作者信息:苗浩15515026488微信同号
本文摘抄自《华为ICT大赛-网络赛道学习空间(中国区)》,如有侵权,请及时联系作者删除文章
原文链接:
一、项目背景
某家大型公司设有一个总部(HQ)和一个分支机构(BR-1)。总部网络通过有线和无线 接入方式为员工实现网络接入。为了提高公司网络的安全。公司总部及分支机构网络出口 部署防火墙,并且为了提高可靠性,在总部开启双机热备,为了公司总部与分支机构间的 通信安全,需要建立IPSec VPN。
作者本人参加了这一届的大赛,因为当时自己水平确实不够,国赛成绩比较差,所以这个图也是作者的意难平,趁着假期把这张拓扑做出来,让后面参加的同学们有一个参考,预祝2023-2024华为ICT大赛的选手可以取得佳绩。
二、网络拓扑
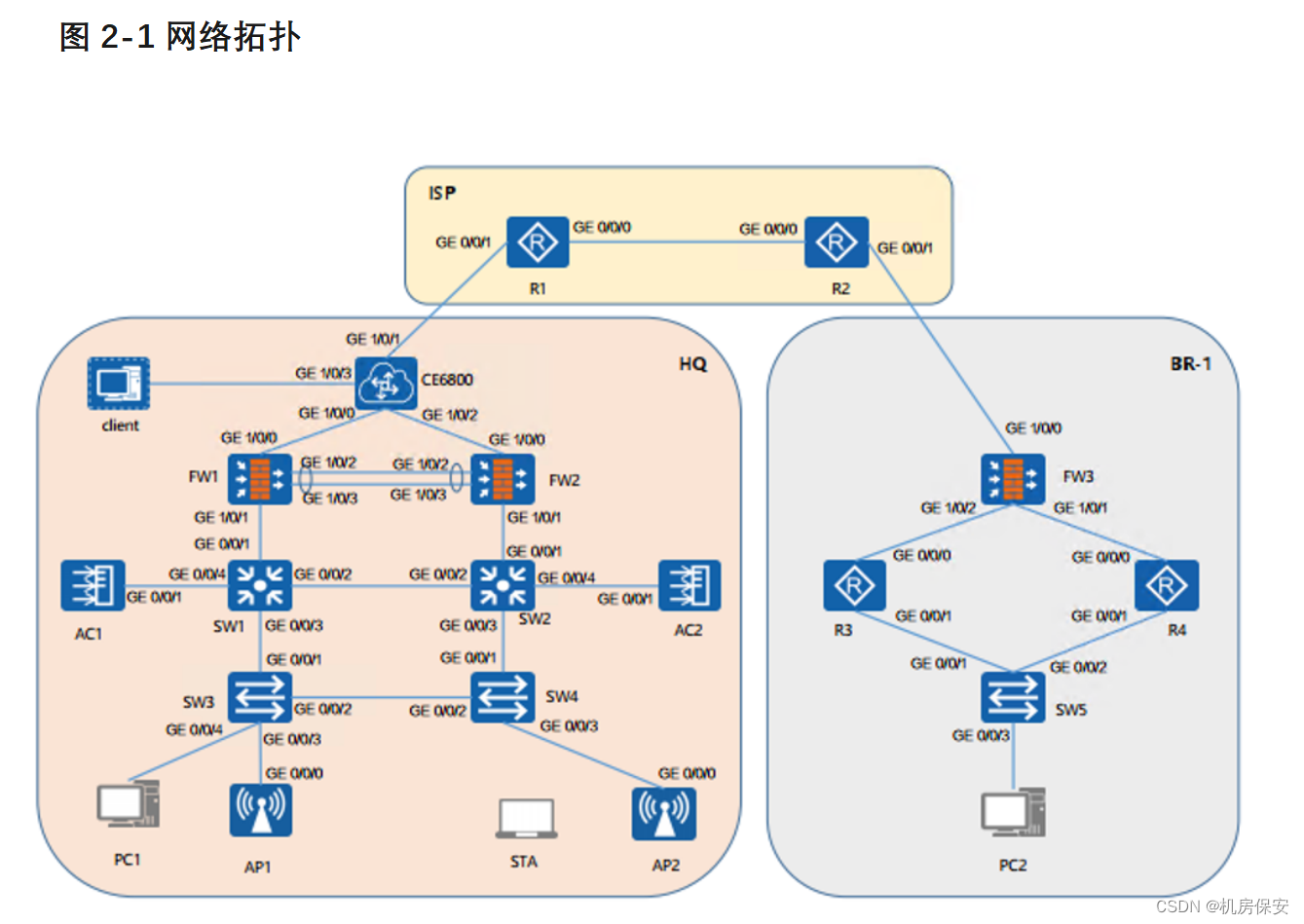
本实验包含以下设备:
- 3台 USG6000V防火墙(FW1 to FW3)
- 4台 AR2220路由器(R1 to R4)
- 2台 S5700交换机(SW1 and SW2)
- 3台 S3700交换机(SW3 to SW5)
- 2台 AC6005(AC1 and AC2)
- 2个 AP4050(AP1 and AP2)
- 1台 CE6800
- 2台 PC(PC1、PC2)
- 1台 STA(STA1)
表2-1 设备登录信息
| 设备 |
用户名 |
默认密码 |
新密码 |
| 防火墙 |
admin |
Admin@123 |
Huawei@123 |
表2-2 VLAN规划信息
| 设备名称 |
端口 |
链路类型 |
VLAN规划 |
| SW1 |
GE0/0/1 |
Trunk |
Allow-pass:104 |
| GE0/0/2 |
Trunk |
Allow-pass:101、102、103、105 |
|
| GE0/0/3 |
Trunk |
Allow-pass:101、102、103 |
|
| SW2 |
GE0/0/1 |
Trunk |
Allow-pass:106 |
| GE0/0/2 |
Trunk |
Allow-pass:101、102、103、105 |
|
| GE0/0/3 |
Trunk |
Allow-pass:101、102、103 |
|
| SW3 |
GE0/0/1 |
Trunk |
Allow-pass:101、102、103 |
| GE0/0/2 |
Trunk |
Allow-pass:101、102、103 |
|
| Eth0/0/3 |
Trunk |
||
| Eth0/0/4 |
Access |
VLAN:102 |
|
| SW4 |
GE0/0/1 |
Trunk |
Allow-pass:101、102、103 |
| GE0/0/2 |
Trunk |
Allow-pass:101、102、103 |
|
| Eth0/0/3 |
Trunk |
表2-3 IP地址规划
| 设备名称 |
端口 |
IP地址 |
| R1 |
Loopback0 |
1.1.1.1/24 |
| GE0/0/1 |
100.1.1.1/24 |
|
| GE0/0/0 |
12.1.1.1/30 |
|
| R2 |
Loopback0 |
2.2.2.2/24 |
| GE0/0/1 |
200.1.1.1/24 |
|
| GE0/0/0 |
12.1.1.2/30 |
|
| .FW1 |
Eth-Trunk0 |
192.168.100.1/30 |
| GE1/0/0 |
100.1.1.2/24 |
|
| GE1/0/1.104 |
192.168.104.1/30 |
|
| FW2 |
Eth-Trunk0 |
192.168.100.2/30 |
| GE1/0/0 |
100.1.1.3/24 |
|
| GE1/0/1.106 |
192.168.106.1/30 |
|
| SW1 |
VLANIF 101 |
192.168.101.2/24 |
| VLANIF 102 |
192.168.102.2/24 |
|
| VLANIF 103 |
10.11.103.4/24 |
|
| VLANIF 104 |
192.168.104.2/30 |
|
| VLANIF 105 |
192.168.105.1/30 |
|
| SW2 |
VLANIF 105 |
192.168.105.2/30 |
| VLANIF 106 |
192.168.106.2/30 |
|
| FW3 |
GE1/0/0 |
200.1.1.2/30 |
| GE1/0/2 |
10.10.1.1/30 |
|
| GE1/0/1 |
10.10.2.1/30 |
|
| R3 |
GE0/0/0 |
10.10.1.2/30 |
| GE0/0/1 |
10.10.3.1/30 |
|
| R4 |
GE0/0/0 |
10.10.2.2/30 |
| GE0/0/1 |
10.10.4.1/30 |
|
| SW5 |
GE0/0/1 |
Vlanif3:10.10.3.2/30 |
| GE0/0/2 |
Vlanif4:10.10.4.2/30 |
|
| Eth0/0/3 |
Vlanif5:10.10.5.1/24 |
|
| CE6800 |
GE1/0/3 |
Vlanif1:192.168.56.100/24 |
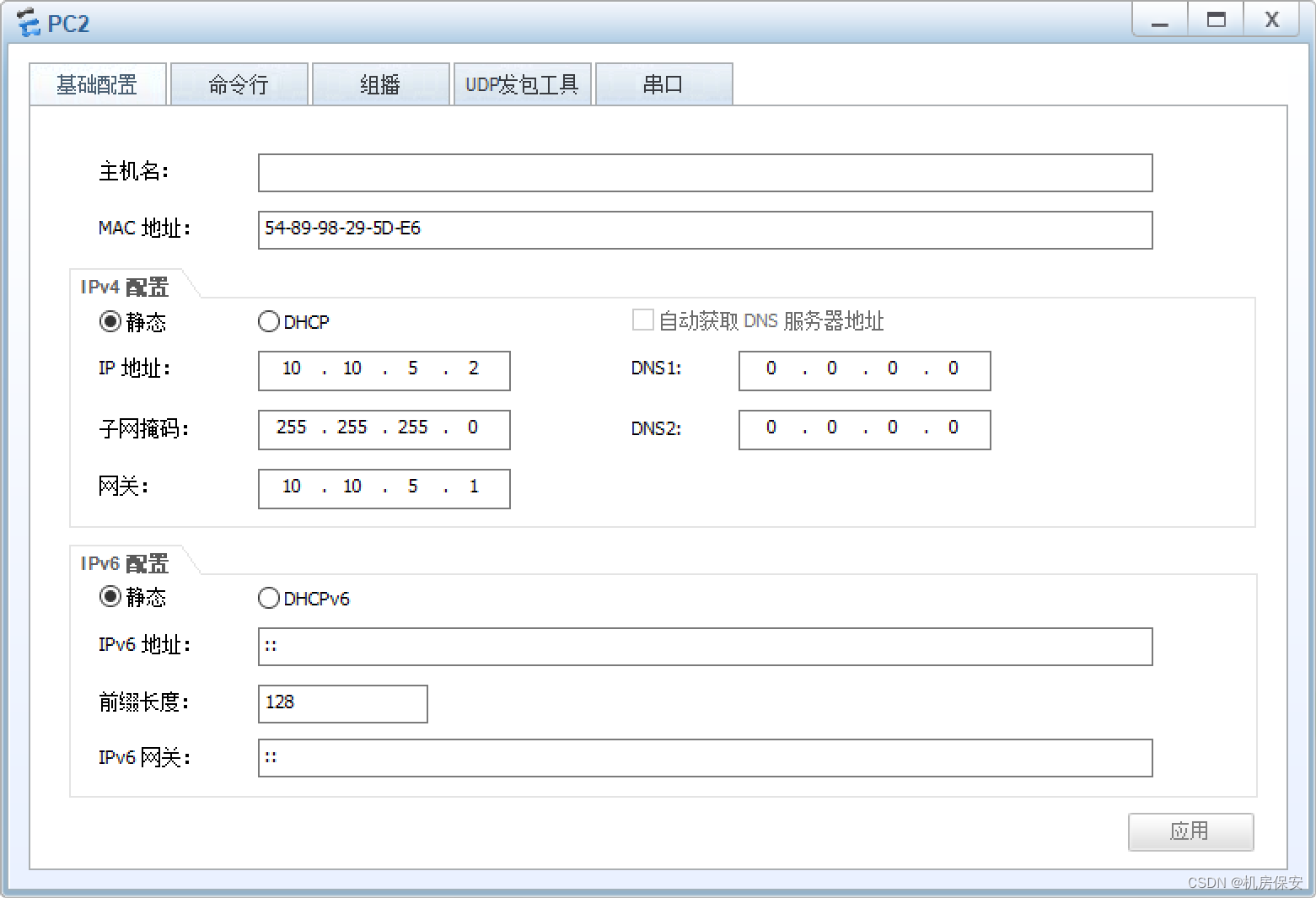
| PC2 |
静态IP |
10.10.5.2/24 |
配置过程:基础配置
设备命名/初始化
#SW1
<Huawei>system-view
[Huawei]sysname SW1
[SW1]
#SW2
<Huawei>system-view
[Huawei]sysname SW2
[SW2]
#SW3
<Huawei>system-view
[Huawei]sysname SW3
[SW3]
#SW4
<Huawei>system-view
[Huawei]sysname SW4
[SW4]
#AC1
<AC6005>system-view
[AC6005]sysname AC1
[AC1]
#AC2
<AC6005>system-view
[AC6005]sysname AC2
[AC2]
#FW1
<USG6000V1>system-view
[USG6000V1]sysname FW1
[FW1]
#FW2
<USG6000V1>system-view
[USG6000V1]sysname FW2
[FW2]
#CE6800
<HUAWEI>system-view immediately
[HUAWEI]sysname CE6800
[CE6800]
#FW3
<USG6000V1>system-view
[USG6000V1]sysname FW3
[FW3]
#AR3
<Huawei>system-view
[Huawei]sysname AR3
[AR3]
#AR4
<Huawei>system-view
[Huawei]sysname AR4
[AR4]
#SW5
<Huawei>system-view
[Huawei]sysname SW5
[SW5]
#AR1
<Huawei>system-view
[Huawei]sysname AR1
[AR1]
#AR2
<Huawei>system-view
[Huawei]sysname AR2
[AR2]
VLAN/链路配置
#SW1
[SW1]vlan batch 101 102 103 104 105
[SW1]interface GigabitEthernet 0/0/1
[SW1-GigabitEthernet0/0/1]port link-type trunk
[SW1-GigabitEthernet0/0/1]port trunk allow-pass vlan 104
[SW1-GigabitEthernet0/0/1]undo port trunk allow-pass vlan 1
[SW1]interface GigabitEthernet 0/0/2
[SW1-GigabitEthernet0/0/2]port link-type trunk
[SW1-GigabitEthernet0/0/2]port trunk allow-pass vlan 101 102 103 105
[SW1-GigabitEthernet0/0/2]undo port trunk allow-pass vlan 1
[SW1]interface GigabitEthernet 0/0/3
[SW1-GigabitEthernet0/0/3]port link-type trunk
[SW1-GigabitEthernet0/0/3]port trunk allow-pass vlan 101 102 103
[SW1-GigabitEthernet0/0/3]undo port trunk allow-pass vlan 1
[SW1]interface GigabitEthernet 0/0/4
[SW1-GigabitEthernet0/0/4]port link-type trunk
[SW1-GigabitEthernet0/0/4]port trunk allow-pass vlan 101 102 103
[SW1-GigabitEthernet0/0/4]undo port trunk allow-pass vlan 1
#SW2
[SW2]vlan batch 101 102 103 105 106
[SW2]interface GigabitEthernet 0/0/1
[SW2-GigabitEthernet0/0/1]port link-type trunk
[SW2-GigabitEthernet0/0/1]port trunk allow-pass vlan 106
[SW2-GigabitEthernet0/0/1]undo port trunk allow-pass vlan 1
[SW2]interface GigabitEthernet 0/0/2
[SW2-GigabitEthernet0/0/2]port link-type trunk
[SW2-GigabitEthernet0/0/2]port trunk allow-pass vlan 101 102 103 105
[SW2-GigabitEthernet0/0/2]undo port trunk allow-pass vlan 1
[SW2]interface GigabitEthernet 0/0/3
[SW2-GigabitEthernet0/0/3]port link-type trunk
[SW2-GigabitEthernet0/0/3]port trunk allow-pass vlan 101 102 103
[SW2-GigabitEthernet0/0/3]undo port trunk allow-pass vlan 1
[SW2]interface GigabitEthernet 0/0/4
[SW2-GigabitEthernet0/0/4]port link-type trunk
[SW2-GigabitEthernet0/0/4]port trunk allow-pass vlan 101 102 103
[SW2-GigabitEthernet0/0/4]undo port trunk allow-pass vlan 1
#SW3
[SW3]vlan batch 101 102 103
[SW3]port-group group-member GigabitEthernet 0/0/1 GigabitEthernet 0/0/2
[SW3-port-group]port link-type trunk
[SW3-port-group]port trunk allow-pass vlan 101 102 103
[SW3-port-group]undo port trunk allow-pass vlan 1
[SW3]interface Ethernet0/0/3
[SW3-Ethernet0/0/3]port link-type trunk
[SW3-Ethernet0/0/3]port trunk allow-pass vlan 101 102 103
[SW3-Ethernet0/0/3]port trunk pvid vlan 101
[SW3-Ethernet0/0/3]undo port trunk allow-pass vlan 1
[SW3]interface Ethernet0/0/4
[SW3-Ethernet0/0/4]port link-type access
[SW3-Ethernet0/0/4]port default vlan 102
#SW4
[SW4]vlan batch 101 102 103
[SW4]port-group group-member GigabitEthernet 0/0/1 GigabitEthernet 0/0/2
[SW4-port-group]port link-type trunk
[SW4-port-group]port trunk allow-pass vlan 101 102 103
[SW4-port-group]undo port trunk allow-pass vlan 1
[SW4]interface Ethernet0/0/3
[SW4-Ethernet0/0/3]port link-type trunk
[SW4-Ethernet0/0/3]port trunk allow-pass vlan 101 102 103
[SW4-Ethernet0/0/3]port trunk pvid vlan 101
[SW4-Ethernet0/0/3]undo port trunk allow-pass vlan 1
#SW5
[SW5]vlan batch 3 4 5
[SW5]interface GigabitEthernet 0/0/1
[SW5-GigabitEthernet0/0/1]port link-type access
[SW5-GigabitEthernet0/0/1]port default vlan 3
[SW5]interface GigabitEthernet 0/0/2
[SW5-GigabitEthernet0/0/2]port link-type access
[SW5-GigabitEthernet0/0/2]port default vlan 4
[SW5]interface Ethernet0/0/3
[SW5-Ethernet0/0/3]port link-type access
[SW5-Ethernet0/0/3]port default vlan 5
#FW1
[FW1]interface Eth-Trunk 0
[FW1-Eth-Trunk0]trunkport GigabitEthernet 1/0/2 1/0/3
#FW2
[FW2]interface Eth-Trunk 0
[FW2-Eth-Trunk0]trunkport GigabitEthernet 1/0/2 1/0/3
#AC1
[AC1]vlan batch 101 102 103
[AC1]interface GigabitEthernet 0/0/1
[AC1-GigabitEthernet0/0/1]port link-type trunk
[AC1-GigabitEthernet0/0/1]port trunk allow-pass vlan 101 102 103
#AC2
[AC2]vlan batch 101 102 103
[AC1]interface GigabitEthernet 0/0/1
[AC1-GigabitEthernet0/0/1]port link-type trunk
[AC1-GigabitEthernet0/0/1]port trunk allow-pass vlan 101 102 103
IP地址配置
#R1
[R1]interface LoopBack 0
[R1-LoopBack0]ip address 1.1.1.1 24
[R1]interface GigabitEthernet 0/0/1
[R1-GigabitEthernet0/0/1]ip address 100.1.1.1 24
[R1]interface GigabitEthernet 0/0/0
[R1-GigabitEthernet0/0/0]ip address 12.1.1.1 30
#R2
[R2]interface LoopBack 0
[R2-LoopBack0]ip address 2.2.2.2 24
[R2]interface GigabitEthernet 0/0/1
[R2-GigabitEthernet0/0/1]ip address 200.1.1.1 24
[R2]interface GigabitEthernet 0/0/0
[R2-GigabitEthernet0/0/0]ip address 12.1.1.2 30
#FW1
[FW1]interface Eth-Trunk 0
[FW1-Eth-Trunk0]ip address 192.168.100.1 30
[FW1]interface GigabitEthernet 1/0/0
[FW1-GigabitEthernet1/0/0]ip address 100.1.1.2 24
[FW1]interface GigabitEthernet 1/0/1.104
[FW1-GigabitEthernet1/0/1.104]vlan-type dot1q 104
[FW1-GigabitEthernet1/0/1.104]ip address 192.168.104.1 30
#FW2
[FW2]interface Eth-Trunk 0
[FW2-Eth-Trunk0]ip address 192.168.100.2 30
[FW2]interface GigabitEthernet 1/0/0
[FW2-GigabitEthernet1/0/0]ip address 100.1.1.3 24
[FW2]interface GigabitEthernet 1/0/1.106
[FW2-GigabitEthernet1/0/1.106]vlan-type dot1q 106
[FW2-GigabitEthernet1/0/1.106]ip address 192.168.106.1 30
#SW1
[SW1]interface Vlanif 101
[SW1-Vlanif101]ip address 192.168.101.2 24
[SW1]interface Vlanif 102
[SW1-Vlanif102]ip address 192.168.102.2 24
[SW1]interface Vlanif 103
[SW1-Vlanif103]ip address 10.11.103.4 24
[SW1]interface Vlanif 104
[SW1-Vlanif104]ip address 192.168.104.2 30
[SW1]interface Vlanif 105
[SW1-Vlanif105]ip address 192.168.105.1 30
#SW2
[SW2]interface Vlanif 105
[SW2-Vlanif105]ip address 192.168.105.2 30
[SW2]interface Vlanif 106
[SW2-Vlanif106]ip address 192.168.106.2 30
#FW3
[FW3]interface GigabitEthernet 1/0/0
[FW3-GigabitEthernet1/0/0]ip address 200.1.1.2 30
[FW3]interface GigabitEthernet 1/0/2
[FW3-GigabitEthernet1/0/2]ip address 10.10.1.1 30
[FW3]interface GigabitEthernet 1/0/1
[FW3-GigabitEthernet1/0/1]ip address 10.10.2.1 30
#R3
[R3]interface GigabitEthernet 0/0/0
[R3-GigabitEthernet0/0/0]ip address 10.10.1.2 30
[R3]interface GigabitEthernet 0/0/1
[R3-GigabitEthernet0/0/1]ip address 10.10.3.1 30
#R4
[R4]interface GigabitEthernet 0/0/0
[R4-GigabitEthernet0/0/0]ip address 10.10.2.2 30
[R4]interface GigabitEthernet 0/0/1
[R4-GigabitEthernet0/0/1]ip address 10.10.4.1 30
#SW5
[SW5]interface Vlanif 3
[SW5-Vlanif3]ip address 10.10.3.2 30
[SW5]interface Vlanif 4
[SW5-Vlanif4]ip address 10.10.4.2 30
[SW5]interface Vlanif 5
[SW5-Vlanif5]ip address 10.10.5.1 24
#CE6800
[CE6800]interface GE 1/0/3
[CE6800-GE1/0/3]undo shutdown
[CE6800-GE1/0/3]port link-type access
[CE6800-GE1/0/3]port default vlan 1
[CE6800-Vlanif1]ip address 192.168.56.100 24
#AC1
[AC1]interface Vlanif 103
[AC1-Vlanif103]ip address 10.11.103.2 24
#AC2
[AC2]interface Vlanif 103
[AC2-Vlanif103]ip address 10.11.103.3 24
三、配置任务
3.1 公司总部网络配置
3.1.1 任务1:配置MSTP
- 在SW1、SW2、SW3、SW4上创建VLAN101、102、103,并开启STP协议,并指定SW1为根桥,SW2为备用根桥。
- 创建MST域,域名:huawei,并允许VLAN101至103从该域转发。
- 根桥设备指定端口开启跟根保护功能。
配置过程:
#SW1
[SW1]stp region-configuration
[SW1-mst-region]region-name huawei
[SW1-mst-region]instance 1 vlan 101 102 103
[SW1-mst-region]active region-configuration
[SW1]stp instance 0 root primary
[SW1]stp instance 1 root primary
#SW2
[SW2]stp region-configuration
[SW2-mst-region]region-name huawei
[SW2-mst-region]instance 1 vlan 101 102 103
[SW2-mst-region]active region-configuration
[SW2]stp instance 0 root secondary
[SW2]stp instance 1 root secondary
#SW3
[SW2]stp region-configuration
[SW2-mst-region]region-name huawei
[SW2-mst-region]instance 1 vlan 101 102 103
[SW2-mst-region]active region-configuration
#SW4
[SW2]stp region-configuration
[SW2-mst-region]region-name huawei
[SW2-mst-region]instance 1 vlan 101 102 103
[SW2-mst-region]active region-configuration
STP根保护/边缘端口
#SW1
[SW1]interface GigabitEthernet 0/0/1
[SW1-GigabitEthernet0/0/1]stp edged-port enable
[SW1-GigabitEthernet0/0/1]stp disable
[SW1]interface GigabitEthernet 0/0/4
[SW1-GigabitEthernet0/0/4]stp edged-port enable
[SW1-GigabitEthernet0/0/4]stp disable
[SW1]interface GigabitEthernet 0/0/2
[SW1-GigabitEthernet0/0/2]stp root-protection
[SW1]interface GigabitEthernet 0/0/3
[SW1-GigabitEthernet0/0/3]stp root-protection
#SW2
[SW2]interface GigabitEthernet 0/0/1
[SW2-GigabitEthernet0/0/1]stp edged-port enable
[SW2-GigabitEthernet0/0/1]stp disable
[SW2]interface GigabitEthernet 0/0/4
[SW2-GigabitEthernet0/0/4]stp edged-port enable
[SW2-GigabitEthernet0/0/4]stp disable
[SW2]interface GigabitEthernet 0/0/3
[SW2-GigabitEthernet0/0/3]stp root-protection 验证:
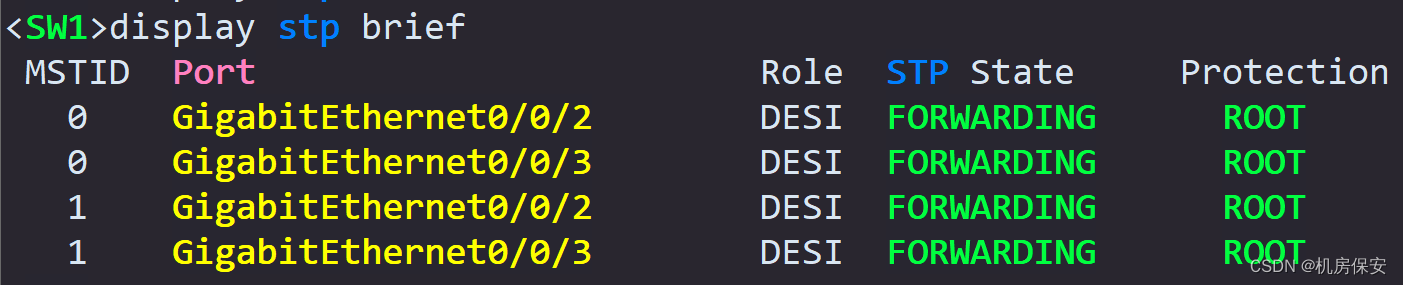
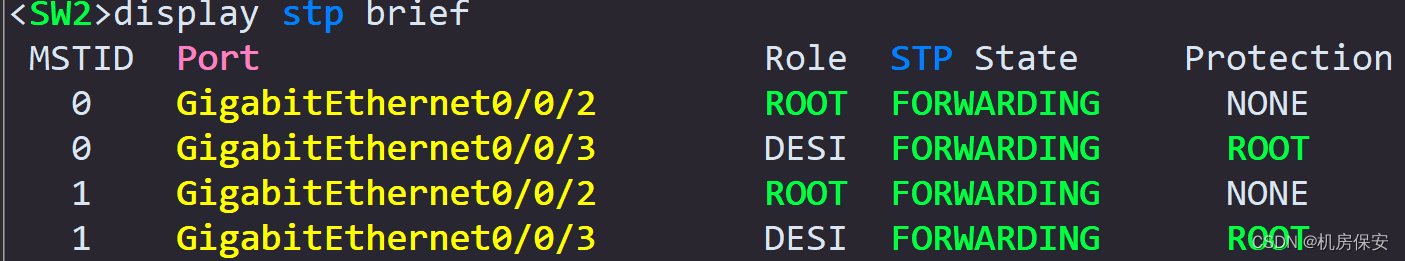

3.1.2 任务2:IP地址
根据图2-1所示的网络拓扑,配置接口IP地址,IP地址规划如表2-3所示。
3.1.3 任务3:配置DHCP
SW1作为总部内部网络的网关,开启DHCP功能,对内部有线及无线网络分配IP地址。在SW1上创建基于接口地址池的DHCP服务,分别为AP1、AP2、STA、PC1分配地址。
- STA和有线PC地址池为192.168.102.0/24,网关为192.168.102.1,DNS服务器IP地址为114.114.114.114。
- AP地址池为192.168.101.0/24,网关为192.168.101.1。
配置过程:
DHCP
#SW1
[SW1]dhcp enable
[SW1]interface Vlanif 101
[SW1-Vlanif101]dhcp select interface
[SW1-Vlanif101]dhcp server option 43 sub-option 2 ip-address 10.11.103.1
[SW1]interface Vlanif 102
[SW1-Vlanif102]dhcp select interface
[SW1-Vlanif102]dhcp server dns-list 114.114.114.114验证:按照这个题目需求应该做不到网关和题目一致

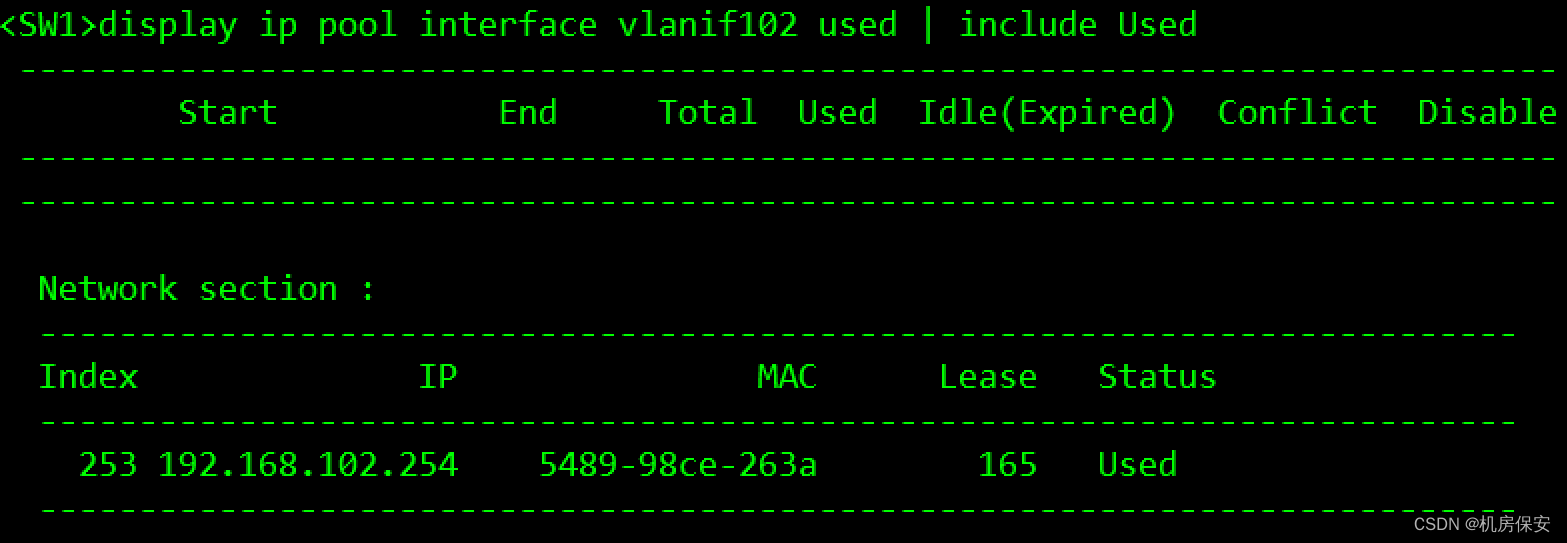
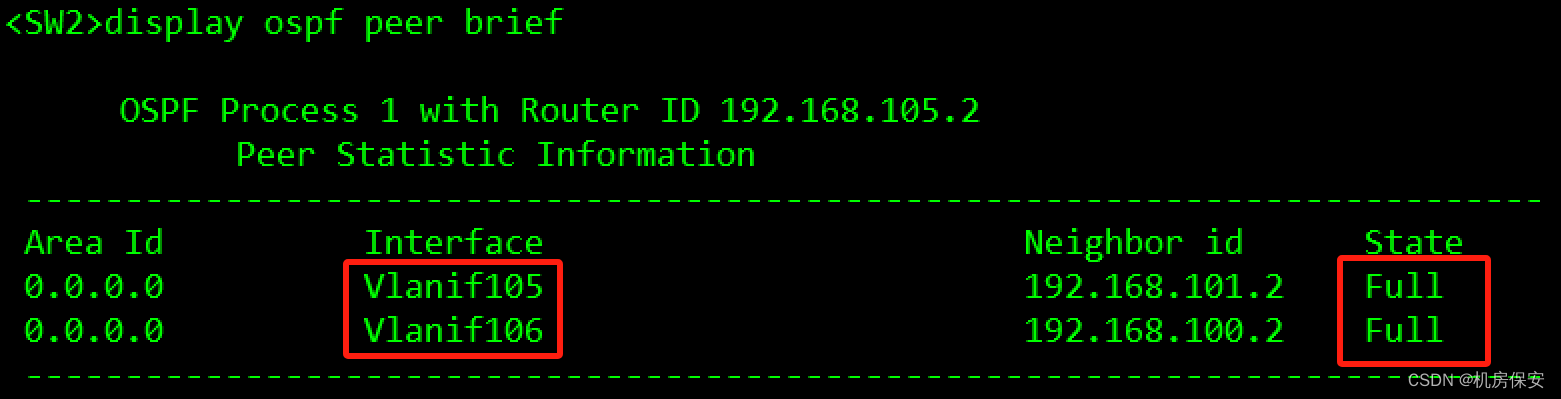
3.1.4 任务4:配置OSPF
- 在FW1、FW2、SW1、SW2上运行OSPF,设置OSPF进程为1。
- 防火墙FW1 GE1/0/1.104、FW2 GE1/0/1.106、SW1 VLANIF104和VLANIF105、SW2 VLANIF105和VLANIF106对应接口开启OSPF,并加入区域0.0.0.0。
- 在SW1上配置路由策略,匹配PC1及STA终端所在网段路由,并在OSPF引入用户路由时应用路由策略。
OSPF
#SW1
[SW1]ip ip-prefix PC1_STA permit 192.168.102.0 24
[SW1]route-policy PC1_STA permit node 10
[SW1-route-policy]if-match ip-prefix PC1_STA
[SW1]ospf 1
[SW1-ospf-1]import-route direct route-policy PC1_STA type 1
[SW1-ospf-1]area 0
[SW1]interface Vlanif 104
[SW1-Vlanif104]ospf enable 1 area 0
[SW1]interface Vlanif 105
[SW1-Vlanif105]ospf enable 1 area 0
#SW2
[SW2]ospf 1
[SW2-ospf-1]area 0
[SW2]interface Vlanif 105
[SW2-Vlanif105]ospf enable 1 area 0
[SW2]interface Vlanif 106
[SW2-Vlanif106]ospf enable 1 area 0
#FW1
FW1]ip route-static 0.0.0.0 0.0.0.0 100.1.1.1
[FW1]ospf 1
[FW1-ospf-1]default-route-advertise type 1
[FW1-ospf-1]area 0
[FW1]interface GigabitEthernet 1/0/1.104
[FW1-GigabitEthernet1/0/1.104]ospf enable 1 area 0
#FW2
[FW2]ip route-static 0.0.0.0 0.0.0.0 100.1.1.1
[FW2]ospf 1
[FW2-ospf-1]default-route-advertise type 1
[FW2-ospf-1]area 0
[FW2]interface GigabitEthernet 1/0/1.106
[FW2-GigabitEthernet1/0/1.106]ospf enable 1 area 0验证:
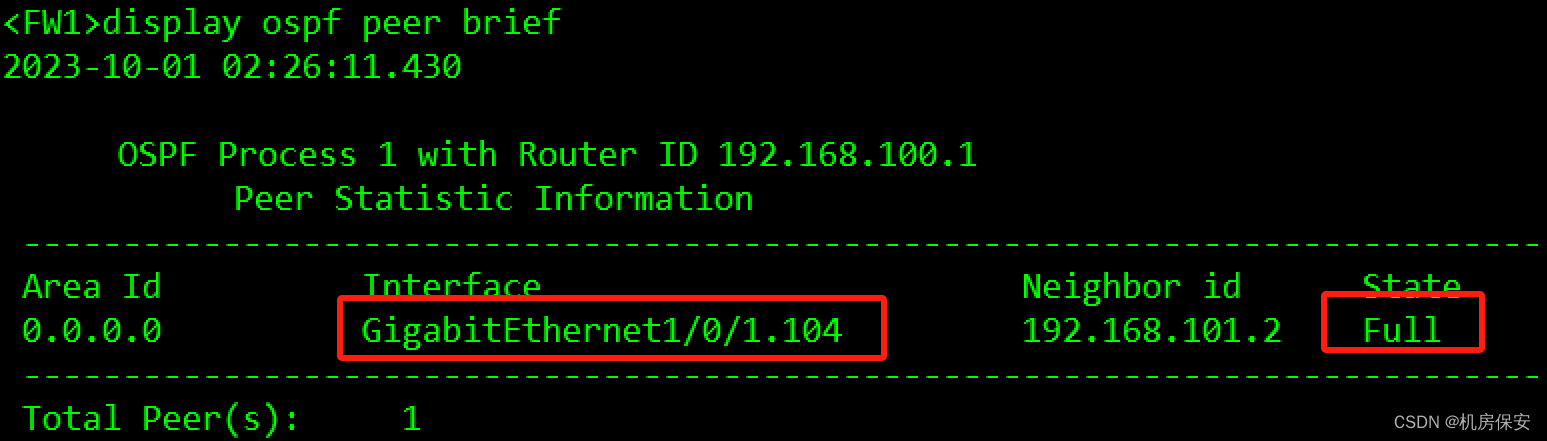
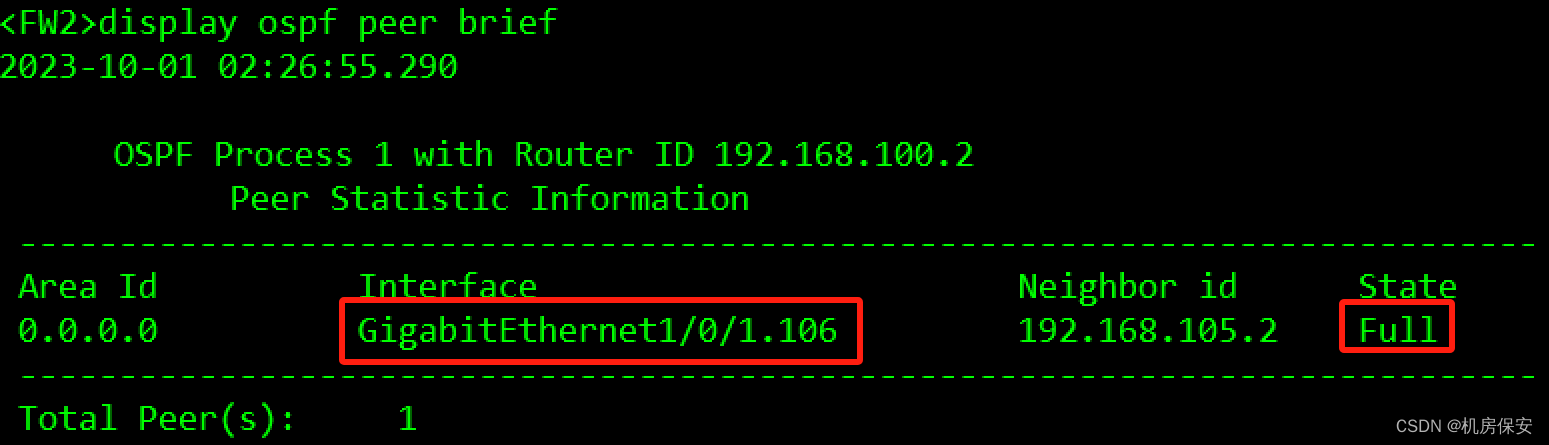
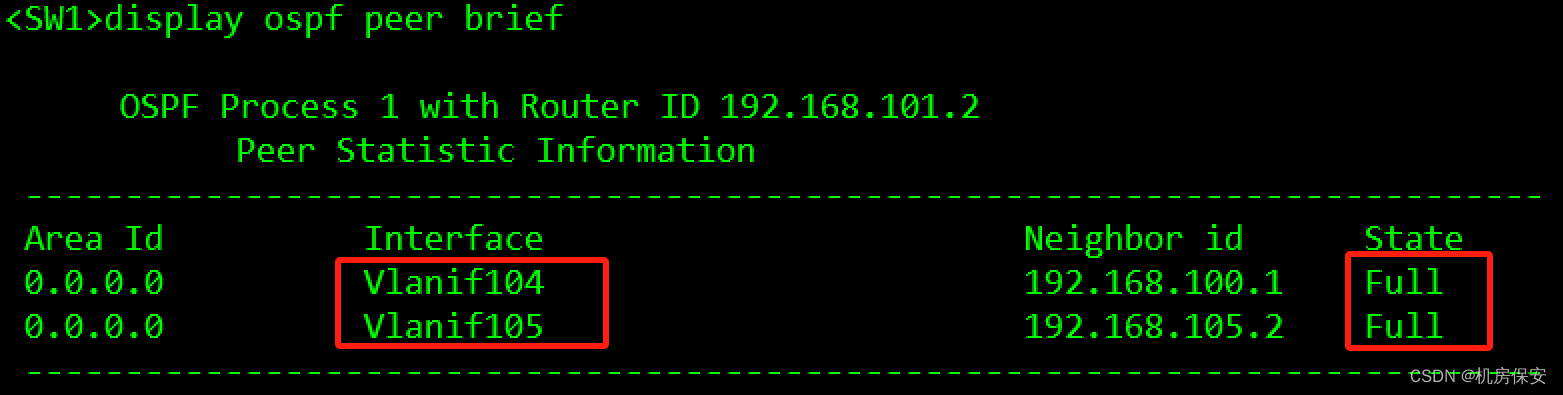

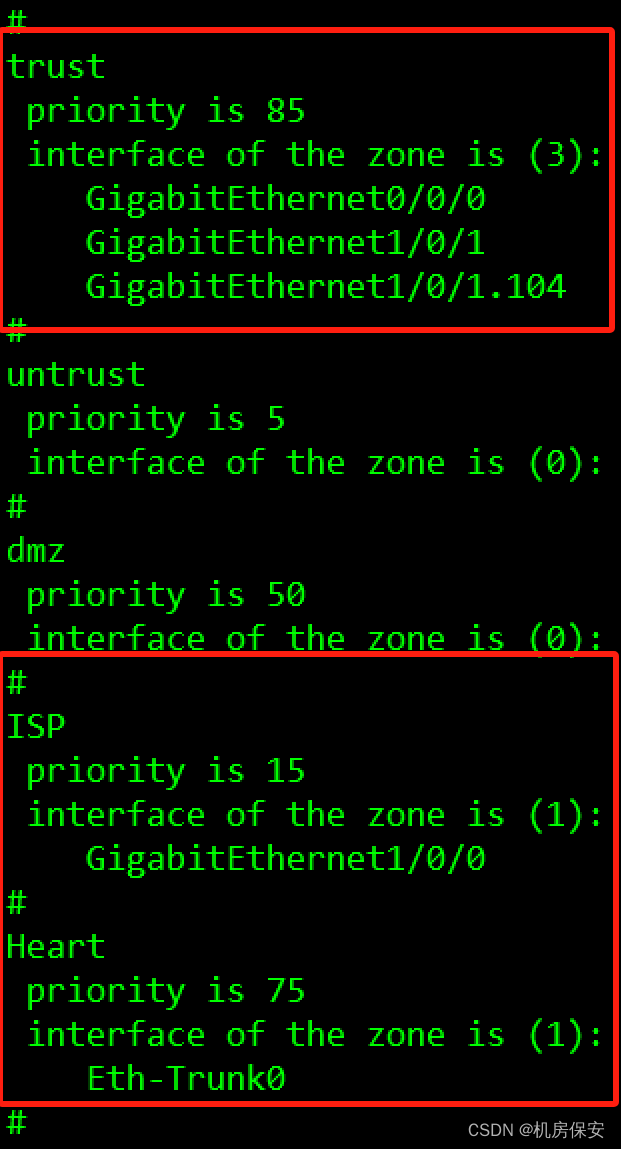
3.1.5 任务5:配置防火墙安全区域
- 创建ISP安全区域,设置优先级为15,将GE1/0/0加入该区域负责与ISP网络直连。
- 创建Heart安全区域,设置优先级为75,将防火墙双机热备心跳口Eth-trunk0接口加入该区域。
- 将GE1/0/1接口及其子接口加入trust区域。
配置过程:
安全区域
#FW1
[FW1]firewall zone name ISP
[FW1-zone-ISP]set priority 15
[FW1-zone-ISP]add interface GigabitEthernet 1/0/0
[FW1]firewall zone name Heart
[FW1-zone-Heart]set priority 75
[FW1-zone-Heart]add interface Eth-Trunk 0
[FW1]firewall zone trust
[FW1-zone-trust]add interface GigabitEthernet 1/0/1
[FW1-zone-trust]add interface GigabitEthernet 1/0/1.104
#FW2
[FW2]firewall zone name ISP
[FW2-zone-ISP]set priority 15
[FW2-zone-ISP]add interface GigabitEthernet 1/0/0
[FW2]firewall zone name Heart
[FW2-zone-Heart]set priority 75
[FW2-zone-Heart]add interface Eth-Trunk 0
[FW2]firewall zone trust
[FW2-zone-trust]add interface GigabitEthernet 1/0/1
[FW2-zone-trust]add interface GigabitEthernet 1/0/1.106
验证:display zone
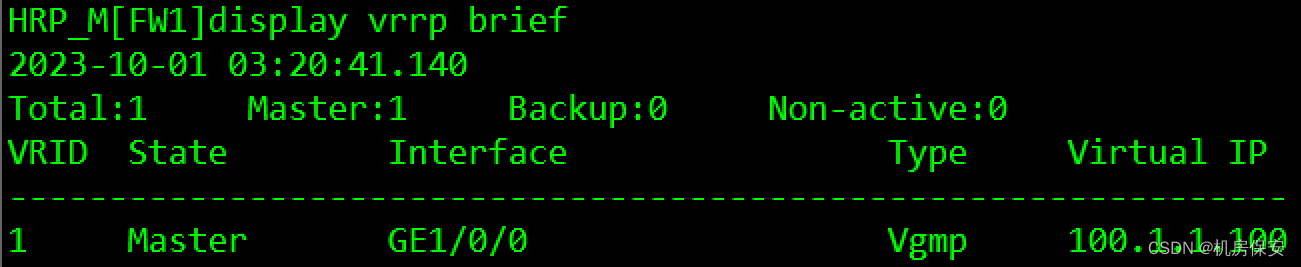
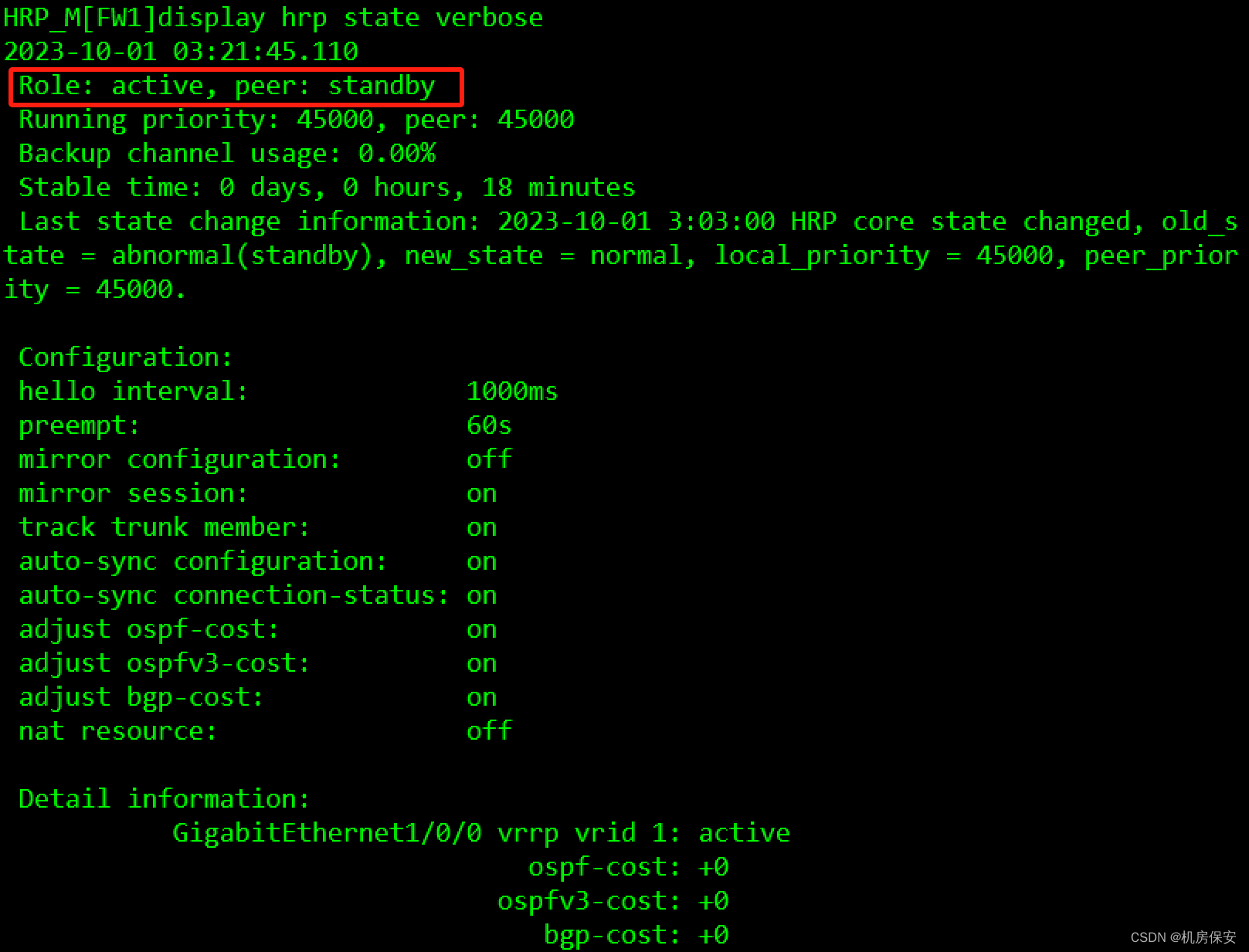
3.1.6 任务6:配置防火墙双机热备
防火墙作为企业出口网关,为提升总部网络可靠性,部署防火墙双机热备,在正常工作时,FW1作为主用设备转发流量,当FW1出现故障,企业网络流量可切换至备用设备FW2,保证企业内外部的正常通信。
- 在FW1、FW2上配置VRRP备份组,具体规划请看表3-1 VRRP规划表。
- 在FW1、FW2上指定心跳接口,心跳接口为Eth-trunk0,启用双机热备。
- OSPF路由优先走FW1。
- 配置Link-group,当FW1的上下接口GE1/0/0或者GE1/0/1出现故障时,触发防火墙主备切换。

配置过程:
#SW2
[SW2]interface Vlanif 106
[SW2-Vlanif106]ospf cost 5
#FW2
[FW2]interface GigabitEthernet 1/0/1.106
[FW2-GigabitEthernet1/0/1.106]ospf cost 5
VRRP
#FW1
[FW1]interface GigabitEthernet 1/0/0
[FW1-GigabitEthernet1/0/0]vrrp vrid 1 virtual-ip 100.1.1.100 active
#FW2
[FW2]interface GigabitEthernet 1/0/0
[FW2-GigabitEthernet1/0/0]vrrp vrid 1 virtual-ip 100.1.1.100 standby
HRP
#FW1
[FW1]hrp interface Eth-Trunk 0 remote 192.168.100.2
[FW1]hrp enable
[FW1]hrp mirror session enable
HRP_M[FW1]hrp auto-sync config static-route (+B)
#FW2
[FW2]hrp interface Eth-Trunk 0 remote 192.168.100.1
[FW2]hrp enable
[FW2]hrp mirror session enable
HRP_S[FW2]hrp standby-device
Link-Group
#FW1
HRP_M[FW1]interface GigabitEthernet 1/0/1 (+B)
HRP_M[FW1-GigabitEthernet1/0/1]link-group 1
HRP_M[FW1]interface GigabitEthernet 1/0/0 (+B)
HRP_M[FW1-GigabitEthernet1/0/0]link-group 1
#FW2
HRP_S[FW2]interface GigabitEthernet 1/0/0
HRP_S[FW2-GigabitEthernet1/0/0]link-group 1
HRP_S[FW2]interface GigabitEthernet 1/0/1
HRP_S[FW2-GigabitEthernet1/0/1]link-group 1验证:


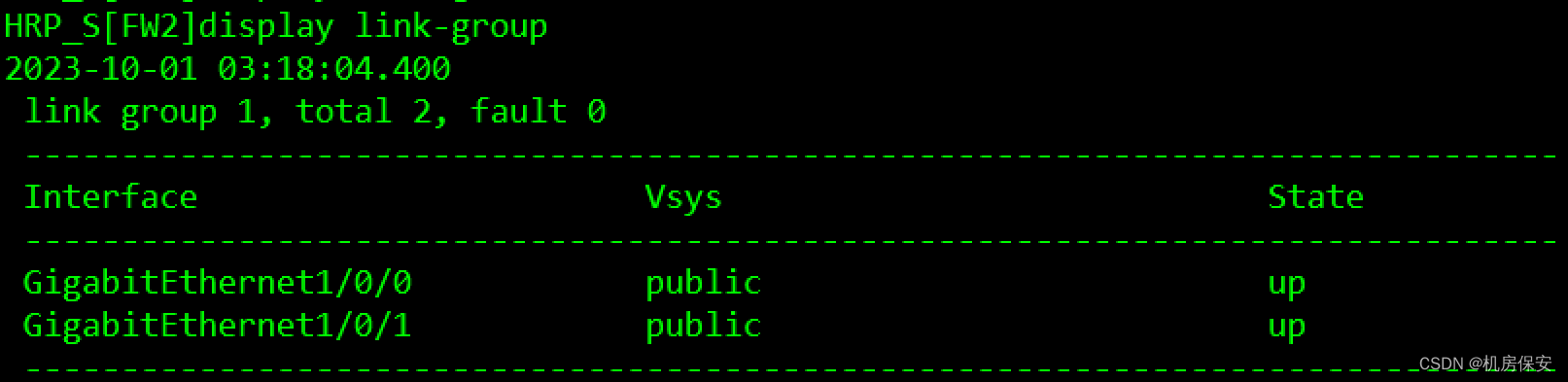
3.1.7 任务7:配置防火墙NAT
为了使私网中192.168.102.0/24网段的用户可以正常访问Internet,需要在防火墙上配置源NAT策略,除了公网接口的IP地址外,公司还向ISP申请了7个IP地址(100.1.1.4~100.1.1.10)作为私网地址转换后的公网地址,因公司员工访问互联网的需求较多,需要开启允许端口转换。
配置过程:
NAT
#FW1
HRP_M[FW1]nat address-group PAT
HRP_M[FW1-address-group-PAT]mode pat (+B)
HRP_M[FW1-address-group-PAT]section 0 100.1.1.4 100.1.1.10
HRP_M[FW1]nat-policy (+B)
HRP_M[FW1-policy-nat]rule name No_PAT (+B)
HRP_M[FW1-policy-nat-rule-PAT]source-zone trust (+B)
HRP_M[FW1-policy-nat-rule-PAT]destination-zone ISP (+B)
HRP_M[FW1-policy-nat-rule-PAT]source-address 192.168.102.0 mask 255.255.255.0 (+B)
HRP_M[FW1-policy-nat-rule-PAT]action source-nat address-group PAT (+B)
安全策略
#FW1
HRP_M[FW1]interface GigabitEthernet 1/0/1.104 (+B)
HRP_M[FW1-GigabitEthernet1/0/1.104]service-manage ping permit (+B)
HRP_M[FW1]interface GigabitEthernet 1/0/0 (+B)
HRP_M[FW1-GigabitEthernet1/0/0]service-manage ping permit (+B)
HRP_M[FW1]interface GigabitEthernet 1/0/1.106 (+B)
HRP_M[FW1-GigabitEthernet1/0/1.106]service-manage ping permit (+B)
HRP_M[FW1]security-policy (+B)
HRP_M[FW1-policy-security]rule name ISP (+B)
HRP_M[FW1-policy-security-rule-ISP]destination-zone ISP (+B)
HRP_M[FW1-policy-security-rule-ISP]source-address 100.1.1.0 mask 255.255.255.0 (+B)
HRP_M[FW1-policy-security-rule-ISP]destination-address 100.1.1.1 mask 255.255.255.255 (+B)
HRP_M[FW1-policy-security-rule-ISP]destination-address 200.1.1.1 mask 255.255.255.255 (+B)
HRP_M[FW1-policy-security-rule-ISP]action permit (+B)
HRP_M[FW1-policy-security]rule name ospf (+B)
HRP_M[FW1-policy-security-rule-ospf]source-zone local (+B)
HRP_M[FW1-policy-security-rule-ospf]destination-zone trust (+B)
HRP_M[FW1-policy-security-rule-ospf]source-address 192.168.104.1 mask 255.255.255.255 (+B)
HRP_M[FW1-policy-security-rule-ospf]source-address 192.168.106.1 mask 255.255.255.255 (+B)
HRP_M[FW1-policy-security-rule-ospf]destination-address 192.168.104.2 mask 255.255.255.255 (+B)
HRP_M[FW1-policy-security-rule-ospf]destination-address 192.168.106.2 mask 255.255.255.255 (+B)
HRP_M[FW1-policy-security-rule-ospf]action permit (+B)
3.1.8 任务8 :配置WLAN
- 根据表3-2 AC数据规划表配置AC1、AC2管理地址VLANIF103,实现AC间互通。
- 配置WLAN基本业务,确保STA能够正确获取IP地址,可以访问互联网(即能ping通1.1.1.1)。
- 使用VRRP实现双机热备份功能,实现当AC1故障时,AC2接替AC1继续工作,保证用户业务不中断,VRRP组:1,接口IP:10.11.103.2和10.11.103.3,虚拟IP:10.11.103.1。
- 在WLAN覆盖区域STA终端实现二层漫游。
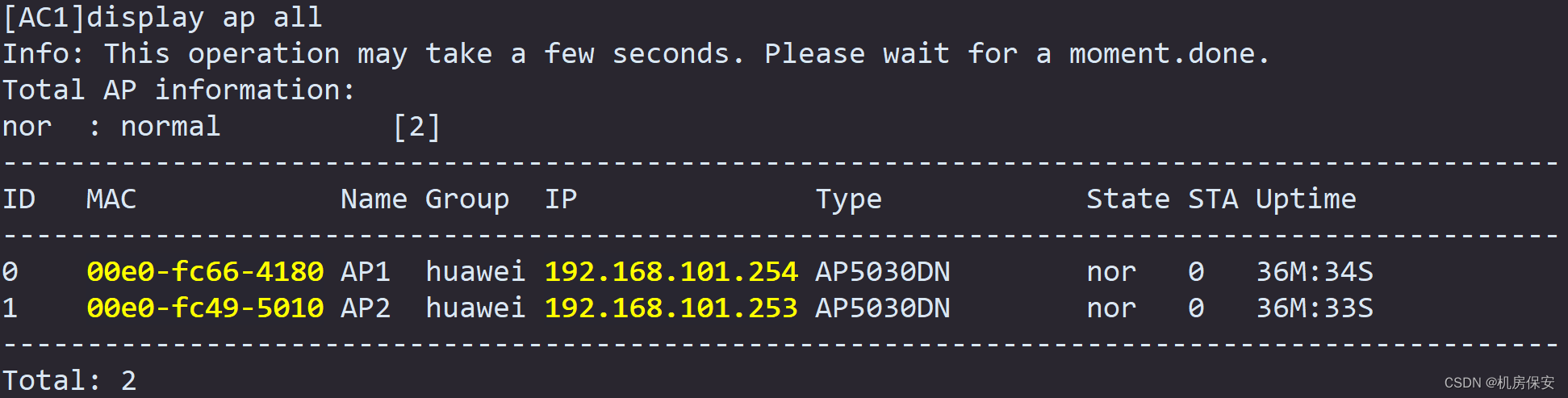
AC和AP建立通信
#AC1
[AC1]ip route-static 0.0.0.0 0.0.0.0 10.11.103.4
#AC2
[AC2]ip route-static 0.0.0.0 0.0.0.0 10.11.103.4
AC-VRRP
#AC1
[AC1]interface Vlanif 103
[AC1-Vlanif103]vrrp vrid 1 virtual-ip 10.11.103.1
[AC1-Vlanif103]vrrp vrid 1 priority 120
[AC1-Vlanif103]admin-vrrp vrid 1
#AC2
[AC2]interface Vlanif 103
[AC2-Vlanif103]vrrp vrid 1 virtual-ip 10.11.103.1
[AC2-Vlanif103]admin-vrrp vrid 1
WLAN业务配置
#AC1
[AC1]capwap source ip-address 10.11.103.1
[AC2]wlan
[AC1-wlan-view]ap-group name huawei
[AC1-wlan-ap-group-huawei]quit
[AC1-wlan-view]regulatory-domain-profile name huawei
[AC1-wlan-regulate-domain-huawei]country-code CN
[AC1-wlan-view]ap-id 0 ap-mac 00e0-fc66-4180
[AC1-wlan-ap-0]ap-name AP1
[AC1-wlan-ap-0]ap-group huawei
[AC1-wlan-view]ap-id 1 ap-mac 00e0-fc49-5010
[AC1-wlan-ap-1]ap-name AP2
[AC1-wlan-ap-1]ap-group huawei
[AC1-wlan-view]ssid-profile name huawei
[AC1-wlan-ssid-prof-huawei]ssid huaweiICT
[AC1-wlan-view]security-profile name huawei
[AC1-wlan-sec-prof-huawei]security wpa-wpa2 psk pass-phrase huawei@123 aes
[AC1-wlan-view]vap-profile name huawei
[AC1-wlan-vap-prof-huawei]forward-mode direct-forward
[AC1-wlan-vap-prof-huawei]service-vlan vlan-id 102
[AC1-wlan-vap-prof-huawei]ssid-profile huawei
[AC1-wlan-vap-prof-huawei]security-profile huawei
[AC1-wlan-view]ap-group name huawei
[AC1-wlan-ap-group-huawei]regulatory-domain-profile huawei
[AC1-wlan-ap-group-huawei]vap-profile huawei wlan 1 radio all
#AC2
[AC2]capwap source ip-address 10.11.103.1
[AC2]wlan
[AC2-wlan-view]ap-group name huawei
[AC2-wlan-ap-group-huawei]quit
[AC2-wlan-view]regulatory-domain-profile name huawei
[AC2-wlan-regulate-domain-huawei]country-code CN
[AC2-wlan-view]ap-id 0 ap-mac 00e0-fc66-4180
[AC2-wlan-ap-0]ap-name AP1
[AC2-wlan-ap-0]ap-group huawei
[AC2-wlan-view]ap-id 1 ap-mac 00e0-fc49-5010
[AC2-wlan-ap-1]ap-name AP2
[AC2-wlan-ap-1]ap-group huawei
[AC2-wlan-view]ssid-profile name huawei
[AC2-wlan-ssid-prof-huawei]ssid huaweiICT
[AC2-wlan-view]security-profile name huawei
[AC2-wlan-sec-prof-huawei]security wpa-wpa2 psk pass-phrase huawei@123 aes
[AC2-wlan-view]vap-profile name huawei
[AC2-wlan-vap-prof-huawei]forward-mode direct-forward
[AC2-wlan-vap-prof-huawei]service-vlan vlan-id 102
[AC2-wlan-vap-prof-huawei]ssid-profile huawei
[AC2-wlan-vap-prof-huawei]security-profile huawei
[AC2-wlan-view]ap-group name huawei
[AC2-wlan-ap-group-huawei]regulatory-domain-profile huawei
[AC2-wlan-ap-group-huawei]vap-profile huawei wlan 1 radio all
#AC HSB配置
#AC1
[AC1]hsb-service 0
[AC1-hsb-service-0]service-ip-port local-ip 10.11.103.2 peer-ip 10.11.103.3 local-data-port 10241 peer-data-port 10241
[AC1-hsb-service-0]service-keep-alive detect retransmit 3 interval 6
[AC1]hsb-group 0
[AC1-hsb-group-0]track vrrp vrid 1 interface Vlanif 103
[AC1-hsb-group-0]bind-service 0
[AC1]hsb-service-type access-user hsb-group 0
[AC1]hsb-service-type access-user dhcp 0
[AC1]hsb-service-type access-user ap 0
[AC1]hsb-group 0
[AC1]hsb enable
#AC2
[AC2]hsb-service 0
[AC2-hsb-service-0]service-ip-port local-ip 10.11.103.3 peer-ip 10.11.103.2 local-data-port 10241 peer-data-port 10241
[AC2-hsb-service-0]service-keep-alive detect retransmit 3 interval 6
[AC2]hsb-group 0
[AC2-hsb-group-0]track vrrp vrid 1 interface Vlanif 103
[AC2-hsb-group-0]bind-service 0
[AC2]hsb-service-type access-user hsb-group 0
[AC2]hsb-service-type access-user dhcp 0
[AC2]hsb-service-type access-user ap 0
[AC2]hsb-group 0
[AC2]hsb enable
#智能漫游
#AC1
[AC1]wlan
[AC1-wlan-view]rrm-profile name huawei
[AC1-wlan-rrm-prof-huawei]smart-roam enable
[AC1-wlan-rrm-prof-huawei]smart-roam roam-threshold snr 15
[AC1-wlan-view]radio-2g-profile name huawei
[AC1-wlan-radio-2g-prof-huawei]rrm-profile huawei
[AC1-wlan-view]radio-5g-profile name huawei
[AC1-wlan-radio-5g-prof-huawei]rrm-profile huawei
[AC1-wlan-view]ap-group name huawei
[AC1-wlan-ap-group-huawei]radio 0
[AC1-wlan-group-radio-huawei/0]radio-2g-profile huawei
[AC1-wlan-ap-group-huawei]radio 1
[AC1-wlan-group-radio-huawei/1]radio-5g-profile huawei
[AC1-wlan-ap-group-huawei]radio 2
[AC1-wlan-group-radio-huawei/2]radio-5g-profile huawei
#AC2
[AC2]wlan
[AC2-wlan-view]rrm-profile name huawei
[AC2-wlan-rrm-prof-huawei]smart-roam enable
[AC2-wlan-rrm-prof-huawei]smart-roam roam-threshold snr 15
[AC2-wlan-view]radio-2g-profile name huawei
[AC2-wlan-radio-2g-prof-huawei]rrm-profile huawei
[AC2-wlan-view]radio-5g-profile name huawei
[AC2-wlan-radio-5g-prof-huawei]rrm-profile huawei
[AC2-wlan-view]ap-group name huawei
[AC2-wlan-ap-group-huawei]radio 0
[AC2-wlan-group-radio-huawei/0]radio-2g-profile huawei
[AC2-wlan-ap-group-huawei]radio 1
[AC2-wlan-group-radio-huawei/1]radio-5g-profile huawei
[AC2-wlan-ap-group-huawei]radio 2
[AC2-wlan-group-radio-huawei/2]radio-5g-profile huawei验证:


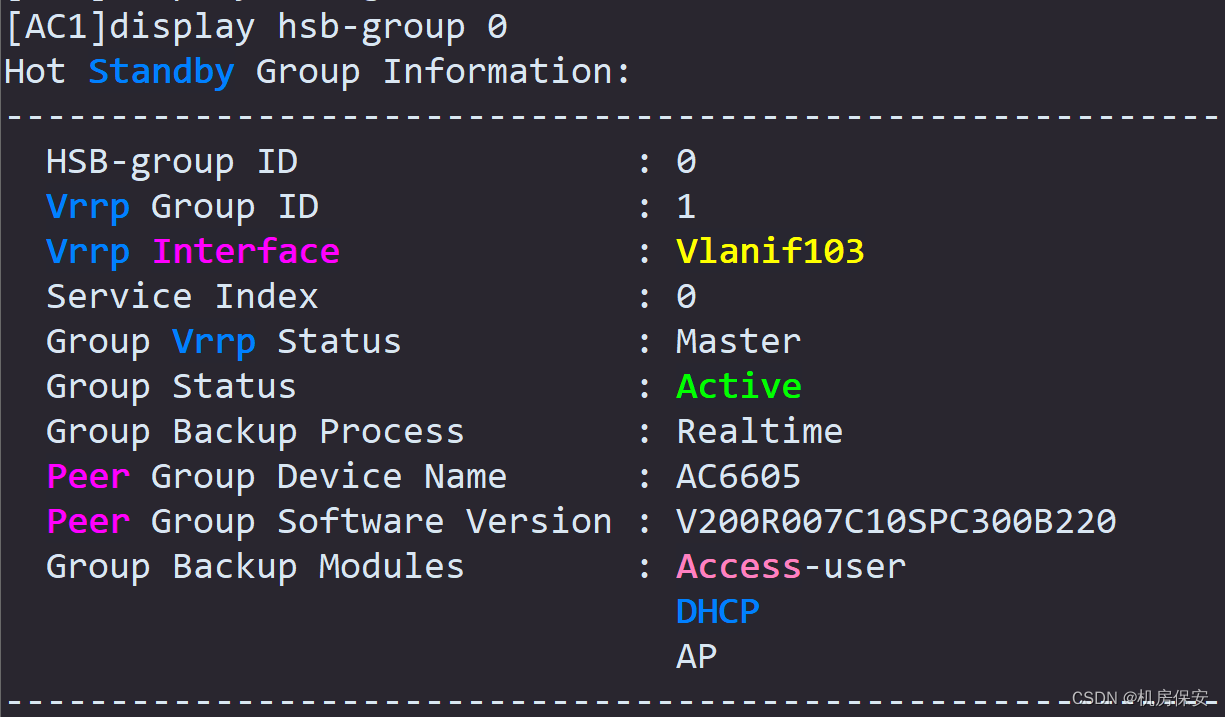
3.1.9 任务9:配置QOS
- 在交换机SW1的GE0/0/1出方向,周一至周五的8:00-18:00点,对TCP目的端口号6881-6999的流量进行限速,承诺的平均速度为2Mbps。
- 在交换机SW1的GE0/0/2和GE0/0/3入方向,对来自PC1和STA的报文DSCP优先级重标记为AF43(38)。
配置过程:
#SW1
[SW1]time-range huawei 8:00 to 18:00 working-day
[SW1]acl 3000
[SW1-acl-adv-3000]rule permit tcp source-port range 6881 6999 destination-port range 6881 6999 time-range huawei
[SW1]interface GigabitEthernet 0/0/1
[SW1-GigabitEthernet0/0/1]traffic-limit outbound acl 3000 cir 4096
[SW1]traffic classifier huawei
[SW1-classifier-huawei]if-match vlan-id 102
[SW1]traffic behavior huawei
[SW1-behavior-huawei]remark vlan-id 102
[SW1-behavior-huawei]remark dscp af43
[SW1]traffic policy huawei
[SW1-trafficpolicy-huawei]classifier huawei behavior huawei
[SW1]interface GigabitEthernet 0/0/2
[SW1-GigabitEthernet0/0/2]traffic-policy huawei inbound
[SW1]interface GigabitEthernet 0/0/3
[SW1-GigabitEthernet0/0/3]traffic-policy huawei inbound 3.1.10 任务10:配置网络自动化
公司现有一台CE6800设备,管理IP地址为192.168.56.100/24。现在需要在客户端Client编写 自动化脚本,抓取设备当前配置文件,图2-1 网络拓扑重客户端Client即装有Python 的主机 (即模拟器所在的主机)
- 配置CE交换机,设备管理地址为VLANIF1:192.168.56.100/24。
- 使能CE交换机的STenlet功能及配置VTY用户界面。
- 在CE交换机创建本地用户python,将用户加入管理员组,并配置用户服务类型为SSH。
- 在CE交换机创建SSH用户,并配置认证方式为简单密码认证,服务类型为SSH。
- 在客户端client主机上运行jupyter Notebook(andconda3)软件,编写Python代码,通过自动化脚本登录CE交换机并显示CE交换机的配置信息。
- 保存Python文件,命名为python_ssh.ipynb。
配置过程:
#配置管理地址
[CE6800]interface Vlanif 1
[CE6800-Vlanif1]ip address 192.168.56.100 24
#配置SSH
[CE6800]stelnet server enable
[CE6800]user-interface vty 0 4
[CE6800-ui-vty0-4]authentication-mode aaa
[CE6800-ui-vty0-4]protocol inbound ssh
[CE6800]aaa
[CE6800-aaa]local-user python password irreversible-cipher Huawei@123
[CE6800-aaa]local-user python level 3
[CE6800-aaa]local-user python service-type ssh
[CE6800]rsa local-key-pair create
[CE6800]ssh user ssh_python
[CE6800]ssh user ssh_python service-type ssh
[CE6800]ssh user ssh_python authentication-type password
#python
import telnetlib
import time
host = '192.168.56.100'
username = 'ssh_python'
password = 'Huawei@123'
tn = telnetlib.Telnet(host)
tn.read_until(b"username:")
tn.write(user.encode('ascii')+b"\n")
tn.read_until(b"Password:")
tn.write(Password.encode('ascii')+b"\n")
tn.write(b"dis cu \n")
tn.write(b" \n")
tn.write(b"return \n")
tn.write(b"quit\n")
附加:在此场景中CE交换机是个大坑,默认接口状态全为down,需要手工把接口打开
[CE6800]interface GE 1/0/0
[CE6800-GE1/0/0]undo shutdown
[CE6800]interface GE 1/0/1
[CE6800-GE1/0/1]undo shutdown
[CE6800]interface GE 1/0/2
[CE6800-GE1/0/2]undo shutdown
[CE6800]interface GE 1/0/3
[CE6800-GE1/0/3]undo shutdown电脑没有python所以没有测试,大概思路是这样的。。。
3.2 分支机构网络配置
3.2.1 任务1:配置IP地址
根据表2-3 IP地址规划表,配置IP地址。
3.2.2 任务2:配置OSPF路由协议
- 在FW3、R3、R4、SW5上运行OSPF,设置OSPF进程为1。
- 防火墙GE1/0/2、GE1/0/1、R3 GE0/0/0、GE0/0/1、R4 GE0/0/0、GE0/0/1、SW5 GE0/0/1、GE0/0/2、Eth0/0/3接口开启OSPF,并将这些接口加入区域。
- 要求PC2不能接收OSPF报文。
- 要求从PC2访问互联网(ping 2.2.2.2)流量优先从R3路由器转发,从互联网到PC2的流量从R4路由器转发。
配置过程:
#FW3
[FW3]ip route-static 0.0.0.0 0 200.1.1.1
[FW3]ospf 1
[FW3-ospf-1]default-route-advertise type 1
[FW3-ospf-1]area 0
[FW3]interface GigabitEthernet 1/0/2
[FW3-GigabitEthernet1/0/2]ospf enable 1 area 0
[FW3-GigabitEthernet1/0/1]ospf cost 5
[FW3]interface GigabitEthernet 1/0/1
[FW3-GigabitEthernet1/0/1]ospf enable 1 area 0
#R3
[R3]ospf 1
[R3-ospf-1]area 0
[R3]interface GigabitEthernet 0/0/0
[R3-GigabitEthernet0/0/0]ospf enable 1 area 0
[R3-GigabitEthernet0/0/0]ospf cost 5
[R3]interface GigabitEthernet 0/0/1
[R3-GigabitEthernet0/0/1]ospf enable 1 area 0
#R4
[R4]ospf 1
[R4-ospf-1]area 0
[R4]interface GigabitEthernet 0/0/1
[R4-GigabitEthernet0/0/1]ospf cost 5
[R4-GigabitEthernet0/0/1]ospf enable 1 area 0
[R4]interface GigabitEthernet 0/0/0
[R4-GigabitEthernet0/0/0]ospf enable 1 area 0
#SW5
[SW5]ospf 1
[SW5-ospf-1]silent-interface Vlanif 5
[SW5-ospf-1]area 0
[SW5]interface Vlanif 3
[SW5-Vlanif3]ospf enable 1 area 0
[SW5]interface Vlanif 4
[SW5-Vlanif4]ospf enable 1 area 0
[SW5-Vlanif4]ospf cost 5
[SW5]interface Vlanif 5
[SW5-Vlanif5]ospf enable 1 area 0
3.2.3 任务3:防火墙配置
- 将FW3 GE1/0/0的接口加入untrust区域,将GE1/0/2和GE1/0/1加入trust区域。
- 配置安全策略,使分支机构用户(PC2)能实现访问ISP网络(1.1.1.1)。
注:禁止将FW1、FW2、FW3安全策略全放通,且安全策略配置需细化。
配置过程:
#FW3
#安全区域
[FW3]firewall zone untrust
[FW3-zone-untrust]add interface GigabitEthernet 1/0/0
[FW3]firewall zone trust
[FW3-zone-trust]add interface GigabitEthernet 1/0/1
[FW3-zone-trust]add interface GigabitEthernet 1/0/2
#安全策略
[FW3]interface GigabitEthernet 1/0/0
[FW3-GigabitEthernet1/0/0]service-manage ping permit
[FW3]interface GigabitEthernet 1/0/1
[FW3-GigabitEthernet1/0/1]service-manage ping permit
[FW3]interface GigabitEthernet 1/0/2
[FW3-GigabitEthernet1/0/2]service-manage ping permit
[FW3]security-policy
[FW3-policy-security]rule name ospf
[FW3-policy-security-rule-ospf]source-zone local
[FW3-policy-security-rule-ospf]destination-zone trust
[FW3-policy-security-rule-ospf]source-address 10.10.2.1 32
[FW3-policy-security-rule-ospf]source-address 10.10.1.1 32
[FW3-policy-security-rule-ospf]destination-address 10.10.2.2 32
[FW3-policy-security-rule-ospf]destination-address 10.10.1.2 32
[FW3-policy-security-rule-ospf]service ospf
[FW3-policy-security-rule-ospf]action permit
[FW3-policy-security]rule name ISP
[FW3-policy-security-rule-ISP]source-zone local
[FW3-policy-security-rule-ISP]destination-zone untrust
[FW3-policy-security-rule-ISP]source-address 200.1.1.2 mask 255.255.255.255
[FW3-policy-security-rule-ISP]destination-address 200.1.1.1 mask 255.255.255.255
[FW3-policy-security-rule-ISP]destination-address 100.1.1.100 mask 255.255.255.255
[FW3-policy-security-rule-ISP]action permit
[FW3-policy-security]rule name nat
[FW3-policy-security-rule-nat]source-zone trust
[FW3-policy-security-rule-nat]destination-zone untrust
[FW3-policy-security-rule-nat]source-address 10.10.5.0 mask 255.255.255.0
[FW3-policy-security-rule-nat]action permit
[FW3]nat-policy
[FW3-policy-nat]rule name easy-ip
[FW3-policy-nat-rule-easy-ip]source-zone trust
[FW3-policy-nat-rule-easy-ip]destination-zone untrust
[FW3-policy-nat-rule-easy-ip]source-address 10.10.5.0 mask 255.255.255.0
[FW3-policy-nat-rule-easy-ip]action source-nat easy-ip 验证:

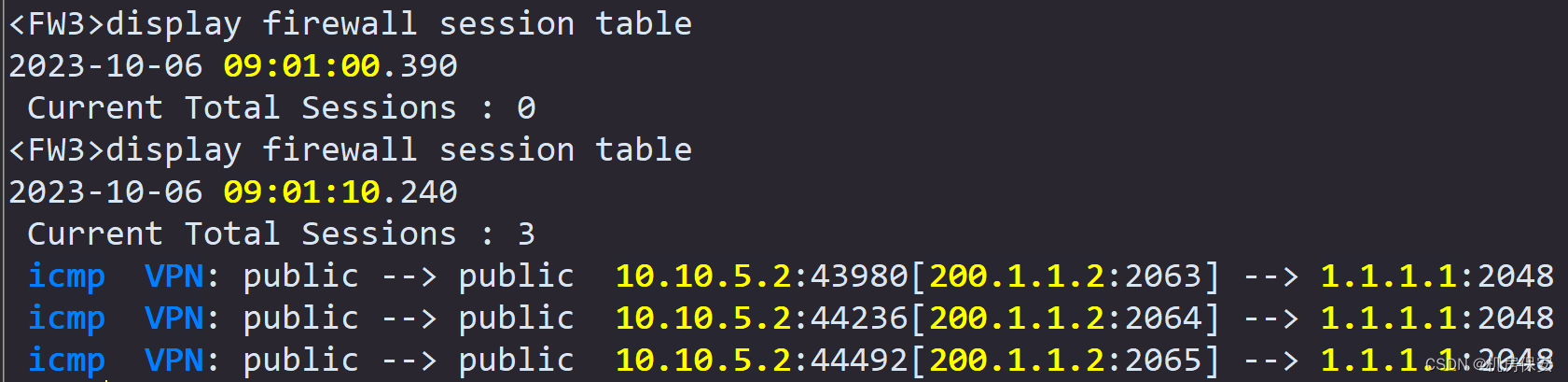
3.3 ISP网络配置
3.3.1 任务1:配置IP地址
根据2-3 IP地址规划表配置路由器IP地址。
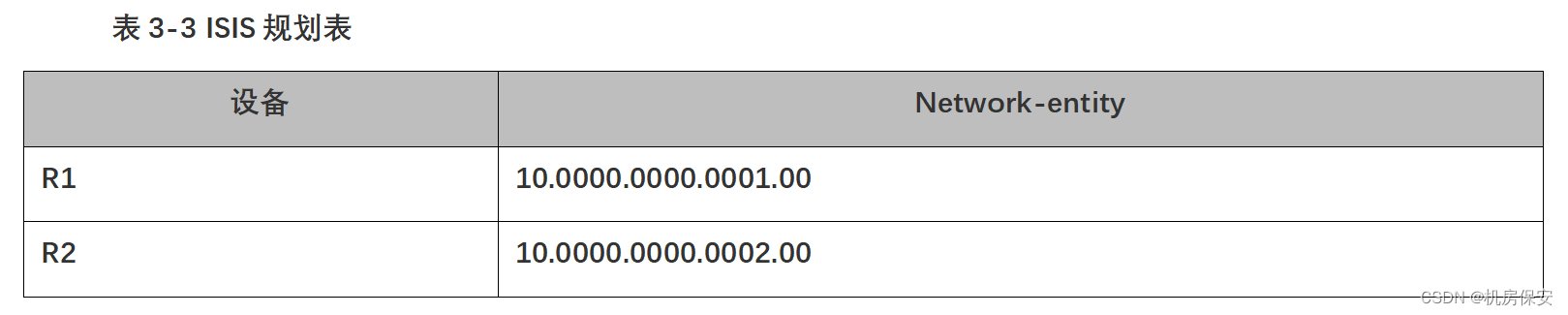
3.3.2 任务2:配置ISIS路由协议
- 根据表3-3 ISIS规划表,配置ISIS路由协议,修改R1和R2为level-2路由器。
- 为提高安全性,配置ISIS接口认证,IS-IS接口的认证模式为简单模式,密码为Huawei@123。
配置过程:
#AR1
[R1]isis 1
[R1-isis-1]network-entity 10.0000.0000.0001.00
[R1-isis-1]is-level level-2
[R1-isis-1]import-route direct
[R1]interface GigabitEthernet 0/0/0
[R1-GigabitEthernet0/0/0]isis enable 1
[R1-GigabitEthernet0/0/0]isis authentication-mode simple Huawei@123
[R1]interface LoopBack 0
[R1-LoopBack0]isis enable 1
#AR2
[R2]isis 1
[R2-isis-1]network-entity 10.0000.0000.0002.00
[R2-isis-1]is-level level-2
[R2-isis-1]import-route direct
[R2]interface GigabitEthernet 0/0/0
[R2-GigabitEthernet0/0/0]isis enable 1
[R2-GigabitEthernet0/0/0]isis authentication-mode simple Huawei@123
[R2]interface LoopBack 0
[R2-LoopBack0]isis enable 1 3.4 总部与分支机构通信配置
3.4.1 任务1:配置IPSec VPN
配置高可靠的IPSec VPN,以VRRP IP地址建立IPSec VPN。
- 在FW1上配置高级ACL 3000,定义总部到分支机构的受保护流量(源:192.168.102.0/24,目的:10.10.0.0/16)
- 在FW3上配置高级ACL 3000,定义分支机构到总部的受保护流量(源:10.10.0.0/16,目的:192.168.102.0/24)
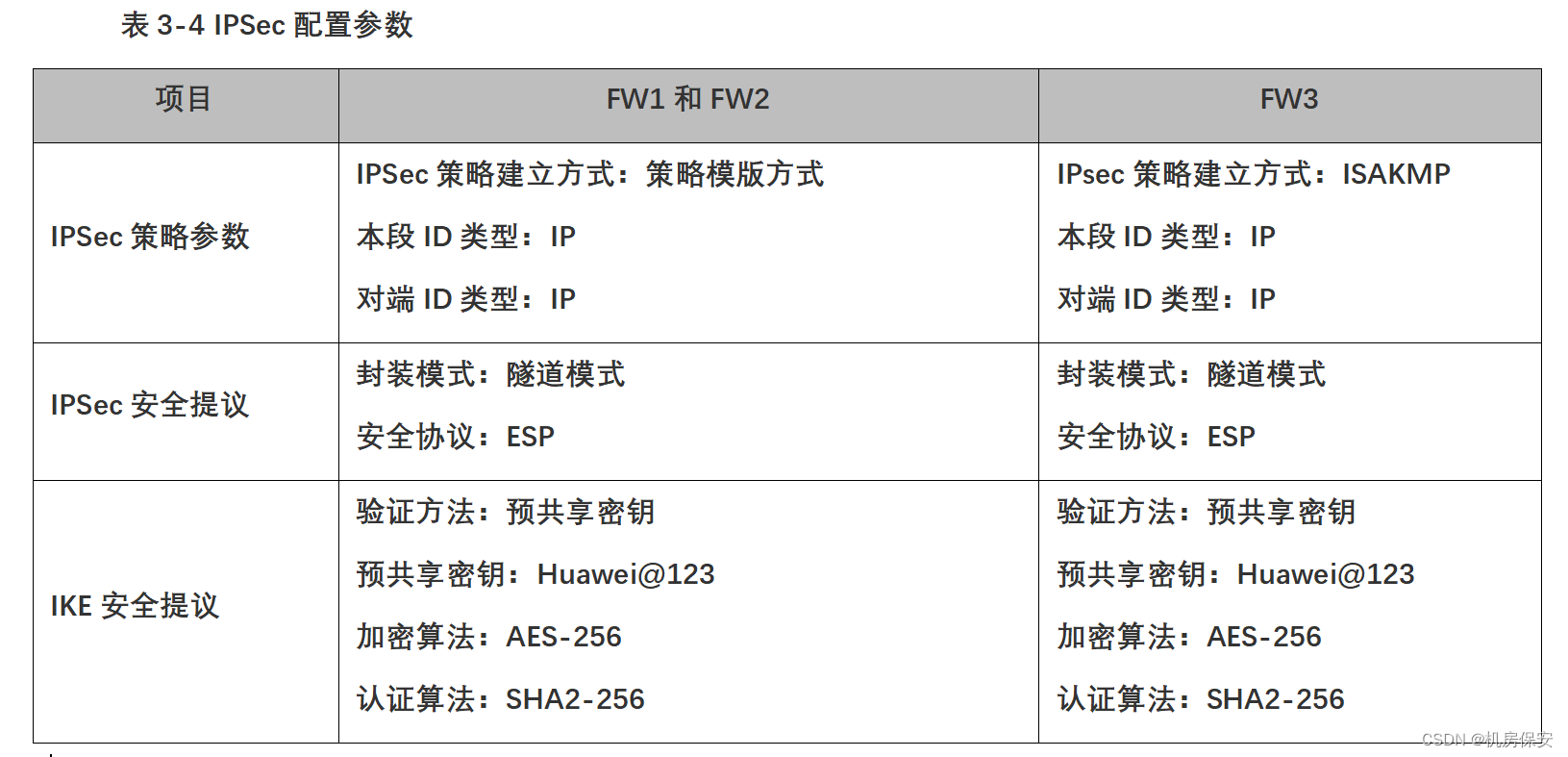
- 公司总部和分支机构通过建立IPSec VPN实现公司内网用户之间互访,采用IKE预共享密钥方式建立IPSec隧道,具体参数请见表3-4 IPSec配置参数。
配置过程:
#FW1
配置感兴趣流
HRP_M[FW1]acl 3000 (+B)
HRP_M[FW1-acl-adv-3000]rule permit ip source 192.168.102.0 0.0.0.255 destination 10.10.0.0 0.0.255.255 (+B)
配置ISAKMP服务端口
HRP_M[FW1]ip service-set ISAKMP type object (+B)
HRP_M[FW1-object-service-set-ISAKMP]service 0 protocol udp source-port 500 destination-port 500 (+B)
放行ISAKMP、ESP服务
HRP_M[FW1]security-policy (+B)
HRP_M[FW1-policy-security]rule name ISP (+B)
HRP_M[FW1-policy-security-rule-ISP]service ISAKMP (+B)
HRP_M[FW1-policy-security-rule-ISP]service esp (+B)
HRP_M[FW1-policy-security-rule-ISP]action permit (+B)
配置IPSec安全提议
HRP_M[FW1]ipsec proposal huawei (+B)
HRP_M[FW1-ipsec-proposal-huawei]encapsulation-mode tunnel (+B)
HRP_M[FW1-ipsec-proposal-huawei]esp encryption-algorithm aes-256 (+B)
HRP_M[FW1-ipsec-proposal-huawei]esp authentication-algorithm sha2-256 (+B)
配置IKE安全提议
HRP_M[FW1]ike proposal 10 (+B)
HRP_M[FW1-ike-proposal-10]authentication-method pre-share (+B)
HRP_M[FW1-ike-proposal-10]encryption-algorithm aes-256 (+B)
HRP_M[FW1-ike-proposal-10]authentication-algorithm sha2-256 (+B)
配置IEK Peer
HRP_M[FW1]ike peer huawei (+B)
HRP_M[FW1-ike-peer-huawei]pre-shared-key Huawei@123
HRP_M[FW1-ike-peer-huawei]ike-proposal 10 (+B)
配置IPSec策略模板
HRP_M[FW1]ipsec policy-template huawei 10 (+B)
HRP_M[FW1-ipsec-policy-templet-huawei-10]security acl 3000 (+B)
HRP_M[FW1-ipsec-policy-templet-huawei-10]ike-peer huawei (+B)
HRP_M[FW1-ipsec-policy-templet-huawei-10]proposal huawei (+B)
HRP_M[FW1-ipsec-policy-templet-huawei-10]tunnel local 100.1.1.100 (+B)
HRP_M[FW1]ipsec policy huawei1 10 isakmp template huawei (+B)
HRP_M[FW1]interface GigabitEthernet 1/0/0 (+B)
HRP_M[FW1-GigabitEthernet1/0/0]ipsec policy huawei1 (+B)
#FW3
[FW3]acl 3000
[FW3-acl-adv-3000]rule permit ip source 10.10.0.0 0.0.255.255 destination 192.168.102.0 0.0.0.255
[FW3]ip service-set ISAKMP type object
[FW3-object-service-set-ISAKMP]service 0 protocol udp source-port 500 destination-port 500
[FW3]security-policy
[FW3-policy-security]rule name ISP
[FW3-policy-security-rule-ISP]service ISAKMP
[FW3-policy-security-rule-ISP]service esp
[FW3-policy-security-rule-ISP]action permit
[FW3]ipsec proposal huawei
[FW3-ipsec-proposal-huawei]encapsulation-mode tunnel
[FW3-ipsec-proposal-huawei]esp encryption-algorithm aes-256
[FW3-ipsec-proposal-huawei]esp authentication-algorithm sha2-256
[FW3]ike proposal 10
[FW3-ike-proposal-10]authentication-method pre-share
[FW3-ike-proposal-10]encryption-algorithm aes-256
[FW3-ike-proposal-10]authentication-algorithm sha2-256
[FW3]ike peer huawei
[FW3-ike-peer-huawei]pre-shared-key Huawei@123
[FW3-ike-peer-huawei]remote-address 100.1.1.100
[FW3-ike-peer-huawei]ike-proposal 10
[FW3]ipsec policy huawei 10 isakmp
[FW3-ipsec-policy-isakmp-huawei-10]security acl 3000
[FW3-ipsec-policy-isakmp-huawei-10]ike-peer huawei
[FW3-ipsec-policy-isakmp-huawei-10]proposal huawei
[FW3]interface GigabitEthernet 1/0/0
[FW3-GigabitEthernet1/0/0]ipsec policy huawei