因入职不久,新公司采用的网络设备多以思科为主,尤其思科防火墙之前接触较少,特意整理此篇留作记录。
首先声明,配置文档皆出自思科官网文档,有部分翻译是个人理解,有些建议还是看原文会比较好。
把关于NAT这块的一些东西配图加过程、配置保存出来,加深理解。后期会更新VPN配图原理、过程、配置部分的整理。
1、基于路由模式的NAT图例及配置:
hostname(config)#nat(inside) 1 10.1.2.0 255.255.255.0
hostname(config)#global(outside) 1 209.165.201.1-209.165.201.15
只是配置了内网主动访问外网的NAT配置,图例中的回程连接属于内网主动发起后外网响应的连接;
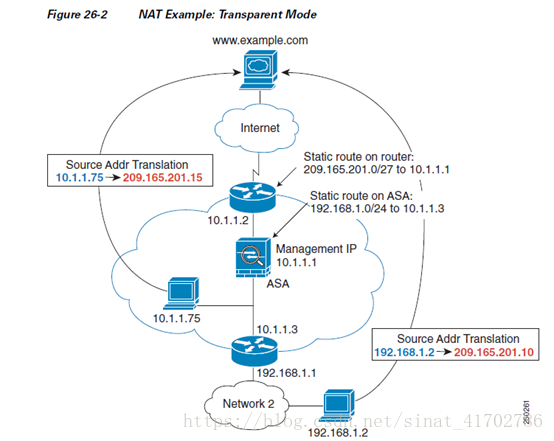
2、基于透明传输模式的NAT,需要在防火墙和防火墙上层路由器做静态路由回指
1. When the inside host at10.1.1.75 sends a packet to a web server, the real source address of the
packet, 10.1.1.75, ischanged to a mapped address, 209.165.201.15.
2. When the serverresponds, it sends the response to the mapped address, 209.165.201.15, and the
ASA receives thepacket because the upstream router includes this mapped network in a staticroute
directed through theASA.
3. The ASA then undoes thetranslation of the mapped address, 209.165.201.15, back to the real
address, 10.1.1.1.75.Because the real address is directly-connected, the ASA sends it directly tothe
host.
4. For host 192.168.1.2,the same process occurs, except that the ASA looks up the route in its route
table and sends thepacket to the downstream router at 10.1.1.3 based on the static route.
See the followingcommands for this example:
hostname(config)# route inside 192.168.1.0 255.255.255.0 10.1.1.3 1
hostname(config)# nat (inside) 1 10.1.1.0 255.255.255.0
hostname(config)# nat (inside) 1 192.168.1.0 255.255.255.0
hostname(config)# global (outside) 1 209.165.201.1-209.165.201.15
同样的,只是配置了内网主动访问外网的NAT配置,图例中的回程连接属于内网主动发起后外网响应的连接;
3、Policy-NAT
Figure 26-3 shows a host on the 10.1.2.0/24 network accessing two different servers.When the host
accesses the server at 209.165.201.11, the real address is translated to209.165.202.129. When the host
accesses the server at 209.165.200.225, the real address is translated to209.165.202.130.
hostname(config)#access-list NET1 permit ip 10.1.2.0 255.255.255.0 209.165.201.0
255.255.255.224
hostname(config)#access-list NET2 permit ip 10.1.2.0 255.255.255.0 209.165.200.224
255.255.255.224
hostname(config)# nat(inside) 1 access-list NET1
hostname(config)# global(outside) 1 209.165.202.129
hostname(config)# nat(inside) 2 access-list NET2
hostname(config)# global(outside) 2 209.165.202.130
inside组和outside组ID号对应,类似的,如果内网访问同一台server的不同端口,需要NAT成不同IP地址,在access-list中添加端口参数;
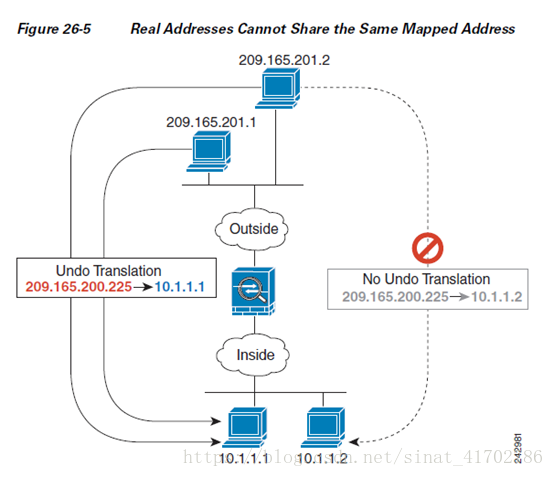
4、使用策略NAT时多个地址无法共享一个,看例子(只是在配置Policy-NAT的一个思路):
See the followingcommands for this example. (Although the second ACE in the example does allow
209.165.201.2 to connectto 209.165.200.225, it only allows 209.165.200.225 to be translated to
10.1.1.1.)
hostname(config)# static(in,out) 209.165.200.225 access-list policy-nat
hostname(config)#access-list policy-nat permit ip host 10.1.1.1 host 209.165.201.1
hostname(config)#access-list policy-nat permit ip host 10.1.1.2 host 209.165.201.2
做了以上策略NAT,目的是想当外网209.165.201.1访问209.165.200.225这个时候映射到10.1.1.1;当外网209.165.201.2访问209.165.200.225这个时候映射到10.1.1.2;而实际上做了策略之后,外网访问209.165.200.225只会映射到
10.1.1.1
5、防火墙上NAT匹配操作顺序:
The ASA matches realaddresses to NAT commands in the following order:
1. NATexemption (nat 0 access-list)—Inorder, until the first match.Identity NAT is not included in
this category; it isincluded in the regular static NAT or regular NAT category. We do not recommend
overlapping addresses inNAT exemption statements because unexpected results can occur.
2. Static NATand Static PAT (regular and policy) (static)—In order, until the first match. Static
identity NAT is includedin this category.
3. Policydynamic NAT (nat access-list)—In order, until the first match. Overlapping addresses are
allowed.
4. Regulardynamic NAT (nat)—Best match.Regular identity NAT is included in this category. The
order of the NAT commandsdoes not matter; the NAT statement that best matches the real address
is used. For example, youcan create a general statement to translate all addresses (0.0.0.0) on an
interface. If you want totranslate a subset of your network (10.1.1.1) to a different address, then you
can create a statement totranslate only 10.1.1.1. When 10.1.1.1 makes a connection, the specific
statement for 10.1.1.1 isused because it matches the real address best. We do not recommend using
overlapping statements; they use more memory and can slow the performance of the ASA.
6、一旦配置了动态NAT或PAT的时候,流量中存在未做NAT的数据,不会进行数据穿透完成访问。必须匹配一条rule,匹配失败则丢弃,没有做任何动态NAT或PAT时,外网正常情况可以访问一个公网IP地址。
7、Static NAT,静态NAT允许外网主动发起连接到mappedaddress to inside hosts,这是和动态NAT的区别。
8、允许属于ASA不同内部区域的地址重叠:
Two networks use anoverlapping address space (192.168.100.0/24), but hosts on each network must
communicate (as allowedby access lists). Without NAT, when a host on the inside network tries toaccess
a host on the overlappingDMZ network, the packet never makes it past the ASA, which sees the packet
as having a destinationaddress on the inside network. Moreover, if the destination address is beingused
by another host on theinside network, that host receives the packet.
To solve this problem,use NAT to provide non-overlapping addresses. If you want to allow access in
both directions, use static NATfor both networks. If you onlywant to allow the inside interfaceto access
hostson the DMZ, thenyou can use dynamic NAT for the inside addresses, and static NAT for theDMZ
addresses you want to access. This example shows static NAT.
想inside和dmz区域双向互访(即双方都可以主动initiate connection),就采用静态NAT,只想一边访问另外一边,使用动态NAT。静态NAT的例子:
Step 1 Translate 192.168.100.0/24 on the inside to 10.1.2.0/24when it accesses the DMZ by entering the
following command:
hostname(config)# static(inside,dmz) 10.1.2.0 192.168.100.0 netmask 255.255.255.0
Step 2 Translate the 192.168.100.0/24 network on the DMZ to10.1.3.0/24 when it accesses the inside by
entering the followingcommand:
hostname(config)# static(dmz,inside) 10.1.3.0 192.168.100.0 netmask 255.255.255.0
Step 3 Configure the following static routes so that traffic tothe dmz network can be routed correctly by the
ASA:
hostname(config)# routedmz 192.168.100.128 255.255.255.128 10.1.1.2 1
hostname(config)# route dmz192.168.100.0 255.255.255.128 10.1.1.2 1
过程如下:
If host 192.168.100.2 onthe DMZ network wants to initiate a connection to host 192.168.100.2 on the
inside network, thefollowing events occur:
1. The DMZ host192.168.100.2 sends the packet to IP address 10.1.2.2.
2. When the ASA receivesthis packet, the ASA translates the source address from 192.168.100.2 to
10.1.3.2.
3. Then the ASAtranslates the destination address from 10.1.2.2 to 192.168.100.2, and thepacket is
forwarded.
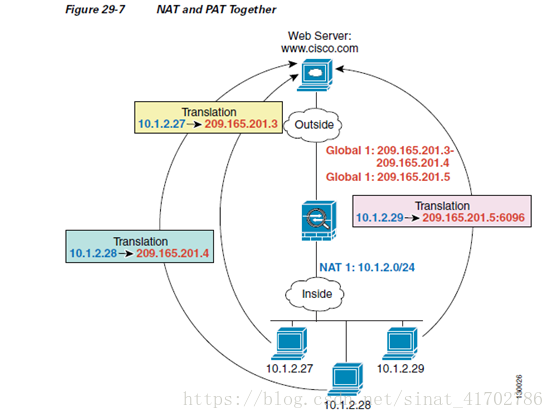
9、内网NAT地址池和global的NAT地址池按照编号ID对应,比如一个insidenat 1
和global nat1 ,global nat 2,1和1对应。可以建立多个inside 1用来添加需要映射的内网IP地址。指定一个外网映射地址的为PAT,指定一组外网映射地址的为NAT,两者都属于动态NAT:
hostname(config)# nat(inside) 1 10.1.2.0 255.255.255.0
hostname(config)# global(outside) 1 209.165.201.3-209.165.201.4
hostname(config)# global(outside) 1 209.165.201.5
global (outside)1里面201.3和201.4为直接NAT,201.5为PAT。
10、Outside NAT和Inside NAT结合的方式,比如防火墙中的dmz区域要同时访问outside和inside:
hostname(config)# nat(dmz) 1 10.1.1.0 255.255.255.0 outside
//建立dmz区域的需要nat的地址段,且标记匹配id为1,并且为outside;
hostname(config)# nat(dmz) 1 10.1.1.0 255.255.255.0
//建立dmz区域需要nat的地址段(应该默认是访问inside地址段,所以后面不带参数)
hostname(config)# static(inside,dmz) 10.1.1.5 10.1.2.27 netmask 255.255.255.255
hostname(config)# global(outside) 1 209.165.201.3-209.165.201.4
//访问外网通过outside域时,nat地址池
hostname(config)# global(inside) 1 10.1.2.30-1-10.1.2.40
//访问inside区域时,nat地址池;
11、静态PAT,即指定端口的静态映射方式:
hostname(config)# static(inside,outside) tcp 209.165.201.3 ftp 10.1.2.27 ftp netmask 255.255.255.255
//指定访问外网209.165.201.3的21端口映射到内网10.1.2.27的21端口。
要求如下:•
1、 Telnetrequests to IP address 209.165.201.5 are redirected to 10.1.1.6.
209.165.201.5访问25的telnet端口映射到10.1.1.6的23端口
2、FTP requests to IP address 209.165.201.5 are redirectedto 10.1.1.3.
•3、HTTP request to an ASA outside IP address 209.165.201.25are redirected to 10.1.1.5.
•4、HTTP port 8080 requests to PAT address 209.165.201.15are redirected to 10.1.1.7 port 80.
hostname(config)# nat (inside) 1 0.0.0.0 0.0.0.0 0 0
hostname(config)# global (outside) 1 209.165.201.15
//首先对内网所有主机做一条默认的PAT,允许正常访问外网。
hostname(config)# static (inside,outside) tcp 209.165.201.5 telnet 10.1.1.6telnet netmask 255.255.255.255
hostname(config)# static (inside,outside) tcp 209.165.201.5 ftp 10.1.1.3ftp netmask 255.255.255.255
hostname(config)# static (inside,outside) tcp interface www 10.1.1.5 wwwnetmask 255.255.255.255
hostname(config)# static (inside,outside) tcp 209.165.201.15 8080 10.1.1.7www netmask 255.255.255.255
12、NAT exempt :NAT豁免,即不NAT直接访问。
NAT豁免使用ID编号为0
Eg:nat(inside) 0 access-list EXEMPT,处于inside域的匹配ACL中的地址段将允许不做NAT直接访问。
12、默认情况下:思科的防火墙不允许inside进来的流量,未经其它接口出去而直接从inside返回(会被ASA直接丢弃)。要打破这一限制,可以使用Hairpinning+static NAT:
原理是允许inside进来的流量,未经其它接口出去而直接从inside接口返回,命令为:
same-security-traffic permit intra-interface,举例配置:
1、same-security-traffic permit intra-interface
!--- 启用Hairpinning功能,允许流量直接原路径返回。
2、nat(inside) 1 192.168.100.0 255.255.255.0
!--- 为内网用户访问公网定义NAT。
3、global(outside) 1 interface
!--- 为内网用户访问公网定义global地址。
4、global (inside) 1 interface
!--- 为内网用户使用Hairpinning访问内部服务器定义global地址。
5、static(inside,outside) 8.8.8.8 192.168.1.8 netmask 255.255.255.255
!--- 使用StaticNAT映身一台服务器,公网IP 8.8.8.8,内网IP192.168.1.8。
6、static (inside,inside) 8.8.8.8 192.168.1.8 netmask 255.255.255.255
!--- 为Hairpinning流量返回路径定义NAT映射:8.8.8.8----> 192.168.1.8。
7、access-listoutside_access_in extended permit tcp any host 8.8.8.8 eq 80
!--- 配置ACL对外发布WWW服务,端口为80。
8、access-groupoutside_access_in in interface outside
!--- 将ACL应用到外部接口。