版权声明:本文为博主原创文章,未经博主允许不得转载。 https://blog.csdn.net/u012325865/article/details/81784517
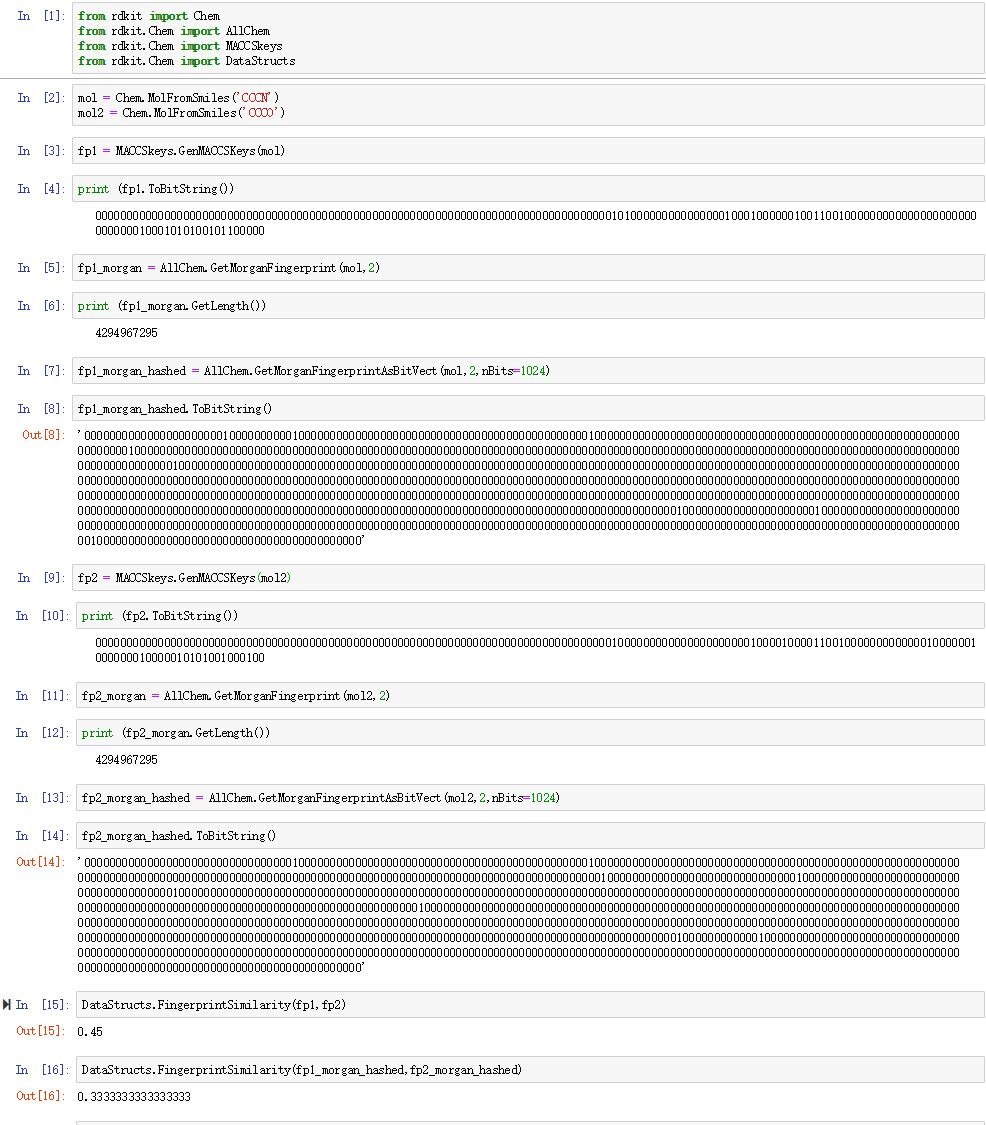
化学指纹识别是一种将绘制的分子转换为0和1位的流的方法。旧指纹类型是MACCS密钥,由前MDL开发,作为在分子数据库中进行子结构筛选的快速方法。公共版本包含166个键,即166 0和1,其中每个键对应于特定的分子特征,例如存在羰基(键154:('[#6] = [#8]',0),RDkit中的#C = O.实现).RDkit中可用的另一种指纹是摩根型指纹,它是一种圆形指纹。每个原子的环境和连通性被分析到给定的半径,并且每种可能性都被编码。通常使用散列算法将很多可能性压缩到预定长度,例如1024。因此,圆形指纹是原子类型和分子连通性的系统探索,而MACCS键依赖于要匹配的预定义分子特征。
#!/usr/bin/python3
# In[1]:
from rdkit import Chem
from rdkit.Chem import AllChem
from rdkit.Chem import MACCSkeys
from rdkit.Chem import DataStructs
# In[2]:
mol = Chem.MolFromSmiles('CCCN')
mol2 = Chem.MolFromSmiles('CCCO')
# In[3]:
fp1 = MACCSkeys.GenMACCSKeys(mol)
# In[4]:
print (fp1.ToBitString())
# out[4]:
00000000000000000000000000000000000000000000000000000000000000000000000000000000001010000000000000001000100000010011001000000000000000000000000000010001010100101100000
# In[5]:
fp1_morgan = AllChem.GetMorganFingerprint(mol,2)
# In[6]:
print (fp1_morgan.GetLength())
# out[6]:
4294967295
# In[7]:
fp1_morgan_hashed = AllChem.GetMorganFingerprintAsBitVect(mol,2,nBits=1024)
# In[8]:
fp1_morgan_hashed.ToBitString()
# out[8]:
'0000000000000000000000100000000001000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000000000000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000000000000000'
# In[9]:
fp2 = MACCSkeys.GenMACCSKeys(mol2)
# In[10]:
print (fp2.ToBitString())
# out[10]:
00000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000000100001000011001000000000000010000001000000010000010101001000100
# In[11]:
fp2_morgan = AllChem.GetMorganFingerprint(mol2,2)
# In[12]:
print (fp2_morgan.GetLength())
# out[12]:
4294967295
# In[13]:
fp2_morgan_hashed = AllChem.GetMorganFingerprintAsBitVect(mol2,2,nBits=1024)
# out[13]:
'0000000000000000000000000000000001000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000100000000000000000000000000000000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000'
# In[14]:
fp2_morgan_hashed.ToBitString()
# In[15]:
DataStructs.FingerprintSimilarity(fp1,fp2)
# out[15]:
0.45
# In[16]:
DataStructs.FingerprintSimilarity(fp1_morgan_hashed,fp2_morgan_hashed)
# out[16]:
0.3333333333333333