Table of contents
3. Experimental content and requirements
4. Experimental order and results
6. Experiment report and topology map download link
1. Purpose of the experiment
1. Understand the process of enterprise network construction
2. Master the networking technology of establishing a small and medium-sized enterprise network;
3. Master the security technology for setting up small and medium-sized enterprise networks
2. Equipment and environment
Microcomputer, Windows series operating system, eNSP software
3. Experimental content and requirements
XX company is headquartered in Beijing and has an office in Shenzhen, connecting the two places through the establishment of a network. The Beijing headquarters has 100 employees, a total of four departments, and one server; the Shenzhen office has 30 employees, and the office is not divided into departments; the router ISP indicates ISP, and LSW2 and LSW3 are three-layer switches used as the aggregation layer; LSW4, LSW5, LSW6, and LSW7 are Layer 2 switches, used as the access layer; the gateway is configured at the aggregation layer;
The ospf protocol is run between each device, and the area division is shown in the figure;
The network segments of VLAN10, VLAN20, VLAN30, VLAN40, and VLAN 50 are 192.168.10.0/24 192.168.20.0/24 192.168.30.0/24 192.168.40.0/24 192.168.50.0/24
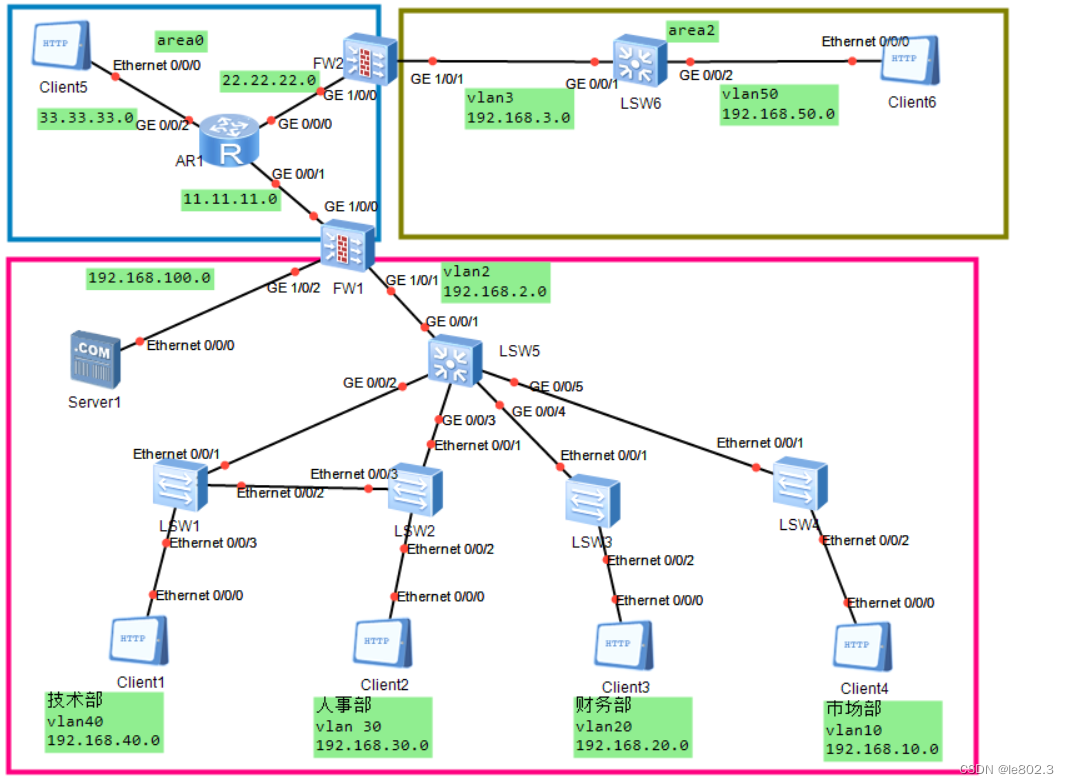
The current requirements are as follows:
- The outgoing interface address of the firewall is 11.11.11.10
- Each network segment uses the last valid address of this network segment as the gateway;
- The personnel mobility of the finance department is low, and the port security technology is used to statically bind the MAC and VLAN information of the access users; the marketing department, the personnel department and the technology department use the dynamic MAC address learning of the port security technology to ensure the legitimacy of the access users;
- RSTP technology is used between the switches of the technical department and the personnel department, and the terminal opens the edge port and BPDU protection function to prevent internal network attacks;
- The network segment of the marketing department is prohibited from pinging the server, but the server resources can be accessed;
- Prohibit the Marketing Department from visiting the Finance Department;
- Realize that the technical department, personnel department and marketing department can access the ISP, and the financial department cannot access the external network; use easy-IP technology when configuring source NAT.
- Map the intranet www server, the external mapping port is 80; the corresponding mapping address is 11.11.11.11
- Headquarters and branches are connected through IPSec VPN
4. Experimental order and results
Basic command configuration:
交换机lsw1
#
interface Ethernet0/0/1
port link-type trunk
port trunk allow-pass vlan 40
#
interface Ethernet0/0/3
port link-type access
port default vlan 40
stp edged-port enable
port-security enable
#
交换机lsw2
#
interface Ethernet0/0/2
port link-type access
port default vlan 30
port-security enable
#
#
interface Ethernet0/0/1
port link-type trunk
port trunk allow-pass vlan 30
#
交换机lsw3
#
interface Ethernet0/0/1
port link-type trunk
port trunk allow-pass vlan 20
#
interface Ethernet0/0/2
port link-type access
port default vlan 20
port-security enable
port-security mac-address sticky
#
交换机lsw4
#
interface Ethernet0/0/1
port link-type trunk
port trunk allow-pass vlan 10
#
interface Ethernet0/0/2
port link-type access
port default vlan 10
port-security enable
#
汇聚层交换机lsw5
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 40
#
interface Vlanif40
ip address 192.168.40.254 255.255.255.0
#
interface GigabitEthernet0/0/3
port link-type trunk
port trunk allow-pass vlan 30
#
interface Vlanif30
ip address 192.168.30.254 255.255.255.0
#
interface GigabitEthernet0/0/4
port link-type trunk
port trunk allow-pass vlan 20
traffic-filter outbound acl 2000
#
interface Vlanif20
ip address 192.168.20.254 255.255.255.0
#
interface GigabitEthernet0/0/5
port link-type trunk
port trunk allow-pass vlan 10
#
interface Vlanif10
ip address 192.168.10.254 255.255.255.0
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 2
traffic-filter outbound acl 3000
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 2
traffic-filter outbound acl 3000
#
interface Vlanif2
ip address 192.168.2.2 255.255.255.0
#
5. Experimental summary
In this experiment, by configuring a network topology diagram of a small and medium-sized enterprise, the network intercommunication of the intranet is realized by using the three-layer VLANIF and the configuration of the aggregation layer gateway. In order to ensure the security of the intranet, static and dynamic binding ports are configured, and rstp is used to prevent Routing loops and internal network attacks, and then configure acl to realize the access control of the department of the internal network, and map the internal network service to allow access from the external network, but cannot access the external network, and finally realize the branch and headquarters by configuring IPSec intercommunication. Among them, I think the most troublesome thing is the analysis of routing. The connectivity between various parts is realized by configuring static routing or default routing. What needs to be corrected when I reply is that I have mapped the internal network address to the public address by configuring ospf. On the Internet, this should not appear. Then there is the security protocol of the firewall. When ipsec is released, the security protocol should be restricted as much as possible to prevent external network attacks, and the security policy should be limited to the maximum extent when the tunnel is open. Finally, through the study of network security this semester, I have basically mastered the use of ensp and the configuration of various network technologies, but the shortcoming is that some basic knowledge is not solid enough. Security can go one step further.
The specific experimental report (including code) and topology diagram can be found in my resources, free download, call me if it is not free, I will not write in detail here.
6. Experiment report and topology map download link
Topology:
experimental report:
The specific experimental report (including code) and topology diagram can be found in my resources, free download, call me if it is not free, I will not write in detail here.