Creating a fake access point (honeypot)
Fake access points can be handy in many scenarios, one example is creating an open AP, this will attract a lot of clients, many of which will automatically connect to it. Then we can sniff all the traffic created by the clients that connect to it, and since its open, the traffic will not be encrypted!
In order to do this, we need two cards:
1. One connected to the Internet.
2. WiFi card to broadcast as an access point.
Clients now send requests to the hacker's wifi card, the hacker sets up his machine so that every request coming from the wifi card is forwarded to the 2nd card that's connected to the Internet.
The response comes back from the 2nd card, through the hacker's machine to the wifi card which forwards it to the client that requested it.
Tool: Man-Toolkit
Mana-Toolkit makes the whole progress very simple, it automatically creates a new AP and starts sslstrip/firelamp and even attempts to bypass HSTS which is used by Gmail and Facebook.
Mana has 3 main start scripts:
1. Start-noupstream: starts an AP with NO internet connection.
2.Start-nat-simple: this starts a regular AP using Internet connection in the upstream interface.
3.start-nat-full: starts AP with an Internet connection, it also starts sslstrip, sslsplit, firelamp and attempts to bypass HSTS.
apt-get install mana-toolkit gvim /etc/mana-toolkit/hostapd-mana.conf gvim /usr/share/mana-toolkit/run-mana/start-nat-simple.sh bash /usr/share/mana-toolkit/run-mana/start-nat-simple.sh
The first ethernet card connects to the Internet.
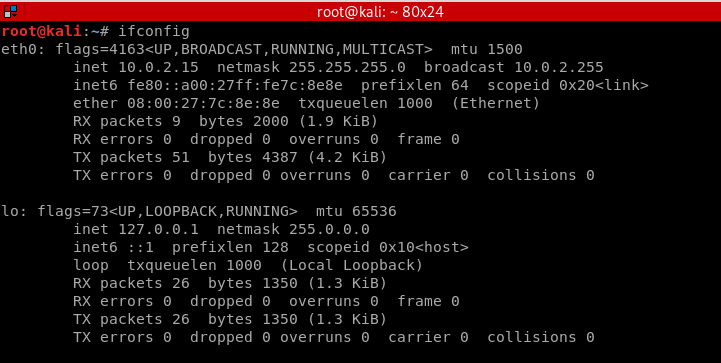
The second wifi card is ready for use.

Download and install Mana from https://github.com/sensepost/mana.
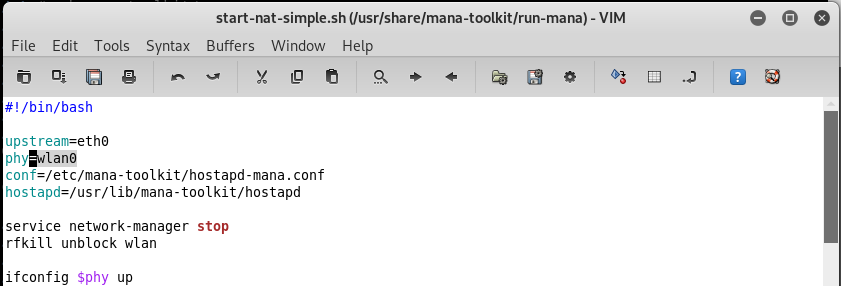
Modify the start-nat-simple.sh file.
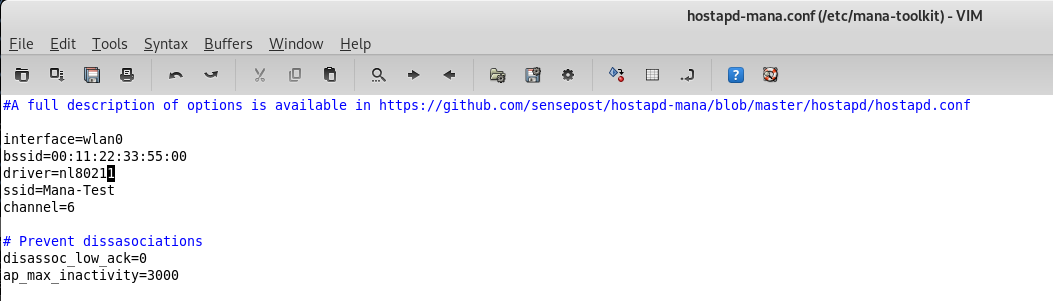
Modify the hostpad-mana.conf file.
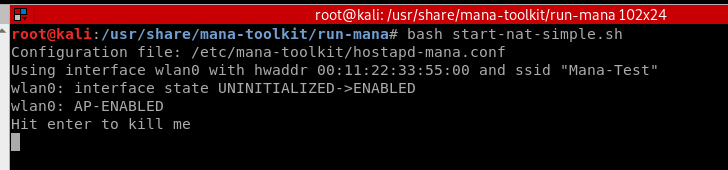
Run mana script successfully.
bash start-nat-simple.sh