Article Directory
1. Write in front
A good reverse can help us understand the encryption implementation, and then restore the encryption algorithm according to the encryption method ( md5, base64, res, des, rsa... ). You can take a look at my previous article: Quickly locate and find the characteristics and skills of encryption methods
target site :
aHR0cHM6Ly9hY2NvdW50LnBwZGFpLmNvbS9wYy9sb2dpbg==
2. Packet capture analysis
The user name userName and password password of this website are both encrypted, password encryption can often be seen, even the user name is not very common!
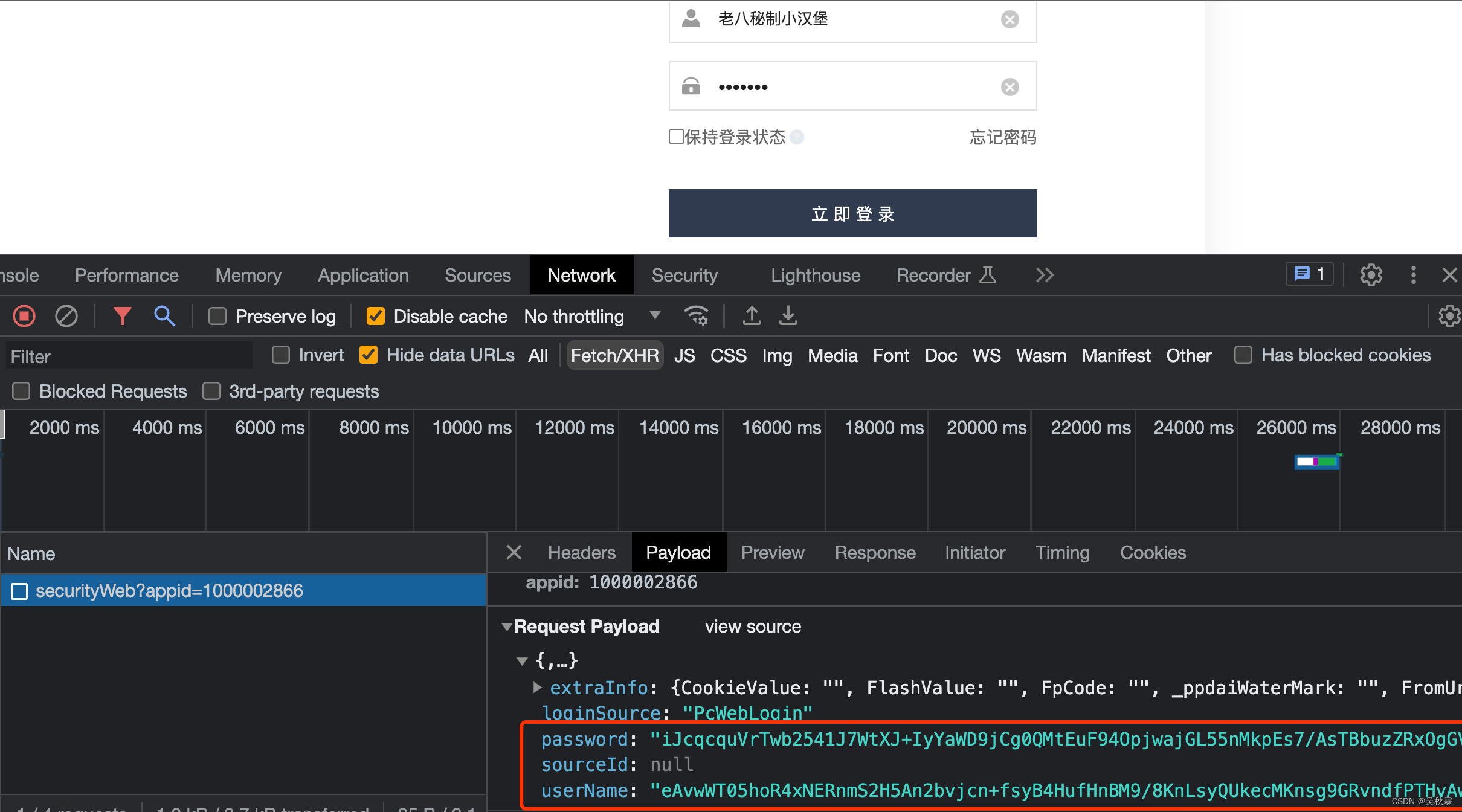
According to my previous articles, such a case is very simple. Search for these two parameters:
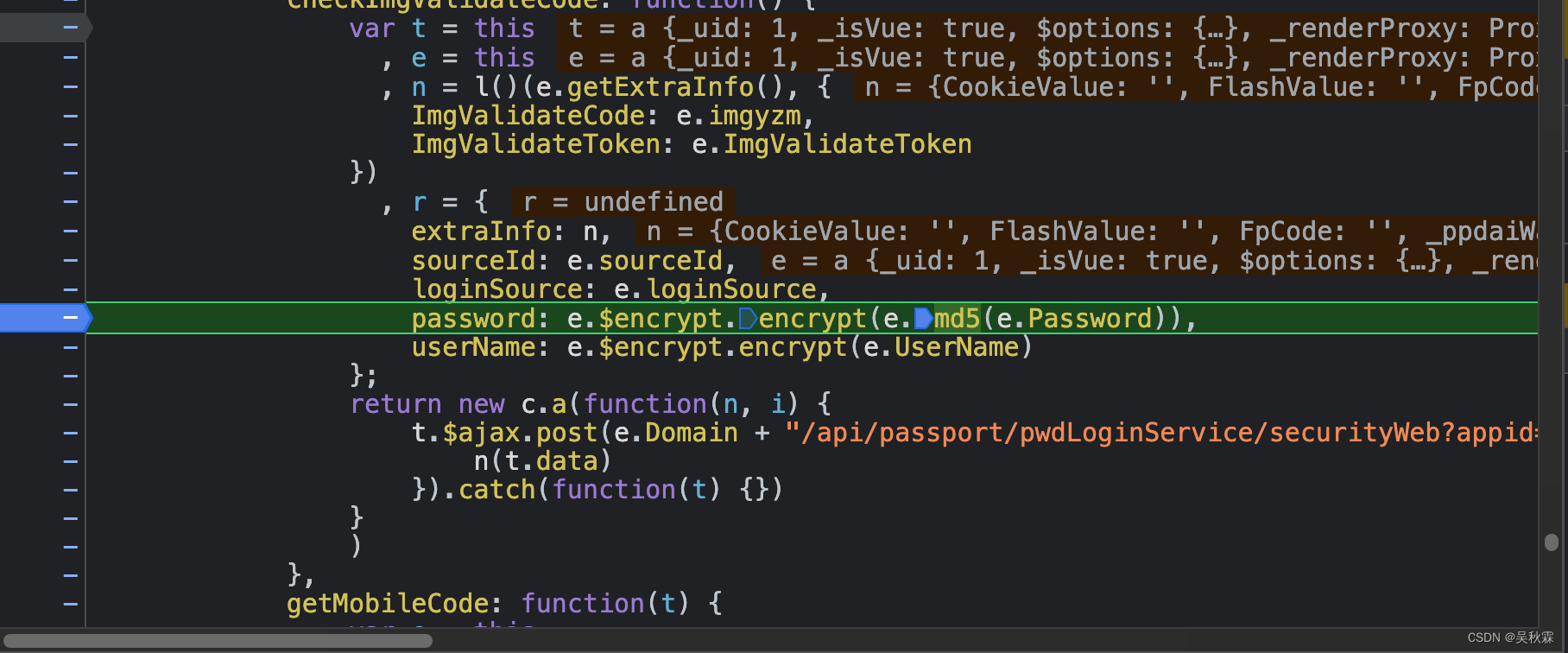
Search and jump to the above picture, you can see that there are two important lines of code:
password: e.$encrypt.encrypt(e.md5(e.Password))
userName: e.$encrypt.encrypt(e.UserName)
These two lines of code are the username and password corresponding to the login box! encrypt is obviously encrypted using an encryption function. If you are not sure, you can make a breakpoint and repeat the login verification
These two lines are not the real encryption code, next we need to find the real encryption code block, move the mouse to the encrypt encryption function and click to jump
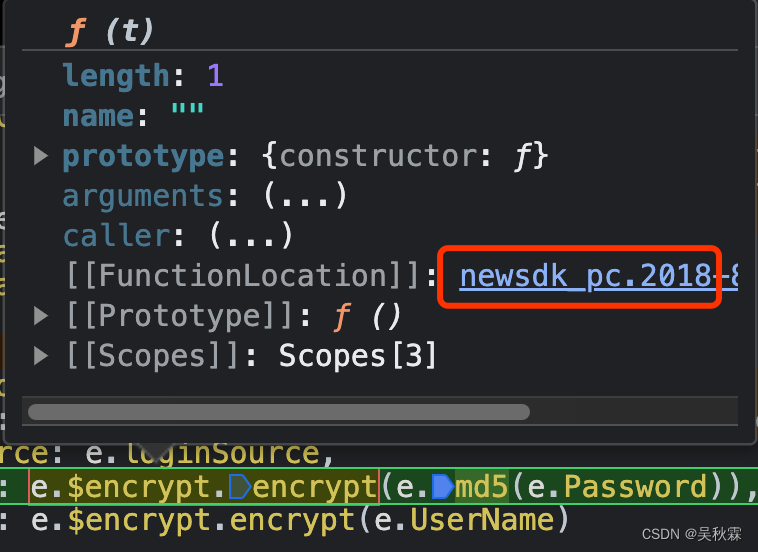
This encryption method is RSA, if there is no public key, it will be automatically generated. The user name is directly encrypted, and the password is obtained after being encrypted by md5 and then encrypted by RSA again. The value of e.md5 is equal to the r function:
function r(t) {
return o(i(a(t)))
}
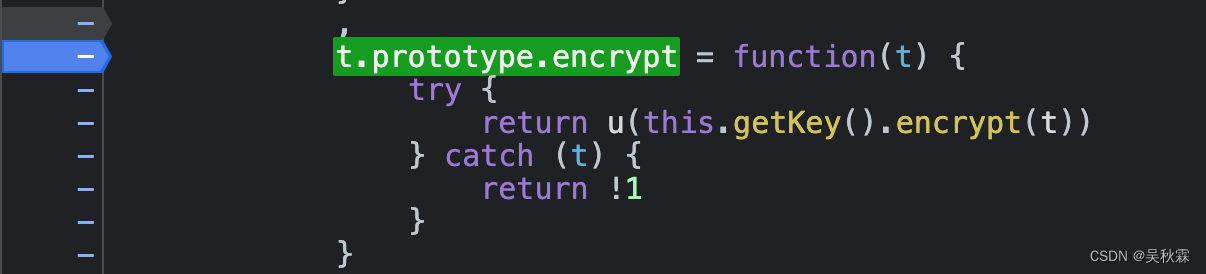
The encryption function is defined in the prototype and needs to be instantiated when calling the encryption function:
The encryption function has been exported as window.JSEncrypt , which is how webpack loads the module:
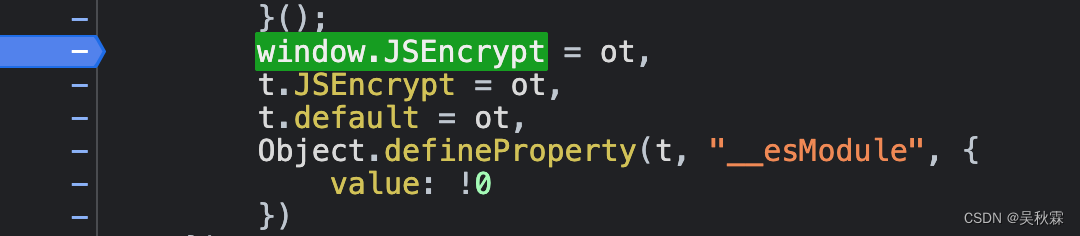
3. Deduct the encryption code
Here, take out the entire JS code and analyze it, and find the code block where the key code of t.prototype.encrypt is located:

Next, we can search to find: o(i(a(t))) and e.md5(e.Password)
in the extracted JS code to find their encryption modules, here we search for e.md5(e.Password) For example, find the following code block:
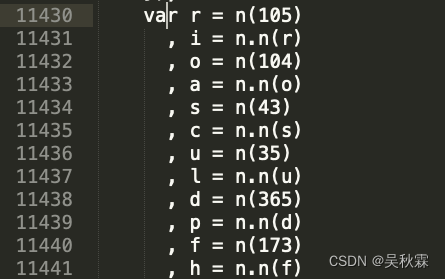
The above n (173) is actually the code block loaded by the loader. The key of the code block in the array is 173 , which can be verified by the principle of webpack loading module. Here n is the loader method
Re-login at the breakpoint under the loader to obtain the n(173) code block:
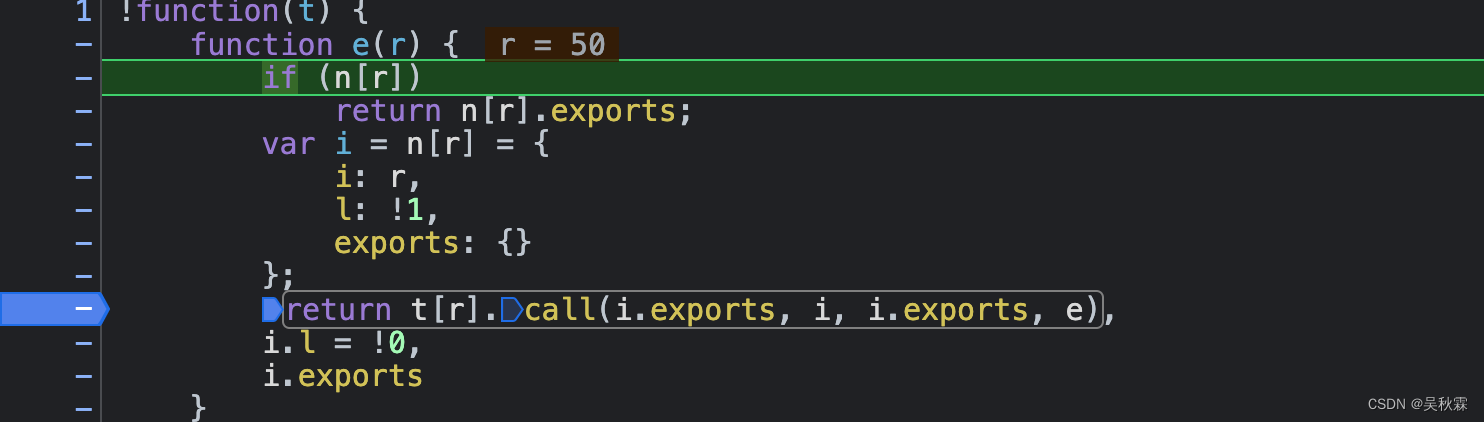
Replace n with loader e, and enter e(173) in the console to get the value. If it is a method, click directly to enter the corresponding method. If it is an object, we will find the link corresponding to FunctionLocation in the object.
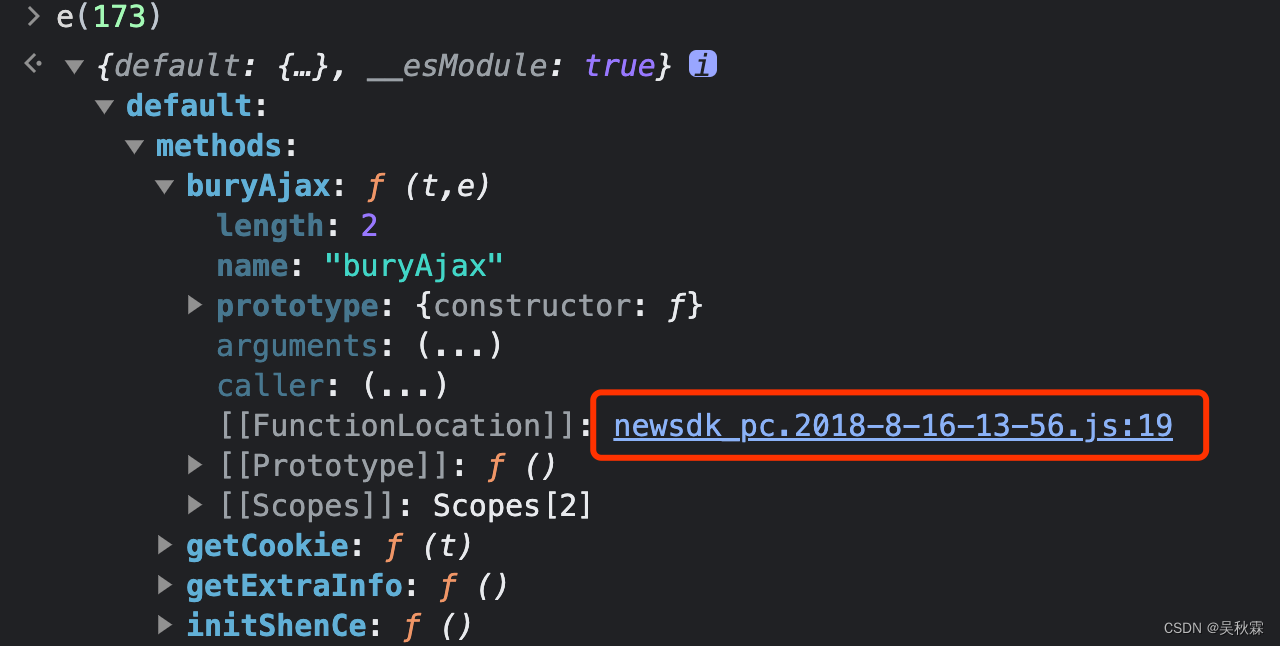
Click to jump as follows:
In this way, all the code blocks similar to n(173) above can be found out and placed in the parentheses at the end of webpack:
(function(){
})([
//加载代码105
//加载代码104
//加载代码173
...
])
The encryption function of this website is defined by assigning to the prototype. t.prototype.encrypt = function(){} , so it needs to be instantiated when calling the encryption method
Export method of md5 encryption function:
window.pcLoginSdk = {
option: {
md5: b.default.hex_md5,
}
}
b.default is the object, the r method is the real encryption function, and various functions are encapsulated in the r method
The calling method of md5 encryption is: window.pcLoginSdk.option.md5
Now let's look at the encrypt and md5 encryption method call codes:
var enc = new window.JSEncrypt;
enc.encrypt('老八秘制小汉堡');
window.pcLoginSdk.option.md5('123456');
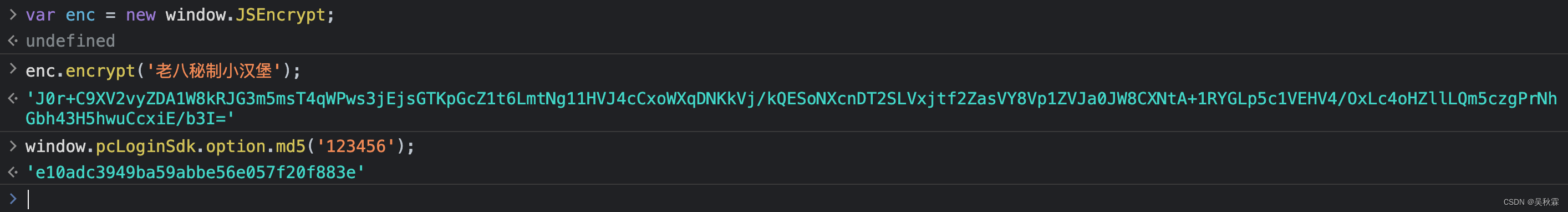
In fact, it is not necessary to dig out the code, just take the whole code and use it. Of course, there are many codes and sometimes other code blocks will load dom and bom. At this time, you must dig out the code. If you don’t dig out the code, you need to supplement the environment!
Well, it's time to say goodbye to everyone here again. It's not easy to create, please give me a like before leaving. Your support is the driving force for my creation, and I hope to bring you more high-quality articles