刚开始接触逆向的题目师傅就给啦一道题目
链接:https://pan.baidu.com/s/13cR9WUr1rydFjjbM2meyug 密码:jg3j 题目和wp都在里面
下面开始记录
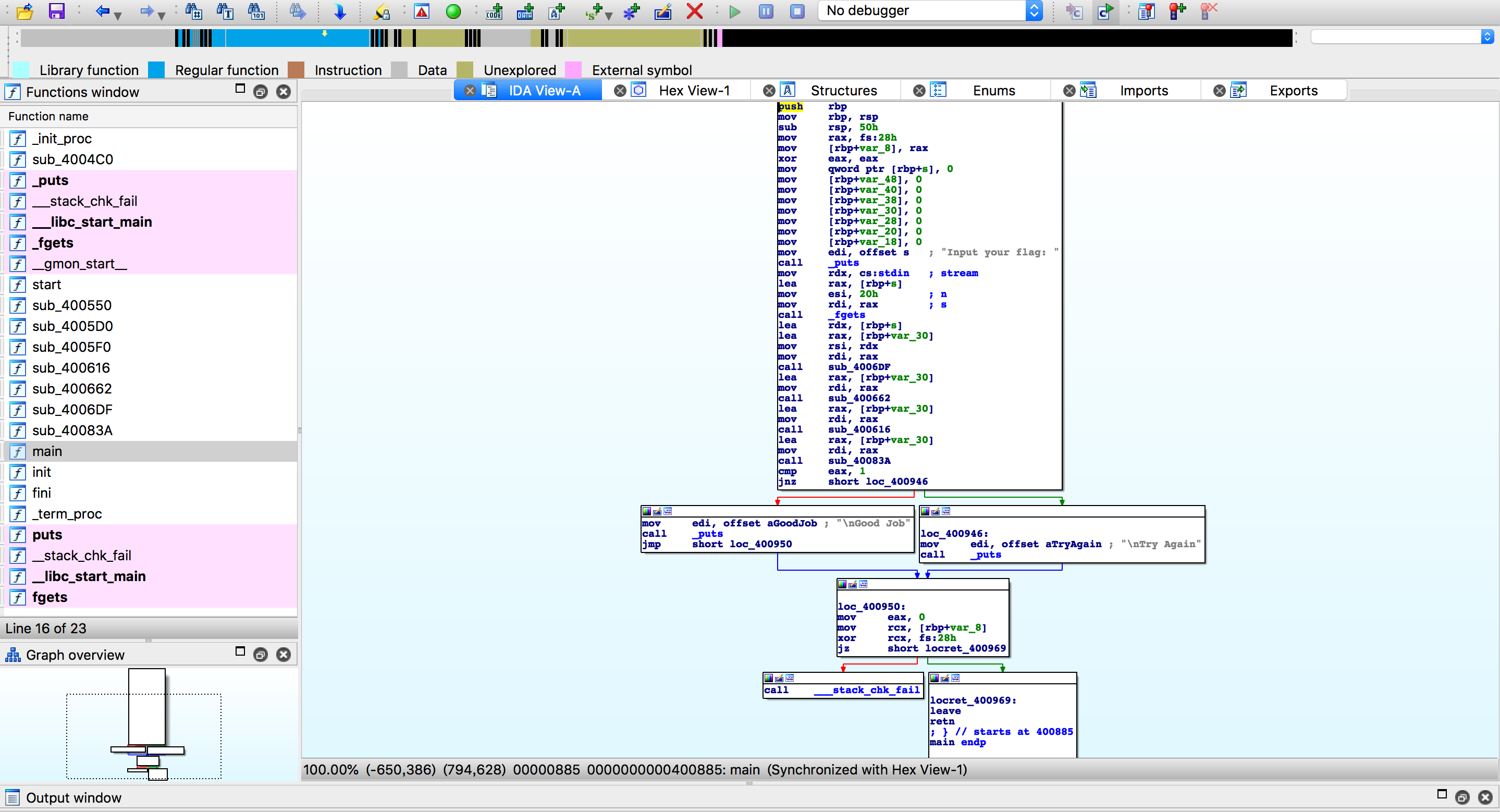
首先ida大法好~一个美丽姑娘的头像
接着f5大法好~
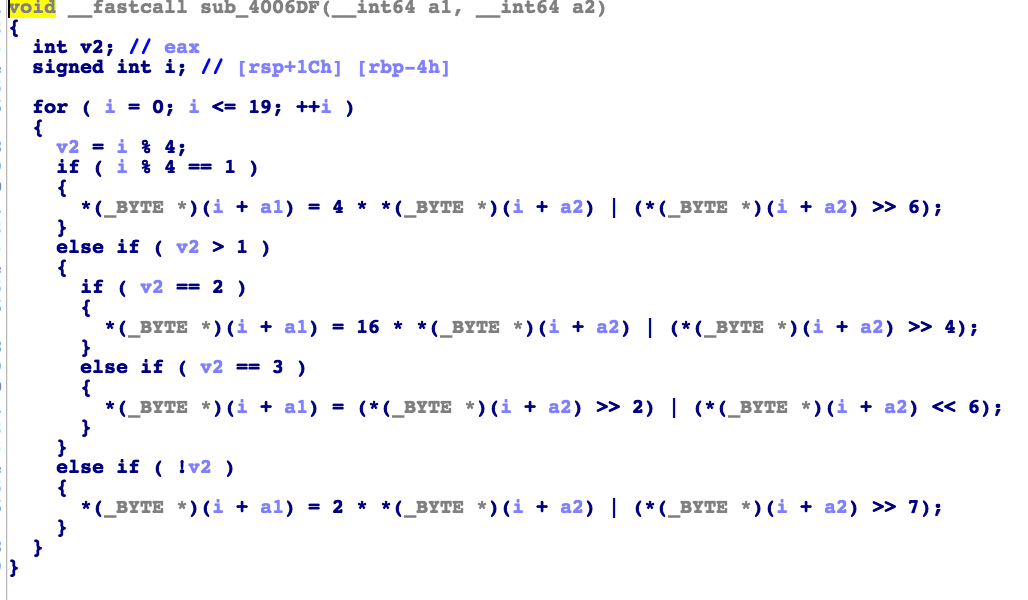
题目本身比较简单,就先看一下第一个sub_4006DF函数

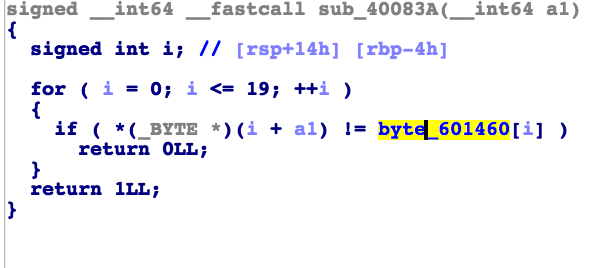
这里的逻辑也是很清楚并没有什么拐弯的就是当i分别满足其中的条件后对v8这个数组进行赋值,之前第一个不懂的就是(i+a1)之后知道了表示的是数组,咱们还是再看看最后一个的判断条件是啥,这是最后一个if语句中的函数判断语句
也就是说将byte_601460中的数组与v8分别对比贴出数组
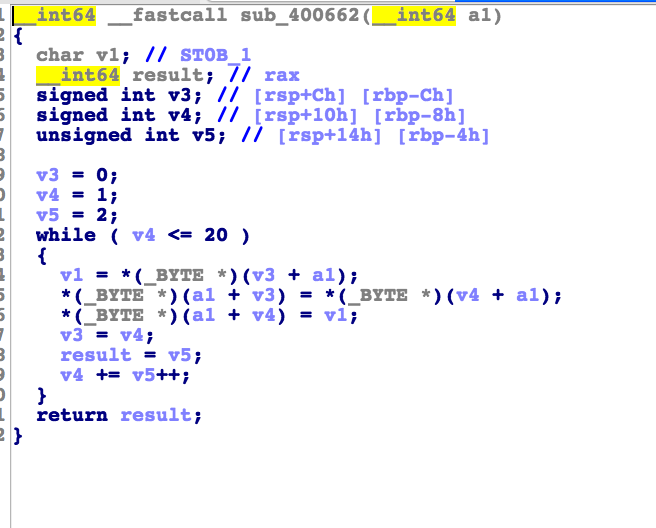
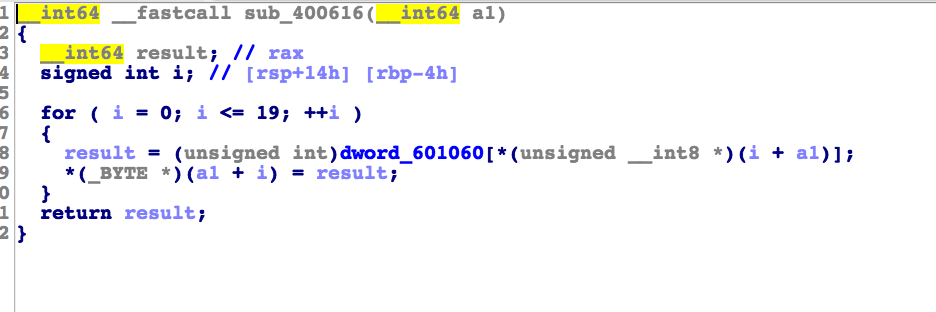
也就是只需要在三个函数(剩下的两个函数sub_400662和sub_400616)变化后s 的值等于这个数组里的数值就可以了,接下来贴
出其他函数的图
这些的逻辑都比较简单就直接贴出逆向的代码了
# A6 4E 05 A2 B6 08 A2 CE 8C EE 20 C2 98 A0 D0 CD
# 23 A6 6A 82
# -*- coding: utf8 -*-
dict=[0x11,0xBF,0xBA,0x0F,0xD5,0xCC,0xBC,0x1E,0x19,0x01,0x87,0x1B,0x96,0xC3,0x86,0x1A,0x7E,0x6B,0x5A,0x8D,0xFB,0xC2,0x8B,0xB3,0xB1,0xDD,0xEF,0x0A,0x4B,0xF8,0x55,0x26,0x76,0xAB,0xC1,0x64,0x17,0xC9,0xAF,0x61,0x67,0x4A,0xCA,0x12,0x24,0xE1,0xAE,0x50,0x3A,0x70,0x37,0xED,0xE0,0x77,0xB7,0x2E,0xA1,0x2D,0x32,0x7B,0x89,0xCF,0xF0,0x94,0x21,0x65,0x0B,0x3F,0x7D,0x29,0x3B,0x05,0x51,0xE7,0x81,0x6E,0x33,0xC6,0xD7,0xAC,0x3C,0x9A,0x22,0xDC,0x7A,0x08,0x6A,0x97,0xF1,0x5F,0x8E,0x62,0x6F,0x13,0x8A,0x82,0x8C,0x2A,0x49,0x39,0x18,0x68,0xD0,0x83,0xB4,0x42,0x36,0x71,0x0C,0x57,0x10,0xF3,0x28,0xD4,0x34,0x0E,0xE4,0xFF,0x06,0xAD,0x5C,0xFC,0xDB,0xDE,0xDA,0x9F,0xEA,0x35,0x5E,0x78,0x52,0xD9,0x4F,0x6D,0xBB,0xA8,0xB0,0x15,0x43,0x90,0x25,0xA6,0x54,0xFE,0x0D,0xEB,0xA9,0xFD,0xE9,0x5D,0x16,0xCB,0x2F,0x4E,0xBD,0xC5,0x09,0x46,0xF7,0xC0,0x1F,0x59,0xD3,0x02,0x23,0x9D,0x60,0x04,0x84,0xF6,0xA4,0x1D,0x31,0x4C,0xC8,0x9B,0xC7,0xDF,0x66,0x2C,0xEC,0x79,0x73,0x30,0x69,0x63,0x95,0xD6,0xBE,0x44,0xE8,0xA5,0xF2,0x99,0xD8,0x38,0xA0,0xE3,0x8F,0xD2,0x53,0x3D,0x56,0x92,0x72,0xFA,0xB8,0xA7,0xCD,0xEE,0x93,0x85,0x6C,0x7F,0xAA,0xB2,0x47,0xCE,0x80,0x20,0x1C,0x7C,0x07,0xE2,0xB9,0x91,0x45,0x74,0x98,0xF5,0x3E,0x03,0xC4,0x00,0x41,0x00,0x2B,0x48,0x27,0xE6,0x5B,0xF4,0x9C,0x88,0x75,0xA2,0xB6,0x14,0xD1,0xE5,0x4D,0x40,0xF9,0x9E,0x58,0xA3]
base=[0xA6,0x4E,0x05,0xA2,0xB6,0x08,0xA2,0xCE,0x8C,0xEE,0x20,0xC2,0x98,0xA0,0xD0,0xCD,0x23,0xA6,0x6A,0x82]
v3=[0,1,3,6,10]
v4=[1,3,6,10,15]
def main():
temp=sub_400616()
temp=sub_400662(temp)
print temp
flag=[]
for i in range(len(temp)):
for j in range(255):
if sub_4006DF_burp(j,i)==temp[i]:
flag.append(chr(j))
break
print "".join(flag)
def sub_400616():
result=[]
for i in range(len(base)):
result.append(dict.index(base[i]))
return result
def sub_400662(result):
for i in range(len(v4)-1,-1,-1):
temp=result[v3[i]]
result[v3[i]]=result[v4[i]]
result[v4[i]]=temp
return result
def sub_4006DF_burp(ch,pos):
if pos%4==0:
result=2*ch | (ch>>7)
if pos%4==1:
result=4*ch | (ch>>6)
if pos%4==2:
result=16*ch | (ch>>4)
if pos%4==3:
result=ch>>2 | (ch<<6)
return result%256
def sub_4006DF(input):
result=[]
for i in range(len(input)):
if i%4==0:
result.append(2*input[i] | (input[i]>>7))
if i%4==1:
result.append(4*input[i] | (input[i]>>6))
if i%4==2:
result.append(16*input[i] | (input[i]>>4))
if i%4==3:
result.append(input[i] | (input[i]<<6))
return result
if __name__=="__main__":
main()
坚持就是胜利✌️(感谢师傅)