搭建L2TP+IPSEC客户端需要对应的源码 xl2tpd-1.3.10和openswan,还需要一些依赖的库,gmp,libpcap。
一、安装openswan
安装依赖库gmp-6.1.2
1、下载:https://gmplib.org/#DOWNLOAD
2、配置
./configure --host=arm-hisiv100nptl-linux --with-pcap=linux --prefix=/work/my/code/vpn/L2TP/gmp/install CC=arm-hisiv100nptl-linux-gcc3、编译
make4、安装
make install
5、下载 openswan
https://download.openswan.org/openswan/old/openswan-2.6/
5、修改makefile.inc
把依赖文件gmp.h 拷贝到目录/openswan-2.6.50/include,libgmp.a 拷贝到 openswan-2.6.50/lib。
修改 Makefile.inc
#LIBGMP?=-lgmp
LIBGMP =-L /openswan-2.6.50/lib -lgmp 6、编译
make CC=arm-hisiv100nptl-linux-gcc programs 7、可能存在的错误
lex.yy.c
/work/my/code/vpn/L2TP/openswan-2.6.50/lib/libipsecconf/parser.l: In function 'parser_y_include':
/work/my/code/vpn/L2TP/openswan-2.6.50/lib/libipsecconf/parser.l:200: error: 'GLOB_BRACE' undeclared (first use in this function)
/work/my/code/vpn/L2TP/openswan-2.6.50/lib/libipsecconf/parser.l:200: error: (Each undeclared identifier is reported only once
/work/my/code/vpn/L2TP/openswan-2.6.50/lib/libipsecconf/parser.l:200: error: for each function it appears in.)
/work/my/code/vpn/L2TP/openswan-2.6.50/lib/libipsecconf/parser.l:207: error: 'GLOB_NOMAGIC' undeclared (first use in this function)
/work/my/code/vpn/L2TP/openswan-2.6.50/lib/libipsecconf/../Makefile.library:107: recipe for target 'lex.yy.o' failed解决:找到交叉编译目录中的glob.h文件,我的路径如下
/opt/hisi-linux-nptl/arm-hisiv100-linux/target/usr/include/glob.h#if ( !defined __USE_POSIX2 || defined __USE_BSD || defined __USE_GNU ) //&& defined __UCLIBC_HAS_GNU_GLOB__
# define GLOB_MAGCHAR (1 << 8)/* Set in gl_flags if any metachars seen. */
#if 1 /* uClibc gnu glob does not support these */
# define GLOB_ALTDIRFUNC (1 << 9)/* Use gl_opendir et al functions. */
# define GLOB_BRACE (1 << 10)/* Expand "{a,b}" to "a" "b". */
# define GLOB_NOMAGIC (1 << 11)/* If no magic chars, retu rn the pattern. */
# define GLOB_TILDE (1 << 12)/* Expand ~user and ~ to home directories. */
# define GLOB_ONLYDIR (1 << 13)/* Match only directories. */
# define GLOB_TILDE_CHECK (1 << 14)/* Like GLOB_TILDE but return an error
if the user name is not available. */
# define __GLOB_FLAGS (GLOB_ERR|GLOB_MARK|GLOB_NOSORT|GLOB_DOOFFS| \
GLOB_NOESCAPE|GLOB_NOCHECK|GLOB_APPEND| \
GLOB_PERIOD|GLOB_ALTDIRFUNC|GLOB_BRACE| \
GLOB_NOMAGIC|GLOB_TILDE|GLOB_ONLYDIR|GLOB_TILDE_CHECK)
#else
# define __GLOB_FLAGS (GLOB_ERR|GLOB_MARK|GLOB_NOSORT|GLOB_DOOFFS| \
GLOB_NOESCAPE|GLOB_NOCHECK|GLOB_APPEND| \
GLOB_PERIOD)
#endif
#else
# define __GLOB_FLAGS (GLOB_ERR|GLOB_MARK|GLOB_NOSORT|GLOB_DOOFFS| \
GLOB_NOESCAPE|GLOB_NOCHECK|GLOB_APPEND| \
注释掉://&& defined __UCLIBC_HAS_GNU_GLOB__
8、安装
修改Makefile.inc
#INC_USRLOCAL=/usr/local
INC_USRLOCAL=/work/my/code/vpn/L2TP/openswan_client/install这里修改成自己安装的目录。
make installa、拷贝虚拟机中的脚本/etc/init.d/ipsec到设备目录/etc/init.d/中,做如下修改。
IPSEC_EXECDIR="${IPSEC_EXECDIR-/usr/local/libexec/ipsec}"
IPSEC_LIBDIR="${IPSEC_LIBDIR-/usr/local/lib/ipsec}"
IPSEC_SBINDIR="${IPSEC_SBINDIR-/usr/local/sbin}"
IPSEC_CONFS="${IPSEC_CONFS-/etc}"修改为:
IPSEC_EXECDIR="${IPSEC_EXECDIR-/usr/libexec/ipsec}"
IPSEC_LIBDIR="${IPSEC_LIBDIR-/usr/lib/ipsec}"
IPSEC_SBINDIR="${IPSEC_SBINDIR-/usr/sbin}"
IPSEC_CONFS="${IPSEC_CONFS-/etc}"b、拷贝安装生成的几个目录到设备上,如lib 、libexec、sbin/ipsec
root@ubuntu16:/work/my/code/vpn/L2TP/openswan_client/install# ls
lib libexec man sbin share根据启动脚本/etc/init.d/ipsec,我们做如下具体的拷贝
目录lib、libexec拷贝到设备/usr目录中
脚本sbin/ipsec拷贝到设备/usr/sbin/中,拷贝完也要做如下修改
IPSEC_EXECDIR="${IPSEC_EXECDIR-/usr/libexec/ipsec}"
IPSEC_LIBDIR="${IPSEC_LIBDIR-/usr/lib/ipsec}"
IPSEC_SBINDIR="${IPSEC_SBINDIR-/usr/sbin}"
IPSEC_CONFS="${IPSEC_CONFS-/etc}"10、添加配置文件
a、/etc/ipsec.conf
内容如下:
config setup
nat_traversal=yes
virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/12
oe=off
protostack=netkey
conn L2TP-PSK-NAT
rightsubnet=vhost:%priv
also=L2TP-PSK-noNAT
conn L2TP-PSK-noNAT
authby=secret
pfs=no
auto=add
keyingtries=3
rekey=no
ikelifetime=8h
keylife=1h
type=transport
left=192.168.9.166
leftprotoport=17/1701
right=192.168.9.161
rightprotoport=17/1701
type 有三种模式 transport、 tunnel、beet,这里选择是transport。left是本地地址,leftprotoport是端口号使用1701端口。right是要连接服务器对应的地址,rightProtoport对应的端口号。
b、/etc/ipsec.secrets
添加内容如下:
192.168.9.166 192.168.9.161: PSK "l2tp_123456789"192.168.9.166是本地地址,也可以用%any代替,192.168.9.161是对应服务器的地址,PSK是预共享秘钥。这个要跟服务器设置要相同。
二、安装xl2tpd
安装依赖库libpcap-1.8.1
1、下载:http://www.linuxfromscratch.org/blfs/view/svn/basicnet/libpcap.html
2、配置
./configure --host=arm-hisiv100nptl-linux --with-pcap=linux --prefix=/work/my/code/vpn/L2TP/libpcap/install CC=arm-hisiv100nptl-linux-gcc 3、编译
make4、安装
make install5、下载xl2tpd-1.3.10
https://www.xelerance.com/archives/147
6、修改Makefile
a、添加变量
LIBSRC ?= b、添加变量$(LIBSRC)
$(CC) $(LDFLAGS) -o pfc -L $(LIBSRC) pfc.o -lpcap $(LDLIBS)
7、编译
make CC=arm-hisiv100nptl-linux-gcc KERNELSRC=/work/my/code/vpn/L2TP/libpcap/install LIBSRC=/work/my/code/vpn/L2TP/libpcap/install/lib8、配置文件
a、添加/etc/xl2tpd/xl2tpd.conf,内容如下
[global]
listen-addr = 192.168.9.166
auth file=/etc/ppp/chap-secrets
[lac l2tp]
lns = 192.168.9.161
redial = yes
redial timeout = 15
require chap = yes
refuse pap = yes
require authentication = yes
name = 2018
ppp debug = yes
pppoptfile = /etc/ppp/peers/options.l2tpd.client
length bit = yeslns 是服务器的地址,name是登录名
b、添加/etc/ppp/chap-secrets,内容如下。
# Secrets for authentication using CHAP
# client server secret IP addresses
2018 * 123 *2018客户端登录名,123登录密码,其他的用*替代。
c、添加/etc/ppp/peers/options.l2tpd.client,内容如下
asyncmap 0
noauth
crtscts
lock
hide-password
modem
netmask 255.255.255.0
proxyarp
lcp-echo-interval 30
lcp-echo-failure 4
ipcp-accept-local
ipcp-accept-remote三、ppp
PPP是一个拨号软件,用来提供用户登录的用户名和密码验证用的。PPTP搭建的VPN也会用到PPP。所以,实际上,PPTP和L2TP是可以共存在一台服务器上的,而且它们还可以共享用户登录账号信息,因为它们都用PPP作为用户登录连接。
所以没有安装可以参考前面pptp客户端配置的文章
https://blog.csdn.net/u011425939/article/details/80498534
四、内核配置
一般情况内核没有默认把ipsec的模式编译进内核的,所以需要把内核中的的对应ipsec选项打开,不然会出现如下问题。
# ipsec auto --up L2TP-PSK-noNAT
002 "L2TP-PSK-noNAT" #1: initiating Main Mode
105 "L2TP-PSK-noNAT" #1: STATE_MAIN_I1: initiate
003 "L2TP-PSK-noNAT" #1: received Vendor ID payload [Openswan (this version) 2.6.50 ]
003 "L2TP-PSK-noNAT" #1: received Vendor ID payload [Dead Peer Detection]
003 "L2TP-PSK-noNAT" #1: received Vendor ID payload [RFC 3947] method set to=115
002 "L2TP-PSK-noNAT" #1: enabling possible NAT-traversal with method RFC 3947 (NAT-Traversal)
002 "L2TP-PSK-noNAT" #1: transition from state STATE_MAIN_I1 to state STATE_MAIN_I2
107 "L2TP-PSK-noNAT" #1: STATE_MAIN_I2: sent MI2, expecting MR2
003 "L2TP-PSK-noNAT" #1: NAT-Traversal: Result using draft-ietf-ipsec-nat-t-ike (MacOS X): no NAT detected
002 "L2TP-PSK-noNAT" #1: transition from state STATE_MAIN_I2 to state STATE_MAIN_I3
109 "L2TP-PSK-noNAT" #1: STATE_MAIN_I3: sent MI3, expecting MR3
003 "L2TP-PSK-noNAT" #1: received Vendor ID payload [CAN-IKEv2]
002 "L2TP-PSK-noNAT" #1: Main mode peer ID is ID_IPV4_ADDR: '192.168.9.161'
002 "L2TP-PSK-noNAT" #1: transition from state STATE_MAIN_I3 to state STATE_MAIN_I4
004 "L2TP-PSK-noNAT" #1: STATE_MAIN_I4: ISAKMP SA established {auth=OAKLEY_PRESHARED_KEY oursig= theirsig= cipher=aes_128 prf=oakley_sha group=modp2048}
002 "L2TP-PSK-noNAT" #2: initiating Quick Mode PSK+ENCRYPT+DONTREKEY+UP+IKEv2ALLOW+SAREFTRACK {using isakmp#1 msgid:82227a67 proposal=defaults pfsgroup=no-pfs}
118 "L2TP-PSK-noNAT" #2: STATE_QUICK_I1: initiate
003 "L2TP-PSK-noNAT" #2: ERROR: netlink response for Add SA [email protected] included errno 93: Protocol not supported
003 "L2TP-PSK-noNAT" #2: state #2: failed to setup outgoing SA
032 "L2TP-PSK-noNAT" #2: STATE_QUICK_I1: internal error这里有个错误93, 说没有SA 和ESP 协议支持,所以需要把它在内核中打开。步骤如下。
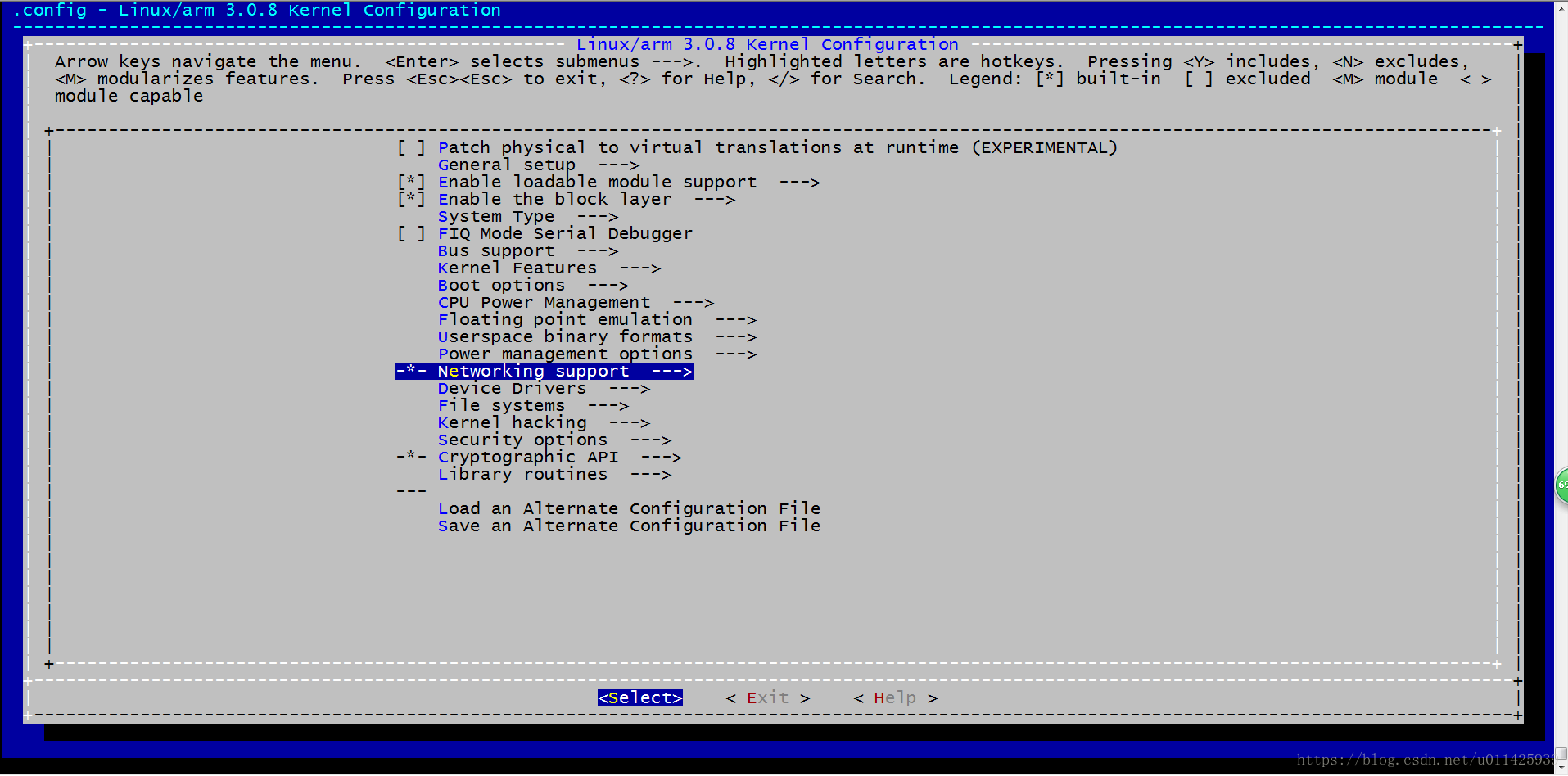
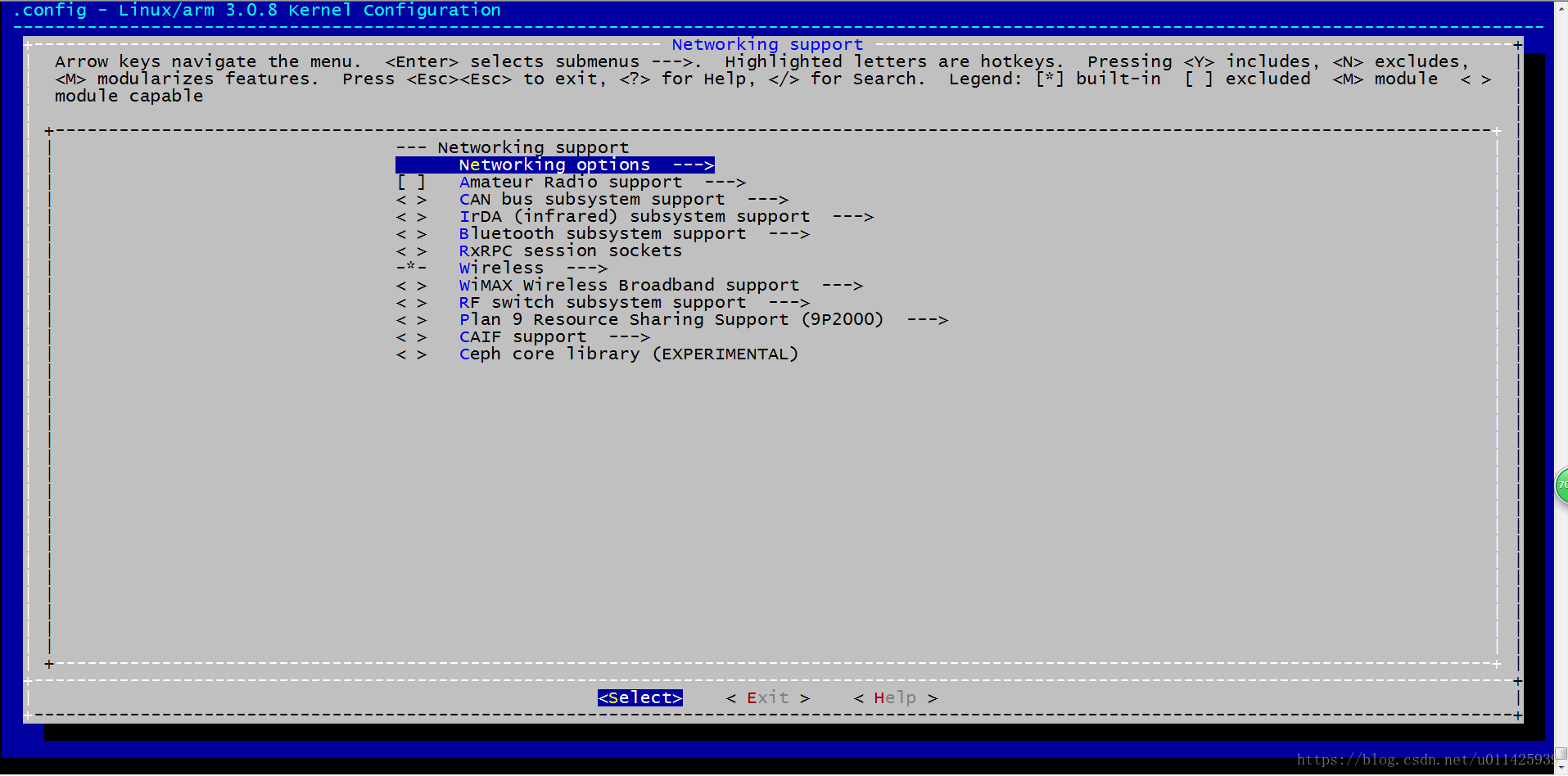
a、Networking support
b、 Networking options
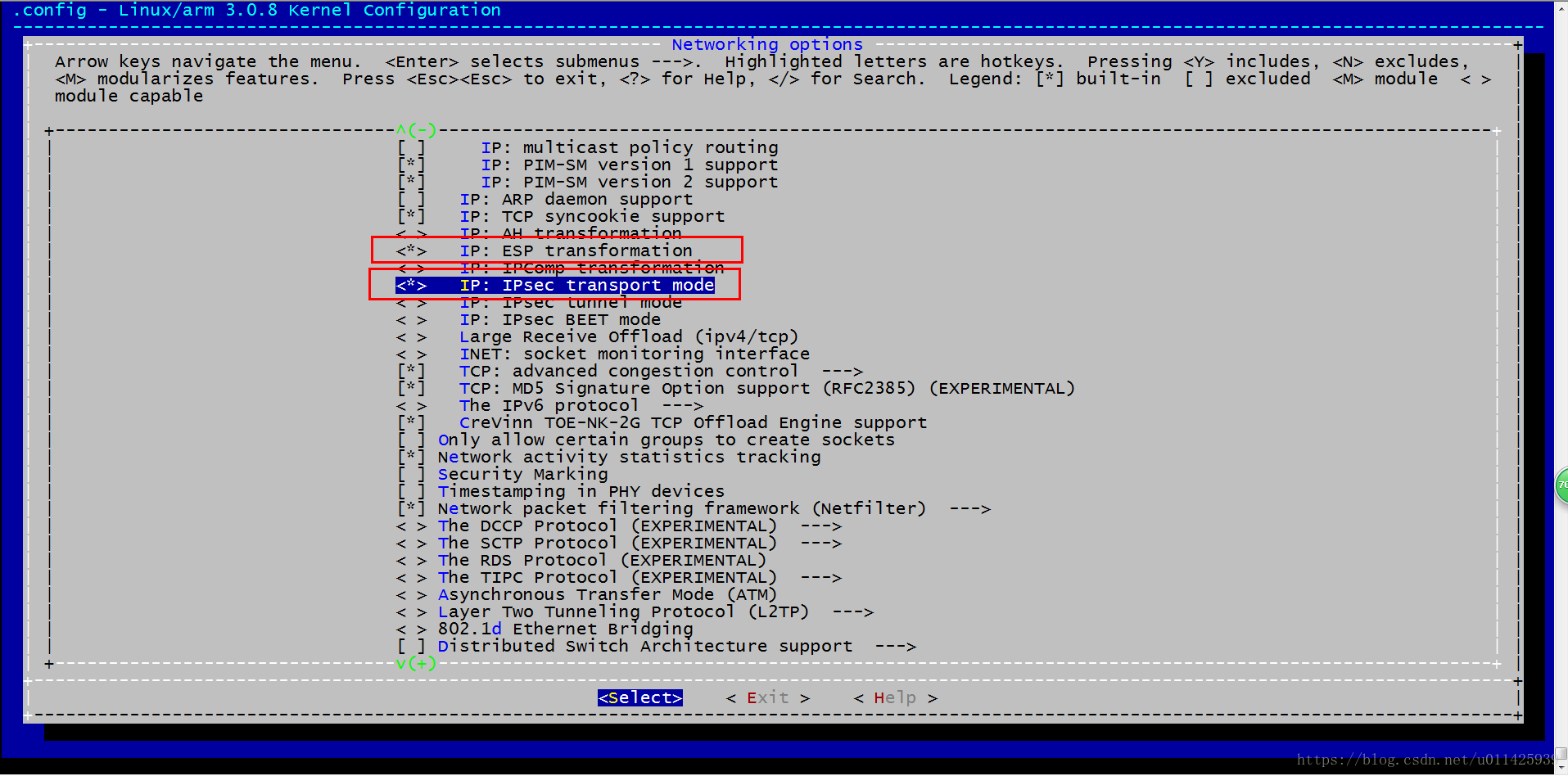
c、找到这个两个选项。
这里选择的是transport 模式 ESP 转换,因为我们在配置文件/etc/ipsec.conf中type就是transport,这个也可以把ipsec的选项都选择。然后去尝试每种模式。但这里只需这个两个选项就可以 了。
d、编译
make
e、下载内核
这里也可以不用下载内核,直接把那两个选项编译成模块的方式,然后用insmod命令方式加载到内核中。
五、连接服务器
这个服务器我使用的是前面文章在Ubuntu中搭建的l2tp+ipsec服务器,所以有很多配置都是跟从这个服务器来配置的。链接
https://blog.csdn.net/u011425939/article/details/80525380
a、首先启动ipsec
ipsec setup start还有其他的命令使用help查看
# ipsec setup --help
Usage: ipsec setup {start|stop|restart|reload|force-reload|condrestart|try-restart|status|version}# ipsec setup restart
ipsec_setup: Stopping Openswan IPsec...
ipsec_setup: Removing orphaned /var/run/pluto/pluto.pid:
ipsec_setup: Starting Openswan IPsec U2.6.50/K3.0.8...
ipsec_setup: ipsec_setup: WARNING: cannot flush state/policy database -- `%defaultroute'. Install a newer version of iproute/iproute2 or install the ipsec-tools package to obtain the setkey command.b、启动xl2tpd
xl2tpd -D以调试的方式启动
# xl2tpd -D
xl2tpd[27109]: setsockopt recvref[30]: Protocol not available
xl2tpd[27109]: L2TP kernel support not detected (try modprobing l2tp_ppp and pppol2tp)
xl2tpd[27109]: xl2tpd version xl2tpd-1.3.10 started on (none) PID:27109
xl2tpd[27109]: Written by Mark Spencer, Copyright (C) 1998, Adtran, Inc.
xl2tpd[27109]: Forked by Scott Balmos and David Stipp, (C) 2001
xl2tpd[27109]: Inherited by Jeff McAdams, (C) 2002
xl2tpd[27109]: Forked again by Xelerance (www.xelerance.com) (C) 2006-2016
xl2tpd[27109]: Listening on IP address 192.168.9.166, port 1701# ipsec auto --up L2TP-PSK-noNAT
002 "L2TP-PSK-noNAT" #1: initiating Main Mode
105 "L2TP-PSK-noNAT" #1: STATE_MAIN_I1: initiate
003 "L2TP-PSK-noNAT" #1: received Vendor ID payload [Openswan (this version) 2.6.50 ]
003 "L2TP-PSK-noNAT" #1: received Vendor ID payload [Dead Peer Detection]
003 "L2TP-PSK-noNAT" #1: received Vendor ID payload [RFC 3947] method set to=115
002 "L2TP-PSK-noNAT" #1: enabling possible NAT-traversal with method RFC 3947 (NAT-Traversal)
002 "L2TP-PSK-noNAT" #1: transition from state STATE_MAIN_I1 to state STATE_MAIN_I2
107 "L2TP-PSK-noNAT" #1: STATE_MAIN_I2: sent MI2, expecting MR2
003 "L2TP-PSK-noNAT" #1: NAT-Traversal: Result using draft-ietf-ipsec-nat-t-ike (MacOS X): no NAT detected
002 "L2TP-PSK-noNAT" #1: transition from state STATE_MAIN_I2 to state STATE_MAIN_I3
109 "L2TP-PSK-noNAT" #1: STATE_MAIN_I3: sent MI3, expecting MR3
003 "L2TP-PSK-noNAT" #1: received Vendor ID payload [CAN-IKEv2]
002 "L2TP-PSK-noNAT" #1: Main mode peer ID is ID_IPV4_ADDR: '192.168.9.161'
002 "L2TP-PSK-noNAT" #1: transition from state STATE_MAIN_I3 to state STATE_MAIN_I4
004 "L2TP-PSK-noNAT" #1: STATE_MAIN_I4: ISAKMP SA established {auth=OAKLEY_PRESHARED_KEY oursig= theirsig= cipher=aes_128 prf=oakley_sha group=modp2048}
002 "L2TP-PSK-noNAT" #2: initiating Quick Mode PSK+ENCRYPT+DONTREKEY+UP+IKEv2ALLOW+SAREFTRACK {using isakmp#1 msgid:210b70d9 proposal=defaults pfsgroup=no-pfs}
118 "L2TP-PSK-noNAT" #2: STATE_QUICK_I1: initiate
002 "L2TP-PSK-noNAT" #2: transition from state STATE_QUICK_I1 to state STATE_QUICK_I2
004 "L2TP-PSK-noNAT" #2: STATE_QUICK_I2: sent QI2, IPsec SA established transport mode {ESP=>0xaa65c77e <0xd326843a xfrm=AES_128-HMAC_SHA1 NATOA=none NATD=none DPD=none}d、echo 'c l2tp' > /var/run/xl2tpd/l2tp-control
这个l2tp 是/etc/xl2tpd/xl2tpd.conf 中的[lac l2tp]
e、如果连接成功会出现一个虚拟的pppx网卡,如下
# ifconfig
eth0 Link encap:Ethernet HWaddr C2:4F:B4:B3:97:D7
inet addr:192.168.9.166 Bcast:192.168.9.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:8371743 errors:0 dropped:3307 overruns:0 frame:0
TX packets:4276852 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:2476538003 (2.3 GiB) TX bytes:248606867 (237.0 MiB)
Interrupt:119
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:4800 errors:0 dropped:0 overruns:0 frame:0
TX packets:4800 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:10056240 (9.5 MiB) TX bytes:10056240 (9.5 MiB)
ppp0 Link encap:Point-to-Point Protocol
inet addr:192.168.223.100 P-t-P:192.168.223.10 Mask:255.255.255.255
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1410 Metric:1
RX packets:3 errors:0 dropped:0 overruns:0 frame:0
TX packets:4 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:3
RX bytes:42 (42.0 B) TX bytes:69 (69.0 B)参考文章:http://blog.sina.com.cn/s/blog_9704e09601013quu.html