版权声明:本文为GJHe原创文章,未经博主允许不得转载。 https://blog.csdn.net/qq_35428201/article/details/82534775
实验拓扑
实验要求
1,公司A和公司B分别通过NAT接入到公网
2,公网配置静态路由互通
3,公司A和公司B启用gre vpn 使两公司互通
接口IP基本配置
AR1
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]un in en
Info: Information center is disabled.
[Huawei]sys AR1
[AR1]inter g0/0/0
[AR1-GigabitEthernet0/0/0]ip add 192.168.1.1 24
[AR1-GigabitEthernet0/0/0]inter g0/0/1
[AR1-GigabitEthernet0/0/1]ip add 1.1.1.1 24AR2
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]un in en
Info: Information center is disabled.
[Huawei]sys AR2
[AR2]inter g0/0/1
[AR2-GigabitEthernet0/0/1]ip add 2.2.2.1 24
[AR2-GigabitEthernet0/0/1]inter g0/0/0
[AR2-GigabitEthernet0/0/0]ip add 1.1.1.2 24AR3
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]un in en
Info: Information center is disabled.
[Huawei]sys AR3
[AR3]inter g0/0/0
[AR3-GigabitEthernet0/0/0]ip add 2.2.2.2 24
[AR3-GigabitEthernet0/0/0]inter g0/0/1
[AR3-GigabitEthernet0/0/1]ip add 3.3.3.1 24AR4
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]un in en
Info: Information center is disabled.
[Huawei]sys AR4
[AR4]inter g0/0/0
[AR4-GigabitEthernet0/0/0]ip add 3.3.3.2 24
[AR4-GigabitEthernet0/0/0]inter g0/0/2
[AR4-GigabitEthernet0/0/2]qu
[AR4]inter g0/0/1
[AR4-GigabitEthernet0/0/1]ip add 192.168.2.1 24公网配置静态路由互通
AR1
[AR1]ip route-static 0.0.0.0 0.0.0.0 1.1.1.2AR2
[AR2]ip route-static 0.0.0.0 0.0.0.0 2.2.2.2AR3
[AR3]ip route-static 0.0.0.0 0.0.0.0 2.2.2.1AR4
[AR4]ip route-static 0.0.0.0 0.0.0.0 3.3.3.1测试公网 已经通了
公网显然现实中使用静态路由走天下很不理想。还是使用动态路由更方便一些,这里我将采用OSPF
AR2
[AR2]ospf
[AR2-ospf-1]area 0
[AR2-ospf-1-area-0.0.0.0]network 1.1.1.0 0.0.0.255
[AR2-ospf-1-area-0.0.0.0]network 2.2.2.0 0.0.0.255AR3
[AR3]ospf
[AR3-ospf-1]area 0
[AR3-ospf-1-area-0.0.0.0]net 2.2.2.0 0.0.0.255
[AR3-ospf-1-area-0.0.0.0]net 3.3.3.0 0.0.0.255AR1
[AR1]ip route-static 0.0.0.0 0.0.0.0 1.1.1.2AR4
[AR4]ip route-static 0.0.0.0 0.0.0.0 3.3.3.1配置NAT
AR1
[AR1]acl number 2002
[AR1-acl-basic-2002]rule permit source 192.168.1.0 0.0.0.255
[AR1-acl-basic-2002]q
[AR1]int g0/0/1
[AR1-GigabitEthernet0/0/1]nat outbound 2002
[AR1-GigabitEthernet0/0/1]qAR4
[AR4]acl number 2002
[AR4-acl-basic-2002]rule permit source 192.168.2.0 0.0.0.255
[AR4-acl-basic-2002]q
[AR4]inter g0/0/0
[AR4-GigabitEthernet0/0/0]nat outbound 2002
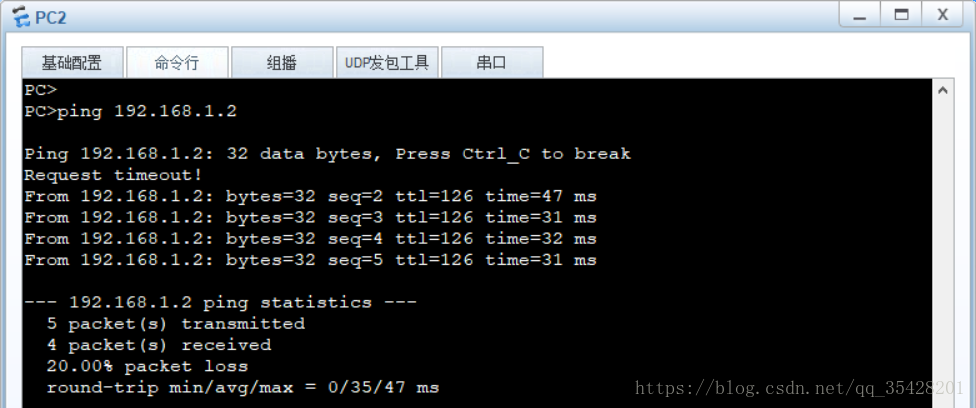
[AR4-GigabitEthernet0/0/0]qPC2测试已经可以访问公网了
配置GRE VPN
AR1
[AR1]interface Tunnel 0/0/0
[AR1-Tunnel0/0/0]tunnel-protocol gre
[AR1-Tunnel0/0/0]ip add 192.168.3.1 24
[AR1-Tunnel0/0/0]source 1.1.1.1
[AR1-Tunnel0/0/0]destination 3.3.3.2
[AR1-Tunnel0/0/0]qu
[AR1]ip route-static 192.168.2.0 24 tunnel 0/0/0AR4
[AR4]interface Tunnel0/0/0
[AR4-Tunnel0/0/0]ip add 192.168.3.2 24
[AR4-Tunnel0/0/0]tunnel-protocol gre
[AR4-Tunnel0/0/0]source 3.3.3.2
[AR4-Tunnel0/0/0]destination 1.1.1.1
[AR4-Tunnel0/0/0]q
[AR4]ip route-static 192.168.1.0 24 tunnel 0/0/0