JS Reverse - Tianyi Cloud Login
foreword
This article is only for technical communication. You are welcome to point out related issues. If you are interested, you can follow me. If you have related python reverse engineering problems, you can private message and discuss.
goals and objectives
Target website: Tianyi Cloud Login
Purpose: To complete the login operation of Tianyi Cloud by constructing login parameters.
related technology
This question involves two aspects of parameter construction:
- Password construction: encrypt the password when logging in, generate ciphertext and pass it to the server
- Several related parameters are constructed: no encryption algorithm is involved, and several variable values are generated after certain calculations for timestamps and random numbers.
The js knowledge points involved in this question:
(personal understanding, or wrong, follow-up understanding deepens and then adjusts)
- Webpack packaging: JS code will generate a fixed pattern after packaging it through wwebpack. This pattern has a standard three-stage pattern, 1. Self-executing function; 2. Loader; 3. Specific module code.
- When the code is called, it will pass the id corresponding to the module to the loader, and run the specified code through the loader.
1. Target parameters
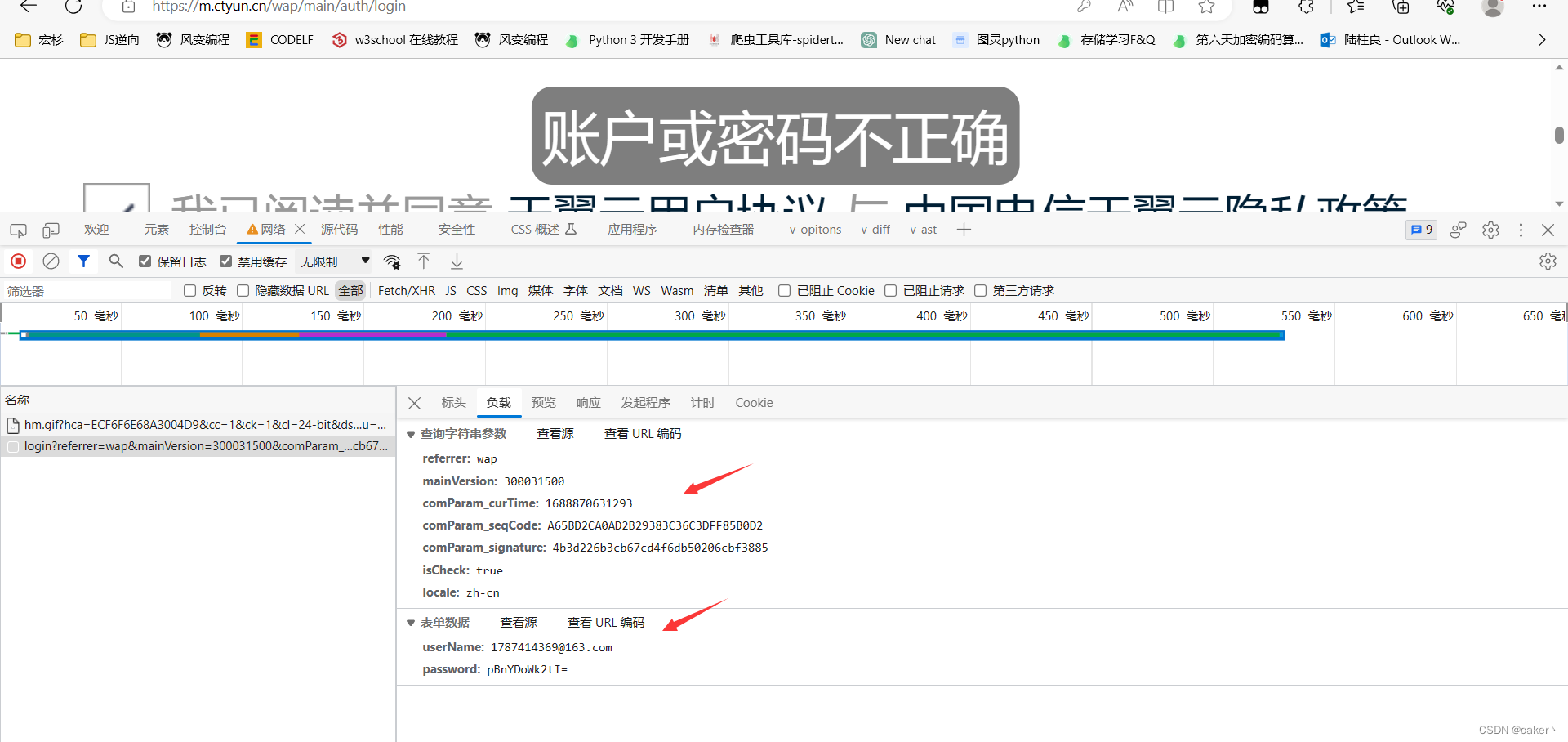
Parameter Description
- userName: username
- password: password