网上关于 纯 l2tp 协议 移植、配置的博文很多,本次移植与测试时看了很多,把 l2tp 协议、网络结构与配置对应关系说清楚、并验证通过的真实记录很少,本篇以实践过程记录为主线,简介 l2tp 与ppp的原理。
L2TP(Layer 2 Tunneling Protocol) VPN是一种用于承载PPP报文的隧道技术;使用L2TP VPN隧道“承载”PPP报文在Internet上传输有多种方式,1、通过传统拨号方式接入Internet,2、以太网方式接入Internet。
PPP(Point-to-Point Protocol),链路层协议。PPP是为了在点对点物理链路(例如RS232串口链路、电话ISDN线路等)上传输OSI模型中的网络层报文而设计的,它改进了之前的一个点对点协议-SLIP协议–只能同时运行一个网络协议、无容错控制、无授权等许多缺陷,PPP是现在最流行的点对点链路控制协议。
ppp与l2tp 协议间的关系,可参考下图:
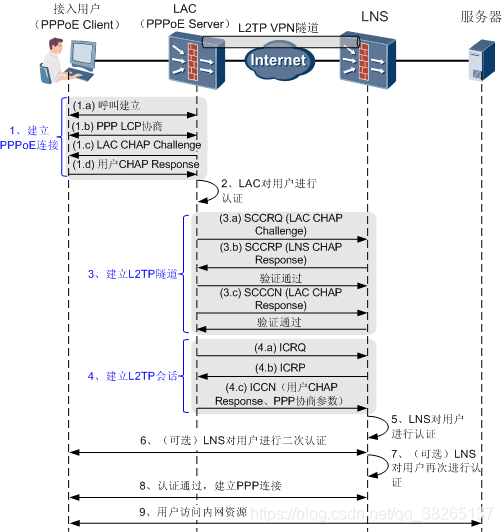
用户通过PPPoE方式发起建立连接指令,其本质就是:
echo “c vpn” > /var/run/xl2tpd/l2tp-control 启动 l2tp vpn 的控制程序,程序中采用 PPPoL2TP 的方式,与 L2TP 的服务器进行鉴权、协商并建立 l2tp vpn 隧道,建成后的隧道在操作系统中体现方式:虚拟的网络设备PPP 网卡。
- l2tp 移植
1.1) 配置 xl2tpd 软件包及依赖库
本文嵌入式系统为新唐nuc980 的 arm9 硬件平台,采用 buildroot 方式移植 xl2tp 软件包,linux版本:4.4.200 ;
menuconfig中配置参数如下:
-> Target packages
-> Networking applications
-*- pppd
[*] filtering
[*] radius
[*] xl2tp
依赖库配置:
-> Target packages
-> Libraries
-> Networking
-*- libpcap
-> Target packages
-> Libraries
-> Crypto
-*- openssl
[*] openssl binary
[*] openssl additional engines
编译生成image 和 rootfs 镜像文件,在目标机上配置 xl2tpd 的参数。nuc980 作为 xl2tpd 的服务器端,ubuntu 16 做为客户端。
1.2)配置 /etc/init.d/xl2tpd 启动脚本
参考配置文件路径:
build-2016/package/xl2tp$ cat xl2tpd
内容如下:
#!/bin/sh
#
PATH=/bin:/usr/bin:/sbin:/usr/sbin
DAEMON=/usr/sbin/xl2tpd
PIDFILE=/var/run/xl2tpd.pid
test -f $DAEMON || exit 0
case "$1" in
start)
start-stop-daemon -S -p $PIDFILE -x $DAEMON -- -D &
;;
stop)
start-stop-daemon -K -p $PIDFILE -x $DAEMON
;;
restart|force-reload)
start-stop-daemon -K -p $PIDFILE -x $DAEMON
sleep 1
start-stop-daemon -S -p $PIDFILE -x $DAEMON
;;
*)
echo "Usage: /etc/init.d/xl2tdp {start|stop|restart|force-reload}"
exit 1
;;
esac
exit 0
把此文件脚本,拷贝至rootfs系统下: /etc/init.d/xl2tpd,赋予执行权限.
chmod 755 xl2tpd
- 服务器端的参数配置
本次实验采用的 xl2tpd ,服务器端内容配置如下。
2.1) 配置 /etc/xl2tpd # cat xl2tpd.conf
[global]
port =1701
ipsec saref = no
access control = no
auth file=/etc/xl2tpd/l2tp-secrets
debug network = yes
debug state = yes
debug packet = yes
debug tunnel = yes
[lns default]
exclusive = yes
ip range = 100.0.0.100-100.0.0.200
local ip = 100.0.0.10
refuse pap = yes
; require authentication = yes
require chap = yes
name = vpnServer
ppp debug = yes
pppoptfile = /etc/ppp/option.l2tpd.lns
length bit = yes
1.2) xl2tpd 的客户端登录认证用户名 缺省文件
/etc/xl2tpd # cat l2tp-secrets ,此文件并没有使能内容。
# Secrets for authenticating l2tp tunnels
# us them secret
# * marko blah2
# zeus marko blah
# * * interop
1.3) xl2tpd服务端ppp通讯参数
/etc/ppp # cat option.l2tpd.lns
#ktune
#ipcp-accept-local
#ipcp-accept-remote
#ms-dns 8.8.8.8
lock
noauth
dump
logfd 2
require-mschap-v2
ms-dns 192.168.123.111 # 给拔号用户分配 dns 服务器地址
lcp-echo-interval 10
lcp-echo-failure 3
#noccp
#auth
#nocrtscts
#idle 1800
#mtu 1500
#mru 1500
#nodefaultroute
#debug
#nolock
#logfile /var/log/ppp.log # 日志文件路径
#proxyarp
#connect-delay 5000
#kdebug 2
#record /var/log/pppd.log
#receive-all
#refuse-chap
#refuse-pap
3.客户端的参数配置
3.1) xl2tp 客户端配置参数
robot@ubuntu: /etc/xl2tpd$ cat xl2tpd.conf
[global]
port =1701
auth file=/etc/xl2tpd/l2tp-secrets
debug network = yes
debug tunnel = yes
debug state = yes
debug packet = yes
[lac vpn]
name = robot ;L2TP的账号
lns = 192.168.123.111 ;L2TP的服务器IP
pppoptfile = /etc/ppp/peers/testvpn.l2tpd ;PPPD拨号配置文件
ppp debug = yes
redial = yes
redial timeout = 15
require chap = yes
refuse pap = yes
require authentication = yes
length bit =yes
rx bps = 100000000
tx bps = 100000000
3.2)xl2tp 鉴权文件,客户端未启用
robot@ubuntu:/etc/xl2tpd$ sudo cat l2tp-secrets
# Secrets for authenticating l2tp tunnels
# us them secret
# * marko blah2
# zeus marko blah
# * * interop
3.3)ppp拨号文件配置内容
robot@ubuntu:/etc/ppp/peers$ sudo cat testvpn.l2tpd
remotename default
user "robot"
password "123"
unit 0
nodeflate
nobsdcomp
noauth
persist
nopcomp
noaccomp
maxfail 5
debug
- 实验参数记录
4.1)启动服务器端命令
/etc/xl2tpd # xl2tpd -C xl2tpd.conf -D
显示内容如下
xl2tpd[1364]: IPsec SAref does not work with L2TP kernel mode yet, enabling force userspace=yes
xl2tpd[1364]: setsockopt recvref[30]: Protocol not available
xl2tpd[1364]: Not looking for kernel support.
xl2tpd[1364]: xl2tpd version xl2tpd-1.3.6 started on (none) PID:1364
xl2tpd[1364]: Written by Mark Spencer, Copyright (C) 1998, Adtran, Inc.
xl2tpd[1364]: Forked by Scott Balmos and David Stipp, (C) 2001
xl2tpd[1364]: Inherited by Jeff McAdams, (C) 2002
xl2tpd[1364]: Forked again by Xelerance (www.xelerance.com) (C) 2006
xl2tpd[1364]: Listening on IP address 0.0.0.0, port 1701
xl2tpd[1364]: network_thread: recv packet from 192.168.123.88, size = 103, tunnel = 0, call = 0 ref=0 refhim=0
4.2)启动客户端命令
root@ubuntu:/etc/xl2tpd# service xl2tpd restart #重启xl2tpd服务
root@ubuntu:/etc/xl2tpd# echo “c vpn” > /var/run/xl2tpd/l2tp-control #启动l2tp登录、触发ppp连接
root@ubuntu:/etc/xl2tpd# ifconfig
ens33 Link encap:Ethernet HWaddr 00:0c:29:54:7b:a5
inet addr:192.168.123.88 Bcast:192.168.123.255 Mask:255.255.255.0
inet6 addr: fe80::42db:54c2:99b8:c1d8/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:8223 errors:0 dropped:0 overruns:0 frame:0
TX packets:3778 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:3051947 (3.0 MB) TX bytes:346937 (346.9 KB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:834 errors:0 dropped:0 overruns:0 frame:0
TX packets:834 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:64959 (64.9 KB) TX bytes:64959 (64.9 KB)
ppp0 Link encap:Point-to-Point Protocol
inet addr:100.0.0.100 P-t-P:100.0.0.10 Mask:255.255.255.255
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:7 errors:0 dropped:0 overruns:0 frame:0
TX packets:7 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:3
RX bytes:69 (69.0 B) TX bytes:63 (63.0 B)
查询客户端 xl2tp 运行日志如下
root@ubuntu:/etc/xl2tpd# systemctl status xl2tpd.service
● xl2tpd.service - LSB: layer 2 tunelling protocol daemon
Loaded: loaded (/etc/init.d/xl2tpd; bad; vendor preset: enabled)
Active: active (running) since Sat 2021-01-02 09:40:06 CST; 20min ago
Docs: man:systemd-sysv-generator(8)
Process: 3844 ExecStop=/etc/init.d/xl2tpd stop (code=exited, status=0/SUCCESS)
Process: 3879 ExecStart=/etc/init.d/xl2tpd start (code=exited, status=0/SUCCESS)
CGroup: /system.slice/xl2tpd.service
├─3884 /usr/sbin/xl2tpd
└─5101 /usr/sbin/pppd passive nodetach : refuse-pap auth require-chap name robot debug file /etc/ppp/peers/testvpn.l2tpd plugin pppol2tp.so pppol2tp 8 # !!!采用 pppol2tp 的拨号方式
Jan 02 09:59:47 ubuntu pppd[5101]: rcvd [LCP EchoRep id=0x7 magic=0x5d9a7049]
Jan 02 09:59:47 ubuntu pppd[5101]: rcvd [LCP EchoReq id=0x15 magic=0x5d9a7049]
Jan 02 09:59:47 ubuntu pppd[5101]: sent [LCP EchoRep id=0x15 magic=0xcda959de]
Jan 02 09:59:57 ubuntu pppd[5101]: rcvd [LCP EchoReq id=0x16 magic=0x5d9a7049]
Jan 02 09:59:57 ubuntu pppd[5101]: sent [LCP EchoRep id=0x16 magic=0xcda959de]
Jan 02 10:00:07 ubuntu pppd[5101]: rcvd [LCP EchoReq id=0x17 magic=0x5d9a7049]
Jan 02 10:00:07 ubuntu pppd[5101]: sent [LCP EchoRep id=0x17 magic=0xcda959de]
Jan 02 10:00:14 ubuntu xl2tpd[3884]: network_thread: recv packet from 192.168.91.45, size = 20, tunnel = 50916, call = 0 ref=0 refhim=0
Jan 02 10:00:14 ubuntu xl2tpd[3884]: control_finish: message type is Hello(6). Tunnel is 34227, call is 0.
Jan 02 10:00:14 ubuntu xl2tpd[3884]: network_thread: recv packet from 192.168.91.45, size = 12, tunnel = 50916, call = 0 ref=0 refhim=0
4.3) 服务器端调试信息
xl2tp 服务器端调试打印信息如下
packet dump:
HEX: {
02 C8 67 00 00 00 00 00 00 00 00 00 80 08 00 00 00 00 00 01 80 08 00 00 00 02 01 00 80 0A 00 00 00 03 00 00 00 03 80 0A 00 00 00 04 00 00 00 00 00 08 00 00 00 06 06 90 80 0C 00 00 00 07 75 62 75 6E 74 75 00 13 00 00 00 08 78 65 6C 65 72 61 6E 63 65 2E 63 6F 6D 80 08 00 00 00 09 10 14 80 08 00 00 00 0A 00 04 }
ASCII: {
g ubuntu xelerance.com }
xl2tpd[1364]: get_call: allocating new tunnel for host 192.168.123.88, port 1701.
xl2tpd[1364]: control_finish: message type is Start-Control-Connection-Request(1). Tunnel is 4116, call is 0.
packet dump:
HEX: {
C8 02 00 67 10 14 00 00 00 00 00 01 80 08 00 00 00 00 00 02 80 08 00 00 00 02 01 00 80 0A 00 00 00 03 00 00 00 03 80 0A 00 00 00 04 00 00 00 00 00 08 00 00 00 06 06 90 80 0C 00 00 00 07 28 6E 6F 6E 65 29 00 13 00 00 00 08 78 65 6C 65 72 61 6E 63 65 2E 63 6F 6D 80 08 00 00 00 09 D7 3E 80 08 00 00 00 0A 00 04 }
ASCII: {
g (none) xelerance.com > }
xl2tpd[1364]: control_finish: sending SCCRP
xl2tpd[1364]: network_thread: recv packet from 192.168.123.88, size = 20, tunnel = 55102, call = 0 ref=0 refhim=0
packet dump:
HEX: {
02 C8 14 00 3E D7 00 00 01 00 01 00 80 08 00 00 00 00 00 03 }
ASCII: {
> }
xl2tpd[1364]: control_finish: message type is Start-Control-Connection-Connected(3). Tunnel is 4116, call is 0.
xl2tpd[1364]: Connection established to 192.168.123.88, 1701. Local: 55102, Remote: 4116 (ref=0/0). LNS session is 'default'
xl2tpd[1364]: network_thread: recv packet from 192.168.123.88, size = 48, tunnel = 55102, call = 0 ref=0 refhim=0
packet dump:
HEX: {
02 C8 30 00 3E D7 00 00 02 00 01 00 80 08 00 00 00 00 00 0A 80 08 00 00 00 0E 55 79 80 0A 00 00 00 0F 00 00 00 02 80 0A 00 00 00 12 00 00 00 00 }
ASCII: {
0 > Uy }
xl2tpd[1364]: control_finish: message type is Incoming-Call-Request(10). Tunnel is 4116, call is 0.
packet dump:
HEX: {
C8 02 00 1C 10 14 55 79 00 01 00 03 80 08 00 00 00 00 00 0B 80 08 00 00 00 0E FC F8 }
ASCII: {
Uy }
xl2tpd[1364]: control_finish: Sending ICRP
xl2tpd[1364]: network_thread: recv packet from 192.168.123.88, size = 50, tunnel = 55102, call = 64760 ref=0 refhim=0
packet dump:
HEX: {
02 C8 32 00 3E D7 F8 FC 03 00 02 00 80 08 00 00 00 00 00 0C 80 0A 00 00 00 18 05 F5 E1 00 80 0A 00 00 00 13 00 00 00 01 00 0A 00 00 00 26 05 F5 E1 00 }
ASCII: {
2 > & }
xl2tpd[1364]: control_finish: message type is Incoming-Call-Connected(12). Tunnel is 4116, call is 21881.
xl2tpd[1364]: start_pppd: I'm running:
xl2tpd[1364]: "/usr/sbin/pppd"
xl2tpd[1364]: "passive"
xl2tpd[1364]: "nodetach"
xl2tpd[1364]: "100.0.0.10:100.0.0.100"
xl2tpd[1364]: "refuse-pap"
xl2tpd[1364]: "name"
xl2tpd[1364]: "vpnServer"
xl2tpd[1364]: "debug"
xl2tpd[1364]: "file"
xl2tpd[1364]: "/etc/ppp/option.l2tpd.lns"
xl2tpd[1364]: "/dev/pts/1"
xl2tpd[1364]: Call established with 192.168.123.88, Local: 64760, Remote: 21881, Serial: 2
xl2tpd[1364]: network_thread: recv packet from 192.168.123.88, size = 26, tunnel = 55102, call = 64760 ref=0 refhim=0
packet dump:
HEX: {
02 00 3E D7 F8 FC FF 03 C0 21 01 01 00 10 02 06 00 00 00 00 05 06 B4 EE 9B D9 }
ASCII: {
> ! }
pppd options in effect:
debug # (from command line)
nodetach # (from command line)
logfd 2 # (from /etc/ppp/option.l2tpd.lns)
dump # (from /etc/ppp/option.l2tpd.lns)
require-mschap-v2 # (from /etc/ppp/option.l2tpd.lns)
refuse-pap # (from command line)
name vpnServer # (from command line)
/dev/pts/1 # (from command line)
lock # (from /etc/ppp/option.l2tpd.lns)
passive # (from command line)
lcp-echo-failure 3 # (from /etc/ppp/option.l2tpd.lns)
lcp-echo-interval 10 # (from /etc/ppp/option.l2tpd.lns)
ms-dns xxx # [don't know how to print value] # (from /etc/ppp/option.l2tpd.lns)
100.0.0.10:100.0.0.100 # (from command line)
using channel 3
Using interface ppp0
Connect: ppp0 <--> /dev/pts/1
sent [LCP ConfReq id=0x1 <asyncmap 0x0> <auth chap MS-v2> <magic 0xba036f5d> <pcomp> <accomp>]
packet dump:
HEX: {
40 02 00 25 10 14 55 79 FF 03 C0 21 01 01 00 19 02 06 00 00 00 00 03 05 C2 23 81 05 06 BA 03 6F 5D 07 02 08 02 }
ASCII: {
@ % Uy ! # o] }
xl2tpd[1364]: network_thread: recv packet from 192.168.123.88, size = 35, tunnel = 55102, call = 64760 ref=0 refhim=0
packet dump:
HEX: {
02 00 3E D7 F8 FC FF 03 C0 21 02 01 00 19 02 06 00 00 00 00 03 05 C2 23 81 05 06 BA 03 6F 5D 07 02 08 02 }
ASCII: {
> ! # o] }
rcvd [LCP ConfAck id=0x1 <asyncmap 0x0> <auth chap MS-v2> <magic 0xba036f5d> <pcomp> <accomp>]
xl2tpd[1364]: network_thread: select timeout
xl2tpd[1364]: network_thread: select timeout
xl2tpd[1364]: network_thread: recv packet from 192.168.123.88, size = 26, tunnel = 55102, call = 64760 ref=0 refhim=0
packet dump:
HEX: {
02 00 3E D7 F8 FC FF 03 C0 21 01 01 00 10 02 06 00 00 00 00 05 06 B4 EE 9B D9 }
ASCII: {
> ! }
rcvd [LCP ConfReq id=0x1 <asyncmap 0x0> <magic 0xb4ee9bd9>]
sent [LCP ConfAck id=0x1 <asyncmap 0x0> <magic 0xb4ee9bd9>]
packet dump:
HEX: {
sent [LCP EchoReq id=0x0 magic=0xba036f5d]
40 02 00 1C 10 14 55 79 FF 03 C0 21 02 01 00 10 02 06 00 00 00 00 05 06 B4 EE 9B D9 }
ASCII: {
@ Uy ! }
packet dump:
HEX: {
40 02 00 14 10 14 55 79 FF 03 C0 21 09 00 00 08 BA 03 6F 5D }
ASCII: {
@ Uy ! o]}
xl2tpd[1364]: network_thread: recv packet from 192.168.123.88, size = 18, tunnel = 55102, call = 64760 ref=0 refhim=0
packet dump:
HEX: {
02 00 3E D7 F8 FC FF 03 C0 21 09 00 00 08 B4 EE 9B D9 }
ASCII: {
> ! }
sent [CHAP Challenge id=0xe2 <f1eb1a13f6aa84ed91ea59c425d14354>, name = "vpnServer"]
rcvd [LCP EchoReq id=0x0 magic=0xb4ee9bd9]
sent [LCP EchoRep id=0x0 magic=0xba036f5d]xl2tpd[1364]: network_thread: recv packet from 192.168.123.88, size = 18, tunnel = 55102, call = 64760 ref=0 refhim=0
packet dump:
HEX: {
02 00 3E D7 F8 FC FF 03 C0 21 0A 00 00 08 B4 EE 9B D9 }
ASCII: {
> ! }
packet dump:
HEX: {
40 02 00 2A 10 14 55 79 FF 03 C2 23 01 E2 00 1E 10 F1 EB 1A 13 F6 AA 84 ED 91 EA 59 C4 25 D1 43 54 76 70 6E 53 65 72 76 65 72 }
ASCII: {
@ * Uy # Y % CTvpnServer}
rcvd [LCP EchoRep id=0x0 magic=0xb4ee9bd9]
xl2tpd[1364]: network_thread: recv packet from 192.168.123.88, size = 69, tunnel = 55102, call = 64760 ref=0 refhim=0
packet dump:
HEX: {
02 00 3E D7 F8 FC FF 03 C2 23 02 E2 00 3B 31 8B E9 AA 52 92 C1 49 5E DB 2D FB 4F 07 91 B7 77 00 00 00 00 00 00 00 00 B4 58 4F 60 A1 16 34 D1 30 3A DD DD 2B 2D AE 8C 59 1C BB 71 10 E8 18 CE 00 72 6F 62 6F 74 }
ASCII: {
> # ;1 R I^ - O w XO` 4 0: +- Y q robot}
rcvd [CHAP Response id=0xe2 <8be9aa5292c1495edb2dfb4f0791b7770000000000000000b4584f60a11634d1303adddd2b2dae8c591cbb7110e818ce00>, name = "robot"]
packet dump:
HEX: {
40 02 00 14 10 14 55 79 FF 03 C0 21 0A 00 00 08 BA 03 6F 5D }
ASCII: {
@ Uy ! o]}
sent [CHAP Success id=0xe2 "S=E58CEE285B030CCAA8A16E0F31DACF1DA26A221F M=Access granted"]
packet dump:
HEX: {
40 02 00 4B 10 14 55 79 FF 03 C2 23 03 E2 00 3F 53 3D 45 35 38 43 45 45 32 38 35 42 30 33 30 43 43 41 41 38 41 31 36 45 30 46 33 31 44 41 43 46 31 44 41 32 36 41 32 32 31 46 20 4D 3D 41 63 63 65 73 73 20 67 72 61 6E 74 65 64 }
ASCII: {
@ K Uy # ?S=E58CEE285B030CCAA8A16E0F31DACF1DA26A221F M=Access granted}
xl2tpd[1364]: network_thread: recv packet from 192.168.123.88, size = 20, tunnel = 55102, call = 64760 ref=0 refhim=0
packet dump:
HEX: {
02 00 3E D7 F8 FC FF 03 80 21 01 01 00 0A 03 06 00 00 00 00 }
ASCII: {
> ! }
sent [CCP ConfReq id=0x1 <deflate 15> <deflate(old#) 15> <bsd v1 15>]
packet dump:
HEX: {
40 02 00 1B 10 14 55 79 FF 03 80 FD 01 01 00 0F 1A 04 78 00 18 04 78 00 15 03 2F }
ASCII: {
@ Uy x x /}
xl2tpd[1364]: network_thread: recv packet from 192.168.123.88, size = 14, tunnel = 55102, call = 64760 ref=0 refhim=0
packet dump:
HEX: {
02 00 3E D7 F8 FC FF 03 80 FD 01 01 00 04 }
ASCII: {
> }
xl2tpd[1364]: network_thread: recv packet from 192.168.123.88, size = 25, tunnel = 55102, call = 64760 ref=0 refhim=0
packet dump:
HEX: {
02 00 3E D7 F8 FC FF 03 80 FD 04 01 00 0F 1A 04 78 00 18 04 78 00 15 03 2F }
ASCII: {
> x x /}
sent [IPCP ConfReq id=0x1 <compress VJ 0f 01> <addr 100.0.0.10>]
rcvd [IPCP ConfReq id=0x1 <addr 0.0.0.0>]
sent [IPCP ConfNak id=0x1 <addr 100.0.0.100>]packet dump:
HEX: {
40 02 00 1C 10 14 55 79 FF 03 80 21 01 01 00 10 02 06 00 2D 0F 01 03 06 64 00 00 0A }
ASCII: {
@ Uy ! - d }
packet dump:
HEX: {
40 02 00 16 10 14 55 79 FF 03 80 21 03 01 00 0A 03 06 64 00 00 64 }
ASCII: {
@ Uy ! d d}
xl2tpd[1364]: network_thread: recv packet from 192.168.123.88, size = 20, tunnel = 55102, call = 64760 ref=0 refhim=0
packet dump:
HEX: {
02 00 3E D7 F8 FC FF 03 80 21 04 01 00 0A 02 06 00 2D 0F 01 }
ASCII: {
> ! - }
rcvd [CCP ConfReq id=0x1]
sent [CCP ConfAck id=0x1]
xl2tpd[1364]: network_thread: recv packet from 192.168.123.88, size = 20, tunnel = 55102, call = 64760 ref=0 refhim=0
packet dump:
HEX: {
02 00 3E D7 F8 FC FF 03 80 21 01 02 00 0A 03 06 64 00 00 64 }
ASCII: {
> ! d d}
packet dump:
HEX: {
40 02 00 10 10 14 55 79 FF 03 80 FD 02 01 00 04 }
ASCII: {
@ Uy }
rcvd [CCP ConfRej id=0x1 <deflate 15> <deflate(old#) 15> <bsd v1 15>]
sent [CCP ConfReq id=0x2]
packet dump:
HEX: {
40 02 00 10 10 14 55 79 FF 03 80 FD 01 02 00 04 }
ASCII: {
@ Uy }
xl2tpd[1364]: network_thread: recv packet from 192.168.123.88, size = 14, tunnel = 55102, call = 64760 ref=0 refhim=0
packet dump:
HEX: {
02 00 3E D7 F8 FC FF 03 80 FD 02 02 00 04 }
ASCII: {
rcvd [IPCP ConfRej id=0x1 <compress VJ 0f 01>]
sent [IPCP ConfReq id=0x2 <addr 100.0.0.10>]
> }
rcvd [IPCP ConfReq id=0x2 <addr 100.0.0.100>]packet dump:
HEX: {
40 02 00 16 10 14 55 79 FF 03 80 21 01 02 00 0A 03 06 64 00 00 0A }
ASCII: {
@ Uy ! d }
xl2tpd[1364]: network_thread: recv packet from 192.168.123.88, size = 20, tunnel = 55102, call = 64760 ref=0 refhim=0
packet dump:
HEX: {
02 00 3E D7 F8 FC FF 03 80 21 02 02 00 0A 03 06 64 00 00 0A }
ASCII: {
sent [IPCP ConfAck id=0x2 <addr 100.0.0.100>]
rcvd [CCP ConfAck id=0x2] > ! d }
packet dump:
HEX: {
40 02 00 16 10 14 55 79 FF 03 80 21 02 02 00 0A 03 06 64 00 00 64 }
ASCII: {
@ Uy ! d d}
rcvd [IPCP ConfAck id=0x2 <addr 100.0.0.10>]
local IP address 100.0.0.10
remote IP address 100.0.0.100
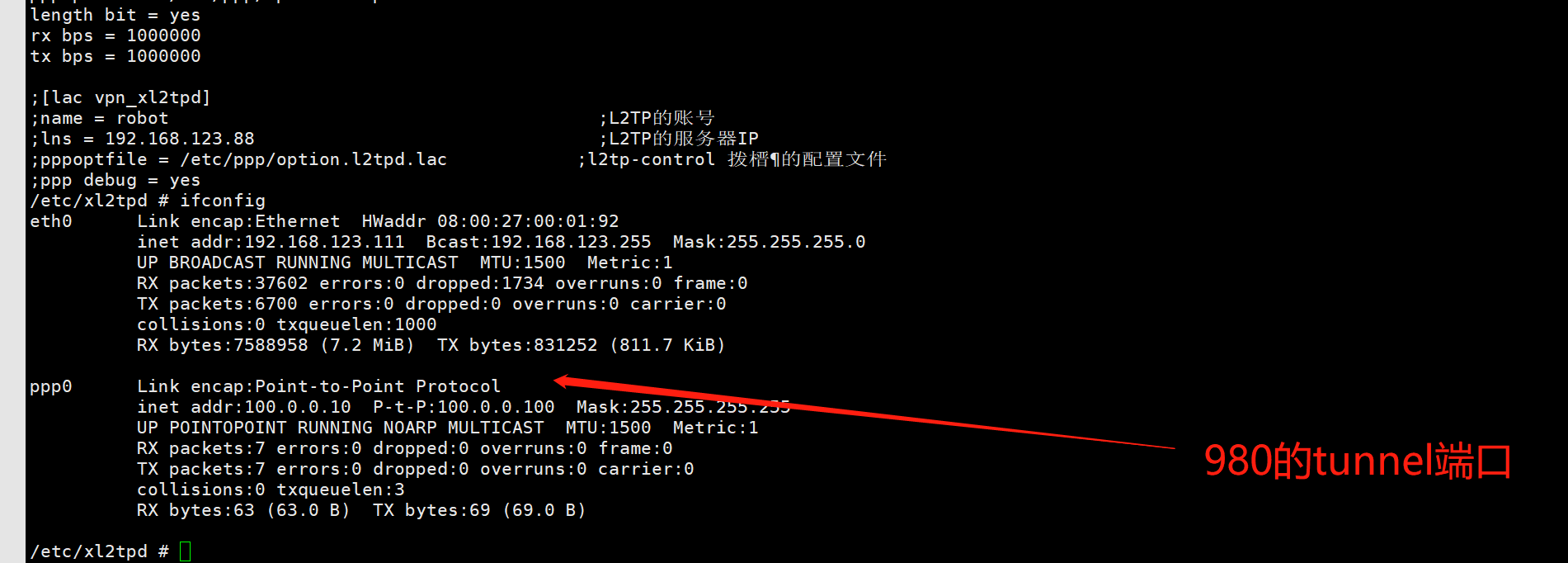
4.3) 实验测试图片
nuc980 arm上的tunnel接入点
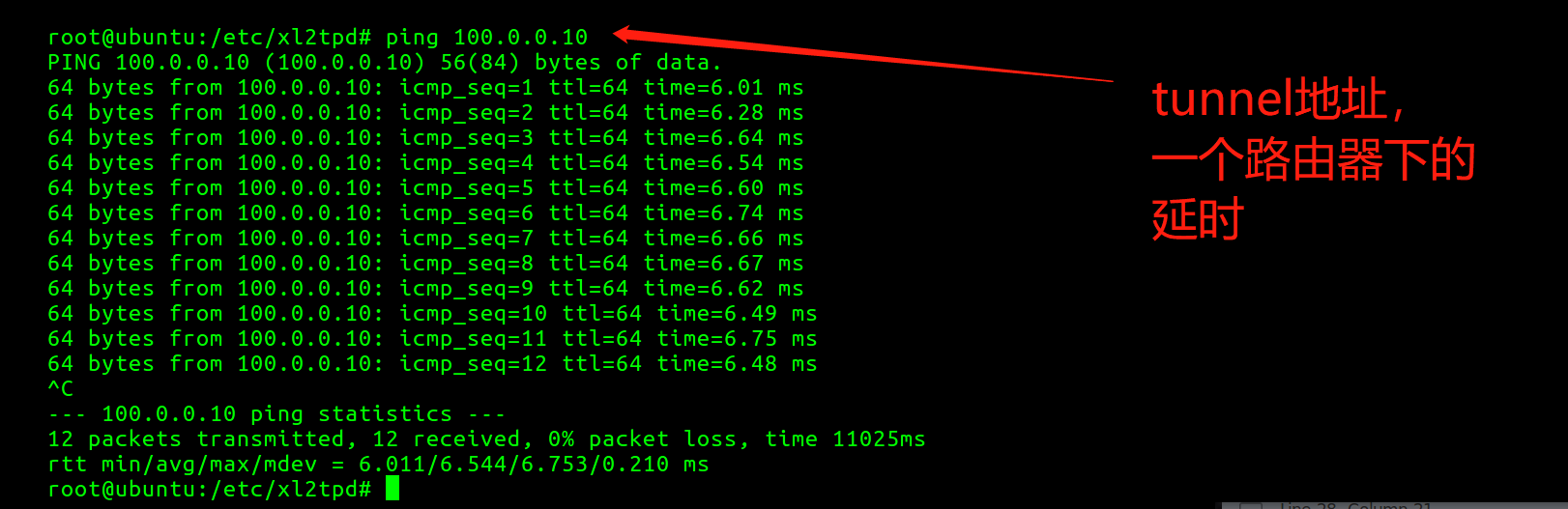
客户端ping 服务端 nuc980 的时延
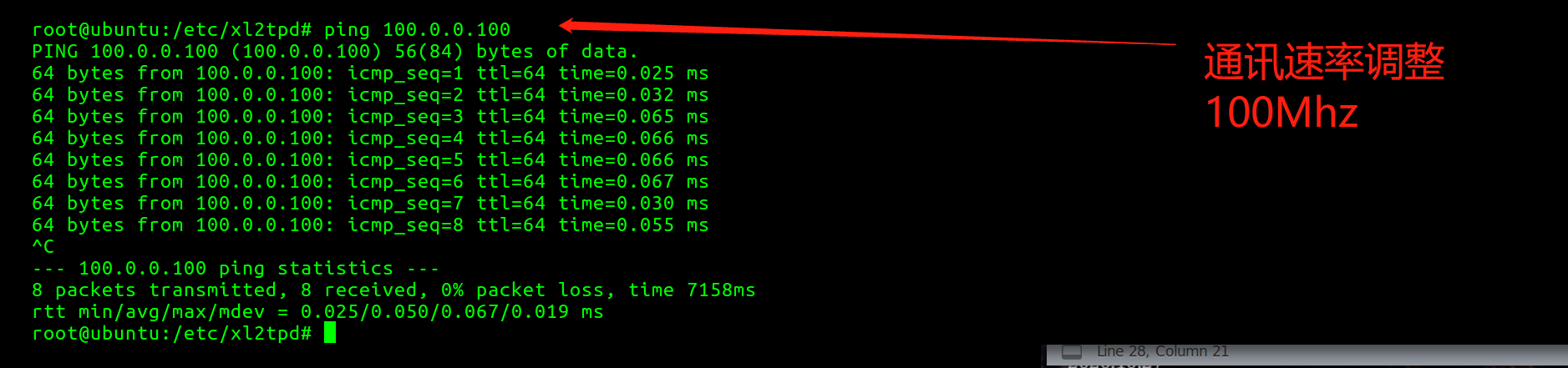
调整xl2tp的conf文件通讯速率后的时延
l2tp 的原理简介,请参考曹世宏的博客:
https://cshihong.blog.csdn.net/article/details/100005648