版权声明:本文为博主原创文章,转载需注明出处。 https://blog.csdn.net/zz_Caleb/article/details/89179278
1、re1
ida反编译看到:
所以flag就在程序中隐藏着,用strings工具进行关键字查找,找到flag: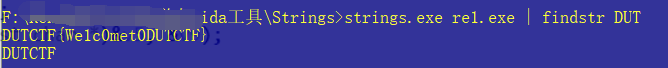
strings工具下载地址:https://docs.microsoft.com/zh-cn/sysinternals/downloads/strings
2、game
手动通关:1 2 3 4 5 6 7 8 | 8 7 6 5 4 3 2 1
ida中查找字符串:
查看这个字符串所在函数的源码:

根据这个函数和这些数字解出flag:
b = [123,32,18,98,119,108,65,41,124,80,125,38,124,111,74,49,83,108,94,108,84,6,96,83,44,121,104,110,32,95,117,101,99,123,127,119,96,48,107,71,92,29,81,107,90,85,64,12,43,76,86,13,114,1,117,126]
a = [18,64,98,5,2,4,6,3,6,48,49,65,32,12,48,65,31,78,62,32,49,32,1,57,96,3,21,9,4,62,3,5,4,1,2,3,44,65,78,32,16,97,54,16,44,52,32,64,89,45,32,65,15,34,18,16]
c = ''
for i in range(len(a)):
a[i] ^= b[i]
a[i] ^= 19
c += chr(a[i])
print(c)3、Hello,CTF
题目告诉我们,不一定是要明文比对。
平时做逆向的时候主要在于反汇编的代码的观察练习,这个题16进制解密这串字符串就行:![]()
解密结果:CrackMeJustForFun
4、open-source
给了源码:
#include <stdio.h>
#include <string.h>
int main(int argc, char *argv[]) {
if (argc != 4) {
printf("what?\n");
exit(1);
}
unsigned int first = atoi(argv[1]);
if (first != 0xcafe) {
printf("you are wrong, sorry.\n");
exit(2);
}
unsigned int second = atoi(argv[2]);
if (second % 5 == 3 || second % 17 != 8) {
printf("ha, you won't get it!\n");
exit(3);
}
if (strcmp("h4cky0u", argv[3])) {
printf("so close, dude!\n");
exit(4);
}
printf("Brr wrrr grr\n");
unsigned int hash = first * 31337 + (second % 17) * 11 + strlen(argv[3]) - 1615810207;
printf("Get your key: ");
printf("%x\n", hash);
return 0;
}
分析一下,要能跳过前面三个if语句,才能把hash输出,根据条件我们可以算出argv[1]=51966,argv[2]=25,argv[3]=h4cky0u
然后把hash输出就行了:
#include <stdio.h>
#include <string.h>
int main() {
unsigned int hash = 51966 * 31337 + (25 % 17) * 11 + strlen("h4cky0u") - 1615810207;
printf("Get your key: ");
printf("%x\n", hash);
return 0;
}
Get your key: c0ffee
5、simple-unpack
题目描述:菜鸡拿到了一个被加壳的二进制文件
winhex打开发现upx壳:
upx -d脱壳后用ida打开拿到flag:
6、logmein
题目提示我们是算法逆向,ida打开文件看伪码:
这里是一个xor的算法,脚本解密即可:
s = ''
v7 = 'harambe' #v7转为字符串的值
v8 = ':"AL_RT^L*.?+6/46'
for i in range(len(v8)):
s += chr(ord(v7[i % 7]) ^ ord(v8[i]))
print(s)这是一个大佬用c++写的: