POC:
https://github.com/xairy/kernel-exploits/blob/master/CVE-2017-1000112/poc.c
内核commit 的patch
https://github.com/torvalds/linux/commit/85f1bd9a7b5a79d5baa8bf44af19658f7bf77bfa
| Includes KASLR and SMEP bypasses. No SMAP bypass. |
| Tested on Ubuntu trusty 4.4.0-* and Ubuntu xenial 4-8-0-* kernels. 测试环境 |
| Linux ubuntu 4.8.0-58-generic |
| Codename:xenial
https://github.com/JonathanSalwan/ROPgadget # ROPgadget --binary /usr/src/linux-source-4.13.0/linux-source-4.13.0/vmlinux >./rop.txt
#apt-get install linux-image-4.8.0-58-generic-dbgsym #apt-cache search linux-source|grep 4.8.0 #apt-get install linux-source-4.8.0 #gdb /usr/lib/debug/boot/vmlinux-4.8.0-58-generic (gdb) set disassembly-flavor intel (gdb) set ls (gdb) set substitute-path /build/linux-hwe-0IbwuF/linux-hwe-4.8.0 /usr/src/linux-source-4.8.0/linux-source-4.8.0 |
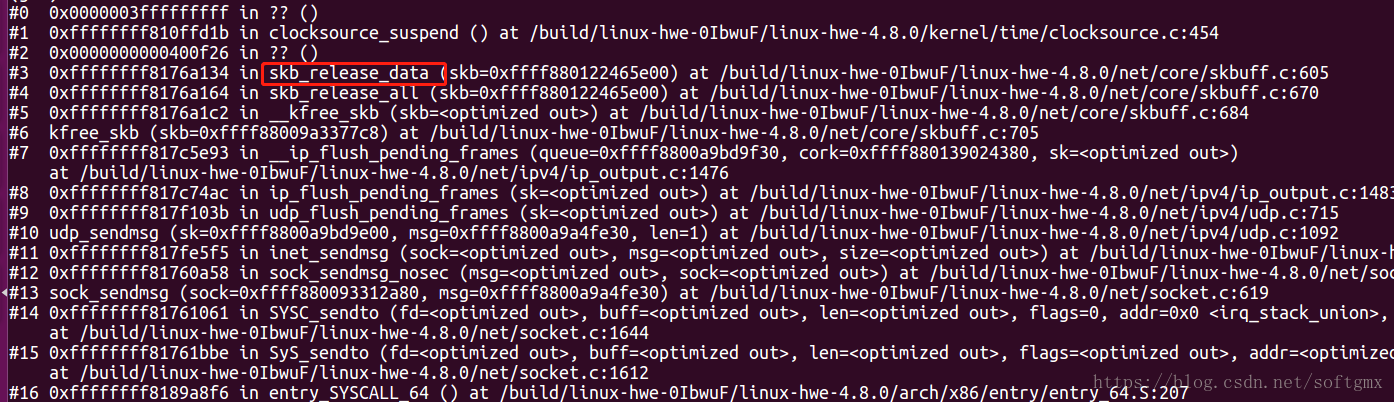
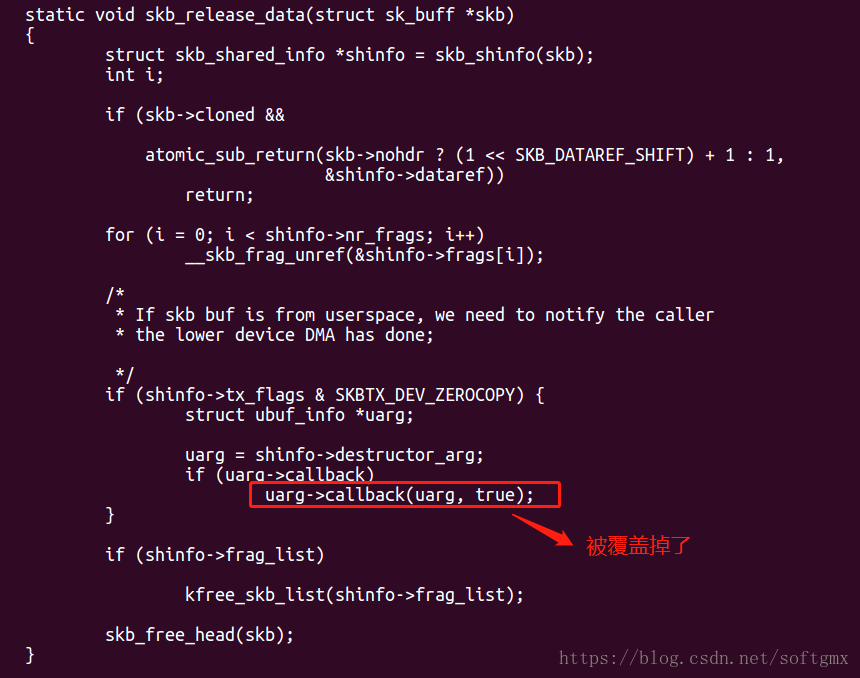
| skb_release_all=>skb_release_data=>shinfo->destructor_arg ,
|