The URL is as follows, use base64 decoding to obtain
aHR0cHM6Ly9pLmZrdy5jb20vaW5kZXguanNw
The most basic step to reverse slider login is to first determine the two requests, the request to obtain the verification code and the request to verify the verification code. Let’s first look at the request to obtain the verification code.
After logging in through repeated errors, trigger the sliding verification code, refresh the verification code, and get the get request, as follows:
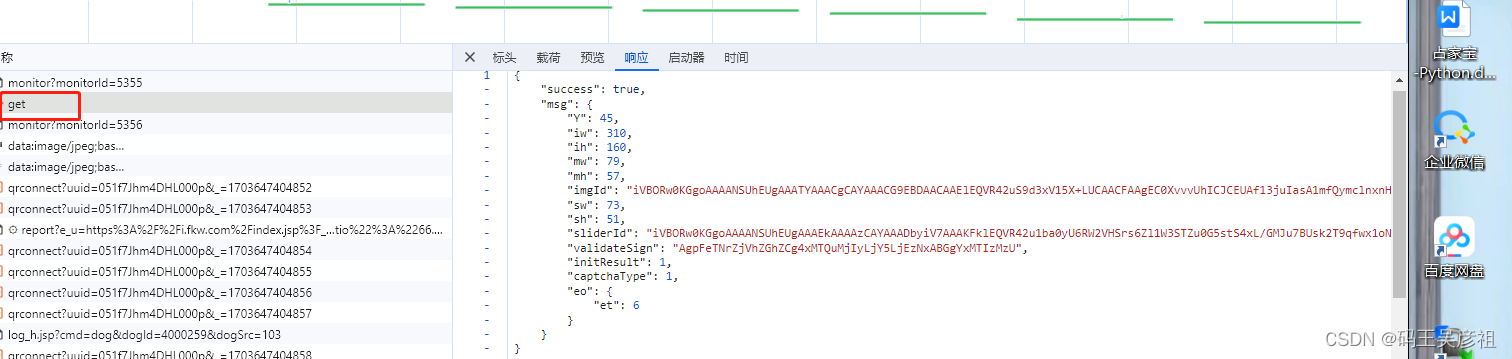
Then analyze the request parameters, which are composed of the following parts
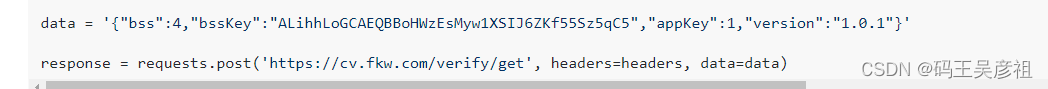
and follow the stack to view the source of the parameters. From the following picture and stack, we know that the parameters are all fixed. parameters, so just fix the parameter request.
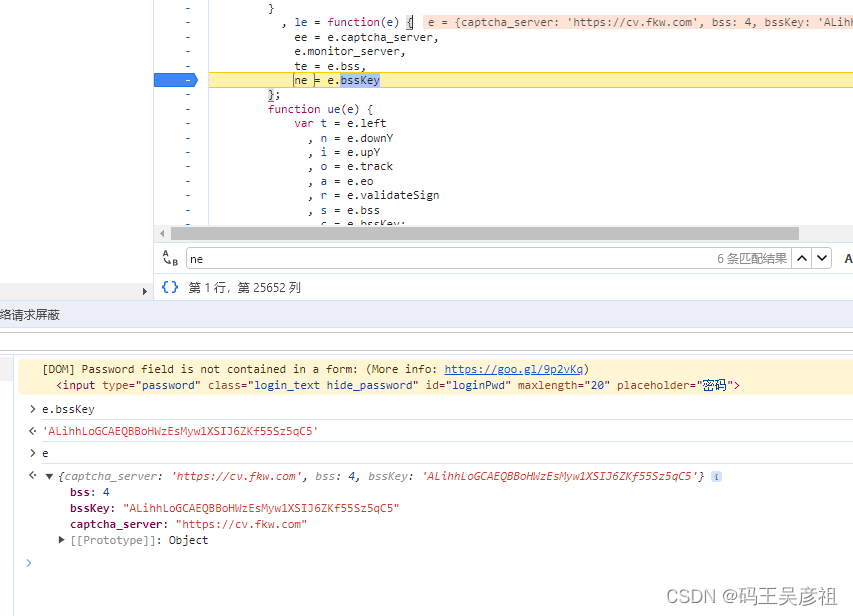
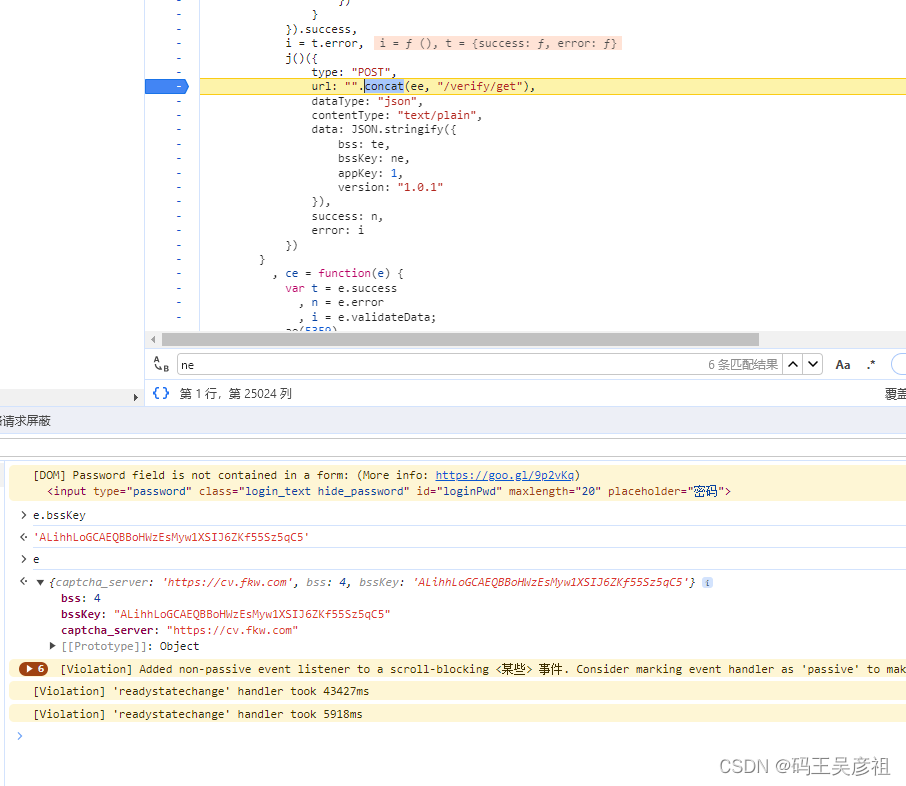
Next, look at the request to verify the verification code
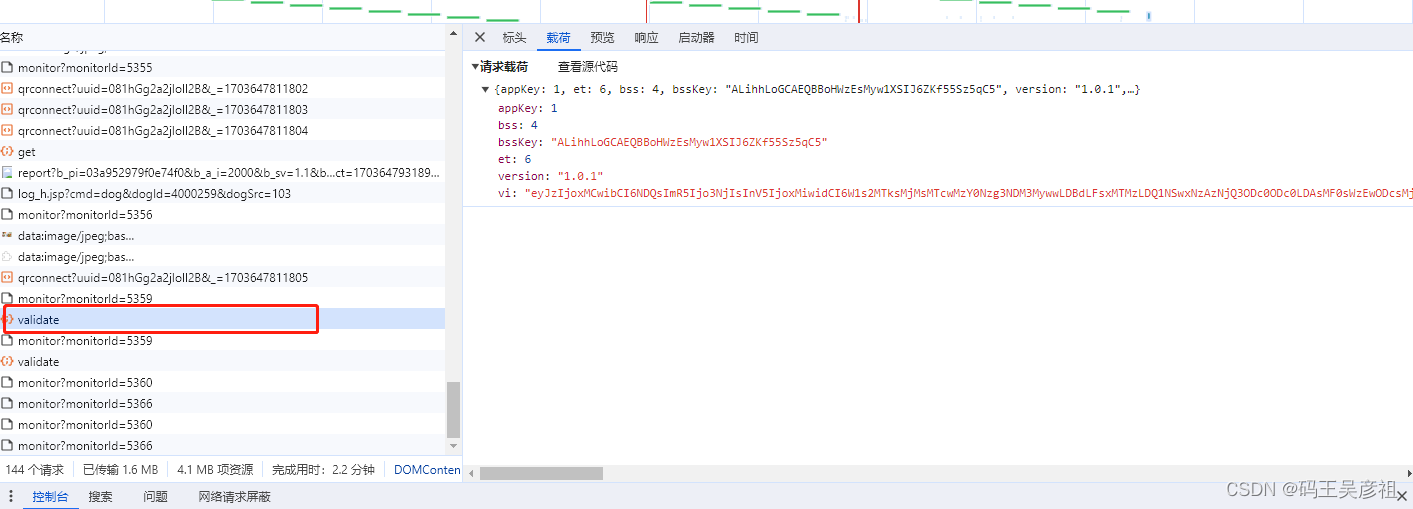
. Through observation, we found that there is actually an extra vi parameter. We checked the origin of the vi parameter with the stack and
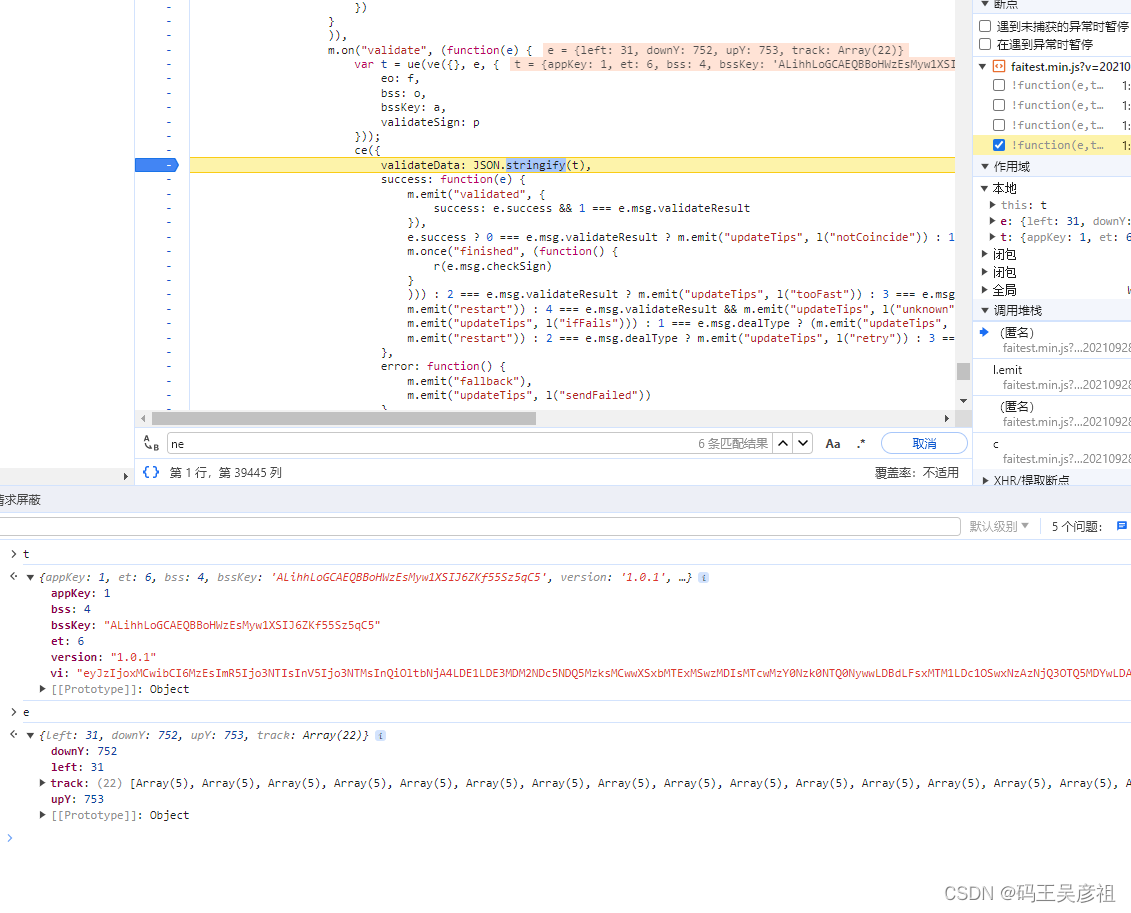
found that vi is in the parameter of t. And t is generated by encryption, where e is the key parameter that needs to be transmitted, and the encryption method is ue, ve, where e is the y value of pressing the slider and raising the y value of the slider, the offset x value, and the slider trajectory 4 It consists of three parts. All the values here can be generated by the algorithm you write. How to write it depends on whether the website verification is strict. You can refer to my previous article here, which contains a simple method for generating slider trajectories . Slider login reverse
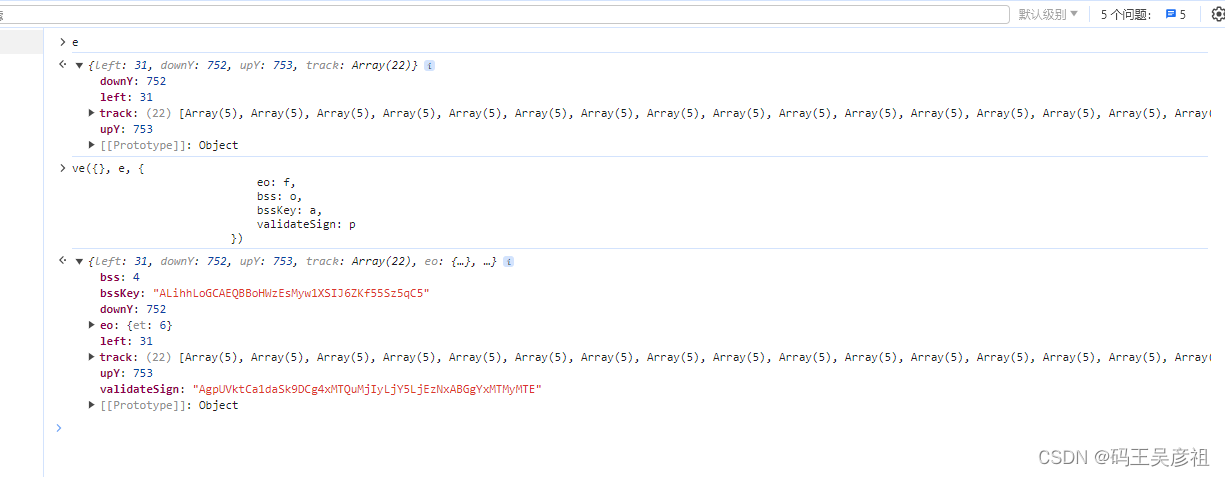
Here, we first check the difference between e and encrypting e with ve. We find that we only add the dictionary of passed parameters, so the ve encryption does not need to be deducted. Let's take a look at ue encryption.
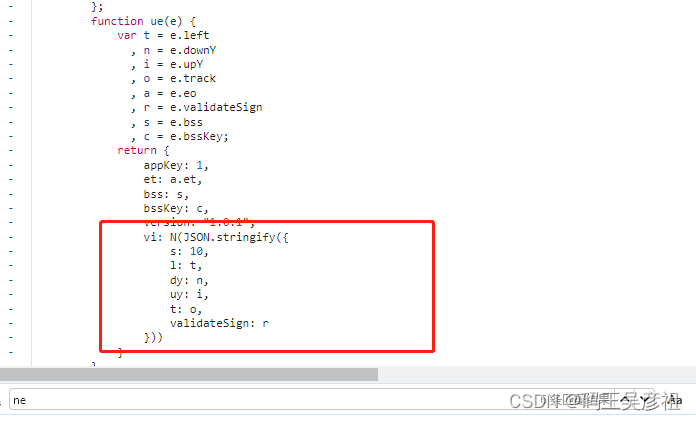
Here, the encryption of ue is directly internal. It shows that the generation method of vi is the N encryption function, and the parameters passed in N are also generated before and have not changed, so here we only need to deduct the N function.
function N(e) {
for (var t, n, i = String(e), o = 0, a = K, r = ""; i.charAt(0 | o) || (a = "=",
o % 1); r += a.charAt(63 & t >> 8 - o % 1 * 8)) {
if ((n = i.charCodeAt(o += .75)) > 255)
throw new L("'btoa' failed: The string to be encoded contains characters outside of the Latin1 range.");
t = t << 8 | n
}
return r
}
We directly deduct N here and find that there are no other encryption function dependencies. This encryption is very simple. Finally, it is assembled into python code. I will not verify the correct drag value here.

Get the correct response to the drag error