
Editor: A Mao
Design: Muyou
As one of the emerging information technologies, cloud computing supports the development of the digital economy and is an important cornerstone of industrial upgrading and enterprise evolution. However, the "spring breeze" of cloud computing is not all satisfactory.
At present, going to the cloud has become an inevitable choice for Chinese enterprises' digital transformation, and it is also the only way to promote the development of Digital China and achieve high-quality growth. However, just like at the beginning of cloud computing many years ago, security issues are still an important factor that most enterprises worry about when going to the cloud.
Issues such as how enterprises safely migrate to the cloud, how to implement cloud security, and how to protect data assets on the cloud are survival and development propositions that modern enterprises must face. “As high as the road is, so high is the devil.” Compared with the past ten years, the risks, threats and challenges faced by cloud security have actually become more severe.
That's right! The world of cloud computing has never been so calm. It seems calm at first glance, but in fact there are turbulent undercurrents. So, how should enterprises efficiently and smoothly meet the requirements for maintenance and compliance, so as to truly transform the cloud into a source of power for their own development?

The origin and development of cloud insurance

As early as 2007, when most people did not know what cloud computing was, relevant national ministries and offices promulgated the " Information Security Level Protection Management Measures" to make regulations on the application of new technologies such as cloud computing, big data, and the Internet of Things. made clear requirements.
Over the years, the National Information Security Standardization Technical Committee has done a lot of fruitful work around the promotion and implementation of the above technologies.
Cloud computing security level protection system (referred to as: cloud level protection) is a standard published by the National Information Security Standardization Technical Committee. It aims to standardize the security management and professional capabilities of cloud computing service providers and ensure the security and stability of the cloud computing environment. .
At present, cloud security standards include three aspects: cloud security management model, cloud security technology system and cloud security protection system, covering the entire life cycle of cloud computing services and running through the entire process of design, implementation, operation and maintenance.
In addition to the general requirements for security, cloud protection standards add scalability requirements for new application security, requiring that security construction should be jointly guaranteed by cloud service providers and cloud tenants and rated separately. Cloud service providers and cloud tenants have different rights to computing resources. The scope of control determines the boundaries of safety responsibilities.
With the continuous development of technology and the in-depth advancement of applications, cloud protection has also been upgraded from the earliest 1.0 to 2.0. While many new contents have been expanded, the objects of level protection, protected content and protection system have also changed. Significant changes.
On the basis of the previous ones, the latest 2.0 standard pays more attention to active defense, from passive defense to safe and trustworthy, dynamic perception and comprehensive audit of the whole process before, during and after the event, realizing the full protection of information system level protection objects such as cloud computing. cover.
However, as the old saying goes, meeting standards does not mean there are no shortcomings or defects. Standards represent the bottom line rather than quality. Among the various service providers and various types of insurance plans on the market, it is often not easy for users to find the kind of safe, reliable and high-quality choice.
Cloud service national team

It is no exaggeration to say that among the many cloud computing services and cloud security providers in China, Tianyi Cloud is unique. For a long time, Tianyi Cloud has closely followed the country's major strategic directions and embarked on a path of high-quality development driven by technological innovation.
Globally, Tianyi Cloud firmly holds the "throne" of the number one operator cloud. In China, Tianyi Cloud has also ranked first in government public cloud infrastructure for three consecutive years, and has entered the top three in public cloud IaaS and public cloud IaaS+PaaS.
What is particularly eye-catching is that Tianyi Cloud accounts for 60% of the public clouds in the 40 industry sectors of the State-owned Assets Supervision and Administration Commission... In the Chinese cloud computing market surrounded by strong players, the report card handed over by Tianyi Cloud can be said to be extraordinary. Not easy.
On the track of cloud computing, the sudden emergence of cloud security has become a beautiful landscape in recent years. Data from analytical institutions predict that the global cloud security market will exceed US$13 billion in 2023.
Specifically domestically, driven by multiple factors such as the COVID-19 epidemic, digital transformation, 5G technology, and artificial intelligence, China's cloud security market has also shown a rapid growth trend. According to a survey by a consulting agency, it will reach 33 billion yuan this year.
Since its inception, Tianyi Cloud has firmly believed that cloud computing will be the foundation of a new generation of IT technology. High-quality cloud services are inseparable from network security. Therefore, Tianyi Cloud has always adhered to the development direction of paying equal attention to service capabilities and qualification compliance.

From September 11 to 17, the 2023 National Cyber Security Publicity Week with the theme of "Cyber Security for the People, Cyber Security Depends on the People" was launched nationwide. As the national team of cloud services, Tianyi Cloud has taken the lead in launching a one-stop cloud protection security construction solution, allowing users to enjoy all-round protection and easily meet the compliance requirements of protection.
This solution integrates various cloud security compliance components such as cloud firewall, terminal security EDR, cloud database audit, cloud log audit, cloud fortress, cloud vulnerability scanning and other cloud security compliance components. It has rich cloud security protection capabilities and also provides a variety of security services. Capabilities include managed detection and response services, security assurance services during important periods, emergency response services, etc., which can fully meet various needs for level protection and assist users in building a complete security operation process.
Classification guarantee compliance is the enterprise security baseline and an important means to maintain the country's critical information infrastructure. Tianyi Cloud hopes to use its leading technology to escort enterprise cloud security and equal protection construction, erect a solid barrier for thousands of industries, and contribute to maintaining national network security.
Tianyi Cloud’s security “hypermarket”

Next, we further analyze Tianyi Cloud’s one-stop cloud and other security construction solutions.
In the early stage of grade protection construction, Tianyi Cloud provides grade protection consulting services to assist customers in confirming grading objects, conducting gap assessments, and formulating Tianyi Cloud technology rectification plans based on the assessment results.
During the rectification, Tianyi Cloud launched the Cloud Level Protection Zone, which is Tianyi Cloud's cloud-native security compliance platform to meet customers' Level of Protection compliance needs. Here, through cloud-native security technology, Tianyi Cloud has built seven security atomic capabilities including next-generation firewall, WAF, host security, bastion host, database audit, log audit, vulnerability scanning, etc.
Security zones such as Tianyi Yunyun rely on rich security atomic capabilities to build global monitoring, security compliance, on-demand delivery, unified management, continuous operations and other advantages. They design cloud security protection systems from the perspective of overall security protection to protect the safe and stable operation of enterprises. Zhiyuan.
In response to different levels of over-warranty requirements, Tianyi Cloud flexibly customizes and builds "shelves" that include network security, terminal security, application security, data security, security management center and other security capabilities. Customers can purchase goods conveniently, quickly and intuitively like in a supermarket. In the same way, we can check and fill in the gaps in our own security construction.
For the majority of government and enterprise customers, Tianyi Cloud provides fixed packages and customized packages. Among them, the fixed package is divided into the basic version of the second-level guaranteed quality, the advanced version of the second-level guaranteed standard, the basic version of the third-level guaranteed standard and the advanced version of the third-level guaranteed standard. Customers who have needs for specific atomic capabilities can choose a customized package for Class A protection, check the required atomic capabilities, and quickly activate the safety Class A protection service.
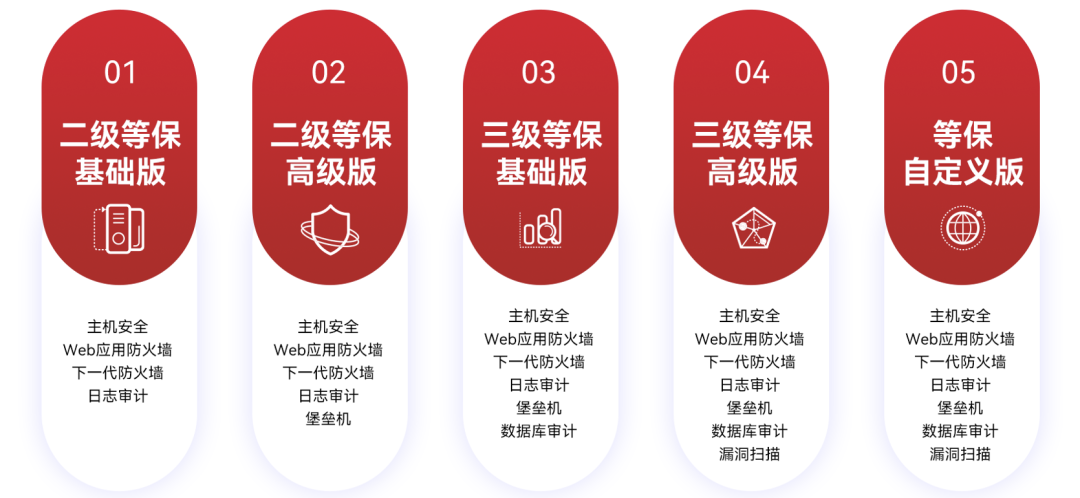
Through the advanced technical architecture, complete security capabilities, rich management functions, and flexible deployment methods of security zones such as Tianyi Cloud, users can easily achieve cloud-based security compliance while building an intelligent cloud security protection system.
At the same time, the cloud and other security zones provide security compliance capabilities such as unified security management, transmission security, and computing environment security, achieving unified management and unified operations, and overall reducing the difficulty of building such security and the complexity of daily management and operations.
While completing the construction of Class A guarantee, Tianyi cloud hosting detection and response service provides users with remotely delivered security operation capabilities. By aggregating the security atomic capability data of cloud and other guarantee zones, it can quickly detect, analyze, discover and respond to threats. Cloud experts are available 24/7 It is on duty around the clock to help users deal with unexpected security incidents. At the same time, combined with other optional services such as security assessment and emergency response, it builds integrated security protection operation capabilities for users.
In this way, throughout the entire process of graded protection construction, Tianyi Cloud provides customers with multi-dimensional opinions and implementation plans in terms of technology, processes, mechanisms, etc. through expert consultation, construction of cloud and other security zones, and security services, allowing customers to start from the lengthy process. Free from strict, complicated work and turn to core value business.
In this way, Tianyi Cloud meets the security and compliance needs of corporate customers' businesses and helps customers successfully pass the security assessment. Of course, passing the MLPS evaluation is not the ultimate goal. Fundamentally solving customers' needs for MLPS compliance and safe cloud use is the direction Tianyi Cloud continues to pursue.
Facing the future, Tianyi Cloud will continue to strengthen technological innovation in the security field, meet the needs of diverse business scenarios with rigorous and meticulous cloud and other security product solutions, and help more customers drive cloud control and use data to empower intelligence.
