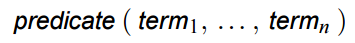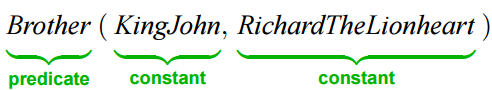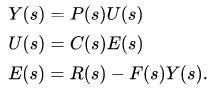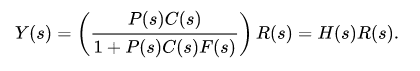1.computer architecture
1.1working principle of scalar & the time/space diagram
Normally,the instruction is divided into 5 parts,namely IF ID EXE MEM WB,in the pipelines,these parts are often used .
Let me show the concrete meaning of the above parts.
IF: (Instruction fetch)
- get the next instruction from memory
- increment program counter value by 4
ID: (Instruction Decode)
- figure out what the instruction says to do
- get values fro the named register
EXE: (Execute)
- On a memory reference,add up base and offset
- On an arithmetic instruction ,do the math
MEM : (Memory Access)
- If load or store,access memory
- If branch,replace PC with destination address
- Otherwise do nothing
WB: (Write Back)
- Place the results in the appropriate register
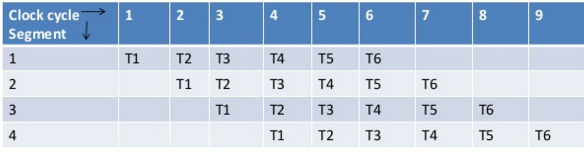
supplement: pipeline processing
It is technique of decomposing a sequential process into suboperations,with each sub-process being executed in a special dedicated segment that operates concurrently.
when reffered to space time diagram:
- a task is the total operation performed going through all segment of pipeline.(任务通过所有管道段执行的总操作)
- the behavior of a pipeline can be illustrated with a space time diagram
1.2 dependency : in the operation of instructions,it may have problems
-
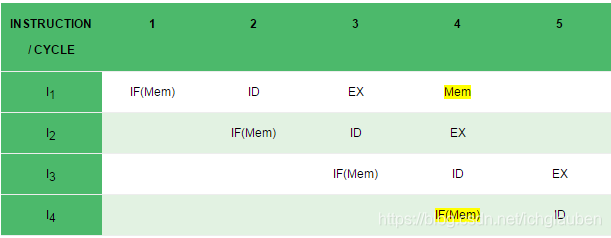
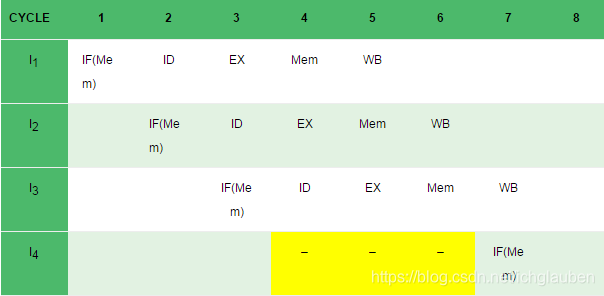
Resource dependency:
A resource conflict is a situation when more than one instruction tries to access the same resource in the same cycle. A resource can be a register, memory, or ALU. -
Structural dependency :
This dependency arises due to the resource conflict in the pipeline. A resource conflict is a situation when more than one instruction tries to access the same resource in the same cycle. A resource can be a register, memory, or ALU.
in the above scenario,in cycle 4,l1 and l4 are trying to access the same resource which introduce conflict.
solution to the structural dependency:we have to keep the instruction on wait until the required resource becomes available.
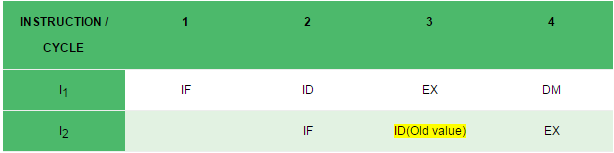
- data Dependency(Data Hazard)
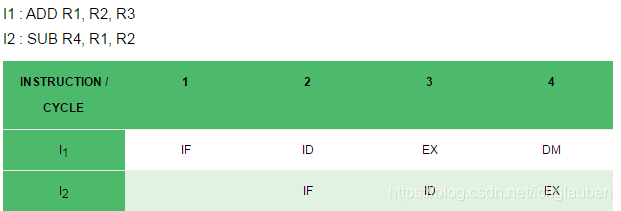
Example: Let there be two instructions I1 and I2 such that:
I1 : ADD R1, R2, R3
I2 : SUB R4, R1, R2
When the above instructions are executed in a pipelined processor, then data dependency condition will occur, which means that I2 tries to read the data before I1 writes it, therefore, I2 incorrectly gets the old value from I1.
solution to the data dependency:operand forwarding we use the interface registers present between the stages to hold intermediate output so that dependent instruction can access new value from the interface register directly.
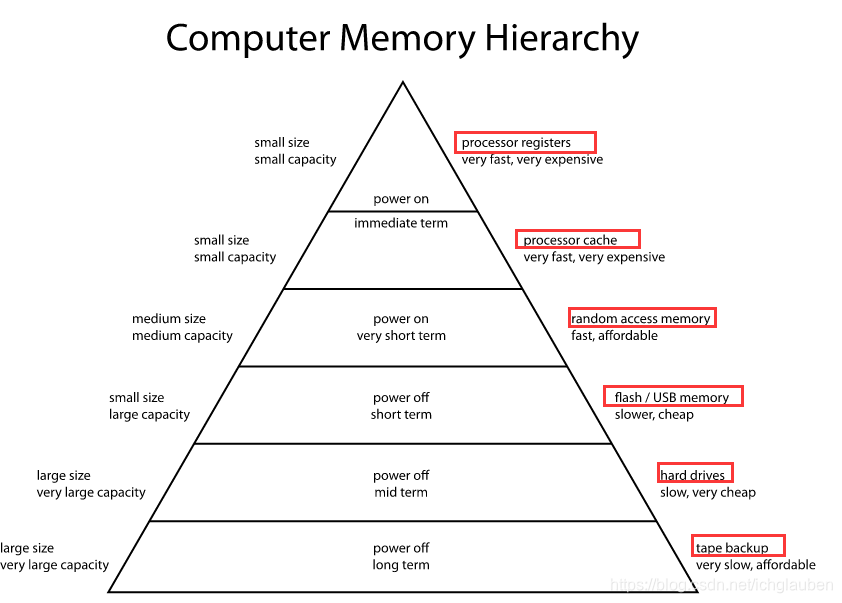
1.3 Memory hierarchy
- In computer architecture,the memory hierarchy separates computer storage into a hierarchy based on response time.
- there are 4 major storage levels
Internal-Porcessor register and cache
Main- the system RAM and controller cards
On-line mass storage-Secondary storage
off-line bulk storage - Tertiary and off-line storage- designing for high performance requires considering the restrictions of the memory hierarchy.
- designing for high performance requires considering the restrictions of the memory hierarchy.
1.4 Virtual Memory and Cache Memory
- Memory is a hardware device that is used to store the information either temporary or permanently.
- a cache memory is a high-speed memory which is used to reduce the access time for data.
- virtual memory is not exactly a physical memory of a computer instead it’s a technique that allows the execution of a large program that may not be completely placed in the main memory . It enables the programmer to execute the programs larger than the main memory.
- key differences between Virtual and Cache Memory
1.virtual memory extends the capacity of main memory virtually for the user.However,the cache memory makes the accessing of data faster for CPU
2.Cache is a memory storage unit whereas as the Virtual Memory is a technique
2.Computer Organization Principle
2.1 Hardware System Architecture
- Von Neumann architecture
it’s a computer architecture based on a 1945 description by the mathematician and physicist John von Neumann
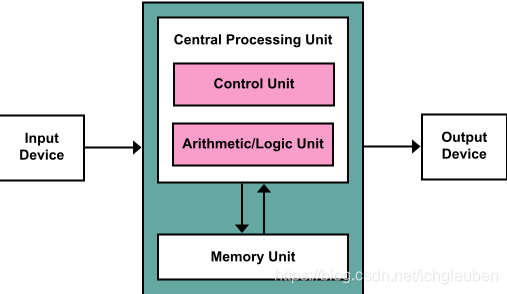
The architecture contains: - A processing unit that contains an arithmetic logic unit and processor registers
- A control unit that contains an instruction register and program counter
- Memory that stores data and instructions
- External mass storage
- IO mechanisms
2.2 complement arthmetic (计算)
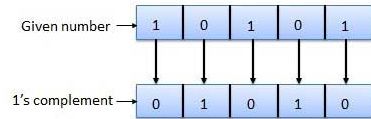
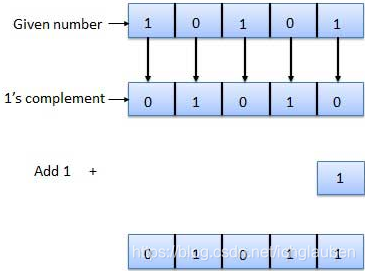
- 1’s complement(complement is used in the digital computers in order to simplify the subtraction operation)
The 1’s complement of a binary number is defined as the value obtained by inverting all the bits in the binary representation of the number
The 1’s complement of a number is found by changing all 1’s to 0’s and all 0’s to 1’s. This is called as taking complement or 1’s complement. Example of 1’s Complement is as follows.
- 2’s complemen
The 2’s complement of binary number is obtained by adding 1 to the Least Significant Bit (LSB) of 1’s complement of the number.
2’s complement = 1’s complement + 1
2.3 Instruction format(zero one two three)
computer performs task on the basis of instruction of provided.A instruction in computer comprises of groups called fields.The most common fields are:
- Operation field which specifies the operation to be performed like addition
- Address field which contain the location of operand,e.g. register or memory location
- Mode field which specifies how operand is to be founded
on the basis of number of addres instruction are classified as: - zero-address Instruction
- one address instruction
use a implied accumulator register for data manipulation.One operand is in ACC and other in register or memory location.
- two address instruction:require more number of bit to represent address. Here destination address can also contain operand.
- three address instruction
These instructions make creation of program much easier but it does not mean that program will run much faster because now instructions contain more information and each micro instruction will be performed once a circle.
3. AI principle
3.1 Three schools
- symbolism
Symbolic artificial intelligence is the term for the collection of all methods in artificial intelligence research that are based on high-level “symbolic” (human-readable) representations of problems, logic and search.
(符号人工智能是人工智能研究中所有方法的集合,它基于问题,逻辑和搜索的高级“符号”(人类可读)表示。) - connectionism (artificial neural network)
The neural network itself isn’t an algorithm, but rather a framework for many different machine learning algorithms to work together and process complex data inputs. - actionism
3.2 Turing testing
Turing proposed that a human evaluator would judge natural language conversations between a human and a machine designed to generate human-like responses.
If the evaluator cannot reliably tell the machine from the human, the machine is said to have passed the test.
3.3 Predicate logic(谓词逻辑)
predicate logic involves using standard forms of logical symbolism . Most simple sentences, for example, ``Peter is generous’’ can be represented in terms of logical formula in which a predicate is applied to one or more arguments
4. operating system
4.1 process
A process is an instance of a computer program that is being executed. It contains the program code and its activity. Dependent on OS, a process may be made up of multiple threads of execution that execute instructions concurrently.
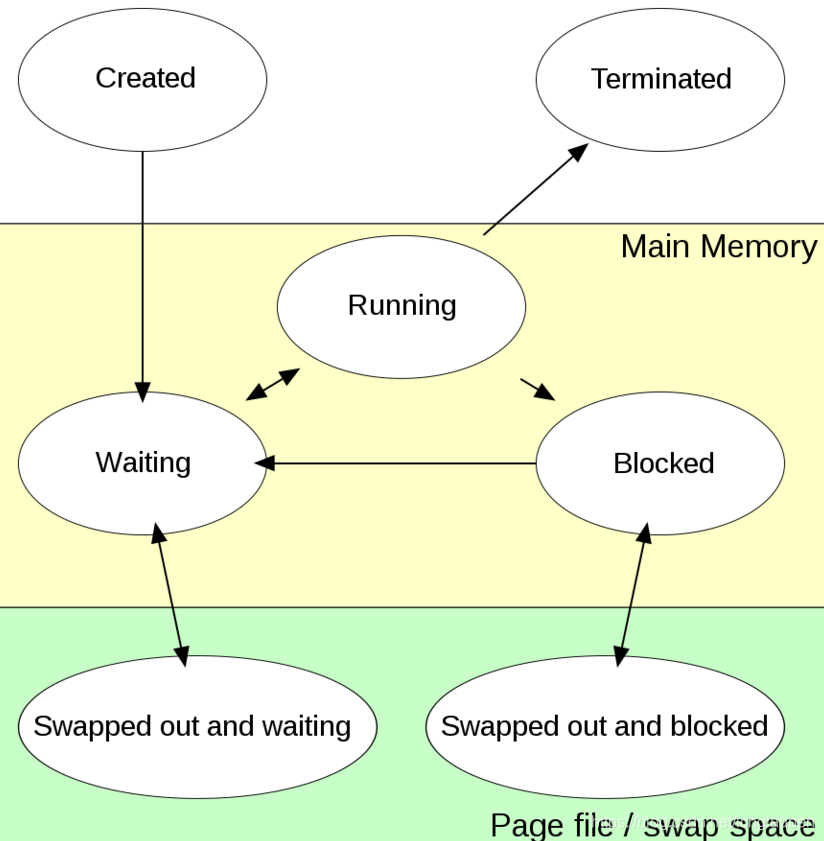
process states:
- First, the process is “created” by being loaded from a secondary storage device (hard disk drive, CD-ROM, etc.) into main memory.
- While the process is “waiting”, it waits for the scheduler to do a so-called context switch and load the process into the processor. The process state then becomes “running”
- If a process needs to wait for a resource ,it is assigned the “blocked” state.
- Once the process finishes execution. The process is removed instantly or is moved to the “terminated” state.
4.2 scheduling
A process scheduler schedules different processes to be assigned to the CPU based on particular scheduling algorithms. There are several popular scheduling algorithms .
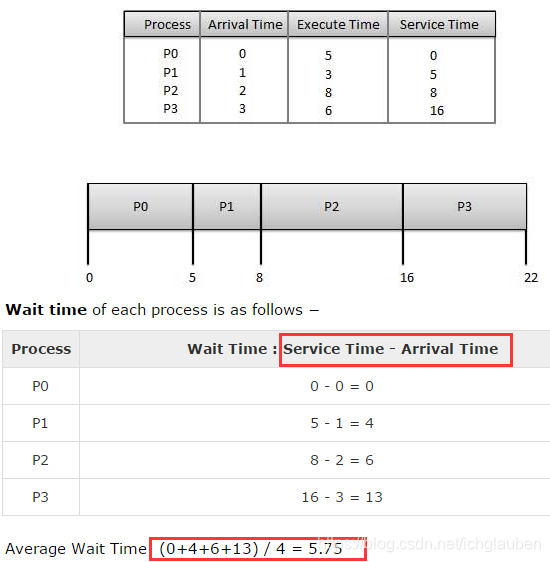
FCFS
- Jobs are executed on first come,first served
- It’s a non-preemptive algorithm
- Its implement is based on FIFO queue
- poor in performance as average wait time is high
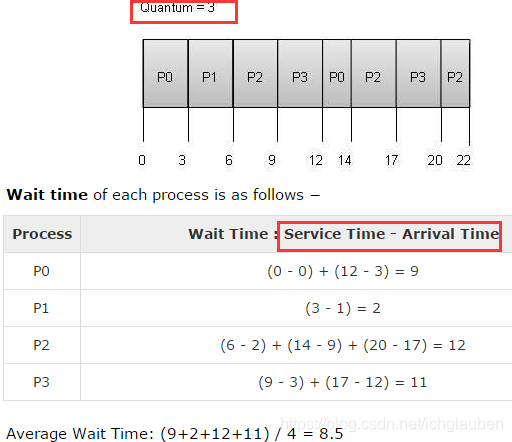
RR (Round Robin)
- it’s a preemptive process scheduling algorithm
- each process is provided a fix time to execute , it is called quantum(定量)
- Once a process is executed for a given time period, it is preempted and other process executes for a given time period.
4.3 Mutual Exclusion
Mutual exclusion is a property of concurrency control,which is instituted for the purpose of preventing race competition.
It’s required that one thread of execution can’t never enter into the critical section while another concurrent thread of execution enters its own critical section.
- critical section: the process is allowed to access the shared resource in this section.
solving problem using mutual exclusion:
- The problem which mutual exclusion addresses is a problem of resource sharing: how can a software system control multiple processes’ access to a shared resource, when each process needs exclusive control of that resource while doing its work?
- successful solving this kind of problems preconditions:
1. it must implement mutual exclusion
2. it must be free of deadlock
deadlock: in concurrent computing,a deadlock is a state which each member of a group is waiting other member to take action.
necessary conditions: a deadlock arises if and only if all of the following conditions hold in a system at the same time
- Mutual exclusion
- Hold and wait or resource holding
- No preemption
- Circular wait
5. Software Engineering
- def: an engineering discipline that is concerned with all aspects of software production
5.1 software risk
- schedule risks: no matter what was the source of the problem .In the end,every software development risk comes up to take more time
- technical risks:every development process is a unique case,the effectiveness of overcoming its issues relies on the quality of programmers.
- management risks:the software development management includes: the bad working environment ,insufficient hardware reliability ,low effectiveness of the programming
5.2 software development process
a software development process is the process of dividing software development work into distinct(清楚的) phases to improve design, product management, and project management.
software methodologies
- 1.waterfall development
The waterfall model is a sequential development approach, in which development is seen as flowing steadily downwards (like a waterfall) through several phases
1* requirement analysis
2* software design
3* implementation
4* testing
5* integration - 2.agile development(敏捷开发)
Agile software development uses iterative development as a basis but advocates a lighter and more people-centric viewpoint than traditional approaches. (敏捷软件开发使用迭代开发作为基础,但提倡比传统方法更轻松,更以人为中心的观点。)
6.Database principle
- A database is an organized collection of data, generally stored and accessed electronically from a computer system.
- These model data as rows and columns in a series of tables, and the vast majority use SQL for writing and querying data.
6.1 Database schema
- def: a database schema is a set of formulas (sentences) called integrity constraints imposed on a database.
- Using the database schema, it is possible to create a blueprint of the database. This blueprint will not contain any data. The database schema uses logical formulas to create integrity constraints.
different kinds of DB schema
- The conceptual schema : expresses the concepts in the database, and how they relate to each other
- The logical schema :is a mapping of entities with their attributes, and the respective relations
- The physical schema : is a particular implementation of a logical schema.
DB schema should have the following properties:
complete minimal and normalized
6.2 SQL
- SQL is a domain-specified language used in programming and designed for managing data held in a relational database management system. It’s useful in handling structured data where there are relations between different entities/variables of the data.
6.3 normalization(标准化)
- Database normalization is a method of designing good relational databases. There are several “normal forms”, each of which have rules which the database should be designed to meet.
first normal form
second normal form
third normal form
1NF : Within a table that is in first normal form, each row has columns that are each represent one thing and contain one element.
(每一行都有一列,每个列代表一个东西并且包含一个元素)
2NF :Within a table that is in second normal form, the data in each columns in each row are dependent on each row’s entire primary key.
(每行中每列的数据取决于每行的整个主键)
A primary key is one or more columns in a row that is used to identify and index that row of the table.
3NF : Within a table that is in third normal form, the data in each column in each row are dependent only on columns that are part of the primary key.
(每行中每列的数据仅取决于主键的部分列)
7.Computer Network
- def: CN is a digital telecommunications network which allows nodes to share resources. In computer networks, computing devices exchange data with each other using connections (data links) between nodes.
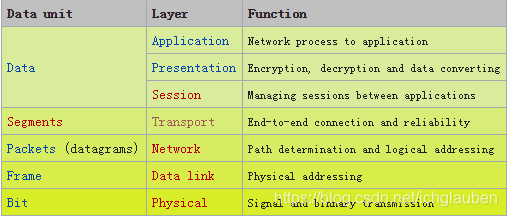
7.1 OSI(Open Systems Interconnection) Model
remove Presentation and Session Layer
- 1 Layer:The physical layer defines electrical and physical specifications for devices.
- 2 Layer:The data link layer provides the functional and procedural means to transfer data between network entities and to detect and possibly correct errors that may occur in the physical layer.
- 3 Layer: the network layer provides the functional and procedural means of transferring variable length data sequences from a source to the destination host using the IP address
- 4 Layer:The transport layer provides transparent transfer of data between end users, providing reliable data transfer services to the upper layers. The Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP) of the Internet Protocol Suite are commonly categorized.
TCP:(transmission control protocol)
provides reliable, ordered delivery of a stream of bytes from a program on one computer to another program on another computer. TCP is used for applications that strictly require reliable transfer(FTP SMTP)
UDP(user diagram protocol):uses a simple transmission model without implicit handshaking dialogues for providing reliability, ordering, or data integrity
(使用简单的传输模型,没有隐式握手对话,以提供可靠性,排序或数据完整性) - 5 Layer:its main purpose is to interact with applications, encrypting and establishing dedicated connections if necessary.
(它的主要目的是在必要时与应用程序交互,加密和建立专用连接)
An Internet Protocol address (IP address) is a numerical label assigned to each device. At present there are two versions of protocols in use.
IPV4:uses 32-bit addressing which limits address space up to 4294967296 (232) possible unique addresses.
IPV6: uses 128-bit addressing which limits address space up to 2128 possible addresses.
8. Data Structure
- In computer science, a data structure is a data organization, management and storage format that enables efficient access and modification.More precisely, a data structure is a collection of data values, the relationships among them, and the functions or operations that can be applied to the data.
8.1 List (Array & Linked List)
array:is a data structure consisting of a collection of elements.
The simplest type of data structure is a linear array, also called one-dimensional array.
- features: 1.easy to find,but hard to modify 2.insert & delete: all elements after the element must modify 3.might suffer from overflow
linked list: is a linear collection of data elements of any type, called nodes, where each node has itself a value, and points to the next node in the linked list.
- features: easy to expend, easy to insert or delete but not quick to search
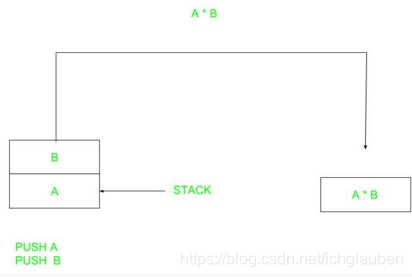
8.2 Stack | Queue
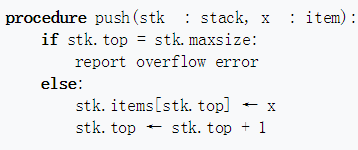
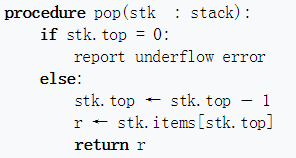
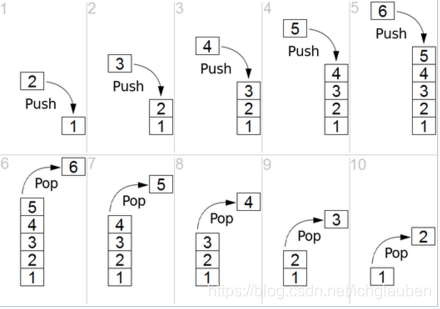
stack:
In computer science, a stack is an abstract data type that serves as a collection of elements, with two principal operations:
- push, which adds an element to the collection
- pop, which removes the most recently added element that was not yet removed.
The order in which elements come off a stack gives rise to its alternative name, LIFO (last in, first out).
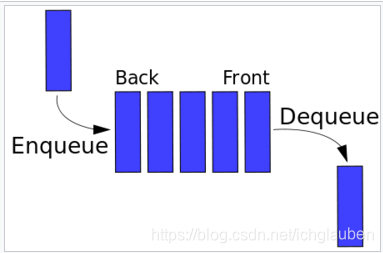
queue:
- a queue is a particular kind of abstract data type (ADT) or collection in which the entities in the collection are kept in order and the principal (or only) operations on the collection are the addition of entities to the rear terminal position, known as enqueue, and removal of entities from the front terminal position, known as dequeue.
This makes the queue a First-In-First-Out (FIFO) data structure.
8.3 Tree (Binary Tree) & Graph
Binary Tree
-
def : a binary tree is a tree data structure in which each node has at most two children, which are referred to as the left child and the right child.
-
properties of B-Tree:
Graph
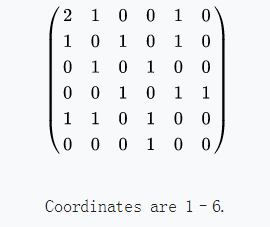
- def: a graph is an abstract data type that is meant to implement the undirected graph and directed graph concepts from mathematics; specifically, the field of graph theory.
- adjacent matrix:
an adjacency matrix is a square matrix used to represent a finite graph. The elements of the matrix indicate whether pairs of vertices are adjacent or not in the graph.
9.Microcomputer System Theory & Interface Technology
-
def : A microcomputer is a small, relatively inexpensive computer with a microprocessor as its central processing unit (CPU).It includes a microprocessor, memory, and minimal input/output (I/O) circuitry mounted on a single printed circuit board.
-
in this term,I went to Taiwan JingYi province University,study Programming interaction design to replace the course.I remembered this course is full of experiment and practice.
-
Our teacher asked us to make a product every week,using web utility (MIT App Inventor 2) & arduino .
-
I remember the find rail cars which find the black adhesive plaster to follow, and the final work I made , is to use a sensor to detect the game of Wack-a mole and print the score to the screen.That was a very nice thing when I saw it worked.
10.Principle of Communication
- def: Communication is the act of conveying meanings from one entity or group to another through the use of mutually understood signs and semiotic rules.
(通过使用相互理解的符号和符号规则将意义从一个实体或群体传达到另一个实体或群体的行为。)
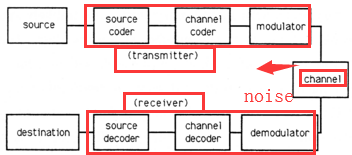
I can describe the communication system with the help of a diagram.
- just as the above graph,the communication system consists of the following parts:namely transmitter,channel,noise and receiver. The transmitter includes signal source,encoder and modulator.The professor mainly taught the modulator and fundamental digital modulation method .
10.1 modulator
- There are mainly two types of modulator,namely digital and analog.The analog includes amplitude modulation and angle modulation.The amplitude consists of AM,DSB,SSB and the angle modulation includes FM and PM
Analog System : Source -> Modulator -> Channel(with noise) -> Demodulator -> Receiver(Destination)
Digital System: Source -> Encode -> Modulator -> Channel(with noise) -> Demodulator -> Decode -> Receiver(Destination)
Amplitude modulated wave: AM DSB SSB VSB
AM: Amplitude Modulation(here the amplitude of the carrier signal is varied in accordance with the instantaneous amplitude of the modulating signal)
DSB :Double Sideband Amplitude Modulation(DSB-AM)
Angle modulation: FM PM
Frequency Modulation:the frequency of the carrier signal is varied in accordance with the instantaneous amplitude of the modulating signal
Phase Modulation:the phase shift of the carrier signal is varied in accordance with the instantaneous amplitude of the modulating signal
10.2 Fundamental digital modulation method
- ASK(Amplitude Shift Keying):a form of amplitude modulation that represents digital data as variations in the amplitude of a carrier wave
- FSK(Frequency Shift Keying):is a frequency modulation scheme in which digital information is transmitted through discrete frequency changes of a carrier signal.
11.Principle of Automatic Control
-
def: The automatic control means that,the system can run automatically without the intervention(干预).This course can be regarded as the extension of signal and system.
-
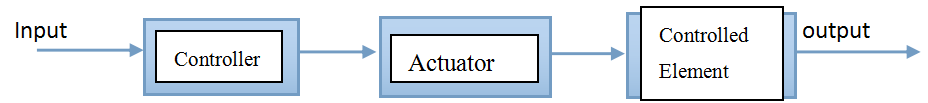
Component:
- Sensor(s), which measure some physical state such as temperature or liquid level.传感器/测量元件
- Controller(s), a controller manipulates the inputs to a system to obtain the desired effect on the output of the system. 即产生控制作用
- Actuator(s)执行器, which changes the controlled parameters like temperature directly.执行器直接改变被控量.
11.1 control system
-
the open loop control system
To overcome the limitations of the open-loop controller, control theory introduces feedback. A closed-loop controller uses feedback to control states or outputs of a dynamical system. -
closed-loop control system
Closed-loop controllers have the following advantages over open-loop controllers:- disturbance rejection
- unstableprocesses can be stabilized
-
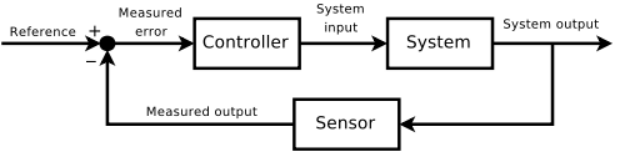
Closed-loop transfer function
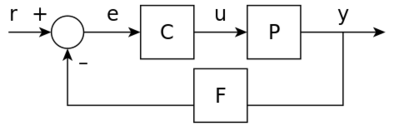
The output of the system y(t) is fed back through a sensor measurement F to a comparison with the reference value r(t). The controller C then takes the error e (difference) between the reference and the output to change the inputs u to the system under control P.
This is shown in the figure. This kind of controller is a closed-loop controller or feedback controller.
If we assume the controller C, the plant P, and the sensor F are linear and time-invariant.
the systems above can be analysed using the Laplace transform on the variables. This gives the following relations:
Solving for Y(s) in terms of R(s) gives
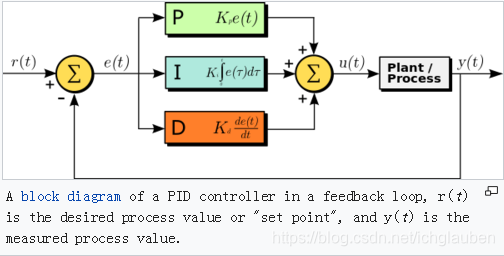
11.2 PID Controller
- def:A proportional–integral–derivative controller (PID controller) is a control loop feedback mechanism control technique widely used in control systems.
Feedback occurs when outputs of a system are routed back as inputs as part of a chain of cause-and-effect that forms a circuit or loop.
12.Signal & System
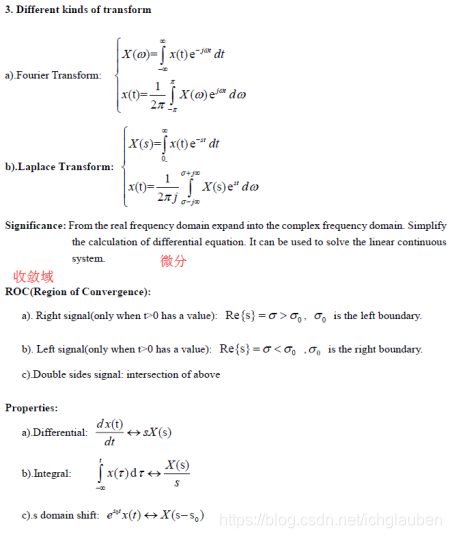
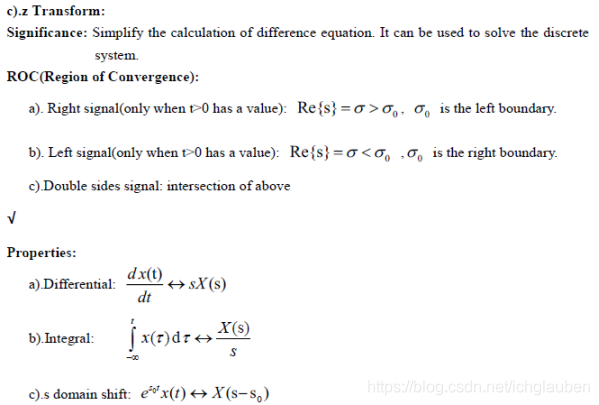
This is one of the most important course in my whole college. In this course ,I’ve learned three kinds of transform,namely fourier,laplace and z.And the most important is,it’s the first time that I acknowledge the concept of frequency domain.
12.1 The basic concept of signal & system
- def of system : A System is any physical set of components that takes a signal, and produces a signal.
- features of system: Superposition叠加性(线性) time-invariant 时不变性 causality 因果性
- def of LTI(Linear Time Invariant):Linear can also be regarded as the superposition(叠加).And the time-invariant means the output signal is depend on the input signal and has nor relation to the input moment.
12.2 Frequency domain
- a frequency-domain graph shows how much of the signal lies within each given frequency band over a range of frequencies.
A frequency-domain representation can also include information on the phase shift that must be applied to each sinusoid in order to be able to recombine the frequency components to recover the original time signal.
(频域表示还可以包括关于必须应用于每个正弦波的相移的信息,以便能够重新组合频率分量以恢复原始时间信号。)
Why use Frequency domain?- By using the frequency domain give us more opportunity to transmit or process the information we need.
12.3 Different kinds of transform
13. sensor & actuator
-
def : A sensor is a device that measures a physical quantity and converts it into a ‘signal’ which can be read by an observer or by an instrument. For example, a mercury thermometer converts the measured temperature into the expansion and contraction of a liquid which can be read on a calibrated glass tube.
-
Thermal Sensors
A sensor that detects temperature. Thermal sensors are in many laptops and computers in order to sound an alarm when a certain temperature has been exceeded. -
Electromagnetic sensors[change | change source]
An electronic device used to measure a physical quantity such as pressure or loudness and convert it into an electronic signal of some kind (e.g. a voltage).
14. Embedded System
-
def : An embedded system is a programmed controlling and operating system with a dedicated function within a larger mechanical or electrical system, often with real-time computing constraints.
Modern embedded systems are often based on microcontrollers . -
features:
- Embedded systems are designed to do a specific task.
- Many embedded systems must be able to do things in real-time - in a short amount of time
- Many embedded systems must be very safe and reliable, especially for medical devices or avionics [.eɪvi’ɑnɪks] (航空电子)controlling airplanes.
-
Hardware:includes the chips, wires, circuit boards, buttons and displays.
- CPU:The most important chip is the central processing unit or CPU. This runs the software instructions. It can be a standard microprocessor or a microcontroller.
- ready-made(预制的) computer board: There are “ready-made” computer boards that can be used in some embedded systems. These often use Windows CE, Linux, NetBSD, or an embedded real-time operating system.
- Peripherals:Embedded systems talk with the outside world or other components using peripherals e.g. USB(Universal Serial Bus)
15.single chip microcomputer (microcomputer)
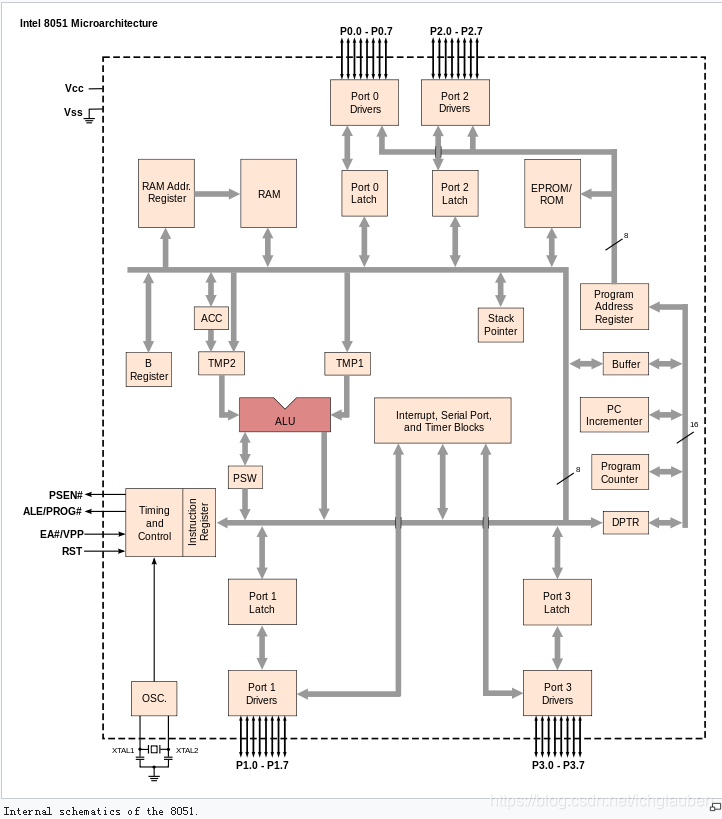
- def : A microcomputer is a small, relatively inexpensive computer with a microprocessor as its central processing unit (CPU). It includes a microprocessor, memory, and minimal input/output (I/O) circuitry mounted on a single printed circuit board.
Mainly introduce the MCS-8051 microcomputer.:The Intel 8051 is an 8-bit microcontroller which means that most available operations are limited to 8 bits. There are 3 basic “sizes” of the 8051: Short, Standard, and Extended. The Short and Standard chips are often available in DIP
Application:
- 8051 chips are used in a wide variety of control systems, telecom applications, robotics as well as in the automotive industry. By some estimations, 8051 family chips make up over 50% of the embedded chip market.
Basic Pins(partly):
-
PIN 9: PIN 9 is the reset pin which is used to reset the microcontroller’s internal registers and ports upon starting up. (Pin should be held high for 2 machine cycles.)
-
PINS 18 & 19: The 8051 has a built-in oscillator amplifier hence we need to only connect a crystal at these pins to provide clock pulses to the circuit.
Ports:
-
PORT P1 (Pins 1 to 8): The port P1 is a general purpose input/output port which can be used for a variety of interfacing tasks. The other ports P0, P2 and P3 have dual roles or additional functions associated with them.
-
PORT P3 (Pins 10 to 17): PORT P3 acts as a normal IO port, but Port P3 has additional functions such as, serial transmit and receive pins, 2 external interrupt pins, 2 external counter inputs, read and write pins for memory access.
-
PORT P2 (pins 21 to 28): PORT P2 can also be used as a general purpose 8 bit port when no external memory is present, but if external memory access is required then PORT P2 will act as an address bus in conjunction with PORT P0 to access external memory.
-
PORT P0 (pins 32 to 39) PORT P0 can be used as a general purpose 8 bit port when no external memory is present, but if external memory access is required then PORT P0 acts as a multiplexed address and data bus that can be used to access external memory in conjunction with PORT P2.
MCS51 Architecture
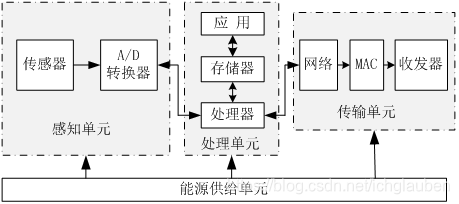
16.WSN(Wireless Sensor Network)
- def : refers to a group of spatially dispersed and dedicated sensors for monitoring and recording the physical conditions of the environment and organizing the collected data at a central location. WSNs measure environmental conditions like temperature, sound, pollution levels, humidity, wind, and so on.
16.1 Application
-
Area monitoring:is a common application of WSNs .In area monitoring, the WSN is deployed over a region where some phenomenon is to be monitored.
-
Health care monitoring
-
Forest fire detection
16.2 Component
The WSN is built of “nodes” – from a few to several hundreds or even thousands, where each node is connected to one (or sometimes several) sensors.
Each such sensor network node has typically several parts:
- a radio transceiver with an internal antenna or connection to an external antenna
- a microcontroller
- an electronic circuit for interfacing with the sensors and an energy source
- a battery or an embedded form of energy harvesting
16.3 Characteristics include:
- Power consumption constraints for nodes using batteries or energy harvesting.
- Ability to cope with node failures (resilience)
- Ability to withstand harsh environmental conditions
17.RFID(Radio-Frequency Identification)
- def : is a technology to record the presence of an object using radio signals. It is used for inventory control or timing sporting events. RFID is not a replacement for barcoding, but a complement for distant reading of codes.
The technology is used for automatically identifying a person, a package or an item. To do this, it relies on RFID tags. These are small transponders
17.1 RFID Tag
A radio-frequency identification system uses tags, or labels attached to the objects to be identified.
A Tag contain as least three parts:
- an integrated circuit that stores and processes information and that modulates and demodulates radio-frequency (RF) signals
- a means of collecting DC power from the incident reader signal
- an antenna for receiving and transmitting the signal
17.2 Readers
RFID systems can be classified by the type of tag and reader.
- A Passive Reader Active Tag (PRAT) system has a passive reader which only receives radio signals from active tags (battery operated, transmit only).
18. Web Application Design
- Web App Development: is the process and practice of developing web applications. There is a consensus that the processes involved are extensions of standard software engineering processes.
18.1 Technologies:
web application development has several characteristics that have to be addressed and these include: short development life-cycle times; different business models;
some of technologies:
-
Cascading Style Sheets (CSS): is a style sheet language used for describing the presentation of a document written in a markup language like HTML
-
ASP.NET is an open-source server-side web application framework designed for web development to produce dynamic web pages.
-
JAVA: is a general-purpose computer-programming language that is concurrent, class-based, object-oriented,[15] and specifically designed to have as few implementation dependencies as possible .It is intended to let application developers “write once, run anywhere” (WORA) .JAVA can be run in any machine
-
JAVA Architecture:
19.Network Security
-
concept : Network security starts with authentication, commonly with a username and a password. Since this requires just one detail authenticating the user name—i.e., the password—this is sometimes termed one-factor authentication.
-
Once authenticated, a firewall enforces access policies such as what services are allowed to be accessed by the network users.[1] Though effective to prevent unauthorized access, this component may fail to check potentially harmful content such as computer worms or Trojans being transmitted over the network.
19.1 Security management
Security management for networks is different for all kinds of situations. A home or small office may only require basic security while large businesses may require high-maintenance and advanced software and hardware to prevent malicious attacks from hacking and spamming.
- types of attack:
- active: DNS spoofing
- passitive: Port Scanner
DNS spoofing, also referred to as DNS cache poisoning, is a form of computer security hacking in which corrupt Domain Name System data is introduced into the DNS resolver’s cache, causing the name server to return an incorrect result record, e.g. an IP address. This results in traffic being diverted to the attacker’s computer
A port scanner is an application designed to probe a server or host for open ports. Such an application may be used by attackers to identify network services running on a host and exploit vulnerabilities.