11.25 配置防盗链
防盗链配置文件
<Directory /data/wwwroot/abc.com>
SetEnvIfNoCase Referer "http://abc.com" local_ref referer白名单
SetEnvIfNoCase Referer "http://123.com" local_ref
SetEnvIfNoCase Referer "^$" local_ref
<FilesMatch "\.(txt|doc|mp3|zip|rar|jpg|gif)">
Order Allow,Deny
Allow from env=local_ref
</FilesMatch>
</Directory>
SetEnvIfNoCase Referer "^$" local_ref 把空referer注释掉,显示forbidden,
指定referer 测试 txt|doc|mp3|zip|rar|jpg|gif 这些格式的都拒绝了
-e 指定referer 必须是http://格式
查看访问日志
11.26 访问控制Directory
目录访问控制配置文件
<Directory /data/wwwroot/abc.com/admin/>
Order deny,allow
Deny from all
Allow from 127.0.0.1
</Directory>
11.27 访问控制FilesMatch
文件访问控制配置文件
<Directory /data/wwwroot/abc.com>
<FilesMatch admin.php(.*)>
Order deny,allow
Deny from all
Allow from 127.0.0.1
</FilesMatch>
</Directory>
返回403状态码 (拒绝)
用127.0.0.1访问返回404状态码 (找不到文件)
11.28 限定某个目录禁止解析php
配置文件
<Directory /data/wwwroot/abc.com/upload>
php_admin_flag engine off
<FilesMatch (.*)\.php(.*)>
Order allow,deny
Deny from all
</FilesMatch>
</Directory>
把filesmatch 注释掉,会直接解析到源代码
11.29 限制user_agent
防止CC攻击
NC 代表忽略大小写
OR 代表或者的意思
F Forbidden的意思
配置文件
<IfModule mod_rewrite.c>
RewriteEngine on
RewriteCond %{HTTP_USER_AGENT} .*curl.* [NC,OR]
RewriteCond %{HTTP_USER_AGENT} .*baidu.com.* [NC]
RewriteRule .* - [F]
</IfModule>
-A 指定Agent
-x 省略hosts
-I 大写i 仅仅查看状态码
-e 指定referer
11.30 PHP相关配置(上)
配置文件已加载
•disable_functions 安全相关的函数要禁掉
配置文件里面加上phpinfo,就访问不了了
date.timezone 定义时区,不定义的话会有一些告警信息
display_errors = On 这个打开的话,会把错误信息显示在浏览器上
改成off 就是不把错误信息输出到浏览器页面上
curl 也没有任何的输出
log_errors = On打开错误日志记录
error_log 定义错误日志路径
error_reporting 定义错误日志级别
错误日志是由httpd创建的
为了保险,可以创建一个touch 一个php_errors.log,然后给777权限500
模拟了一个错误。状态码返回500,比之前的报错级别高
11.31 PHP相关配置(下)
网站隔离,防止被黑,定义open_basedir
open_basedir 它的作用就是把php限定在指定的目录下面,不让它去别的目录读写文件
open_basedir = /data/wwwroot/abc1.com:/tmp
tmp 是默认的临时文件目录,网站上传图片,会临时放到这个目录下,在放到指定的目录下
这个在虚拟主机配置文件里面设置
vim /usr/local/apache2.4/conf/extra/httpd-vhosts.conf
php_admin_value open_basedir "/data/wwwroot/abc.com:/tmp/"
11.32 PHP扩展模块安装
缺少autoconf包
yum -y install autoconf
./configure --with-php-config=/usr/local/php7/bin/php-config
make && make install
/usr/local/php7/bin/php -m
查看php模块
在配置文件里面增加一行
在源码码包文件下有许多模块可以直接编译/usr/local/src/php-7.1.6/ext/
课堂内容
目录
一、配置防盗链
二、访问控制Directory
三、访问控制FilesMatch
四、限定某个目录禁止解析php
五、限制user_agent
六、php相关配置
七、php扩展模块装安
八、扩展
一、配置防盗链
盗链,全称是盗取链接,假如我们的网站有很多好看的图片,别人可以查看我们网站图片的链接,然后应用在他的网站上,这样的话,去访问他的网站,实际上消耗的是我们的流量(因为实际链接在我们这里),这样我们就不得不去配置防盗链,使得别人不能复制我们图片的链接。
1.在Apache子配置文件/usr/local/apache2.4/conf/extra/httpd-vhosts.conf中添加配置
<Directory /usr/local/apache2.4/htdocs/b.com>
SetEnvIfNoCase Referer "b.com" local_ref
SetEnvIfNoCase Referer "^$" local_ref
<filesmatch "\.(txt|doc|mp3|zip|rar|jpg|gif|png)">
Order Allow,Deny
Allow from env=local_ref
</filesmatch>
</Directory>2.测试配置文件及重载
[root@localhost ~]# /usr/local/apache2.4/bin/apachectl -t
Syntax OK
[root@localhost ~]# /usr/local/apache2.4/bin/apachectl graceful3.测试
//curl -e参数模拟refer为http://www.baidu.com,refer必须以http开头
//因为不是允许的refer,所以访问被禁止
[root@localhost ~]# curl -e "http://www.baidu.com" -x127.0.0.1:80 b.com/img/b.com.jpg -I
HTTP/1.1 403 Forbidden
Date: Fri, 29 Jun 2018 08:15:55 GMT
Server: Apache/2.4.33 (Unix) PHP/5.6.30
Content-Type: text/html; charset=iso-8859-1
//以被允许的refer(http://b.com)可以正常访问
[root@localhost ~]# curl -e "http://b.com" -x127.0.0.1:80 b.com/img/b.com.jpg -I
HTTP/1.1 200 OK
Date: Fri, 29 Jun 2018 08:16:28 GMT
Server: Apache/2.4.33 (Unix) PHP/5.6.30
Last-Modified: Thu, 28 Jun 2018 03:08:53 GMT
ETag: "4117-56fab0d131b40"
Accept-Ranges: bytes
Content-Length: 16663
Content-Type: image/jpeg
二、访问控制Directory
有时候为了安全需要,要对网站的某些目录限制访问的来源IP。可以通过对目录的控制来实现。
1.修改apache子配置文件/usr/local/apache2.4/conf/extra/httpd-vhosts.conf
[root@localhost img]# vim /usr/local/apache2.4/conf/extra/httpd-vhosts.conf
<VirtualHost *:80>
ServerAdmin [email protected]
DocumentRoot "/usr/local/apache2.4/htdocs/b.com"
ServerName b.com
//增加如下内容
<Directory /usr/local/apache2.4/htdocs/b.com/img/>
//Order确定执行顺序,整个语句都会执行一遍,与iptables的执行过程不同
//如果先deny,后allow,则会先执行deny的操作,再执行允许的动作。后面的动作会覆盖前面的操作
//如果先allow,后deny all,则最后的结果会是deny
Order deny,allow
Deny from all
Allow from 127.0.0.1 192.168.1.9
</Directory>
ErrorLog "logs/b.com-error_log"
CustomLog "logs/b.com-access_log" combined
</VirtualHost>2.测试配置及重载
[root@localhost img]# /usr/local/apache2.4/bin/apachectl -t
Syntax OK
[root@localhost img]# /usr/local/apache2.4/bin/apachectl graceful
3.验证
本地测试
//从本地访问
[root@localhost img]# curl -x127.0.0.1:80 b.com/img/admin.php -I
HTTP/1.1 200 OK
Date: Sat, 30 Jun 2018 01:44:33 GMT
Server: Apache/2.4.33 (Unix) PHP/5.6.30
X-Powered-By: PHP/5.6.30
Content-Type: text/html; charset=UTF-8
//更换目标IP,源ip变更,不在允许范围内。403错误
[root@localhost img]# curl -x192.168.1.212:80 b.com/img/admin.php -I
HTTP/1.1 403 Forbidden
Date: Sat, 30 Jun 2018 01:43:18 GMT
Server: Apache/2.4.33 (Unix) PHP/5.6.30
Content-Type: text/html; charset=iso-8859-1
//日志
127.0.0.1 - - [29/Jun/2018:21:13:50 -0400] "HEAD HTTP://b.com/img/admin.php HTTP/1.1" 200 - "-" "curl/7.29.0"
192.168.1.212 - - [29/Jun/2018:21:15:11 -0400] "HEAD HTTP://b.com/img/admin.php HTTP/1.1" 403 - "-" "curl/7.29.0"
192.168.1.212 - - [29/Jun/2018:21:16:47 -0400] "HEAD HTTP://b.com/img/admin.php HTTP/1.1" 403 - "-" "curl/7.29.0"远程浏览器测试
1.从192.168.1.9测试
C:\Users\kennminn>ipconfig
...
以太网适配器 external:
连接特定的 DNS 后缀 . . . . . . . :
IPv4 地址 . . . . . . . . . . . . : 192.168.1.9
子网掩码 . . . . . . . . . . . . : 255.255.255.0
默认网关. . . . . . . . . . . . . : 192.168.1.1
...
日志
192.168.1.9 - - [29/Jun/2018:21:52:21 -0400] "GET /img/admin.php HTTP/1.1" 200 6 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/67.0.3396.99 Safari/537.36"2.从192.168.1.169访问
//在192.168.1.169上需在hosts文件增加b.com的解析
C:\Users\DBTrial>ipconfig
Windows IP 配置
以太网适配器 本地连接:
连接特定的 DNS 后缀 . . . . . . . :
本地链接 IPv6 地址. . . . . . . . : fe80::bd14:9580:f094:4fc1%11
IPv4 地址 . . . . . . . . . . . . : 192.168.1.169
子网掩码 . . . . . . . . . . . . : 255.255.255.0
默认网关. . . . . . . . . . . . . : 192.168.1.1
C:\Users\DBTrial>ping b.com
正在 Ping a.com [192.168.1.212] 具有 32 字节的数据:
来自 192.168.1.212 的回复: 字节=32 时间<1ms TTL=64
来自 192.168.1.212 的回复: 字节=32 时间<1ms TTL=64
来自 192.168.1.212 的回复: 字节=32 时间<1ms TTL=64
192.168.1.212 的 Ping 统计信息:
数据包: 已发送 = 3,已接收 = 3,丢失 = 0 (0% 丢失),
往返行程的估计时间(以毫秒为单位):
最短 = 0ms,最长 = 0ms,平均 = 0ms
Control-C
日志
//403错误,说明配置成功
192.168.1.169 - - [29/Jun/2018:22:06:30 -0400] "GET /img/admin.php HTTP/1.1" 403 222 "-" "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/56.0.2924.90 Safari/537.36 2345Explorer/9.2.1.17116"
三、访问控制FilesMatch
访问控制除了可以对整个目录进行控制,还可以针对具体的页面进行控制
如限制b.com下的admin.php后带任意字符的页面。
1.修改apache子配置文件/usr/local/apache2.4/conf/extra/httpd-vhosts.conf
[root@localhost img]# vim /usr/local/apache2.4/conf/extra/httpd-vhosts.conf
//添加filesmatch段的内容
<VirtualHost *:80>
ServerAdmin [email protected]
DocumentRoot "/usr/local/apache2.4/htdocs/b.com"
ServerName b.com
<Directory /usr/local/apache2.4/htdocs/b.com>
//filesmath不区分大小写,(.*)是正则,表示任意字符
<FilesMatch "admin.php(.*)">
Order deny,allow
Deny from all
Allow from 127.0.0.1 192.168.1.9
</FilesMatch>
</Directory>
ErrorLog "logs/b.com-error_log"
CustomLog "logs/b.com-access_log" combined
</VirtualHost>2.测试配置文件及重载
[root@localhost img]# /usr/local/apache2.4/bin/apachectl -t
Syntax OK
[root@localhost img]# /usr/local/apache2.4/bin/apachectl graceful3.验证
本地验证
//本地访问admin.php,该页面存在
[root@localhost img]# curl -x127.0.0.1:80 b.com/img/admin.php -I
HTTP/1.1 200 OK
Date: Sat, 30 Jun 2018 02:28:35 GMT
Server: Apache/2.4.33 (Unix) PHP/5.6.30
X-Powered-By: PHP/5.6.30
Content-Type: text/html; charset=UTF-8
//本地访问/admin.phpaffafa,该页面不存在
//报404,找不到页面,但是表明还是可以访问的
[root@localhost img]# curl -x127.0.0.1:80 b.com/img/admin.phpaffafa -I
HTTP/1.1 404 Not Found
Date: Sat, 30 Jun 2018 02:29:06 GMT
Server: Apache/2.4.33 (Unix) PHP/5.6.30
Content-Type: text/html; charset=iso-8859-1
//变更目录ip,源ip也变更,访问admin.php,403错,说明配置成功
[root@localhost img]# curl -x192.168.1.212:80 b.com/img/admin.php -I
HTTP/1.1 403 Forbidden
Date: Sat, 30 Jun 2018 02:28:43 GMT
Server: Apache/2.4.33 (Unix) PHP/5.6.30
Content-Type: text/html; charset=iso-8859-1
//变更目录ip,源ip也变更,访问admin.phpaffafa,403错,说明配置成功
[root@localhost img]# curl -x192.168.1.212:80 b.com/img/admin.phpaffafa -I
HTTP/1.1 403 Forbidden
Date: Sat, 30 Jun 2018 02:28:48 GMT
Server: Apache/2.4.33 (Unix) PHP/5.6.30
Content-Type: text/html; charset=iso-8859-1
//变更ip,源ip也变更,访问其他页面不受影响
[root@localhost img]# curl -x192.168.1.212:80 b.com/img/qqq.jpg -I
HTTP/1.1 200 OK
Date: Sat, 30 Jun 2018 02:36:34 GMT
Server: Apache/2.4.33 (Unix) PHP/5.6.30
Last-Modified: Fri, 01 Jun 2018 02:43:58 GMT
ETag: "571e-56d8b8e401780"
Accept-Ranges: bytes
Content-Length: 22302
Content-Type: image/jpeg
日志
127.0.0.1 - - [29/Jun/2018:22:28:35 -0400] "HEAD HTTP://b.com/img/admin.php HTTP/1.1" 200 - "-" "curl/7.29.0"
127.0.0.1 - - [29/Jun/2018:22:29:06 -0400] "HEAD HTTP://b.com/img/admin.phpaffafa HTTP/1.1" 404 - "-" "curl/7.29.0"
192.168.1.212 - - [29/Jun/2018:22:28:43 -0400] "HEAD HTTP://b.com/img/admin.php HTTP/1.1" 403 - "-" "curl/7.29.0"
192.168.1.212 - - [29/Jun/2018:22:28:48 -0400] "HEAD HTTP://b.com/img/admin.phpaffafa HTTP/1.1" 403 - "-" "curl/7.29.0"
192.168.1.212 - - [29/Jun/2018:22:36:34 -0400] "HEAD HTTP://b.com/img/qqq.jpg HTTP/1.1" 200 - "-" "curl/7.29.0"
远程浏览器测试
从192.168.1.9访问

192.168.1.9 - - [29/Jun/2018:22:37:33 -0400] "GET /img/admin.php HTTP/1.1" 200 6 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/67.0.3396.99 Safari/537.36"从192.168.1.169访问
规则限制的面页无法访问
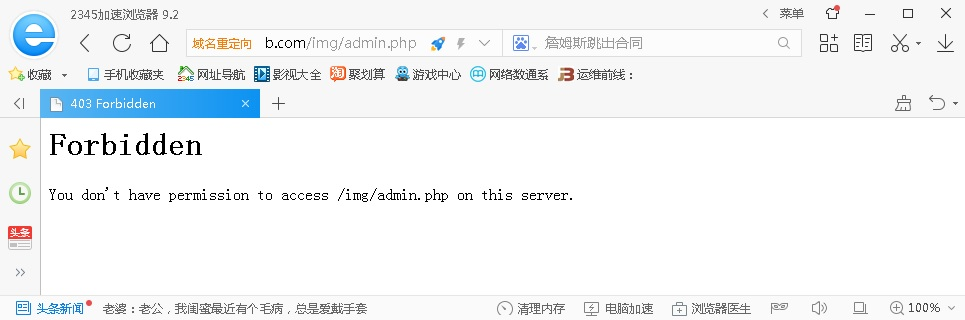
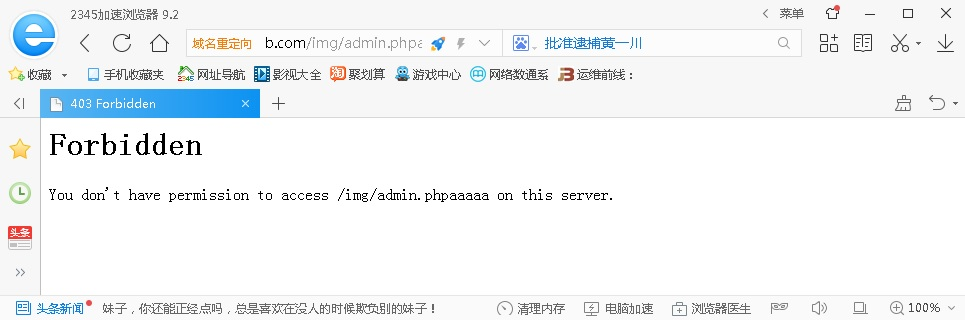
其他页面不受影响
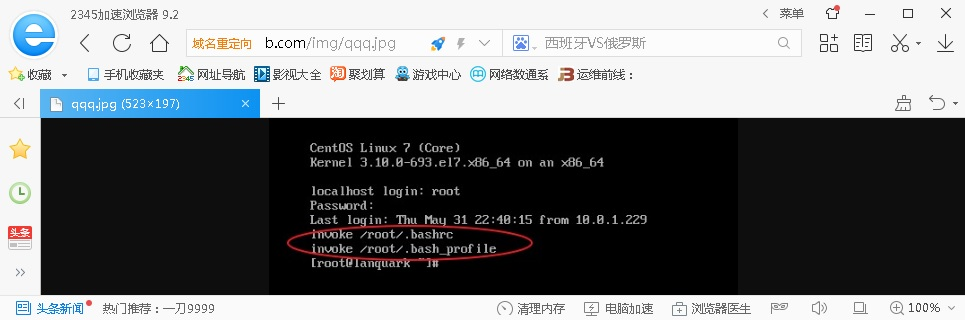
日志
192.168.1.169 - - [29/Jun/2018:22:41:06 -0400] "GET /img/admin.php HTTP/1.1" 403 222 "-" "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/56.0.2924.90 Safari/537.36 2345Explorer/9.2.1.17116"
192.168.1.169 - - [29/Jun/2018:22:41:40 -0400] "GET /img/admin.phpaaaaa HTTP/1.1" 403 227 "-" "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/56.0.2924.90 Safari/537.36 2345Explorer/9.2.1.17116"
192.168.1.169 - - [29/Jun/2018:22:50:30 -0400] "GET /img/qqq.jpg HTTP/1.1" 200 22302 "http://b.com/img/" "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/56.0.2924.90 Safari/537.36 2345Explorer/9.2.1.17116"四、限定某个目录禁止解析php
有些目录是存放静态文件的目录,如图片目录,本身不需要允许php的解析。如果没有注意,允许了php解析,而且又开放了该目录的文件上传权限。很可能被别有用心的人利用上传木马,导致服务器被攻破。除了开发人员在程序开发过程中要注意安全的设计,也可以通过apache限制某些目录的php解析。
1.修改apache子配置文件/usr/local/apache2.4/conf/extra/httpd-vhosts.conf
[root@localhost img]# vim /usr/local/apache2.4/conf/extra/httpd-vhosts.conf
<VirtualHost *:80>
ServerAdmin [email protected]
DocumentRoot "/usr/local/apache2.4/htdocs/b.com"
ServerName b.com
//添加此段内容限制img目录的php解析权限
<Directory /usr/local/apache2.4/htdocs/b.com/img>
php_admin_flag engine off
</Directory>
<Directory /usr/local/apache2.4/htdocs/b.com>
<FilesMatch "admin.php(.*)">
Order deny,allow
Deny from all
Allow from 127.0.0.1 192.168.1.9
</FilesMatch>
</Directory>
ErrorLog "logs/b.com-error_log"
CustomLog "logs/b.com-access_log" combined
</VirtualHost>
2.检测配置及重载
[root@localhost img]# /usr/local/apache2.4/bin/apachectl -t
Syntax OK
[root@localhost img]# /usr/local/apache2.4/bin/apachectl graceful3.验证
本地验证
//无法解析
[root@localhost img]# curl -x127.0.0.1:80 b.com/img/admin.php
<?php
echo "b.com"
?>日志
127.0.0.1 - - [29/Jun/2018:23:33:18 -0400] "HEAD http://b.com/img/admin.php HTTP/1.1" 200 - "-" "curl/7.29.0"从远程浏览器访问
直接下载,无法解析
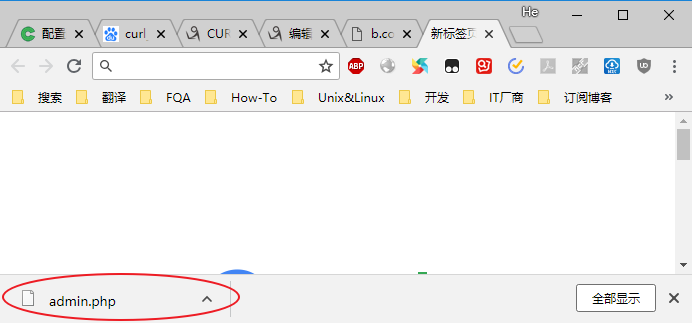
日志
192.168.1.9 - - [29/Jun/2018:23:37:05 -0400] "GET /img/admin.php HTTP/1.1" 200 23 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/67.0.3396.99 Safari/537.36"五、限制user_agent
有时候网站可能会遭受CC攻击,这可以通过限制user—agent来减小攻击压力。
CC攻击(Distributed HTTP flood,分布式HTTP洪水攻击)
CC攻击是DDoS攻击的一种类型,使用代理服务器向受害服务器发送大量貌似合法的请求(通常使用HTTP GET)。CC(Challenge Collapsar,挑战黑洞)根据其工具命名,攻击者创造性地使用代理机制,利用众多广泛可用的免费代理服务器发动DDoS攻击。许多免费代理服务器支持匿名模式,这使追踪变得非常困难。
以b.com为例
1.修改apache子配置文件/usr/local/apache2.4/conf/extra/httpd-vhosts.conf
[root@localhost img]# vim /usr/local/apache2.4/conf/extra/httpd-vhosts.conf
<VirtualHost *:80>
ServerAdmin [email protected]
DocumentRoot "/usr/local/apache2.4/htdocs/b.com"
ServerName b.com
//增加以下配置,限制curl,baidu.com代理的访问
<IfModule mod_rewrite.c>
RewriteEngine on
RewriteCond %{HTTP_USER_AGENT} .*curl.* [NC,OR]
RewriteCond %{HTTP_USER_AGENT} .*baidu.com.* [NC]
RewriteRule .* - [F]
</IfModule>
<Directory /usr/local/apache2.4/htdocs/b.com/img>
php_admin_flag engine off
</Directory>
<Directory /usr/local/apache2.4/htdocs/b.com>
<FilesMatch "admin.php(.*)">
Order deny,allow
Deny from all
Allow from 127.0.0.1 192.168.1.9
</FilesMatch>
</Directory>
ErrorLog "logs/b.com-error_log"
CustomLog "logs/b.com-access_log" combined
</VirtualHost>
2.测试配置文件及重载
[root@localhost img]# /usr/local/apache2.4/bin/apachectl -t
Syntax OK
[root@localhost img]# /usr/local/apache2.4/bin/apachectl graceful3.验证
//以curl代理访问,403错误被禁止,说明限制成功
[root@localhost img]# curl -x127.0.0.1:80 b.com/img/admin.php -I
HTTP/1.1 403 Forbidden
Date: Sat, 30 Jun 2018 05:21:36 GMT
Server: Apache/2.4.33 (Unix) PHP/5.6.30
Content-Type: text/html; charset=iso-8859-1
//baidu.com的代理也被限制,403禁止访问
[root@localhost img]# vim /usr/local/apache2.4/conf/extra/httpd-vhosts.conf
[root@localhost img]# curl -A "www.baidu.com" -x127.0.0.1:80 b.com/img/admin.php -I
HTTP/1.1 403 Forbidden
Date: Sat, 30 Jun 2018 05:27:45 GMT
Server: Apache/2.4.33 (Unix) PHP/5.6.30
Content-Type: text/html; charset=iso-8859-1
//以不受限代理访问,可以正常访问
[root@localhost img]# curl -A "kennminn" -x127.0.0.1:80 b.com/img/admin.php -I
HTTP/1.1 200 OK
Date: Sat, 30 Jun 2018 05:22:39 GMT
Server: Apache/2.4.33 (Unix) PHP/5.6.30
Last-Modified: Sat, 30 Jun 2018 01:04:12 GMT
ETag: "17-56fd18ae06548"
Accept-Ranges: bytes
Content-Length: 23
Content-Type: application/x-httpd-php
六、php相关配置
1.查看php配置文件:
[root@localhost img]# /usr/local/php/bin/php -i | grep -i "loaded configuration file"
PHP Warning: Unknown: It is not safe to rely on the system's timezone settings. You are *required* to use the date.timezone setting or the date_default_timezone_set() function. In case you used any of those methods and you are still getting this warning, you most likely misspelled the timezone identifier. We selected the timezone 'UTC' for now, but please set date.timezone to select your timezone. in Unknown on line 0
Loaded Configuration File => /usr/local/php/etc/php.ini通过-i选项查出来的配置文件有时候可能不准。最准确的是在网站目录下建立一个phpinfo()函数的页面来查看。
以b.com为例
//新建该页面
[root@localhost b.com]# cat /usr/local/apache2.4/htdocs/b.com/index.php
<?php
phpinfo();
?>从浏览器访问
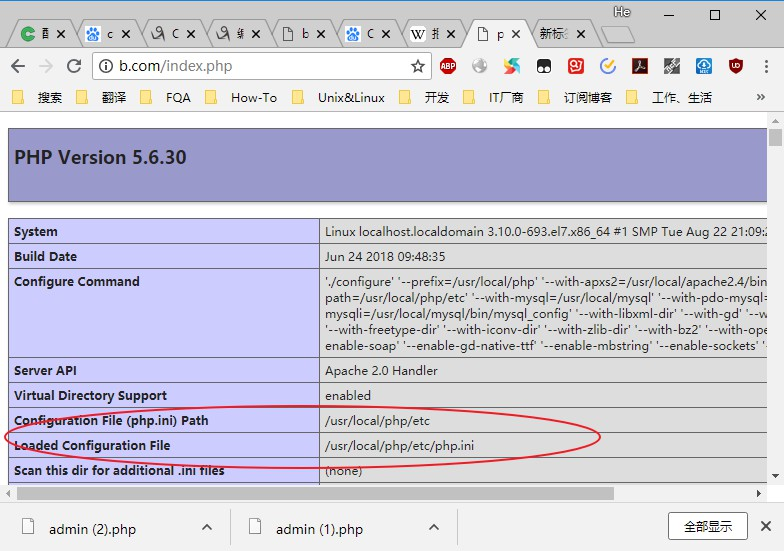
可以看到正确的php配置文件所在路径。
2.设置时区参数(date.timezone)
[root@localhost b.com]# vim /usr/local/php/etc/php.ini
[Date]
; Defines the default timezone used by the date functions
; http://php.net/date.timezone
//修改时区为亚洲/上海
date.timezone = Asia/Shanghai
; http://php.net/date.default-latitude
3.禁用特殊函数
[root@localhost b.com]# vim /usr/local/php/etc/php.ini
; It receives a comma-delimited list of function names.
; http://php.net/disable-functions
//将不常用特殊函数添加到此处进行限制,可以被一些木马利用。生产场景phpinfo()函数也会被禁用,避免泄露信息。
disable_functions = eval,assert,popen,passthru,escapeshellarg,escapeshellcmd,passthru,exec,system,chroot,scandir,chgrp,chown,escapeshellcmd,escapeshellarg,shell_exec,proc_get_status,ini_alter,ini_restore,dl,pfsockopen,openlog,syslog,readlink,symlink,leak,popepassthru,stream_socket_server,popen,proc_open,proc_close,phpinfo,
; This directive allows you to disable certain classes for security reasons.
phpinfo禁用后效果如下
[root@localhost ~]# curl -A "kennminn" -x127.0.0.1:80 b.com/index.php

4.显示错误信息
[root@localhost b.com]# vim /usr/local/php/etc/php.ini
; Production Value: Off
; http://php.net/display-errors
//修改为on可方便调试
display_errors = on
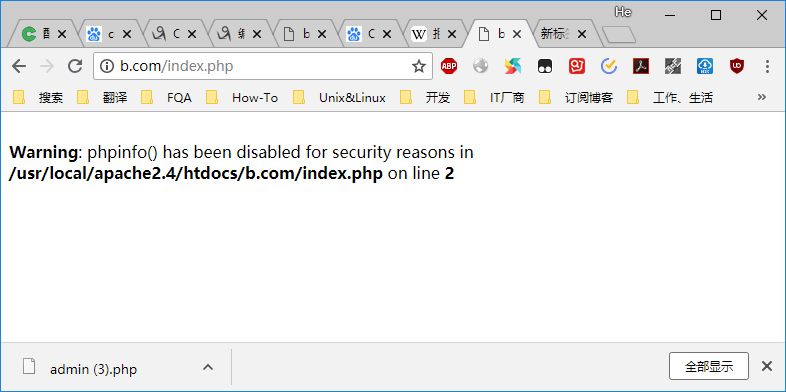
5.生产环境中不应显示错误信息在页面上。但是如果仅显示白页,就无法追踪错误。所以可以配置错误日志来记录相应的错误。
//开启错误日志记录功能
log_errors = On
//设置错误日志保存的位置
error_log = /tmp/php_errors.log
Log errors to syslog (Event Log on Windows).
;error_log = syslog
//定义日志级别,可以定义日志信息的内容。级别高,只会记录级别高的事件,如果级别低,记录的事件就会比较多。
//默认会记录所有的错误,但是不会记录通知和一般性的警告。
; Production Value: E_ALL & ~E_DEPRECATED & ~E_STRICT
; http://php.net/error-reporting
error_reporting = E_ALL & ~E_DEPRECATED & ~E_STRICT再访问b.com/index.php
/tmp下已经生成php_errors.log
[root@localhost ~]# ls /tmp/
mysql.sock systemd-private-05b1537c095c42ca87b1e5f8efea340a-chronyd.service-qFphPx
pear systemd-private-05b1537c095c42ca87b1e5f8efea340a-vgauthd.service-5t7uqL
php_errors.log systemd-private-05b1537c095c42ca87b1e5f8efea340a-vmtoolsd.service-dsi0fk
[root@localhost ~]# cat /tmp/php_errors.log
[30-Jun-2018 06:43:27 UTC] PHP Warning: phpinfo() has been disabled for security reasons in /usr/local/apache2.4/htdocs/b.com/index.php on line 2
[30-Jun-2018 06:43:28 UTC] PHP Warning: phpinfo() has been disabled for security reasons in /usr/local/apache2.4/htdocs/b.com/index.php on line 2
[30-Jun-2018 06:43:29 UTC] PHP Warning: phpinfo() has been disabled for security reasons in /usr/local/apache2.4/htdocs/b.com/index.php on line 2
6.open_basedir隔离虚拟主机目录
可以php.ini进行全局配置。但是无法细化。所以不推荐。
; and below. This directive makes most sense if used in a per-directory
; or per-virtualhost web server configuration file.
; http://php.net/open-basedir
//将目录限制在bbb.com,无此目录。
open_basedir = /usr/local/apache2.4/htdocs/bbb.com:/tmp/
; This directive allows you to disable certain functions for security reasons.
//测试配置及重载
[root@localhost ~]# /usr/local/apache2.4/bin/apachectl -t
Syntax OK
[root@localhost ~]# /usr/local/apache2.4/bin/apachectl graceful
//验证,500错误,无法正常访问
[root@localhost ~]# curl -x127.0.0.1:80 b.com/index.php -I
HTTP/1.0 500 Internal Server Error
Date: Sat, 30 Jun 2018 07:51:34 GMT
Server: Apache/2.4.33 (Unix) PHP/5.6.30
X-Powered-By: PHP/5.6.30
Connection: close
Content-Type: text/html; charset=UTF-8
//修改为正确有目录
; and below. This directive makes most sense if used in a per-directory
; or per-virtualhost web server configuration file.
; http://php.net/open-basedir
//将目录限制在b.com,此目录存在。
open_basedir = /usr/local/apache2.4/htdocs/b.com:/tmp/
; This directive allows you to disable certain functions for security reasons.
//测试配置及重载
[root@localhost ~]# /usr/local/apache2.4/bin/apachectl -t
Syntax OK
[root@localhost ~]# /usr/local/apache2.4/bin/apachectl graceful
//测试,可以正常访问了。
[root@localhost ~]#curl -x127.0.0.1:80 b.com/index.php -I
HTTP/1.1 200 OK
Date: Sat, 30 Jun 2018 07:57:03 GMT
Server: Apache/2.4.33 (Unix) PHP/5.6.30
X-Powered-By: PHP/5.6.30
Content-Type: text/html; charset=UTF-8也可以在apace子配置文件/usr/local/apache2.4/conf/extra/httpd-vhosts.conf针对每个虚拟主机来设置隔离。推荐此种方式。
[root@localhost b.com]# vim /usr/local/apache2.4/conf/extra/httpd-vhosts.conf
<VirtualHost *:80>
ServerAdmin [email protected]
DocumentRoot "/usr/local/apache2.4/htdocs/a.com"
ServerName a.com
ServerAlias aaa.com
//添加下述语句限制a.com的目录
php_admin_value open_basedir "/usr/local/apache2.4/htdocs/a.com:/tmp/"
ErrorLog "logs/a.com-error_log"
CustomLog "logs/a.com-access_log" combined
</VirtualHost>
<VirtualHost *:80>
ServerAdmin [email protected]
DocumentRoot "/usr/local/apache2.4/htdocs/b.com"
ServerName b.com
//添加下述语句限制b.com的目录
php_admin_value open_basedir "/usr/local/apache2.4/htdocs/b.com:/tmp/"
# <IfModule mod_rewrite.c>
# RewriteEngine on
# RewriteCond %{HTTP_USER_AGENT} .*curl.* [NC,OR]
# RewriteCond %{HTTP_USER_AGENT} .*baidu.com.* [NC]
# RewriteRule .* - [F]
# </IfModule>
# <Directory /usr/local/apache2.4/htdocs/b.com/img>
# php_admin_flag engine off
# </Directory>
# <Directory /usr/local/apache2.4/htdocs/b.com>
# <FilesMatch "admin.php(.*)">
# Order deny,allow
# Deny from all
# Allow from 127.0.0.1
# </FilesMatch>
# </Directory>
ErrorLog "logs/b.com-error_log"
CustomLog "logs/b.com-access_log" combined
</VirtualHost>
//测试配置文件及重载
[root@localhost b.com]# /usr/local/apache2.4/bin/apachectl -t
Syntax OK
[root@localhost b.com]# /usr/local/apache2.4/bin/apachectl graceful
//访问测试
[root@localhost b.com]# curl -x127.0.0.1:80 b.com/index.php -I
HTTP/1.1 200 OK
Date: Sat, 30 Jun 2018 08:31:26 GMT
Server: Apache/2.4.33 (Unix) PHP/5.6.30
X-Powered-By: PHP/5.6.30
Content-Type: text/html; charset=UTF-8七、php扩展模块安装
有时候php安装编译完成后,这时候发现缺少了一个模块,但又不想重新编译php模块,可以使用扩展模块编译。
查看模块
[root@localhost b.com]# /usr/local/php/bin/php -m
[PHP Modules]
bz2
Core
ctype
date
dom
ereg
exif
fileinfo
filter
gd
hash
iconv
json
libxml
mbstring
mcrypt
mysql
mysqli
openssl
pcre
PDO
pdo_mysql
pdo_sqlite
Phar
posix
Reflection
session
SimpleXML
soap
sockets
SPL
sqlite3
standard
tokenizer
xml
xmlreader
xmlwriter
zlib
[Zend Modules]
以redis包为例
1.下载redis软件包
[root@localhost b.com]# wget https://codeload.github.com/phpredis/phpredis/zip/develop -C /usr/local/src/phpredis-develop.zip
[root@localhost b.com]# ls /usr/local/src/
apr-1.6.3 apr-util-1.6.1 httpd-2.4.33 mysql-5.6.36 php-5.5.38.tar.bz2 php-5.6.30.tar.gz
apr-1.6.3.tar.gz apr-util-1.6.1.tar.gz httpd-2.4.33.tar.gz mysql-5.6.36.tar.gz php-5.6.30 phpredis-develop.zip2.解压软件包
[root@localhost src]# unzip phpredis-develop.zip3.切换到phpredis-develop目录
[root@localhost src]# cd phpredis-develop/
4.编译
//生成配置文件,比较特殊,默认的包没有.configure文件,需要用phpize生成
[root@localhost phpredis-develop]# /usr/local/php/bin/phpize
Configuring for:
PHP Api Version: 20131106
Zend Module Api No: 20131226
Zend Extension Api No: 220131226
//configure
[root@localhost phpredis-develop]# ./configure --with-php-config=/usr/local/php/bin/php-config
checking for grep that handles long lines and -e... /usr/bin/grep
checking for egrep... /usr/bin/grep -E
...中间略...
checking whether stripping libraries is possible... yes
checking if libtool supports shared libraries... yes
checking whether to build shared libraries... yes
checking whether to build static libraries... no
creating libtool
appending configuration tag "CXX" to libtool
configure: creating ./config.status
config.status: creating config.h
//编译安装
[root@localhost phpredis-develop]# make && make install
/bin/sh /usr/local/src/phpredis-develop/libtool --mode=compile cc -I. -I/usr/local/src/phpredis-develop -DPHP_ATOM_INC -I/usr/local/src/phpredis-develop/include -I/usr/local/src/phpredis-develop/main -I/usr/local/src/phpredis-develop -I/usr/local/php/include/php -I/usr/local/php/include/php/main -I/usr/local/php/include/php/TSRM -I/usr/local/php/include/php/Zend -I/usr/local/php/include/php/ext -I/usr/local/php/include/php/ext/date/lib -DHAVE_CONFIG_H -g -O2 -c /usr/local/src/phpredis-develop/redis.c -o redis.lo
mkdir .libs
...中间略...
See any operating system documentation about shared libraries for
more information, such as the ld(1) and ld.so(8) manual pages.
----------------------------------------------------------------------
Build complete.
Don't forget to run 'make test'.
Installing shared extensions: /usr/local/php/lib/php/extensions/no-debug-zts-20131226/
//根据提示,可以看到共享的扩展已经安装到了 /usr/local/php/lib/php/extensions/no-debug-zts-20131226/目录
[root@localhost phpredis-develop]# ls -l /usr/local/php/lib/php/extensions/no-debug-zts-20131226/
total 2572
-rwxr-xr-x. 1 root root 607600 Jun 24 09:49 opcache.so
-rwxr-xr-x. 1 root root 2023136 Jun 30 04:57 redis.so
5.配置加载扩展模块
//查看扩展模块存放目录
[root@localhost phpredis-develop]# /usr/local/php/bin/php -i |grep extension_dir
extension_dir => /usr/local/php/lib/php/extensions/no-debug-zts-20131226 => /usr/local/php/lib/php/extensions/no-debug-zts-20131226
sqlite3.extension_dir => no value => no value
//编译php.ini
[root@localhost phpredis-develop]# vim /usr/local/php/etc/php.ini
//在文件最后加添
extension = redis.so
//测试配置及重载
[root@localhost phpredis-develop]# /usr/local/apache2.4/bin/apachectl -t
Syntax OK
[root@localhost phpredis-develop]# /usr/local/apache2.4/bin/apachectl graceful
//验证
[root@localhost phpredis-develop]# /usr/local/php/bin/php -m | grep redis
redis另外一种方法快速安装redis.so模块 /usr/local/php7/bin/pecl install redis
技巧(以php-7为例):
如果想要编译一个模块,而且他自带的源码包目录/usr/local/src/php-7.1.6/ext 下有,那么只需要进行以下一些步骤,就可以完成扩展模块的安装
在你需要增加的拓展模块的目录下执行 /usr/local/php7/bin/phpize ,生成一个configure 文件
执行 ./configure –with-php-config=/usr/local/php7/bin/php-config 配置php-config文件
开始编译 make
编译后移动到目录 make install
修改配置文件vim /usr/local/php7/etc/php.ini ,新增所需extension=xxxxxxx.so 拓展模块
在PHP的源码包中没有第三方模块的包,但是在PHP源码包的/ext/目录下有好多扩展模块,如果所需要的扩展模块在该目录下,可以直接进行安装
在源码包中安装模块,在php的源码包中,有一个ext目录,这个目录下有很多的模块
[root@localhost php-7.1.6]# ls ext/
bcmath dom gd json odbc pdo_mysql pspell snmp sysvshm xsl
bz2 enchant gettext ldap opcache pdo_oci readline soap tidy zip
calendar exif gmp libxml openssl pdo_odbc recode sockets tokenizer zlib
com_dotnet ext_skel hash mbstring pcntl pdo_pgsql reflection spl wddx
ctype ext_skel_win32.php iconv mcrypt pcre pdo_sqlite session sqlite3 xml
curl fileinfo imap mysqli pdo pgsql shmop standard xmlreader
date filter interbase mysqlnd pdo_dblib phar simplexml sysvmsg xmlrpc
dba ftp intl oci8 pdo_firebird posix skeleton sysvsem xmlwriter
以添加zip模块为例
[root@localhost php-7.1.6]# /usr/local/php7/bin/php -m |grep zip
//当前没有zip模块
[root@localhost php-7.1.6]# 配置编译zip模块
[root@localhost php-7.1.6]# cd ext/zip/
//生成配置文件
[root@localhost zip]# /usr/local/php7/bin/phpize
Configuring for:
PHP Api Version: 20160303
Zend Module Api No: 20160303
Zend Extension Api No: 320160303
[root@localhost zip]#
//配置
[root@localhost zip]# ./configure --with-php-config=/usr/local/php7/bin/php-config
[root@localhost zip]# ./configure --with-php-config=/usr/local/php7/bin/php-config
checking for grep that handles long lines and -e... /usr/bin/grep
checking for egrep... /usr/bin/grep -E
checking for a sed that does not truncate output... /usr/bin/sed
checking for cc... cc
...中间略...
creating libtool
appending configuration tag "CXX" to libtool
configure: creating ./config.status
config.status: creating config.h
//编译安装
[root@localhost zip]# make && make install
[root@localhost php-7.1.6]# make && make install
/bin/sh /usr/local/src/php-7.1.6/libtool --silent --preserve-dup-deps --mode=compile /usr/local/src/php-7.1.6/meta_ccld -Iext/date/lib -DZEND_ENABLE_STATIC_TSRMLS_CACHE=1 -DHAVE_TIMELIB_CONFIG_H=1 -Iext/date/ -I/usr/local/src/php-7.1.6/ext/date/ -DPHP_ATOM_INC -I/usr/local/src/php-7.1.6/include -I/usr/local/src/php-7.1.6/main -I/usr/local/src/php-7.1.6 -I/usr/local/src/php-7.1.6/ext/date/lib -I/usr/include/libxml2 -I/usr/include/freetype2 -I/usr/local/src/php-7.1.6/ext/mbstring/oniguruma -I/usr/local/src/php-7.1.6/ext/mbstring/libmbfl -I/usr/local/src/php-7.1.6/ext/mbstring/libmbfl/mbfl -I/usr/local/mysql/include -I/usr/local/src/php-7.1.6/ext/sqlite3/libsqlite -I/usr/local/src/php-7.1.6/TSRM -I/usr/local/src/php-7.1.6/Zend -D_REENTRANT -I/usr/include -g -O2 -fvisibility=hidden -pthread -DZTS -DZEND_SIGNALS -c /usr/local/src/php-7.1.6/ext/date/php_date.c -o ext/date/php_date.lo
...中间略...
Build complete.
Don't forget to run 'make test'.
Installing shared extensions: /usr/local/php7/lib/php/extensions/no-debug-zts-20160303/
//查看模块
[root@localhost zip]# ls /usr/local/php7/lib/php/extensions/no-debug-zts-20160303/
opcache.so zip.so
//再在/usr/local/php7/etc/php.ini文件最后添加
extension = zip.so
//检查配置及重载
[root@localhost zip]# /usr/local/apache2.4/bin/apachectl -t
Syntax OK
[root@localhost zip]# /usr/local/apache2.4/bin/apachectl graceful
//模块已经添加
[root@localhost zip]# /usr/local/php7/bin/php -m |grep zip
zip
八、扩展
几种限制ip的方法 http://ask.apelearn.com/question/6519
apache 自定义header http://ask.apelearn.com/question/830
apache的keepalive和keepalivetimeout http://ask.apelearn.com/question/556
apache开启压缩 http://ask.apelearn.com/question/5528
apache2.2到2.4配置文件变更 http://ask.apelearn.com/question/7292
apache options参数 http://ask.apelearn.com/question/1051
apache禁止trace或track防止xss http://ask.apelearn.com/question/1045
apache 配置https 支持ssl http://ask.apelearn.com/question/1029
apache rewrite教程 http://coffeelet.blog.163.com/blog/static/13515745320115842755199/ http://www.cnblogs.com/top5/archive/2009/08/12/1544098.html
apache rewrite 出现死循环 http://ask.apelearn.com/question/1043
php错误日志级别参考 http://ask.apelearn.com/question/6973
php开启短标签 http://ask.apelearn.com/question/120
php.ini详解 http://legolas.blog.51cto.com/2682485/493917

















































