一、防火墙识别
- 公司网络的边界一般都会有防火墙进行保护,防火墙上会有一些检测机制,我们的目的是尽量隐蔽地扫描出防火墙的规则,以及开放端口。
- 扫描原理:通过发送数据包,检查回包,可能识别端口是否经过防火墙过滤。
- 设备多种多样,结果存在一定误差。
可根据下面四种方法来判断防火墙的过滤规则:
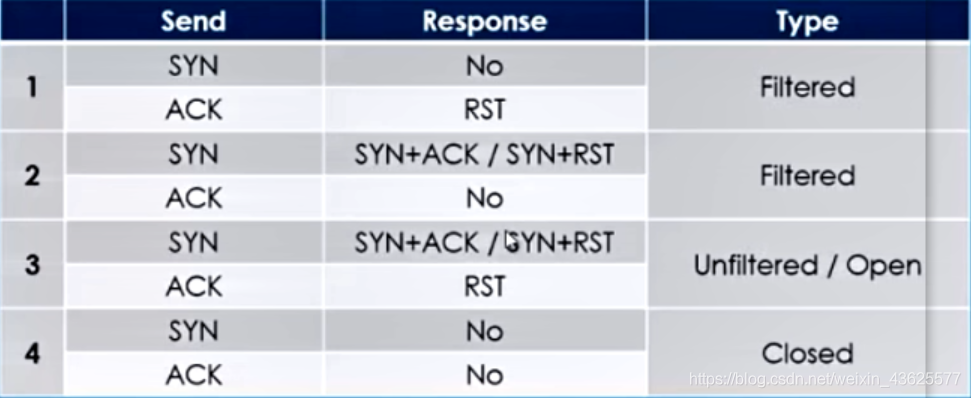
1、使用python脚本进行防火墙识别——fw_detect.py
#!/usr/bin/python
#该脚本用于实现判断防火墙的过滤端口
from scapy.all import *
import sys
if len(sys.argv) != 3:
print ("This script needs 2 args!\nExample:./fw_detect.py 192.168.0.0 80")
sys.exit()
ip = sys.argv[1]
port = int(sys.argv[2])
SYN_response = sr1(IP(dst = ip) / TCP(flags = "S", dport = port), timeout = 1, verbose = 0)
ACK_response = sr1(IP(dst = ip) / TCP(flags = "A", dport = port), timeout = 1, verbose = 0)
if (SYN_response == None) and (ACK_response == None):
print("1. Port is filtered or host is down!")
elif (SYN_response[TCP].flags == "SA" or SYN_response[TCP].flags == "SR") and (ACK_response == None):
print("2. Port is filtered!")
elif int(SYN_response[TCP].flags) == 18:
print ("Port is unfiltered and open" )
elif int(SYN_response[TCP].flags) == 20:
print ("Port is unfiltered and closed")
else:
print ("4. Port is Closed!")2、nmap
- nmap有系列防火墙过滤检测功能
root@kali:~# nmap 192.168.247.129 -p25 //默认发SYN包
Starting Nmap 7.70 ( https://nmap.org ) at 2019-05-04 17:21 CST
Nmap scan report for bogon (192.168.247.129)
Host is up (0.00027s latency).
PORT STATE SERVICE
25/tcp open smtp
MAC Address: 00:0C:29:8F:74:74 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.18 seconds
root@kali:~# nmap -sA 192.168.247.129 -p25 //-sA:发ACK包
Starting Nmap 7.70 ( https://nmap.org ) at 2019-05-04 17:21 CST
Nmap scan report for bogon (192.168.247.129)
Host is up (0.00037s latency).
PORT STATE SERVICE
25/tcp unfiltered smtp
MAC Address: 00:0C:29:8F:74:74 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.08 seconds二、负载均衡识别
负载均衡(Load Balance)其意思就是分摊到多个操作单元上进行执行,例如Web服务器、FTP服务器、企业关键应用服务器和其它关键任务服务器等,从而共同完成工作任务。
负载均衡从其应用的地理结构上分为本地负载均衡(Local Load Balance)和全局负载均衡(Global Load Balance,也叫地域负载均衡)。
- 本地负载均衡是指对本地的服务器群做负载均衡;
- 全局负载均衡是指对分别放置在不同的地理位置、有不同网络结构的服务器群间作负载均衡。
它提供了一种廉价有效透明的方法扩展网络设备和服务器的带宽、增加吞吐量、加强网络数据处理能力、提高网络的灵活性和可用性。因此,存在同一个域名对应多个IP地址(智能DNS、DNS轮询)
针对web的服务负载均衡经常使用Nginx、Apache应用层负载均衡。
1、lbd
- lbd 域名/IP
root@kali:~# lbd www.sina.com
lbd - load balancing detector 0.4 - Checks if a given domain uses load-balancing.
Written by Stefan Behte (http://ge.mine.nu)
Proof-of-concept! Might give false positives.
Checking for DNS-Loadbalancing: FOUND #一个域名被解析成两个IP地址
spool.grid.sinaedge.com has address 221.204.241.188
spool.grid.sinaedge.com has address 61.158.251.244
Checking for HTTP-Loadbalancing [Server]:
nginx
NOT FOUND
Checking for HTTP-Loadbalancing [Date]: 09:29:44, 09:29:44, 09:29:44, 09:29:44, 09:29:44, 09:29:44, 09:29:44, 09:29:45, 09:29:45, 09:29:45, 09:29:45, 09:29:45, 09:29:45, 09:29:45, 09:29:45, 09:29:45, 09:29:46, 09:29:46, 09:29:46, 09:29:46, 09:29:46, 09:29:46, 09:29:46, 09:29:46, 09:29:46, 09:29:46, 09:29:47, 09:29:47, 09:29:47, 09:29:47, 09:29:47, 09:29:47, 09:29:47, 09:29:47, 09:29:47, 09:29:48, 09:29:48, 09:29:48, 09:29:48, 09:29:48, 09:29:48, 09:29:48, 09:29:49, 09:29:49, 09:29:49, 09:29:49, 09:29:49, 09:29:49, 09:29:49, 09:29:50, NOT FOUND
Checking for HTTP-Loadbalancing [Diff]: FOUND
< X-Via-Edge: 15569621901482f568b7bf4fb9e3d2add258c
> X-Via-Edge: 15569621902842f568b7bf4fb9e3d739f6bf4
< X-Via-CDN: f=edge,s=cnc.zhengzhou.ha2ts4.201.nb.sinaedge.com,c=123.139.86.47;f=Edge,s=cnc.zhengzhou.ha2ts4.201,c=61.158.251.201
> X-Via-CDN: f=edge,s=cnc.zhengzhou.ha2ts4.197.nb.sinaedge.com,c=123.139.86.47;f=Edge,s=cnc.zhengzhou.ha2ts4.201,c=61.158.251.197
www.sina.com does Load-balancing. Found via Methods: DNS HTTP[Diff]
三、WAF识别
WAF:Web应用防护系统(也称为:网站应用级入侵防御系统。英文:Web Application Firewall,简称: WAF)。利用国际上公认的一种说法:Web应用防火墙是通过执行一系列针对HTTP/HTTPS的安全策略来专门为Web应用提供保护的一款产品。
1、wafw00f
root@kali:~# wafw00f -l #列出可检测到的WAF
^ ^
_ __ _ ____ _ __ _ _ ____
///7/ /.' \ / __////7/ /,' \ ,' \ / __/
| V V // o // _/ | V V // 0 // 0 // _/
|_n_,'/_n_//_/ |_n_,' \_,' \_,'/_/
<
...'
WAFW00F - Web Application Firewall Detection Tool
By Sandro Gauci && Wendel G. Henrique
Can test for these WAFs:
Profense
NetContinuum
Incapsula WAF
CloudFlare
NSFocus
Safedog
Mission Control Application Shield
USP Secure Entry Server
Cisco ACE XML Gateway
Barracuda Application Firewall
Art of Defence HyperGuard
BinarySec
Teros WAF
F5 BIG-IP LTM
F5 BIG-IP APM
F5 BIG-IP ASM
F5 FirePass
F5 Trafficshield
InfoGuard Airlock
Citrix NetScaler
Trustwave ModSecurity
IBM Web Application Security
IBM DataPower
DenyALL WAF
Applicure dotDefender
Juniper WebApp Secure
Microsoft URLScan
Aqtronix WebKnight
eEye Digital Security SecureIIS
Imperva SecureSphere
Microsoft ISA Server
root@kali:~# wafw00f http://www.baidu.com
^ ^
_ __ _ ____ _ __ _ _ ____
///7/ /.' \ / __////7/ /,' \ ,' \ / __/
| V V // o // _/ | V V // 0 // 0 // _/
|_n_,'/_n_//_/ |_n_,' \_,' \_,'/_/
<
...'
WAFW00F - Web Application Firewall Detection Tool
By Sandro Gauci && Wendel G. Henrique
Checking http://www.baidu.com
Generic Detection results:
The site http://www.baidu.com seems to be behind a WAF or some sort of security solution
Reason: The server returned a different response code when a string trigged the blacklist.
Normal response code is "200", while the response code to an attack is "302"
Number of requests: 12
2、nmap
root@kali:~# nmap www.baidu.com --script=http-waf-detect.nse
Starting Nmap 7.70 ( https://nmap.org ) at 2019-05-05 09:37 CST
Nmap scan report for www.baidu.com (61.135.169.125)
Host is up (0.022s latency).
Other addresses for www.baidu.com (not scanned): 61.135.169.121
Not shown: 998 filtered ports
PORT STATE SERVICE
80/tcp open http
| http-waf-detect: IDS/IPS/WAF detected:
|_www.baidu.com:80/?p4yl04d3=<script>alert(document.cookie)</script>
443/tcp open https
| http-waf-detect: IDS/IPS/WAF detected:
|_www.baidu.com:443/?p4yl04d3=<script>alert(document.cookie)</script>
Nmap done: 1 IP address (1 host up) scanned in 59.83 seconds四、nmap
虽然前面介绍了那么多的扫描方法,但是nmap仍是最强大的扫描器,现将nmap的帮助信息显示如下:
oot@kali:~# nmap
Nmap 7.70 ( https://nmap.org )
Usage: nmap [Scan Type(s)] [Options] {target specification}
TARGET SPECIFICATION: #目标主机说明
Can pass hostnames, IP addresses, networks, etc.
Ex: scanme.nmap.org, microsoft.com/24, 192.168.0.1; 10.0.0-255.1-254
-iL <inputfilename>: Input from list of hosts/networks
-iR <num hosts>: Choose random targets
--exclude <host1[,host2][,host3],...>: Exclude hosts/networks
--excludefile <exclude_file>: Exclude list from file
HOST DISCOVERY: #主机发现
-sL: List Scan - simply list targets to scan
-sn: Ping Scan - disable port scan
-Pn: Treat all hosts as online -- skip host discovery
-PS/PA/PU/PY[portlist]: TCP SYN/ACK, UDP or SCTP discovery to given ports
-PE/PP/PM: ICMP echo, timestamp, and netmask request discovery probes
-PO[protocol list]: IP Protocol Ping
-n/-R: Never do DNS resolution/Always resolve [default: sometimes]
--dns-servers <serv1[,serv2],...>: Specify custom DNS servers
--system-dns: Use OS's DNS resolver
--traceroute: Trace hop path to each host
SCAN TECHNIQUES: #扫描技术
-sS/sT/sA/sW/sM: TCP SYN/Connect()/ACK/Window/Maimon scans
-sU: UDP Scan
-sN/sF/sX: TCP Null, FIN, and Xmas scans
--scanflags <flags>: Customize TCP scan flags
-sI <zombie host[:probeport]>: Idle scan
-sY/sZ: SCTP INIT/COOKIE-ECHO scans
-sO: IP protocol scan
-b <FTP relay host>: FTP bounce scan
PORT SPECIFICATION AND SCAN ORDER: #端口说明和扫描顺序
-p <port ranges>: Only scan specified ports
Ex: -p22; -p1-65535; -p U:53,111,137,T:21-25,80,139,8080,S:9
--exclude-ports <port ranges>: Exclude the specified ports from scanning
-F: Fast mode - Scan fewer ports than the default scan
-r: Scan ports consecutively - don't randomize
--top-ports <number>: Scan <number> most common ports
--port-ratio <ratio>: Scan ports more common than <ratio>
SERVICE/VERSION DETECTION: #服务/版本探测
-sV: Probe open ports to determine service/version info
--version-intensity <level>: Set from 0 (light) to 9 (try all probes)
--version-light: Limit to most likely probes (intensity 2)
--version-all: Try every single probe (intensity 9)
--version-trace: Show detailed version scan activity (for debugging)
SCRIPT SCAN: #脚本扫描
-sC: equivalent to --script=default
--script=<Lua scripts>: <Lua scripts> is a comma separated list of
directories, script-files or script-categories
--script-args=<n1=v1,[n2=v2,...]>: provide arguments to scripts
--script-args-file=filename: provide NSE script args in a file
--script-trace: Show all data sent and received
--script-updatedb: Update the script database.
--script-help=<Lua scripts>: Show help about scripts.
<Lua scripts> is a comma-separated list of script-files or
script-categories.
OS DETECTION: #操作系统探测
-O: Enable OS detection
--osscan-limit: Limit OS detection to promising targets
--osscan-guess: Guess OS more aggressively
TIMING AND PERFORMANCE: #时间和性能
Options which take <time> are in seconds, or append 'ms' (milliseconds),
's' (seconds), 'm' (minutes), or 'h' (hours) to the value (e.g. 30m).
-T<0-5>: Set timing template (higher is faster)
--min-hostgroup/max-hostgroup <size>: Parallel host scan group sizes
--min-parallelism/max-parallelism <numprobes>: Probe parallelization
--min-rtt-timeout/max-rtt-timeout/initial-rtt-timeout <time>: Specifies
probe round trip time.
--max-retries <tries>: Caps number of port scan probe retransmissions.
--host-timeout <time>: Give up on target after this long
--scan-delay/--max-scan-delay <time>: Adjust delay between probes
--min-rate <number>: Send packets no slower than <number> per second
--max-rate <number>: Send packets no faster than <number> per second
FIREWALL/IDS EVASION AND SPOOFING: #防火墙/ID规避和欺骗
-f; --mtu <val>: fragment packets (optionally w/given MTU)
-D <decoy1,decoy2[,ME],...>: Cloak a scan with decoys
-S <IP_Address>: Spoof source address
-e <iface>: Use specified interface
-g/--source-port <portnum>: Use given port number
--proxies <url1,[url2],...>: Relay connections through HTTP/SOCKS4 proxies
--data <hex string>: Append a custom payload to sent packets
--data-string <string>: Append a custom ASCII string to sent packets
--data-length <num>: Append random data to sent packets
--ip-options <options>: Send packets with specified ip options
--ttl <val>: Set IP time-to-live field
--spoof-mac <mac address/prefix/vendor name>: Spoof your MAC address
--badsum: Send packets with a bogus TCP/UDP/SCTP checksum
OUTPUT: #输出显示
-oN/-oX/-oS/-oG <file>: Output scan in normal, XML, s|<rIpt kIddi3,
and Grepable format, respectively, to the given filename.
-oA <basename>: Output in the three major formats at once
-v: Increase verbosity level (use -vv or more for greater effect)
-d: Increase debugging level (use -dd or more for greater effect)
--reason: Display the reason a port is in a particular state
--open: Only show open (or possibly open) ports
--packet-trace: Show all packets sent and received
--iflist: Print host interfaces and routes (for debugging)
--append-output: Append to rather than clobber specified output files
--resume <filename>: Resume an aborted scan
--stylesheet <path/URL>: XSL stylesheet to transform XML output to HTML
--webxml: Reference stylesheet from Nmap.Org for more portable XML
--no-stylesheet: Prevent associating of XSL stylesheet w/XML output
MISC: #杂记
-6: Enable IPv6 scanning
-A: Enable OS detection, version detection, script scanning, and traceroute
--datadir <dirname>: Specify custom Nmap data file location
--send-eth/--send-ip: Send using raw ethernet frames or IP packets
--privileged: Assume that the user is fully privileged
--unprivileged: Assume the user lacks raw socket privileges
-V: Print version number
-h: Print this help summary page.
EXAMPLES: #举例
nmap -v -A scanme.nmap.org
nmap -v -sn 192.168.0.0/16 10.0.0.0/8
nmap -v -iR 10000 -Pn -p 80
SEE THE MAN PAGE (https://nmap.org/book/man.html) FOR MORE OPTIONS AND EXAMPLES