Disclaimer: This article is only for learning and communication, and it is prohibited to be used for illegal purposes, commercial activities, etc. Otherwise, do so at your own risk. If there is any infringement, please inform and delete, thank you! This tutorial is not written specifically for a certain website, purely technical research
Table of contents
case analysis
Target case: aHR0cDovL2JhY2t0ZXN0LjEwanFrYS5jb20uY24vYmFja3Rlc3QvYXBwLmh0bWwjL215c3RyYXRlZ3k=
1. Corresponding parameters and interfaces
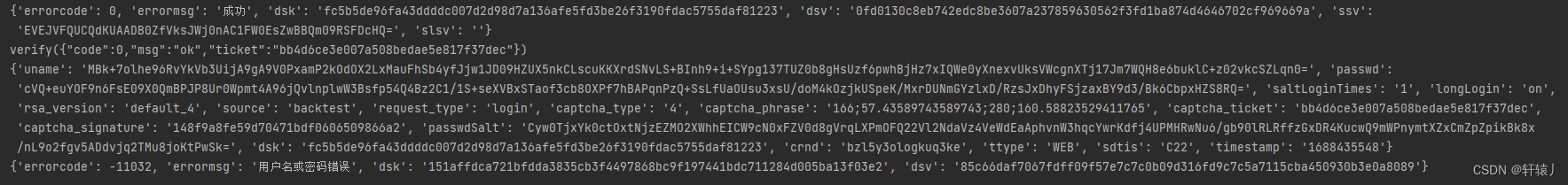
Slider interface
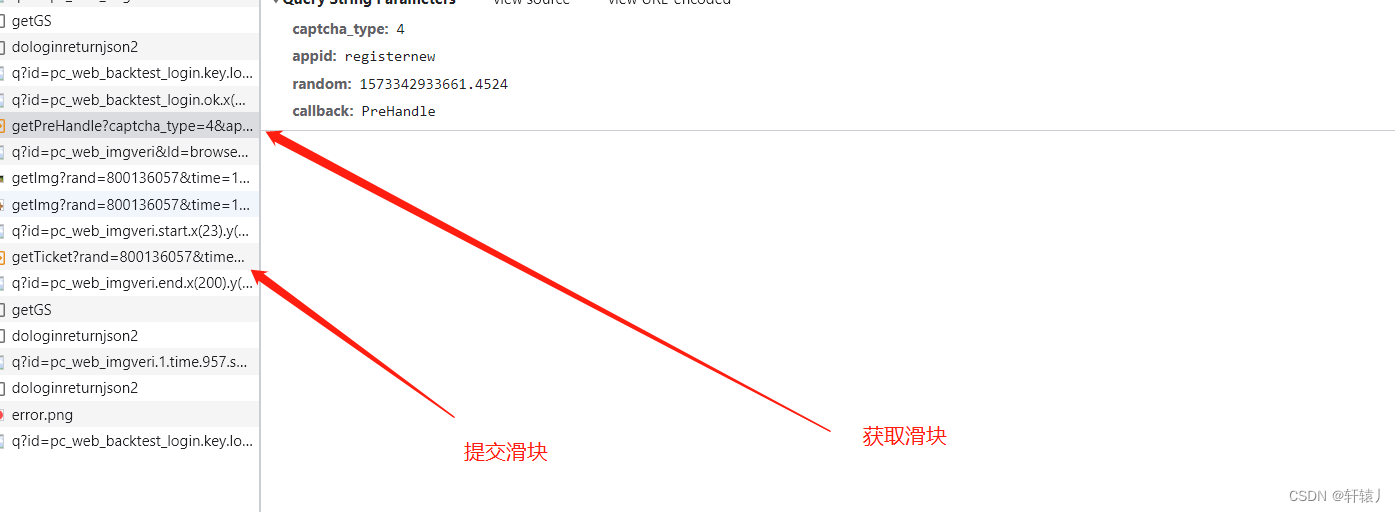
The interface after the slider is processed
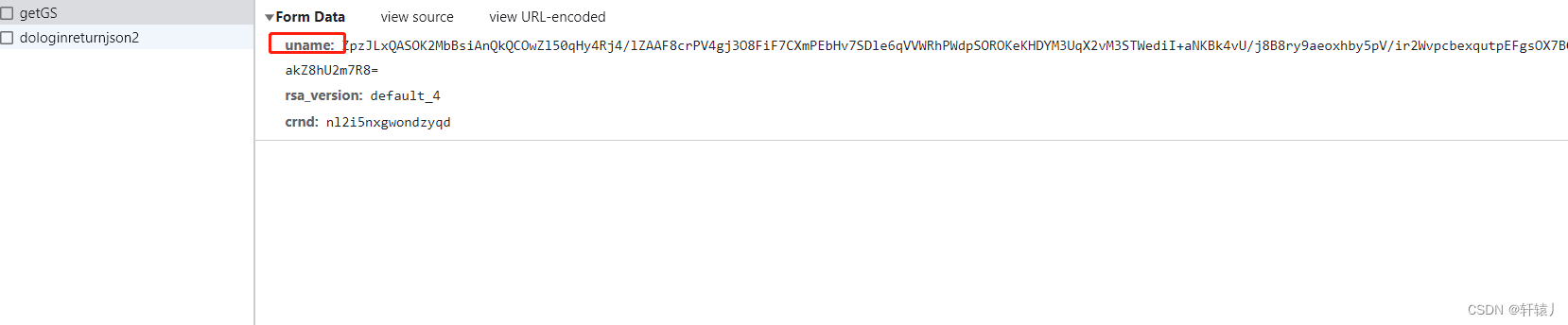
Add the interface submitted by the slider
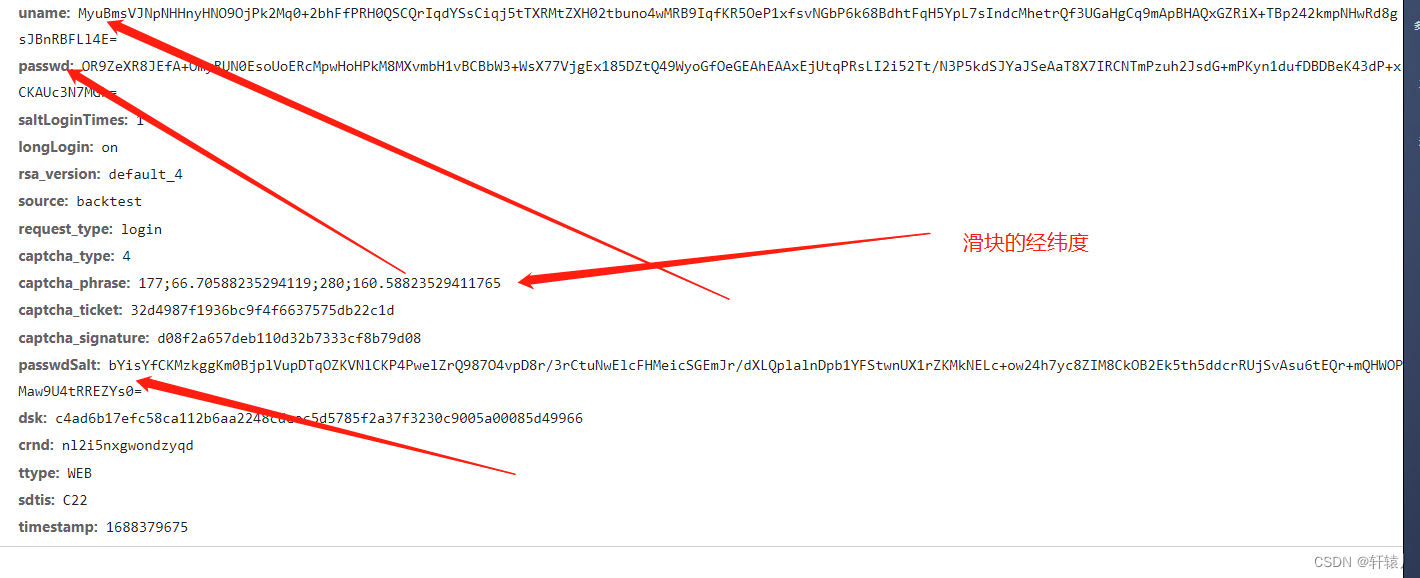
Parameter sharing
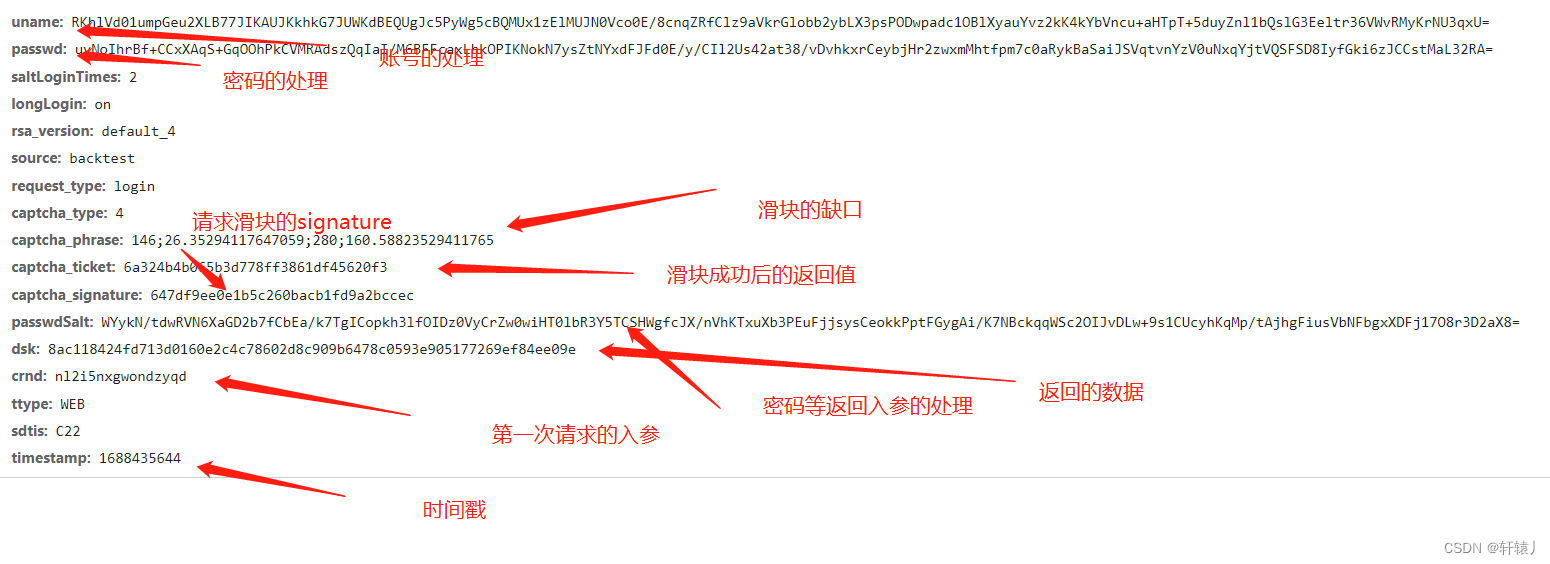
First of all, let's check the interface with only one parameter. Search Dafa according to the old rules.
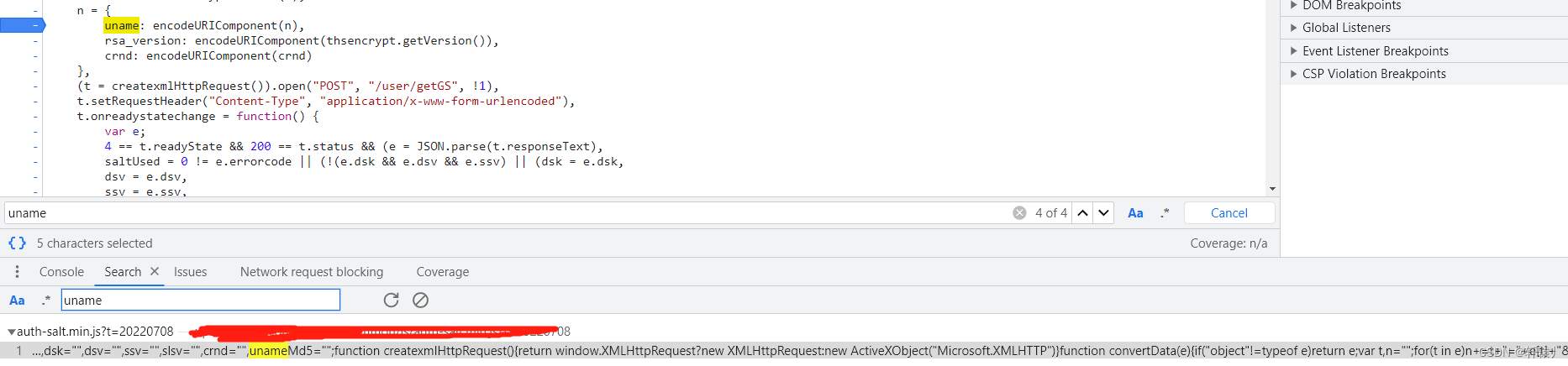
After clicking Login, we find that it has been generated here. Then we can see that thsencrypt.encode encrypts the things we input. You can
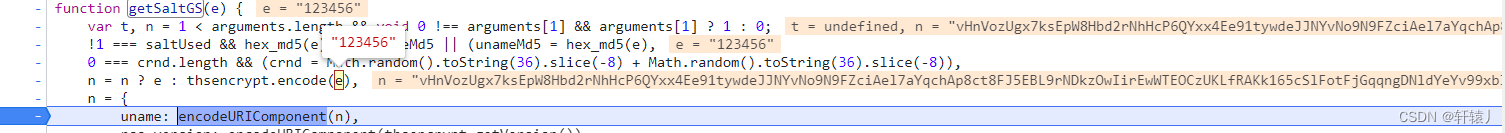
see it here. It turns out that he has encrypted the account with rsa. The key of rsa is that b and the length is c. After that, hex2b64 is performed. I directly deducted hex2b64. You can see this thing and restore it yourself. You can see that it is already right

here Now, the first parameter has been settled here, so let’s continue to look down. Then let’s look
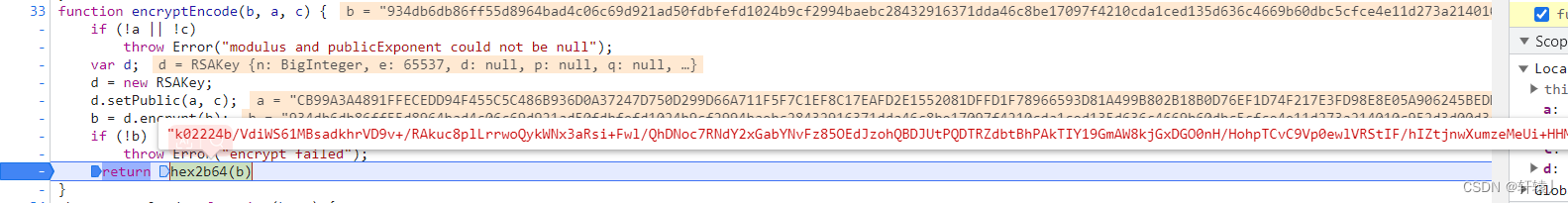
at the second interface, or search for the breakpoint of Dafa.

Here you can see that the password is the md5 of the password we entered and then After performing rsa, perform hex2b64.
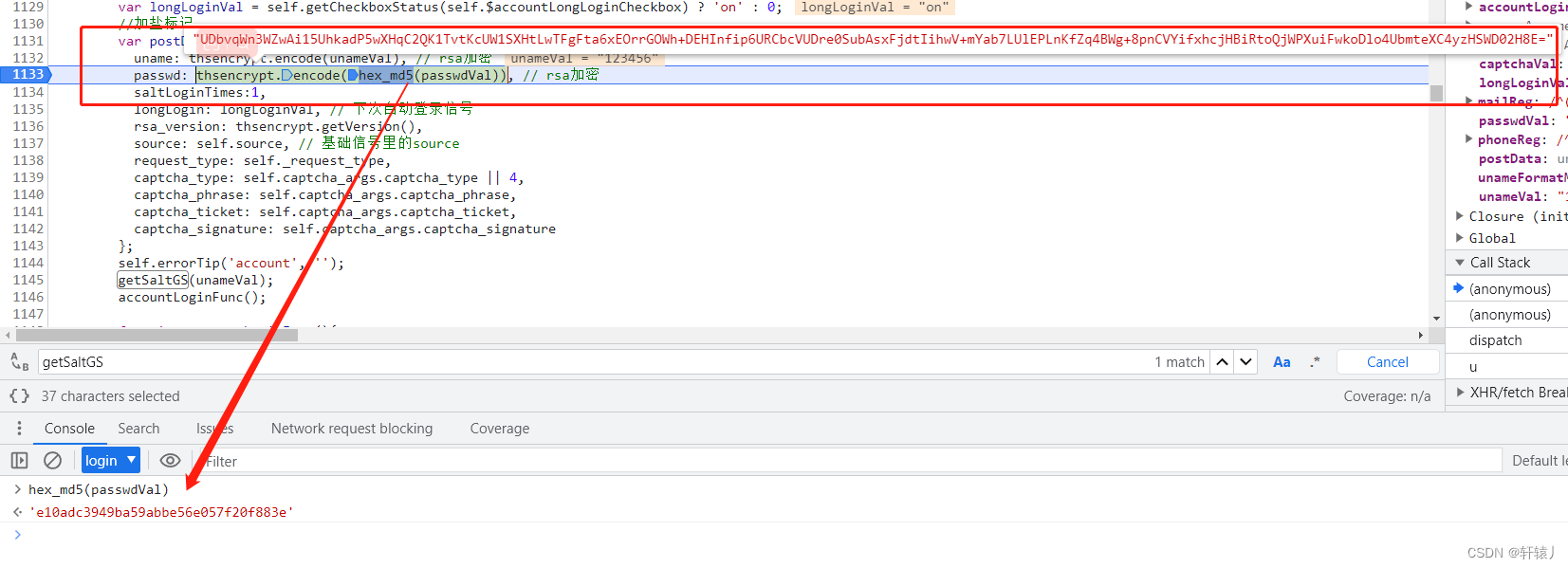
Here you can see that it encrypts the password and account.
We can see that by performing sha256 on the previously returned data and input parameters, you can restore it through python.
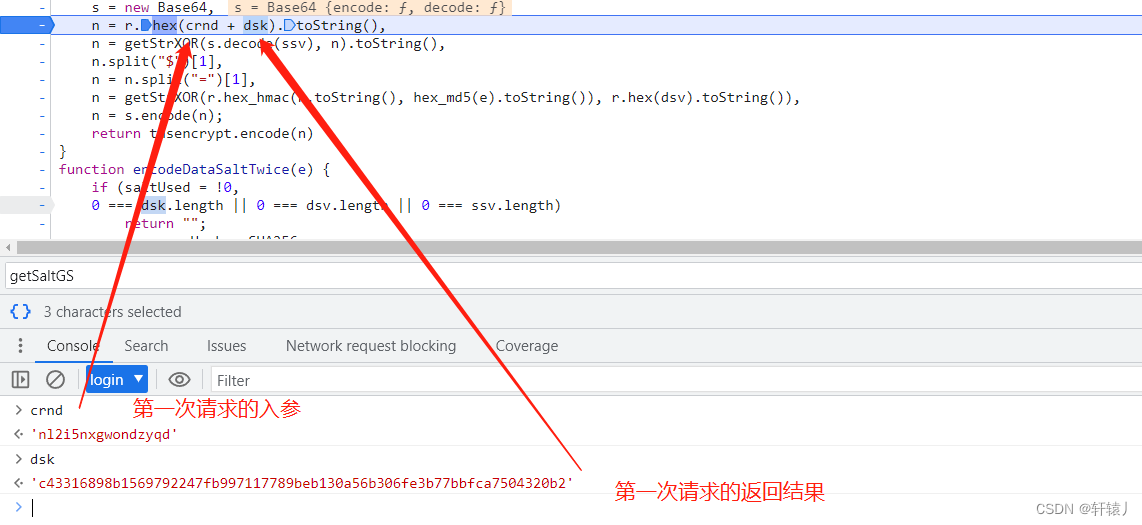
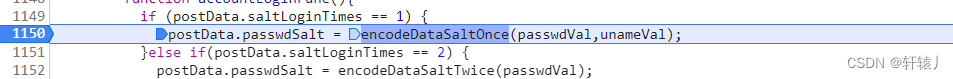
Here you can see that it is correct. The data returned for the first time is base64 decoded and then getStrXOR is carried out. I deducted this by performing getStrXOR
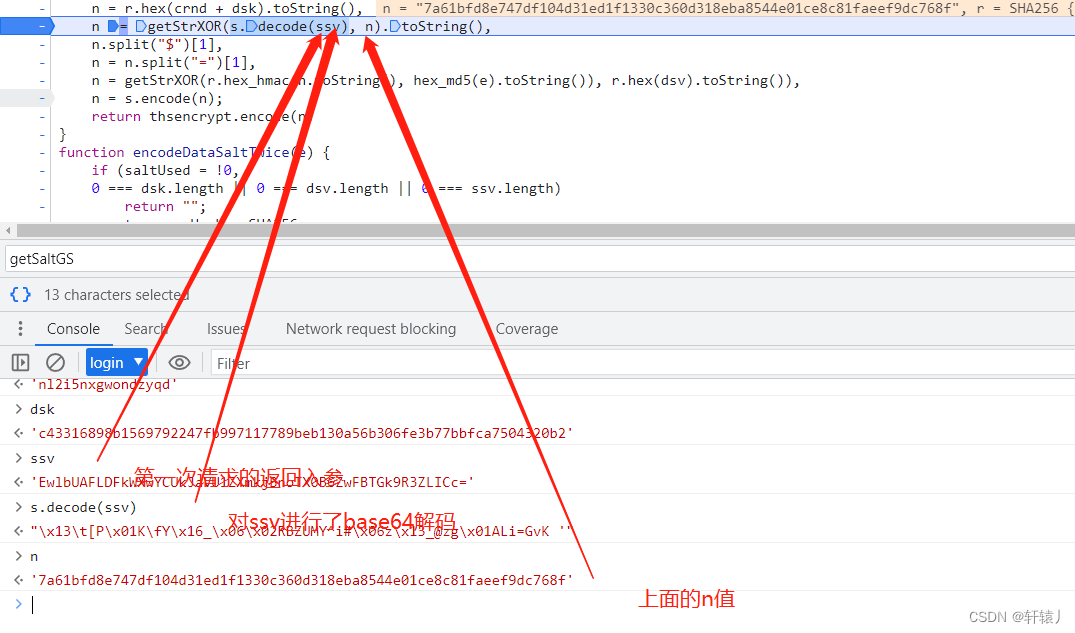
through the sha256 encryption of the md5 of the n value and the password and the sha256 of the dsv. Encode, the nested encryption is a bit more difficult
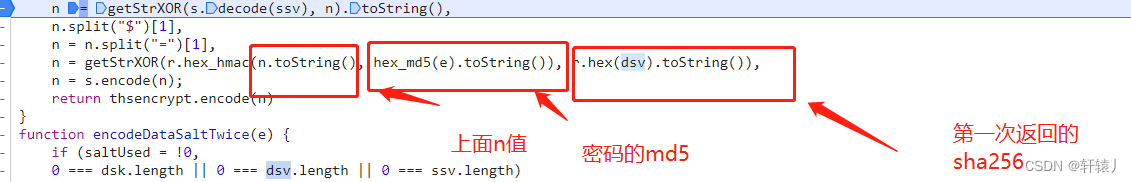
. Basically all the encryption has been done here. Then let’s look at the slider. The first time is the request gap, and the second time is verification. The input parameters are all in the request slider interface. It can be found, so let’s look at the phrase.
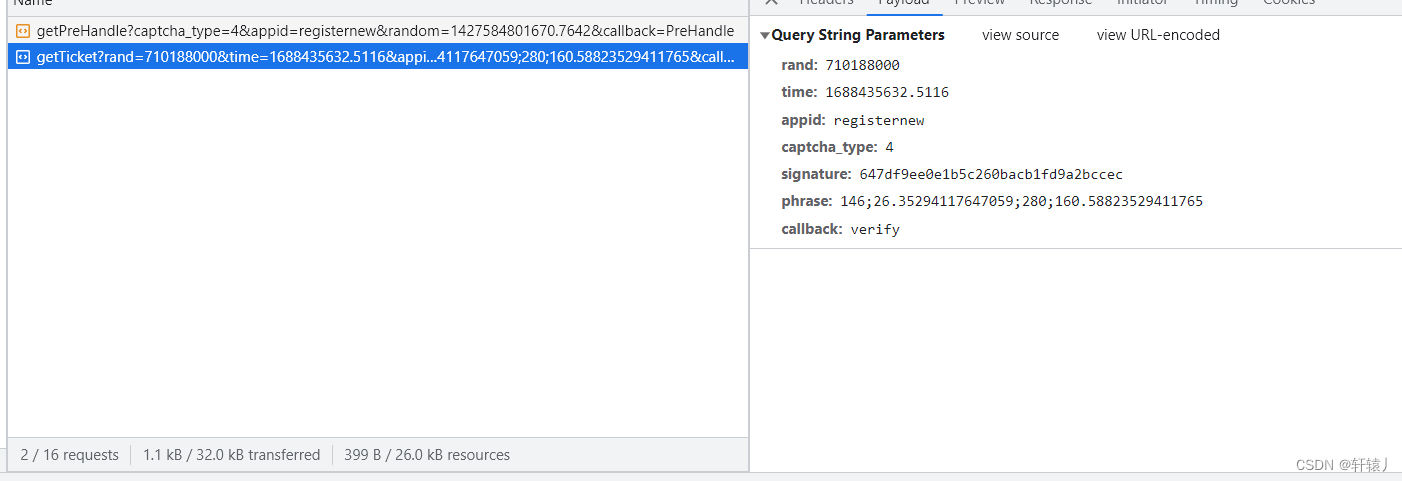
Here you can see that there is no encryption.
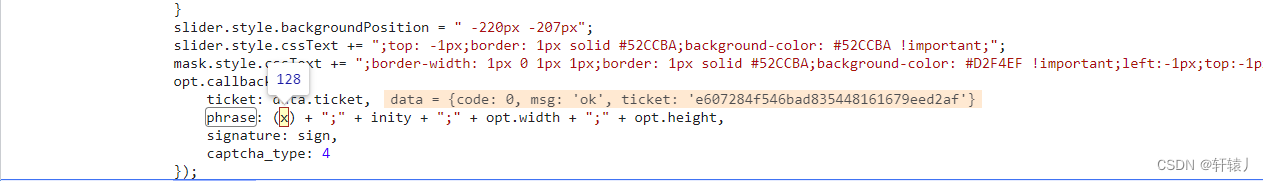
The difficulty is all over here. The input parameter explanation in dologinreturnjson2 is a bit
small. If you don’t bring it, you can’t log in. Through analysis, it is found that it is the value in the cookie, which
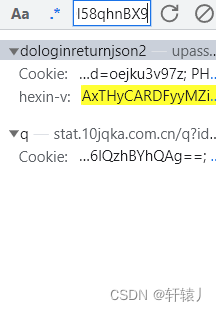
can be seen through hook technology
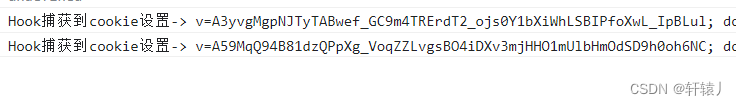
You can analyze it yourself and search for it

The introductory case of the combination of slider and login in this issue is over here, see you in the next issue! ! !
Bye-Bye! ! !

Show results
Part of js code sharing
const crypto = require('crypto');
const md5 = require('md5');
var b64map = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"
, b64padchar = "=";
function hex2b64(b) {
var a, c, d = "";
for (a = 0; a + 3 <= b.length; a += 3)
c = parseInt(b.substring(a, a + 3), 16),
d += b64map.charAt(c >> 6) + b64map.charAt(c & 63);
a + 1 == b.length ? (c = parseInt(b.substring(a, a + 1), 16),
d += b64map.charAt(c << 2)) : a + 2 == b.length && (c = parseInt(b.substring(a, a + 2), 16),
d += b64map.charAt(c >> 2) + b64map.charAt((c & 3) << 4));
for (; 0 < (d.length & 3); )
d += b64padchar;
return d
}
function getStrXOR(e, t) {
for (var n, s = e.length, r = t.length, o = "", d = 0; d < s; d++)
n = d % r,
o += String.fromCharCode(e.charCodeAt(d) ^ t.charCodeAt(n));
return o
}
function hmac_(keys, values) {
const hmac = crypto.createHmac('sha256', keys);
hmac.update(values);
return hmac.digest('hex')
}
function encodeDataSaltOnce(e, t, n, ssv, dsv) {
n = getStrXOR(atob(ssv), n).toString();
n.split("$")[1];
n = n.split("=")[1];
n = getStrXOR(hmac_(n.toString(), md5(e).toString()), dsv);
return btoa(n);
}
console.log(encodeDataSaltOnce('1231', "12312312343", 'ed32b85f205edd7090065e2012537c484d1a90d65a702f1011853e0deb69eb71', "QQxeUwEVXQdBWAdQUkBcVUANZ2VDE2ZgUl55fn0zZWBNCHI3V2g", "ee690f22f66d7666de70f45158c0997452bf9bdbd0d1137d78d4ca1bda2224bd"))