1. Write in front
For crawler developers, they may encounter various websites more or less in their careers, some of which require login to browse. Then during the simulated login, it is found that the submitted login information ( username , password ) is encrypted, how to deal with it? Here I found a website case, as the saying goes, changing the soup without changing the medicine , the reference of the case is an important supplement for the accumulation of reverse skills and methods
target site :
aHR0cDovL2xvZ2luLndzZ2pwLmNvbS5jbi8=
2. Analysis request
This time our goal is to conduct a reverse analysis on the encryption of the form information ( username , password ) submitted by login, so we directly construct a non-existent information at will and click submit and then perform packet capture analysis:
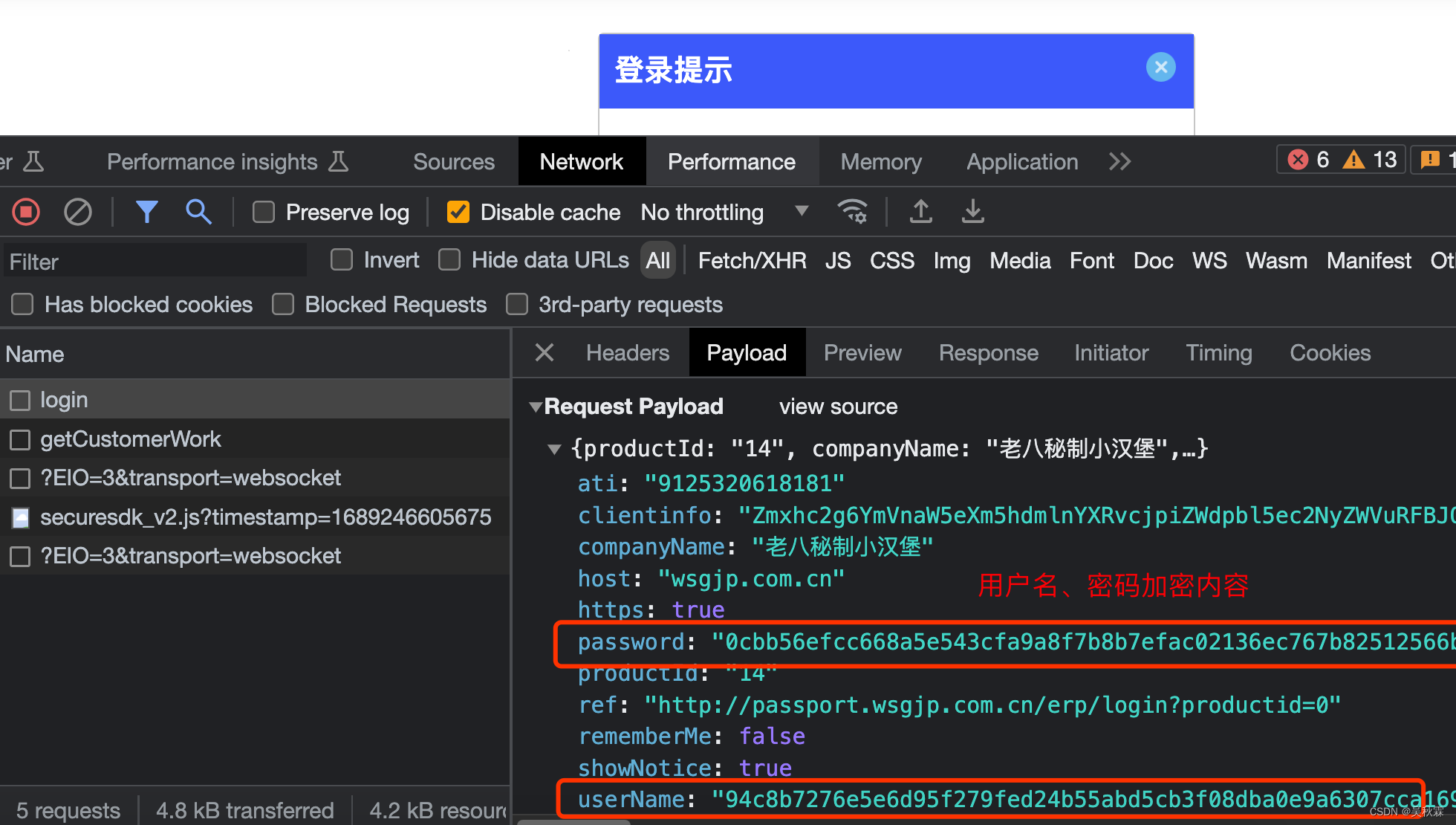
What needs to be said here is for us novices, how can we quickly find the requested URL during JS reverse analysis, sometimes there are a lot of requested URLs, which may be as few as dozens to hundreds
How do we quickly screen and screen, such as making good use of keyword search:
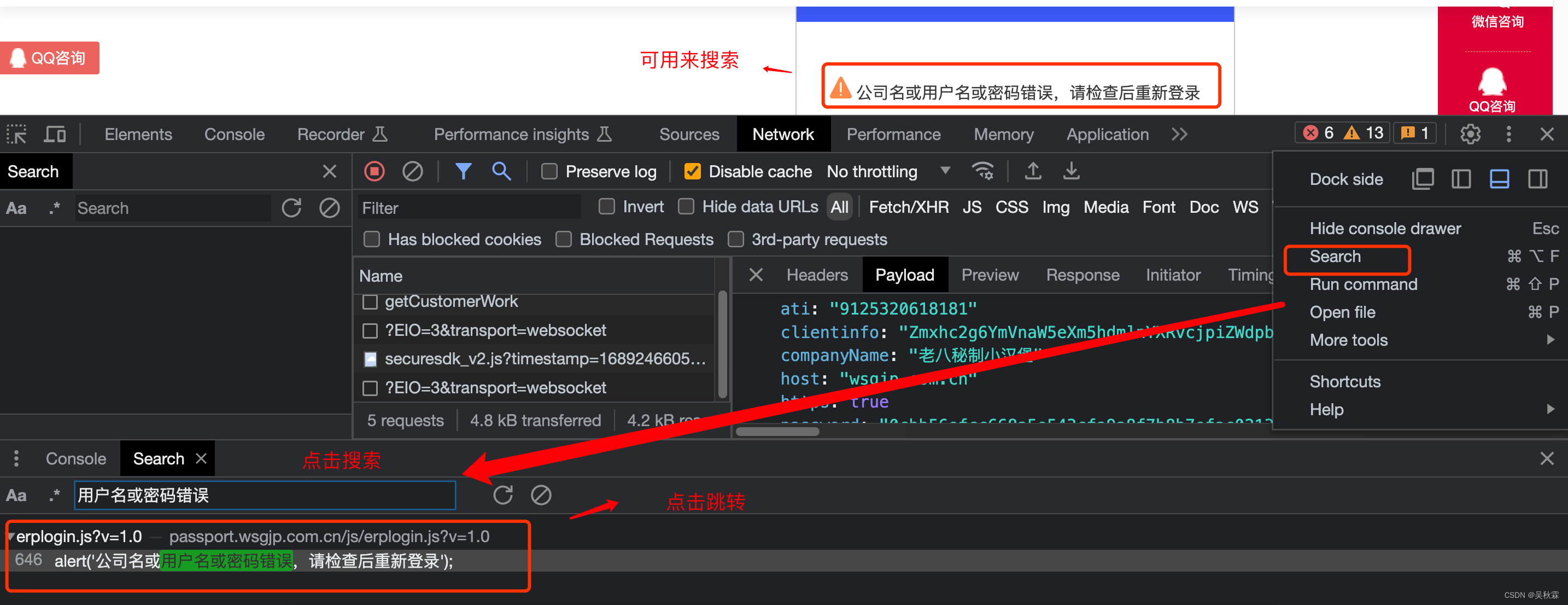
Because all submit click operation requests will be sent to the server, and the server will send the data to render to the website, so the feedback information above must be requested through a certain URLl
3. Find encryption points
Next, we need to find out how the above username and password are encrypted. According to the above method, we use password as a keyword search:
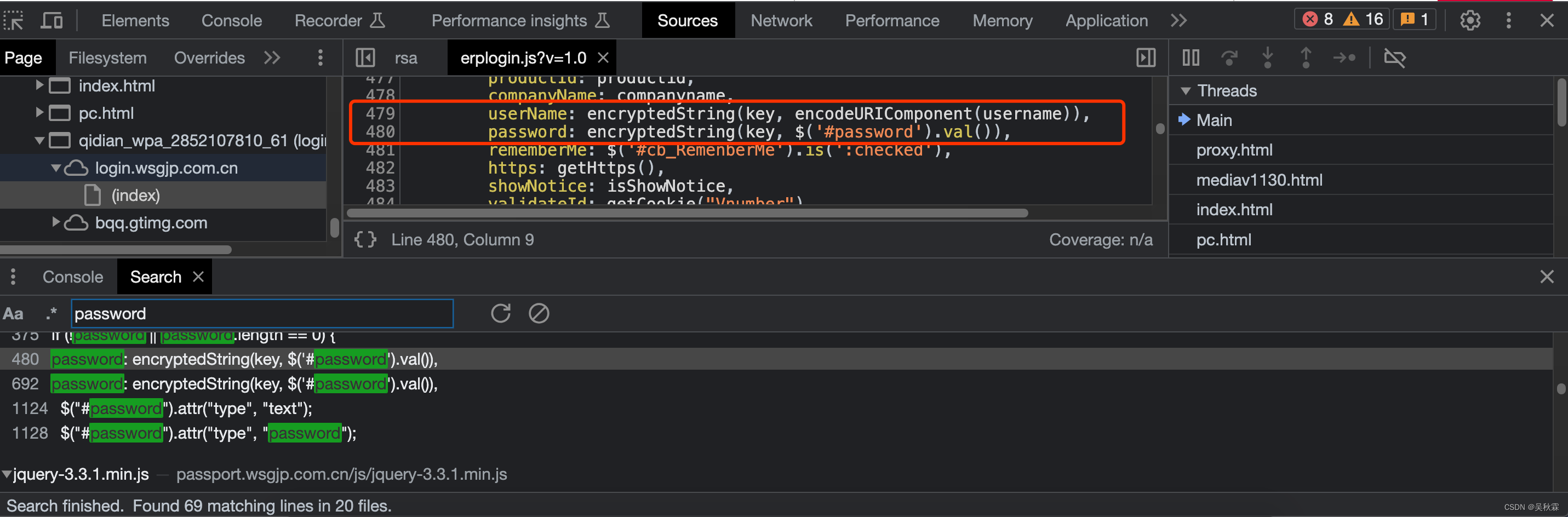
Here we can see that sometimes there may be multiple files with the password we searched for . If this is a novice with little experience, then we will slowly look, analyze and discover. For example, there is an encrypted code in the js file at the key word in green in the above picture, just like we use the investigation method, the encryption and decryption of these characteristic words are the objects we are looking for
We can see the two lines of encrypted call codes found in the search:
userName: encryptedString(key, encodeURIComponent(username)),
password: encryptedString(key, $('#password').val()),
Only after we breakpoint analysis can we know whether these two lines of code are the encryption point we are looking for, because when searching, we can see that these keywords often exist in multiple files, and some JS does not use them
Ok, now let's analyze the breakpoint:
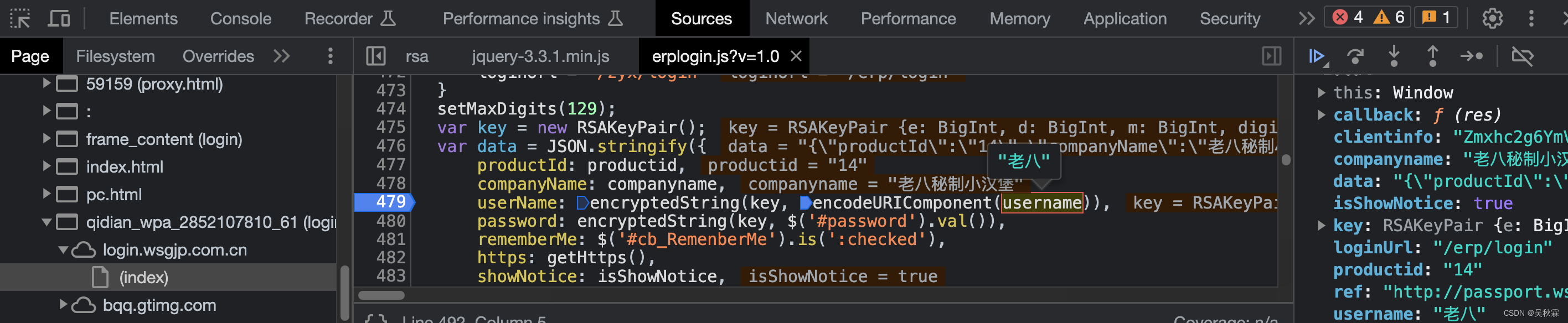
After setting the breakpoint, we submit the login information again, and we can see that the breakpoint stays at the 479 line breakpoint. We can see that userName and password encrypted values are generated by encryptedString by hovering the mouse
Sometimes when doing JS reverse analysis, making good use of console debugging can help us judge our inferences more intuitively. You must remember this little Tips ! Let's put the encryption function into the Console console output to see:
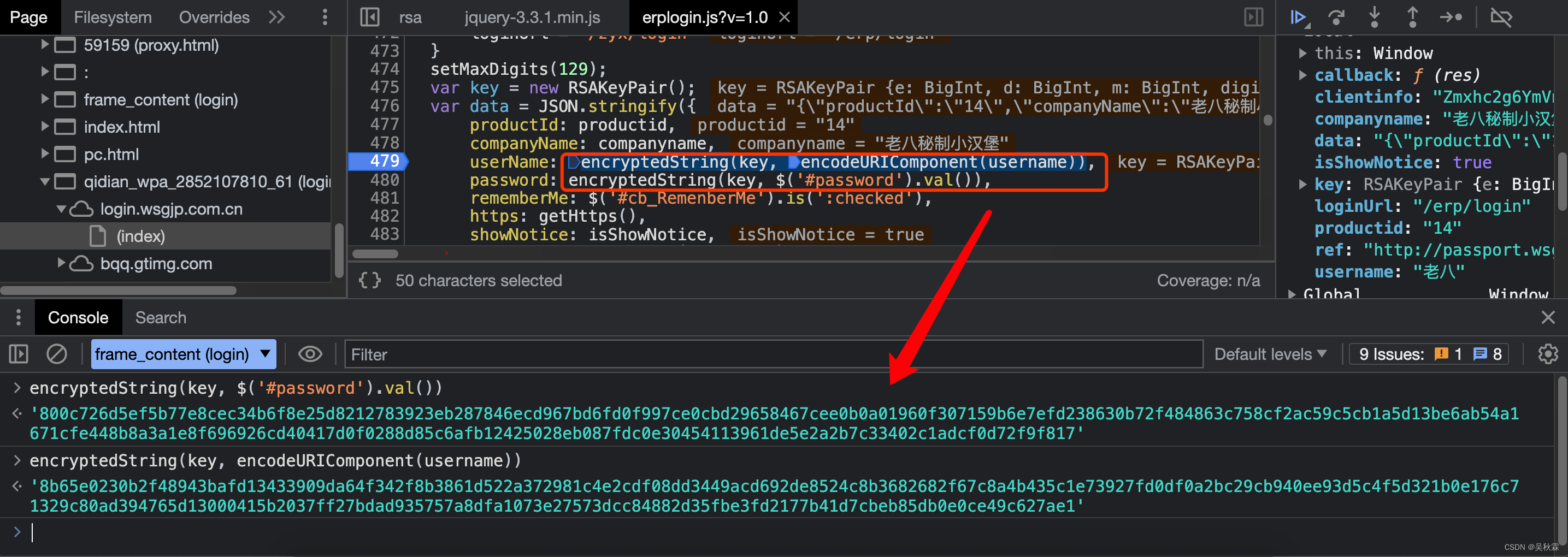
we can see that the encryption call is in the setMaxDigits function and the RSAKeyPair function is called before encryption , so these two functions also need to be deducted, and the encryptedString encryption called last function
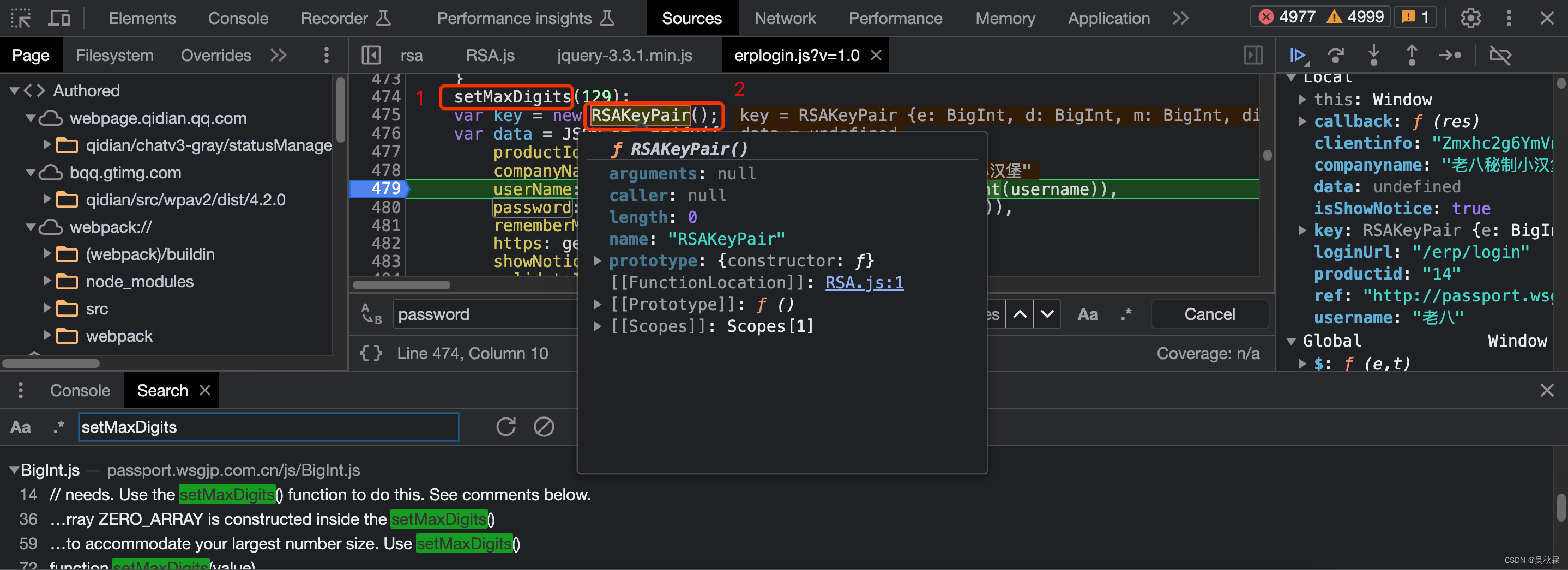
4. Deduction code
Code deduction, the main deduction is the logic and algorithm in the target code! When deducting the code, you only need to move the mouse to the function name, a prompt box will pop up as shown in the figure above, click to jump to the target function, you can find that there are not many codes in these functions, about a few What Baixing needs to pay attention to is that sometimes the amount of code is very large when deduction of JS code, remember not to take it all at once, many of them are useless logic, which seriously affects the efficiency
function RSAKeyPair() {
var encryptionExponent = "010001";
var decryptionExponent = "";
var modulus = "9A568982EE4BF010C38B5195A6F2DC7D66D5E6C02098CF25044CDD031AC08C6569D7063BB8959CB3FCB5AF572DE355AFA684AF7187948744E673275B494F394AF7F158841CA8B63BF65F185883F8D773A57ED731EDCD1AF2E0E57CD45F5F3CB4EBDD38F4A267E5ED02E7B44B93EDFFDADBDC8368019CD496BEC735BAF9E57125";
this.e = biFromHex(encryptionExponent);
this.d = biFromHex(decryptionExponent);
this.m = biFromHex(modulus);
this.digitSize = 2 * biHighIndex(this.m) + 2;
this.chunkSize = this.digitSize - 11;
this.radix = 16;
this.barrett = new BarrettMu(this.m);
}
function twoDigit(n) {
return (n < 10 ? "0" : "") + String(n);
}
function encryptedString(key, s) {
if (key.chunkSize > key.digitSize - 11) {
return "Error";
}
var a = new Array();
var sl = s.length;
var i = 0;
while (i < sl) {
a[i] = s.charCodeAt(i);
i++;
}
var al = a.length;
var result = "";
var j, k, block;
for (i = 0; i < al; i += key.chunkSize) {
block = new BigInt();
j = 0;
var x;
var msgLength = (i + key.chunkSize) > al ? al % key.chunkSize : key.chunkSize;
var b = new Array();
for (x = 0; x < msgLength; x++) {
b[x] = a[i + msgLength - 1 - x];
}
b[msgLength] = 0; // marker
var paddedSize = Math.max(8, key.digitSize - 3 - msgLength);
for (x = 0; x < paddedSize; x++) {
b[msgLength + 1 + x] = Math.floor(Math.random() * 254) + 1;
}
b[key.digitSize - 2] = 2; // marker
b[key.digitSize - 1] = 0; // marker
for (k = 0; k < key.digitSize; ++j) {
block.digits[j] = b[k++];
block.digits[j] += b[k++] << 8;
}
var crypt = key.barrett.powMod(block, key.e);
var text = key.radix == 16 ? biToHex(crypt) : biToString(crypt, key.radix);
result += text + " ";
}
return result.substring(0, result.length - 1); // Remove last space.
}
var biRadixBase = 2;
var biRadixBits = 16;
var bitsPerDigit = biRadixBits;
var biRadix = 1 << 16; // = 2^16 = 65536
var biHalfRadix = biRadix >>> 1;
var biRadixSquared = biRadix * biRadix;
var maxDigitVal = biRadix - 1;
var maxInteger = 9999999999999998;
var maxDigits;
var ZERO_ARRAY;
var bigZero, bigOne;
function setMaxDigits(value)
{
maxDigits = value;
ZERO_ARRAY = new Array(maxDigits);
for (var iza = 0; iza < ZERO_ARRAY.length; iza++) ZERO_ARRAY[iza] = 0;
bigZero = new BigInt();
bigOne = new BigInt();
bigOne.digits[0] = 1;
}
setMaxDigits(20);
// The maximum number of digits in base 10 you can convert to an
// integer without JavaScript throwing up on you.
var dpl10 = 15;
// lr10 = 10 ^ dpl10
var lr10 = biFromNumber(1000000000000000);
function BigInt(flag)
{
if (typeof flag == "boolean" && flag == true) {
this.digits = null;
}
else {
this.digits = ZERO_ARRAY.slice(0);
}
this.isNeg = false;
}
function biFromDecimal(s)
{
var isNeg = s.charAt(0) == '-';
var i = isNeg ? 1 : 0;
var result;
// Skip leading zeros.
while (i < s.length && s.charAt(i) == '0') ++i;
if (i == s.length) {
result = new BigInt();
}
else {
var digitCount = s.length - i;
var fgl = digitCount % dpl10;
if (fgl == 0) fgl = dpl10;
result = biFromNumber(Number(s.substr(i, fgl)));
i += fgl;
while (i < s.length) {
result = biAdd(biMultiply(result, lr10),
biFromNumber(Number(s.substr(i, dpl10))));
i += dpl10;
}
result.isNeg = isNeg;
}
return result;
}
function biCopy(bi)
{
var result = new BigInt(true);
result.digits = bi.digits.slice(0);
result.isNeg = bi.isNeg;
return result;
}
function biFromNumber(i)
{
var result = new BigInt();
result.isNeg = i < 0;
i = Math.abs(i);
var j = 0;
while (i > 0) {
result.digits[j++] = i & maxDigitVal;
i = Math.floor(i / biRadix);
}
return result;
}
function reverseStr(s)
{
var result = "";
for (var i = s.length - 1; i > -1; --i) {
result += s.charAt(i);
}
return result;
}
var hexatrigesimalToChar = new Array(
'0', '1', '2', '3', '4', '5', '6', '7', '8', '9',
'a', 'b', 'c', 'd', 'e', 'f', 'g', 'h', 'i', 'j',
'k', 'l', 'm', 'n', 'o', 'p', 'q', 'r', 's', 't',
'u', 'v', 'w', 'x', 'y', 'z'
);
function biToString(x, radix)
// 2 <= radix <= 36
{
var b = new BigInt();
b.digits[0] = radix;
var qr = biDivideModulo(x, b);
var result = hexatrigesimalToChar[qr[1].digits[0]];
while (biCompare(qr[0], bigZero) == 1) {
qr = biDivideModulo(qr[0], b);
digit = qr[1].digits[0];
result += hexatrigesimalToChar[qr[1].digits[0]];
}
return (x.isNeg ? "-" : "") + reverseStr(result);
}
function biToDecimal(x)
{
var b = new BigInt();
b.digits[0] = 10;
var qr = biDivideModulo(x, b);
var result = String(qr[1].digits[0]);
while (biCompare(qr[0], bigZero) == 1) {
qr = biDivideModulo(qr[0], b);
result += String(qr[1].digits[0]);
}
return (x.isNeg ? "-" : "") + reverseStr(result);
}
var hexToChar = new Array('0', '1', '2', '3', '4', '5', '6', '7', '8', '9',
'a', 'b', 'c', 'd', 'e', 'f');
function digitToHex(n)
{
var mask = 0xf;
var result = "";
for (i = 0; i < 4; ++i) {
result += hexToChar[n & mask];
n >>>= 4;
}
return reverseStr(result);
}
function biToHex(x)
{
var result = "";
var n = biHighIndex(x);
for (var i = biHighIndex(x); i > -1; --i) {
result += digitToHex(x.digits[i]);
}
return result;
}
function charToHex(c)
{
var ZERO = 48;
var NINE = ZERO + 9;
var littleA = 97;
var littleZ = littleA + 25;
var bigA = 65;
var bigZ = 65 + 25;
var result;
if (c >= ZERO && c <= NINE) {
result = c - ZERO;
} else if (c >= bigA && c <= bigZ) {
result = 10 + c - bigA;
} else if (c >= littleA && c <= littleZ) {
result = 10 + c - littleA;
} else {
result = 0;
}
return result;
}
function hexToDigit(s)
{
var result = 0;
var sl = Math.min(s.length, 4);
for (var i = 0; i < sl; ++i) {
result <<= 4;
result |= charToHex(s.charCodeAt(i))
}
return result;
}
function biFromHex(s)
{
var result = new BigInt();
var sl = s.length;
for (var i = sl, j = 0; i > 0; i -= 4, ++j) {
result.digits[j] = hexToDigit(s.substr(Math.max(i - 4, 0), Math.min(i, 4)));
}
return result;
}
function biFromString(s, radix)
{
var isNeg = s.charAt(0) == '-';
var istop = isNeg ? 1 : 0;
var result = new BigInt();
var place = new BigInt();
place.digits[0] = 1; // radix^0
for (var i = s.length - 1; i >= istop; i--) {
var c = s.charCodeAt(i);
var digit = charToHex(c);
var biDigit = biMultiplyDigit(place, digit);
result = biAdd(result, biDigit);
place = biMultiplyDigit(place, radix);
}
result.isNeg = isNeg;
return result;
}
function biDump(b)
{
return (b.isNeg ? "-" : "") + b.digits.join(" ");
}
function biAdd(x, y)
{
var result;
if (x.isNeg != y.isNeg) {
y.isNeg = !y.isNeg;
result = biSubtract(x, y);
y.isNeg = !y.isNeg;
}
else {
result = new BigInt();
var c = 0;
var n;
for (var i = 0; i < x.digits.length; ++i) {
n = x.digits[i] + y.digits[i] + c;
result.digits[i] = n % biRadix;
c = Number(n >= biRadix);
}
result.isNeg = x.isNeg;
}
return result;
}
function biSubtract(x, y)
{
var result;
if (x.isNeg != y.isNeg) {
y.isNeg = !y.isNeg;
result = biAdd(x, y);
y.isNeg = !y.isNeg;
} else {
result = new BigInt();
var n, c;
c = 0;
for (var i = 0; i < x.digits.length; ++i) {
n = x.digits[i] - y.digits[i] + c;
result.digits[i] = n % biRadix;
// Stupid non-conforming modulus operation.
if (result.digits[i] < 0) result.digits[i] += biRadix;
c = 0 - Number(n < 0);
}
// Fix up the negative sign, if any.
if (c == -1) {
c = 0;
for (var i = 0; i < x.digits.length; ++i) {
n = 0 - result.digits[i] + c;
result.digits[i] = n % biRadix;
// Stupid non-conforming modulus operation.
if (result.digits[i] < 0) result.digits[i] += biRadix;
c = 0 - Number(n < 0);
}
// Result is opposite sign of arguments.
result.isNeg = !x.isNeg;
} else {
// Result is same sign.
result.isNeg = x.isNeg;
}
}
return result;
}
function biHighIndex(x)
{
var result = x.digits.length - 1;
while (result > 0 && x.digits[result] == 0) --result;
return result;
}
function biNumBits(x)
{
var n = biHighIndex(x);
var d = x.digits[n];
var m = (n + 1) * bitsPerDigit;
var result;
for (result = m; result > m - bitsPerDigit; --result) {
if ((d & 0x8000) != 0) break;
d <<= 1;
}
return result;
}
function biMultiply(x, y)
{
var result = new BigInt();
var c;
var n = biHighIndex(x);
var t = biHighIndex(y);
var u, uv, k;
for (var i = 0; i <= t; ++i) {
c = 0;
k = i;
for (j = 0; j <= n; ++j, ++k) {
uv = result.digits[k] + x.digits[j] * y.digits[i] + c;
result.digits[k] = uv & maxDigitVal;
c = uv >>> biRadixBits;
//c = Math.floor(uv / biRadix);
}
result.digits[i + n + 1] = c;
}
// Someone give me a logical xor, please.
result.isNeg = x.isNeg != y.isNeg;
return result;
}
function biMultiplyDigit(x, y)
{
var n, c, uv;
result = new BigInt();
n = biHighIndex(x);
c = 0;
for (var j = 0; j <= n; ++j) {
uv = result.digits[j] + x.digits[j] * y + c;
result.digits[j] = uv & maxDigitVal;
c = uv >>> biRadixBits;
//c = Math.floor(uv / biRadix);
}
result.digits[1 + n] = c;
return result;
}
function arrayCopy(src, srcStart, dest, destStart, n)
{
var m = Math.min(srcStart + n, src.length);
for (var i = srcStart, j = destStart; i < m; ++i, ++j) {
dest[j] = src[i];
}
}
var highBitMasks = new Array(0x0000, 0x8000, 0xC000, 0xE000, 0xF000, 0xF800,
0xFC00, 0xFE00, 0xFF00, 0xFF80, 0xFFC0, 0xFFE0,
0xFFF0, 0xFFF8, 0xFFFC, 0xFFFE, 0xFFFF);
function biShiftLeft(x, n)
{
var digitCount = Math.floor(n / bitsPerDigit);
var result = new BigInt();
arrayCopy(x.digits, 0, result.digits, digitCount,
result.digits.length - digitCount);
var bits = n % bitsPerDigit;
var rightBits = bitsPerDigit - bits;
for (var i = result.digits.length - 1, i1 = i - 1; i > 0; --i, --i1) {
result.digits[i] = ((result.digits[i] << bits) & maxDigitVal) |
((result.digits[i1] & highBitMasks[bits]) >>>
(rightBits));
}
result.digits[0] = ((result.digits[i] << bits) & maxDigitVal);
result.isNeg = x.isNeg;
return result;
}
var lowBitMasks = new Array(0x0000, 0x0001, 0x0003, 0x0007, 0x000F, 0x001F,
0x003F, 0x007F, 0x00FF, 0x01FF, 0x03FF, 0x07FF,
0x0FFF, 0x1FFF, 0x3FFF, 0x7FFF, 0xFFFF);
function biShiftRight(x, n)
{
var digitCount = Math.floor(n / bitsPerDigit);
var result = new BigInt();
arrayCopy(x.digits, digitCount, result.digits, 0,
x.digits.length - digitCount);
var bits = n % bitsPerDigit;
var leftBits = bitsPerDigit - bits;
for (var i = 0, i1 = i + 1; i < result.digits.length - 1; ++i, ++i1) {
result.digits[i] = (result.digits[i] >>> bits) |
((result.digits[i1] & lowBitMasks[bits]) << leftBits);
}
result.digits[result.digits.length - 1] >>>= bits;
result.isNeg = x.isNeg;
return result;
}
function biMultiplyByRadixPower(x, n)
{
var result = new BigInt();
arrayCopy(x.digits, 0, result.digits, n, result.digits.length - n);
return result;
}
function biDivideByRadixPower(x, n)
{
var result = new BigInt();
arrayCopy(x.digits, n, result.digits, 0, result.digits.length - n);
return result;
}
function biModuloByRadixPower(x, n)
{
var result = new BigInt();
arrayCopy(x.digits, 0, result.digits, 0, n);
return result;
}
function biCompare(x, y)
{
if (x.isNeg != y.isNeg) {
return 1 - 2 * Number(x.isNeg);
}
for (var i = x.digits.length - 1; i >= 0; --i) {
if (x.digits[i] != y.digits[i]) {
if (x.isNeg) {
return 1 - 2 * Number(x.digits[i] > y.digits[i]);
} else {
return 1 - 2 * Number(x.digits[i] < y.digits[i]);
}
}
}
return 0;
}
function biDivideModulo(x, y)
{
var nb = biNumBits(x);
var tb = biNumBits(y);
var origYIsNeg = y.isNeg;
var q, r;
if (nb < tb) {
// |x| < |y|
if (x.isNeg) {
q = biCopy(bigOne);
q.isNeg = !y.isNeg;
x.isNeg = false;
y.isNeg = false;
r = biSubtract(y, x);
// Restore signs, 'cause they're references.
x.isNeg = true;
y.isNeg = origYIsNeg;
} else {
q = new BigInt();
r = biCopy(x);
}
return new Array(q, r);
}
q = new BigInt();
r = x;
// Normalize Y.
var t = Math.ceil(tb / bitsPerDigit) - 1;
var lambda = 0;
while (y.digits[t] < biHalfRadix) {
y = biShiftLeft(y, 1);
++lambda;
++tb;
t = Math.ceil(tb / bitsPerDigit) - 1;
}
// Shift r over to keep the quotient constant. We'll shift the
// remainder back at the end.
r = biShiftLeft(r, lambda);
nb += lambda; // Update the bit count for x.
var n = Math.ceil(nb / bitsPerDigit) - 1;
var b = biMultiplyByRadixPower(y, n - t);
while (biCompare(r, b) != -1) {
++q.digits[n - t];
r = biSubtract(r, b);
}
for (var i = n; i > t; --i) {
var ri = (i >= r.digits.length) ? 0 : r.digits[i];
var ri1 = (i - 1 >= r.digits.length) ? 0 : r.digits[i - 1];
var ri2 = (i - 2 >= r.digits.length) ? 0 : r.digits[i - 2];
var yt = (t >= y.digits.length) ? 0 : y.digits[t];
var yt1 = (t - 1 >= y.digits.length) ? 0 : y.digits[t - 1];
if (ri == yt) {
q.digits[i - t - 1] = maxDigitVal;
} else {
q.digits[i - t - 1] = Math.floor((ri * biRadix + ri1) / yt);
}
var c1 = q.digits[i - t - 1] * ((yt * biRadix) + yt1);
var c2 = (ri * biRadixSquared) + ((ri1 * biRadix) + ri2);
while (c1 > c2) {
--q.digits[i - t - 1];
c1 = q.digits[i - t - 1] * ((yt * biRadix) | yt1);
c2 = (ri * biRadix * biRadix) + ((ri1 * biRadix) + ri2);
}
b = biMultiplyByRadixPower(y, i - t - 1);
r = biSubtract(r, biMultiplyDigit(b, q.digits[i - t - 1]));
if (r.isNeg) {
r = biAdd(r, b);
--q.digits[i - t - 1];
}
}
r = biShiftRight(r, lambda);
// Fiddle with the signs and stuff to make sure that 0 <= r < y.
q.isNeg = x.isNeg != origYIsNeg;
if (x.isNeg) {
if (origYIsNeg) {
q = biAdd(q, bigOne);
} else {
q = biSubtract(q, bigOne);
}
y = biShiftRight(y, lambda);
r = biSubtract(y, r);
}
// Check for the unbelievably stupid degenerate case of r == -0.
if (r.digits[0] == 0 && biHighIndex(r) == 0) r.isNeg = false;
return new Array(q, r);
}
function biDivide(x, y)
{
return biDivideModulo(x, y)[0];
}
function biModulo(x, y)
{
return biDivideModulo(x, y)[1];
}
function biMultiplyMod(x, y, m)
{
return biModulo(biMultiply(x, y), m);
}
function biPow(x, y)
{
var result = bigOne;
var a = x;
while (true) {
if ((y & 1) != 0) result = biMultiply(result, a);
y >>= 1;
if (y == 0) break;
a = biMultiply(a, a);
}
return result;
}
function biPowMod(x, y, m)
{
var result = bigOne;
var a = x;
var k = y;
while (true) {
if ((k.digits[0] & 1) != 0) result = biMultiplyMod(result, a, m);
k = biShiftRight(k, 1);
if (k.digits[0] == 0 && biHighIndex(k) == 0) break;
a = biMultiplyMod(a, a, m);
}
return result;
}
The pile of JS above is the code to implement the encryption algorithm. Let’s take a look at the code and do a simple analysis. Although we don’t need to understand the logic of too many encryption algorithms, if we can understand it and know why, then we can also Can implement its entire encryption algorithm in other ways or languages:
- The RSAKeyPair function defines an RSA key pair. You can see that encryptionExponent is the public key and decryptionExponent is the private key. Then, by calling other functions, the public and private key indices and other variables are stored in the RSA key object.
- The encryptedString function mainly implements some encryption operations on strings, and accepts keys and strings as parameters. Check whether the chunkSize of the key is legal, convert the string into a character array, and encrypt the character array in blocks according to the chunkSize. During the encryption process, use randomly generated padding data and return the encrypted string
- The BigInt function is a large integer class for processing large numbers. It contains properties and methods of large integers, such as creating large integers, copying large integers, comparing sizes, adding, subtracting, etc.
- The biFromHex function converts a hexadecimal string to a big integer. It starts at the end of the string, converts every four digits to a decimal digit, and stores it in the digits property of the big integer object
- The biMultiply function implements the multiplication operation of two large integers. It uses the traditional vertical multiplication algorithm, multiplying bit by bit and taking into account the carry
- The biModulo function calculates the result of the modulo operation of two large integers, that is, returns the remainder of the division
- The biPowMod function calculates the power modulo result of a large integer. It uses a fast exponentiation algorithm for computational efficiency
One thing they do: together form a simple RSA encryption algorithm
Here you can see that $('#password') in the password encryption place represents the jQuery selector of the password input box, and passes parameters by simulating user input. So here we need to simply write two test function calls to verify:
// 用户名加密
function UsernameEncryption(username) {
setMaxDigits(129);
var key = new RSAKeyPair();
return encryptedString(key, encodeURIComponent(username))
}
// 密码加密
function PasswordEncryption() {
setMaxDigits(129);
var key = new RSAKeyPair();
var password = '123456'
$('#password').val(password);
return encryptedString(key, $('#password').val())
}
Next, just put the above packaged JS code directly into the debugging tool for testing. There are still many JS debugging tools . What to make up ):
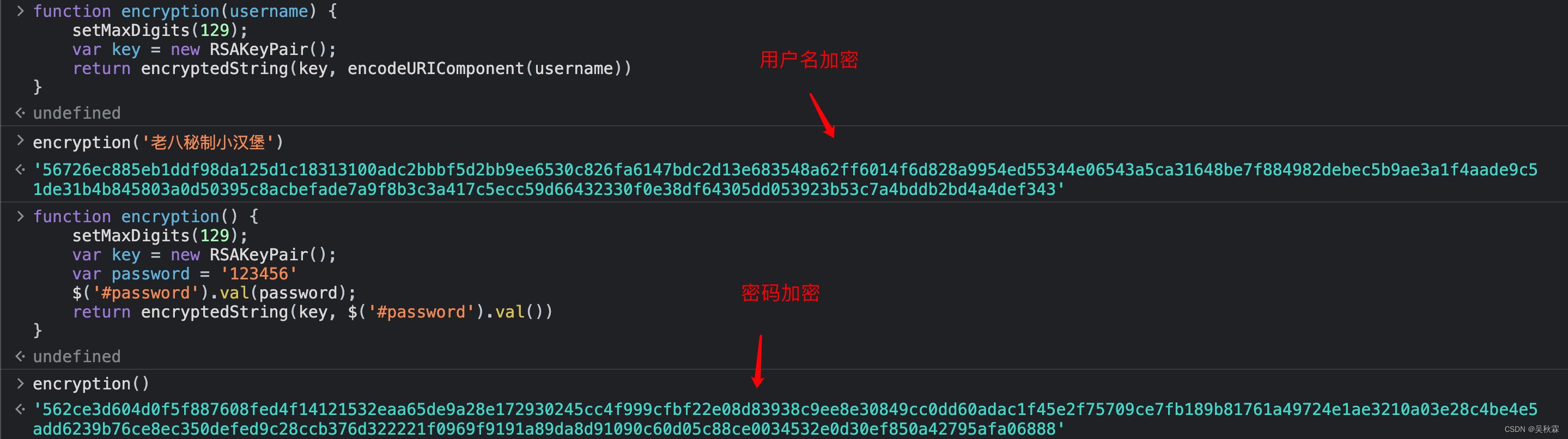
At this point, we have completely obtained the encryption scheme for the login submission information. The JS code deducted above can be called in our Python code, or it can be implemented by ourselves. Of course, there must be a certain degree of difficulty. Generally, most of the JS reverse work in the way of direct call
This is a very simple case. It is not too difficult to find the encryption point to deduct the corresponding JS code. These are some common techniques in JS reverse engineering.
Well, it's time to say goodbye to everyone here again. It's not easy to create, please give me a like before leaving. Your support is the driving force for my creation, and I hope to bring you more high-quality articles