq91Tfgp6P
SQyvdfiRdV4r07crpQIDAQAB
</textarea>
<hr/>
注意+号的处理
</div>
</body>
</html>
|
2、后端代码
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
|
public
class
IndexController : Controller
{
public
ActionResult Login()
{
return
View();
}
[HttpPost]
public
ActionResult Login(
string
pwd)
{
//密钥格式要生成pkcs#1格式的 而不是pkcs#8格式的
string
privateKey =
@"MIICWwIBAAKBgQCa4KHNwDX44gGmmIAtRu4gjVYtGWZzcm4t+1wjUD4dn7fMLPvuK7ai4UrfDeEJE1RPwudJw+lJ6crql8wSIg7/DbTlG3ihsCT6dT9H5B9OoeR7K9VW
UesaW/iyVL6HXiYOANabW14pvJATDmdq91Tfgp6PSQyvdfiRdV4r07crpQIDAQAB
AoGABb+3gdb+qeG0b1CogVsT/7//UOaTzPk/FGneKQQTf4SsN+H7lVhTYTG9ARFC
JyoWg8IXqmn2ljhywHPTWWD2RCZIn2sYT1sVkGb70EgHGQLBraFHElmw+DsVJ+nD
fBCfMrJ1TYXlwigjRkaueaoGgG8LdR8XD+Xs5LersPLjZgECQQCguSB7C4wF6oSw
EDmwNF8ffT5cQc1U2OIq6NBG8rafrjb7LsjhOd03pmY7i4LbW3Vvq4AhQpJEdF1C
vd+Sk/BBAkEA9rBhqnyumV09zFEomSX3zZu+bdhTzM4bJDfEa95swp1gANCVvF/t
DCnlBf51EhCWdeGSpARPUkQnXrYfFUDiZQJAAZEshuaa6+fYeVr/JP+tucHf3Mhr
dxtSQTbZ6QcuzqnFMXfIT6HfzU4bCxOWKAthPsB+VFSw1mgIDMGLL4OvwQJAJlVy
V9PYLezXVZCnBmVoBINXLCqZmxHMFey0kS6XKAbcjEPdgNBHPcSk2jGYb540Q00y
RFqHGPmORKF4Yw0aIQJAd5JRtD3z2MgP/vPoKHJNHqY8bboVcmwqVAm6xCZoTCZz
jNV1Cnsdf4wBV3LCDzYBy+xR4qYNUy5CFXN+8WzzAA=="
;
try
{
RSACryptoServiceProvider rsaCryptoServiceProvider = CreateRsaProviderFromPrivateKey(privateKey);
//把+号,再替换回来
byte
[] res = rsaCryptoServiceProvider.Decrypt(Convert.FromBase64String(pwd.Replace(
"%2B"
,
"+"
)),
false
);
return
Content(Encoding.UTF8.GetString(res));
}
catch
(Exception exception)
{
}
return
Content(
""
);
}
private
RSACryptoServiceProvider CreateRsaProviderFromPrivateKey(
string
privateKey)
{
var privateKeyBits = System.Convert.FromBase64String(privateKey);
var RSA =
new
RSACryptoServiceProvider();
var RSAparams =
new
RSAParameters();
using
(BinaryReader binr =
new
BinaryReader(
new
MemoryStream(privateKeyBits)))
{
byte
bt = 0;
ushort
twobytes = 0;
twobytes = binr.ReadUInt16();
if
(twobytes == 0x8130)
binr.ReadByte();
else
if
(twobytes == 0x8230)
binr.ReadInt16();
else
throw
new
Exception(
"Unexpected value read binr.ReadUInt16()"
);
twobytes = binr.ReadUInt16();
if
(twobytes != 0x0102)
throw
new
Exception(
"Unexpected version"
);
bt = binr.ReadByte();
if
(bt != 0x00)
throw
new
Exception(
"Unexpected value read binr.ReadByte()"
);
RSAparams.Modulus = binr.ReadBytes(GetIntegerSize(binr));
RSAparams.Exponent = binr.ReadBytes(GetIntegerSize(binr));
RSAparams.D = binr.ReadBytes(GetIntegerSize(binr));
RSAparams.P = binr.ReadBytes(GetIntegerSize(binr));
RSAparams.Q = binr.ReadBytes(GetIntegerSize(binr));
RSAparams.DP = binr.ReadBytes(GetIntegerSize(binr));
RSAparams.DQ = binr.ReadBytes(GetIntegerSize(binr));
RSAparams.InverseQ = binr.ReadBytes(GetIntegerSize(binr));
}
RSA.ImportParameters(RSAparams);
return
RSA;
}
private
int
GetIntegerSize(BinaryReader binr)
{
byte
bt = 0;
byte
lowbyte = 0x00;
byte
highbyte = 0x00;
int
count = 0;
bt = binr.ReadByte();
if
(bt != 0x02)
return
0;
bt = binr.ReadByte();
if
(bt == 0x81)
count = binr.ReadByte();
else
if
(bt == 0x82)
{
highbyte = binr.ReadByte();
lowbyte = binr.ReadByte();
byte
[] modint = { lowbyte, highbyte, 0x00, 0x00 };
count = BitConverter.ToInt32(modint, 0);
}
else
{
count = bt;
}
while
(binr.ReadByte() == 0x00)
{
count -= 1;
}
binr.BaseStream.Seek(-1, SeekOrigin.Current);
return
count;
}
}
|
测试源码在下面GitHub上有(可以给我留言)
https://github.com/xiaoruilin/EncryptionDecrypt